SAML Domains
After selecting an alias and the SAML2 domain type, the Domain configuration wizard will present the options for configuring the SAML Domain as seen below.
SAML Configuration Options
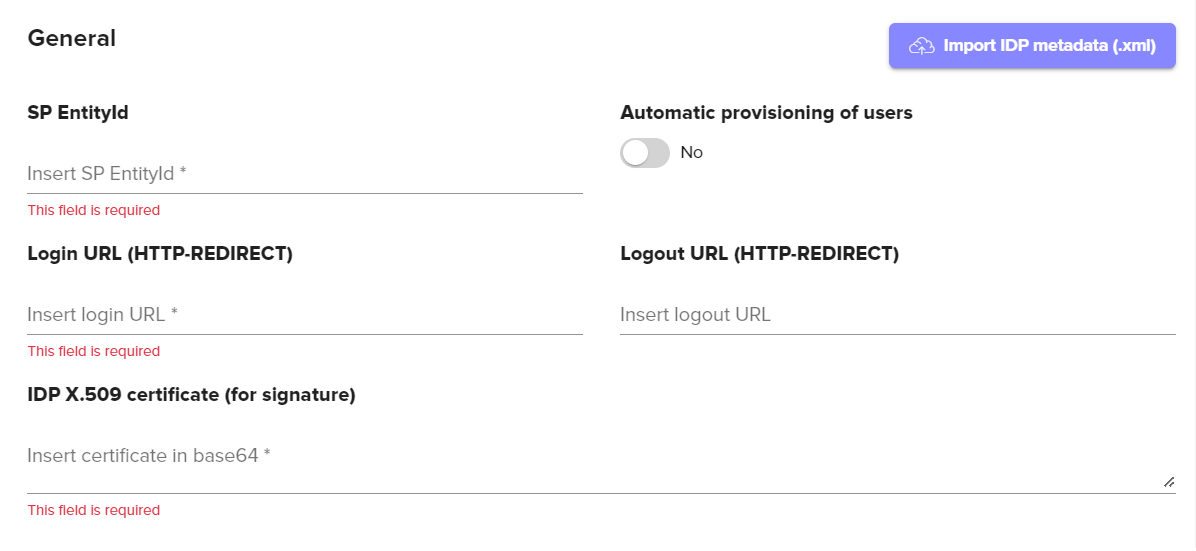
General Configuration Options | Description |
|---|---|
EntityId | This value will be “https://the-url-of-your-signum-deployment.com/the-alias-of-your-domain. For example, if the Alias of your SAML Domain was companyname.com this would be “https://signumdemo.com/companyname.com”. |
Import IDP Metadata | This option allows for importing an .xml configuration file from your IDP and will help auto-populate some of the IDP provided configuration fields in Signum. |
Automatic Provisioning of Users | If enabled, this setting will import a user's email, name, and group membership in Signum the first time the user authenticates against the IDP. If this setting is not enabled, you will need to manually populate these data fields for users. Troubleshooting Tip You may see an error, “User found, but does not belong to any roles” when attempting to login to Signum after authenticating with the IDP. This is because every user accessing the Admin Web Console must be assigned a Role in Signum and the authenticating user has not yet been assigned one by the Signum Administrator. This can be solved by either having the System Admin login to Signum and assign this new Signum user to a role or by using SAML Groups to assign an entire group of users to a particular role which will allow those group members to automatically log in. |
Login URL | This will be provided by your IDP. |
Logout URL | This will be provided by your IDP. |
IDP X.509 Certificate | This will be provided by your IDP. |
IDP Configuration | Description |
|---|---|
URL for Assertions | Configured at your IDP. This value will be “https://the-url-of-your-signum-deployment.com/Auth/SamlConsumer”. For example, if the URL of your Signum deployment is signumdemo, this value would be “https://signumdemo.com/Auth/SamlConsumer” . |
