EJBCA 8.3 Release Notes
MAY 2024
The EJBCA team is pleased to announce the release of EJBCA 8.3. With this release, the EJBCA Container Set is introduced for customer EJBCA deployment on Kubernetes using the Helm charts also part of the release. The release also brings support for hybrid certificates and MS Auto-enrollment improvements among other things.
For available deployment options and associated versions, refer to Supported Versions.
Highlights
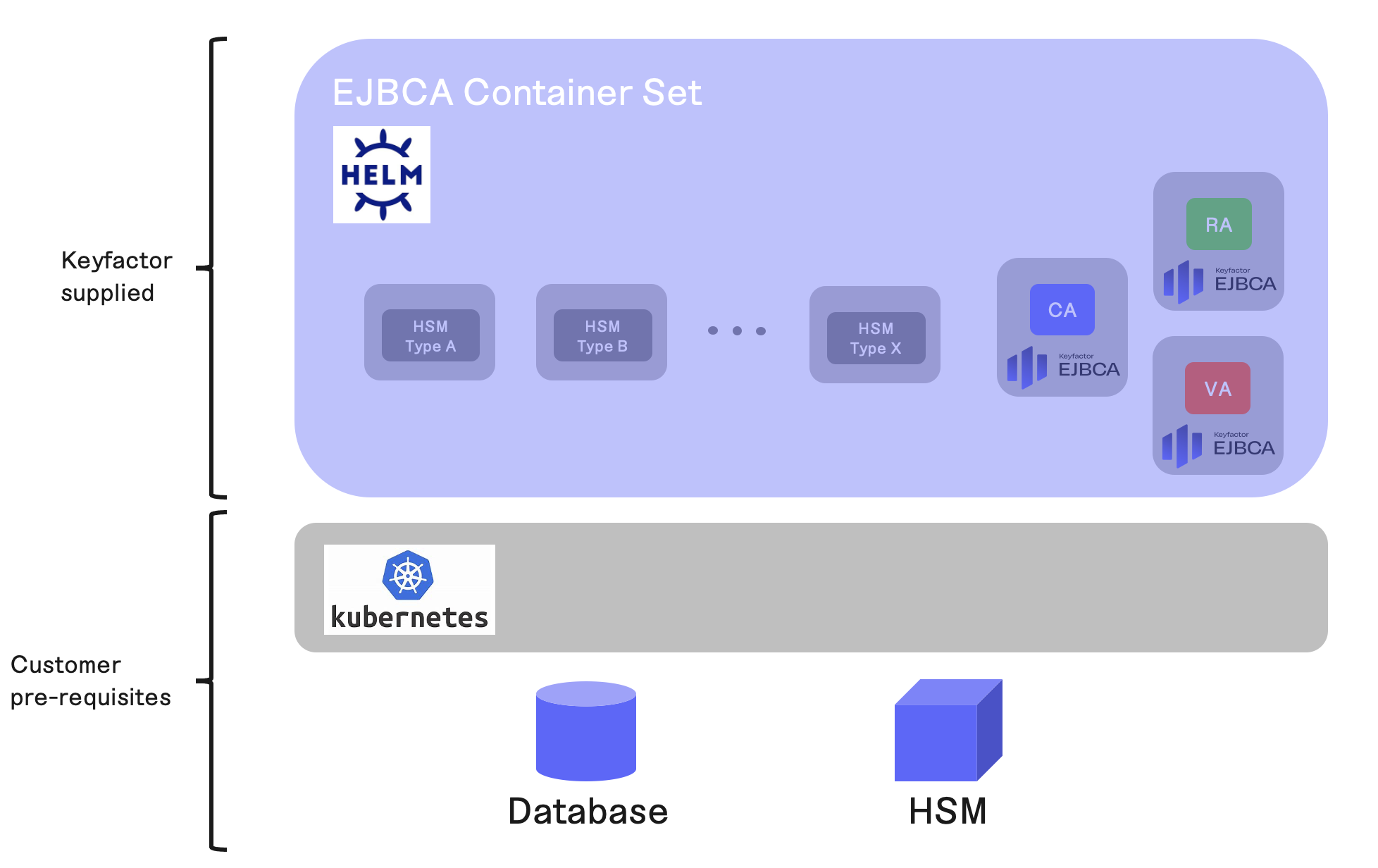
EJBCA Container Set
EJBCA introduces the EJBCA Container Set, enabling customers to deploy EJBCA on Kubernetes using Helm charts included in this release. The EJBCA Container Set provides separate container variants for Certificate Authority (CA), Registration Authority (RA), and Validation Authority (VA). Customer deployments are designed to utilize a setup where RA(s) and VA(s) are distinct EJBCA instances from the CA(s), connected via the Peers protocol.