SAML Attribute Mapping
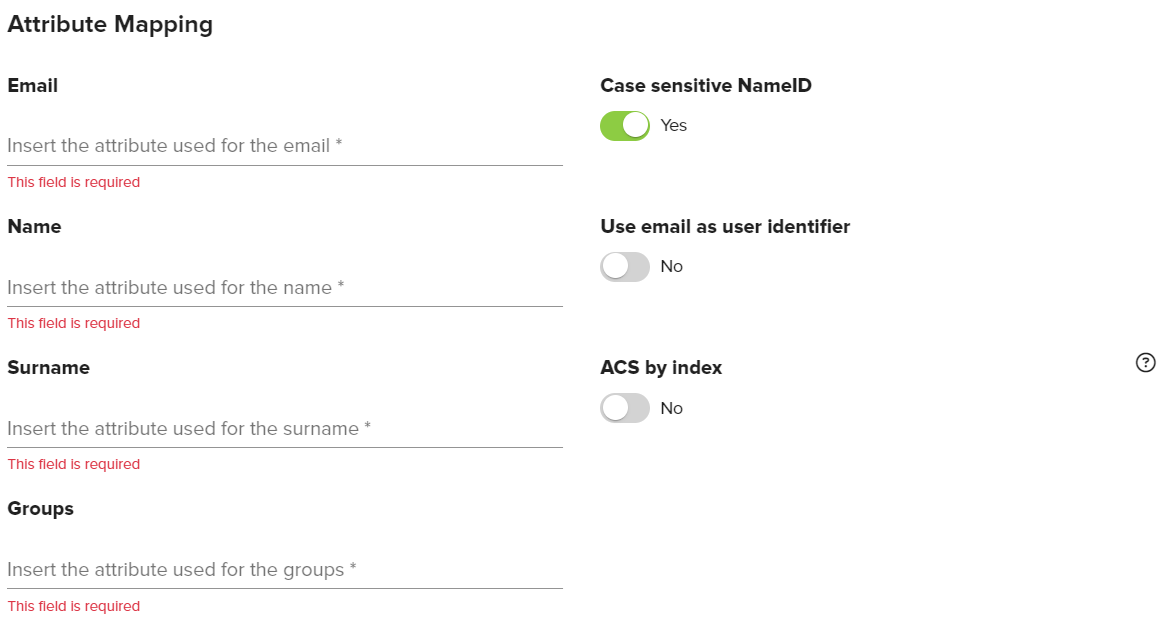
Attribute Mapping Options | Description |
|---|---|
The value you have configured for the “email” attribute in the SAML assertion. | |
Name | The value you have configured for the “name” attribute in the SAML assertion. |
Surname | The value you have configured for the “surname” attribute in the SAML assertion. |
Groups | The value you have configured for the “groups” attribute in the SAML assertion. |
Case Sensitive NameID | Enabled by default. When enabled this setting treats the NameID field as case sensitive. |
Use email as User Identifier | Enable this option if your organization uses the email attribute as the identifier for users instead of name or surnames. Note, this option needs to be configured at the time of domain creation. It is not possible to edit this property once a domain has been created. Most use cases will want to enable this setting. |
ACS by index | Disabled by default. This property specifies how to indicate to the IDP (through the SAML authentication request) the URL that will consume the SAML assertion generated by the IDP. If it is disabled, AssertionConsumerServiceURL will be added to the authentication request. If it is enabled, AssertionConsumerServiceIndex will be added in the request. If it is enabled, you must configure the IDP so that the index "0" corresponds to the URL "https://the-url-of-your-signum-deployment/Auth/SamlConsumer". |
SSO Login Button
You can enable a UI button on the Admin Web Console login page both during and after the creation of a SAML domain. This button allows users to go directly to the Identity Provider (IDP). This feature applies to both SAML and OAuth2 domains. If needed, multiple domains can be configured this way, enabling authentication with multiple IDPs directly from the login page.
To enable, select SAML or Oauth domain that has been created from the list of domains (Access>Domains) and toggle the SSO Login Button.