For Hardware Security Module (HSM) integration in a container-based deployment, the EJBCA Container Set includes sidecar containers tailored to each supported HSM type. Alternatively, an EJBCA container-based deployment may integrate with HSMs using REST API integrations, which do not require a sidecar container.
Hybrid Certificates
EJBCA 8.3 introduces support for hybrid certificates, enabling the use of multiple signing keys in a single hybrid CA. Certificates issued by this CA will have signatures and public keys of two different algorithms. Typically, the system is set up to use a quantum-safe algorithm as the alternative algorithm. This setup allows parts of the ecosystem to validate the certificate using both keys and algorithms, while other parts may ignore the non-critical extensions and alternative algorithm, treating the certificate as a traditional RSA/ECC X.509 certificate.
Note that the quantum-safe algorithms currently implemented in EJBCA are NIST draft algorithms and not for production use, see Hybrid CA.
Microsoft Auto-Enrollment Improvements
Microsoft Auto-enrollment support has been significantly improved. It is recommended to configure auto-enrollment aliases on the CA(s) rather than the RA(s) in distributed deployments, enhancing operations in multi-domain and multi-RA deployments. Additionally, ECDSA is now supported as an algorithm in Microsoft auto-enrollment. EJBCA 8.3 also introduces the "supply in the request" option for Subject Name. For more information, see Microsoft Auto-enrollment Overview.
EJBCA updated with top-level menu
EJBCA now has a top-level menu, relocated from the left side to align with other Keyfactor products. The menu structure remains the same, ensuring that existing users can find previous menu items under the corresponding top-level categories.
Documentation on docs.keyfactor.com
As of EJBCA 8.3, the EJBCA product documentation is available at docs.keyfactor.com.
EJBCA RA Web Translated to French
The EJBCA RA user interface is now available in French. A huge thank you goes out to David Carella from Linagora who made this possible.
Announcements
Upcoming Technology Stack upgrade in EJBCA 9
As a Java application running on an application server, EJBCA 8.3 runs on WildFly 24/26 or JBoss EAP 7.4 and supports running on Java 11 or Java 17. Due to changes in recent WildFly versions and JBoss EAP 8 that are not backward compatible with WildFly 26 and JBoss 7.4, the upgrade from EJBCA 8 to the upcoming new major version EJBCA 9 will require a complete tech stack upgrade.
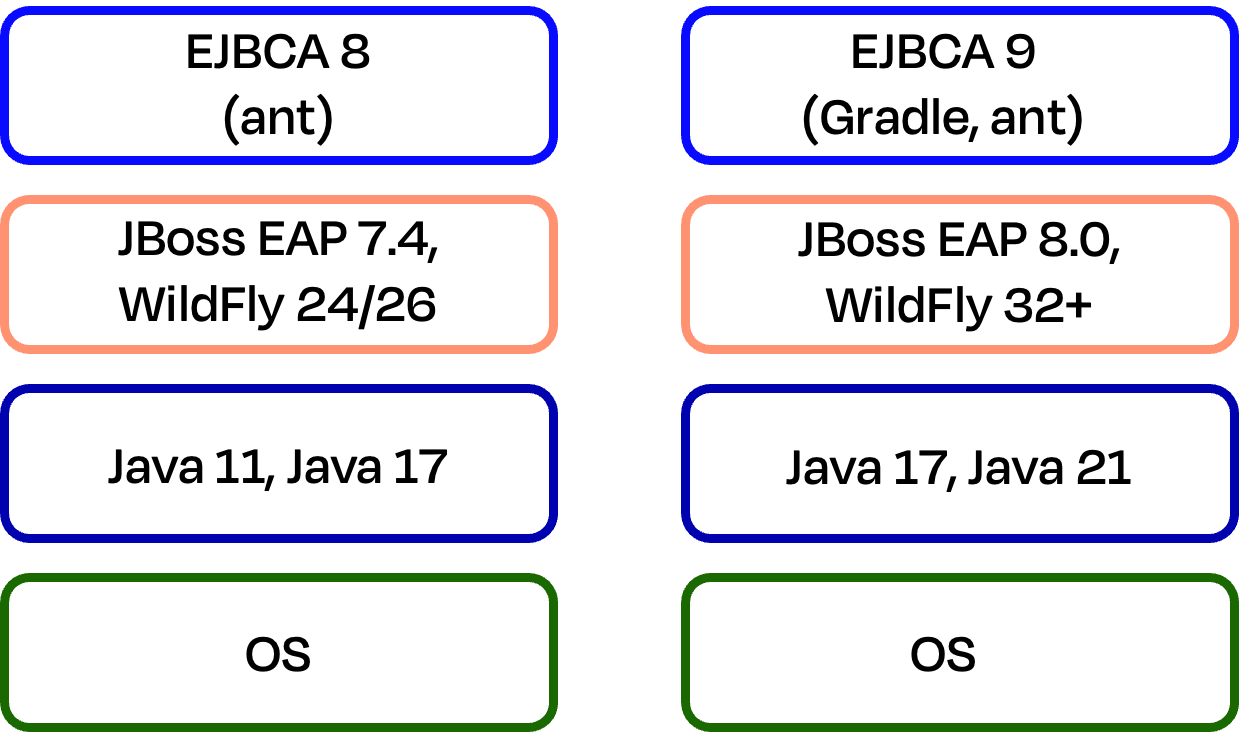
Overview of the EJBCA 8 and EJBCA 9 tech stacks
Overview of the EJBCA 8 and EJBCA 9 tech stacks.
EJBCA customers with software-based deployments are advised to plan for an upgrade to the EJBCA 9 tech stack once EJBCA 9 is released during the second half of 2024.
Security Issue
EJBCA 8.3 resolves a security issue affecting the CMP CLI client bundled with EJBCA. The issue does not affect EJBCAs server-side CMP implementation.
We rate the issue as having a severity level of medium. Once EJBCA 8.3 has been generally available across all platforms for at least two weeks, a CVE with the identifier CVE-2024-36066 will be published.
Removal of legacy OCSP key renewal mechanism
A legacy key renewal mechanism (using the SOAP API) has been removed, as it has been made redundant by automated key renewal over Peers for a few years. With this, properties matching ocsp.rekeying.* in ocsp.properties are no longer used and can be removed.
Deprecation of Certificate Profile and revocation status specific OCSP Response validities
Response validities (and Max-Age for the HTTP header) can be configured to be specially handled per certificate profile or if the status is revoked by setting them in ocsp.properties. This functionality has been redundant for the last few years by instead configuring the values in the OCSP Responder, and will be removed in the next release of EJBCA. The properties that will be removed are:
ocsp.999.untilNextUpdate
ocsp.999.revoked.untilNextUpdate
ocsp.999.maxAge
ocsp.999.revoked.maxAge
In addition, the following properties were unused and have been removed in this release:
ocsp.revoked.untilNextUpdate
ocsp.revoked.maxAge
Deprecation of DSTU and GOST algorithms
As of EJBCA 8.3, support for the DSTU and GOST algorithms is deprecated and will be removed in the next release.
Removal of DSA algorithm
Support for the DSA algorithm has been removed in EJBCA 8.3, following its deprecation in EJBCA 8.2. Users of this algorithm must migrate to other algorithms.
Note that if you have used ConfigDump in earlier versions to export Certificate Profiles with all key algorithms selected (per default behavior), you must remove DSA from the list before importing the profiles into EJBCA 8.3.
Removal of Configuration Checker
The experimental user interface tool Configuration Checker is removed in EJBCA 8.3, since support and development have been dropped.
Removal of ca.keystorepass property from cesecore.properties
The ca.keystorepass property, declared in cesecore.properties, and its associated functionality has been removed. The property enabled the setting of a default keystore password for soft crypto tokens, and only when created from the CLI. Besides being of questionable functionality, its use would at best be considered poor security practice and has thus been removed.