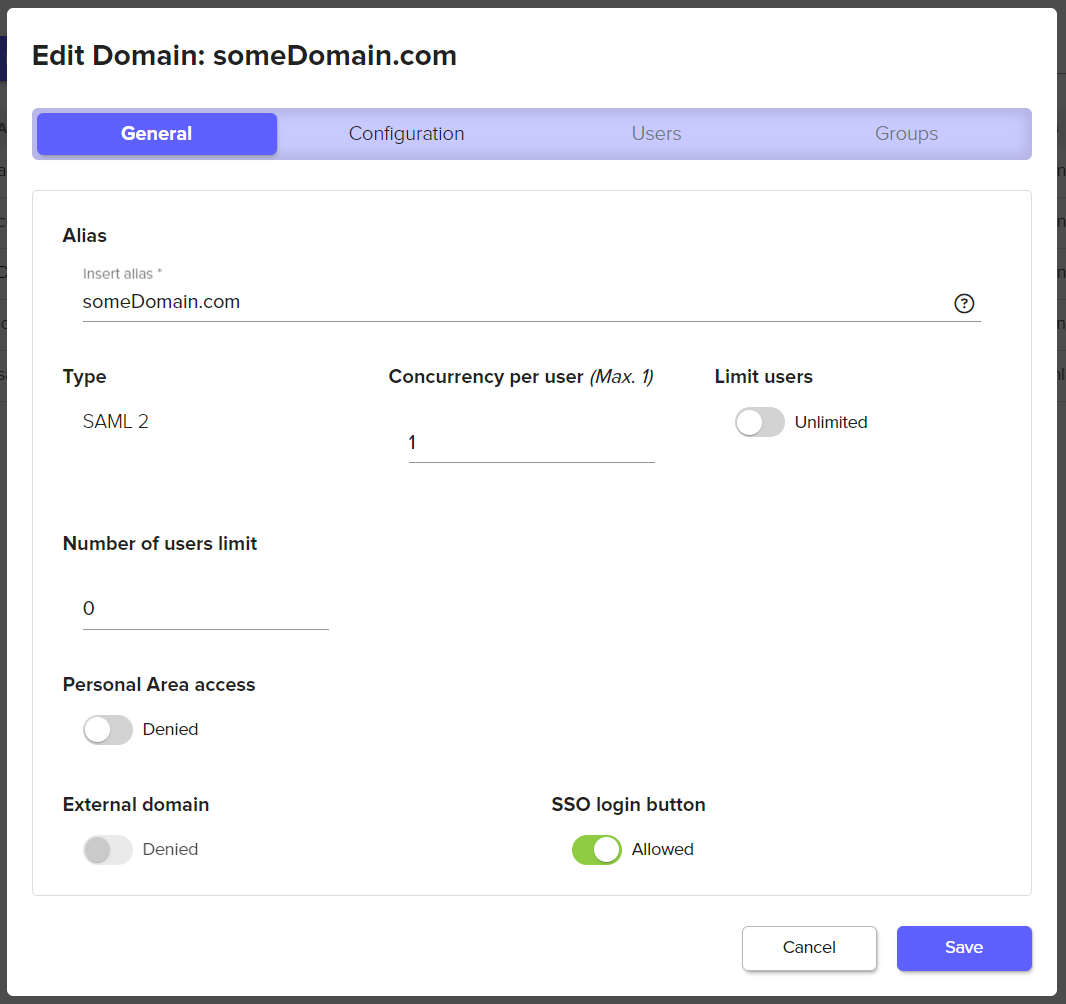
On the Admin Web Console login page you should now see a button with the alias of your domain.

IDP URL Configuration
Users can also be directed directly to the IDP login page, skipping the Signum login page by navigating directly to a URL with the below configuration. After authenticating, the user will be sent back to the Signum Admin Web Console.
URL |
|---|
https://Your-Signum-URL/login?domain=The-Domain-Alias |
.png)