Upgrade Information
Review the EJBCA 8.3 Upgrade Notes for important information about this release. For upgrade instructions and information on upgrade paths, see Upgrading EJBCA.
Change Log: Resolved Issues
The following lists implemented features and fixed issues in EJBCA 8.3.1 and EJBCA 8.3.0. (EJBCA 8.3.0 was an internal release, not available for customers).
Issues Resolved in 8.3.1
Released May 2024
Bug Fixes
ECA-12422 - External RA Cannot Query Peered CA Certificate Profiles
ECA-12428 - Upgrade JDBC drivers used by EJBCA containers
Issues Resolved in 8.3.0
Released May 2024
New Features
ECA-10867 - Make the nextUpdateHours element configurable in the GetPolicesResponse
ECA-11319 - Add REST API endpoint for key recovery
ECA-11559 - Autoenrollment: Support "Supply in the request" enrollment
ECA-11623 - Recreate the menu as Primefaces and changing to a top-menu
ECA-11859 - Add support for being able to restrict keys/algorithms in the certificate profile for alternative signatures.
ECA-11931 - Add ConfigDump support for the hybrid settings for the CA
ECA-11932 - Add ConfigDump support for the hybrid settings for Certificate Profiles
ECA-1Z1997 - REST add ability to add end endtity with key recovery enabled
ECA-12024 - Allow enrollment of Hybrid CSRs through UI.
ECA-12091 - RA mode support for EST over CoAPs
ECA-12104 - Review only: P11NG Cli command to list keypairs in the same way as EJBCA does
ECA-12107 - Server Name Indicator support in Coap-proxy
ECA-12138 - Use SCEP alias name for defaultCA if CA is not specified in request
ECA-12206 - Support alternative signature in ExtendedInformation and in KeyStoreCreateSessionBean
ECA-12339 - SBOM for EJBCA Container Set
Improvements
ECA-10214 - Extend REST /v1/ca results to include external CAs
ECA-10671 - Allow setting OCSP settings in the UI and CLI that can only be set in the ocsp.properties when using pre-signed proofs
ECA-10949 - Move MSAE Config to the CA
ECA-11606 - Add ability to test encrypt/decrypt-only keys on a crypto token
ECA-11750 - Add CryptoToken Key Usage to ConfigDump
ECA-11798 - Improve handling of HSM connection timeouts
ECA-11889 - Load CKAs, such as public key value and key usage, more efficiently from PKCS11 HSMs when listing keys
ECA-11941 - Enable validity start and end dates in the past
ECA-11985 - Adapt to stricter SubjectDN checks in IETFUtils.rDNsFromString
ECA-11996 - Add API in Crypto Token and P11NG to read key usage
ECA-12008 - Cleanup: Fix warnings introduced from x509-common-util
ECA-12009 - Change AcmeReplayNonceFilter to ContainerResponseFilter
ECA-12010 - Update documentation related to LW CMP Profile
ECA-12015 - Add time limit of certificate archival during CRL generation
ECA-12016 - ejbca.sh importcacert should include full CA chain
ECA-12017 - Add republish button per item in Publisher Queue
ECA-12019 - Include "id-etsi-ext-valassured-ST-certs" extension in the Certificate Profile
ECA-12023 - Use CKA_KEY_TYPE for P11 key algorithm, by upgrading p11ng, and use publicKey to get correct algorithm for CMS
ECA-12031 - Remove support for DSA
ECA-12035 - Add a prohibition to create a non-hybrid CA under a hybrid root, and vice versa.
ECA-12036 - Updated readme and security policy, add Issue templates
ECA-12037 - Include ECDSA hashing mechanisms in the Legacy Java PKCS#11 providers disabledMechanisms
ECA-12042 - CoAP proxy updates to support Software Appliance multi-NIC capabilities
ECA-12053 - RA Web Edit End Entity pressing enter selects Revoke And Delete, reorder so that is not the default
ECA-12062 - Add wildcard unit tests to DomainBlacklistBaseDomainCheckerTest
ECA-12063 - Change the default value of httpsserver.tokentype property to P12
ECA-12070 - Add OAuth (optional) support for userinfo
ECA-12073 - Reduce overhead for listing keys with P11NG Crypto token
ECA-12076 - Cleanup: Remove OcspKeyRenewalSession
ECA-12087 - Update language files, from David Carella
ECA-12088 - Remove jndi.properties.glassfish and jndi.properties.jbosseap6
ECA-12090 - Modify CreateCsrCommand to not require an SDN
ECA-12094 - Change behavior of Pre-Certificate Revocation Service
ECA-12106 - L10n: Localize Message Use entity CN (for SAN/dNSName extension) in Admin UI
ECA-12108 - Improve GUI info when testing key pair
ECA-12115 - Add support for maxWorkerJobs in configdump of publish queue service
ECA-12117 - Create multi-stage Dockerfile
ECA-12134 - Correct MSAE SPN format help in Admin UI
ECA-12156 - Minor language updates for Peer systems
ECA-12163 - Allow EJBCA container to import JSON via configdump
ECA-12174 - Clean up code after implementation of issuance/revocation prompted ocsp response pre-production
ECA-12182 - Upgrade MailAttachment to not use > JDK17 classes
ECA-12213 - SCEP GetCACaps returns error in SCEP CA mode when no CA is passed in message
ECA-12225 - L10n: French GUI language fixes
ECA-12226 - L10n: RA GUI Missing keys and fixes (ICAO, OAuth, etc.)
ECA-12228 - Minor code cleanup
ECA-12230 - Refactor "Add End Entity" page
ECA-12241 - Introduce granular search criteria in REST API
ECA-12254 - Remove ConfigurationChecker
ECA-12257 - RA GUI Make New Request page improvements
ECA-12266 - Remove all localizations used in crypto tokens
ECA-12268 - Review only: Ability to issue Link Certificate using previous signature algorithm when changed
ECA-12271 - Remove Services related localizations
ECA-12293 - Review: admin-gui: Adding more id= attributes to the new menu
ECA-12301 - Upgrade Apache CXF to 4.0.4
ECA-12316 - Introduce 'begins with' search operation in REST API
ECA-12322 - MSAE Intermediate CAs with same DN causes issues with LDAPS
ECA-12325 - Allow ejbca.sh change slot PINs w/o providing the previous PIN
ECA-12330 - Drop ca.keystorepass and ca.cmskeystorepass
ECA-12337 - Update p11ng to support Ed448 on Utimaco
ECA-12364 - Upgrade EJBCA to BC 1.78
ECA-12367 - Admin and RA UI language improvements from David Carella
ECA-12382 - Show alternative signing algorithm when enrolling via CSR in RA GUI
ECA-12384 - Fix documentation error in step-by-step instruction for ra web make new request with CSR
ECA-12387 - Warning removal: Add missing serialVersionUID
ECA-12388 - Warning cleanup: Update references to org.junit.rules.Timeout
ECA-12389 - Warning cleanup: Update references to org.junit.Assert.assertThat
ECA-12397 - Add list/table of deprecated and dropped features to the documentation
ECA-12400 - Upgrade to Nimbus-Jose to 9.37.3
ECA-12414 - Localization - French translation for RA web
Bug Fixes
ECA-11548 - Unable to only create deltacrl in REST
ECA-11626 - Enrollment code (minimum bit length) by pass
ECA-11962 - Fix InternalKeyBinding rekeying when keyspec is an OID
ECA-11969 - ejbca-db-cli verify broken - P11ng ClassNotFoundException
ECA-11970 - User can add Crypto Token with just spaces
ECA-11988 - RA Search engine keeps old incorrect results
ECA-11989 - RA Misleading message when no criteria selected.
ECA-11991 - CE cannot be compiled due to MSAE classes
ECA-11994 - Fix session timeout issue when edit ca
ECA-11995 - URI Name Constraints Not Accepting Multiple Subdomains
ECA-12006 - SCP Publisher doesn't validate empty URL fields
ECA-12011 - custom_data in REST v1/endentity requires extension_data set as well
ECA-12013 - Typo when SCEP_CLIENT_CERTIFICATE_RENEWAL_CLASSNAME can not be instansiated
ECA-12014 - CompressedCollection fails in some environments during CRL generation. Remove it
ECA-12025 - Notification Timeout Not Returning Generated Certificate
ECA-12026 - Missing OCSP transaction log entries
ECA-12040 - /v1/certificate/expire does not return certificates if maxNumberOfResults is not mentioned
ECA-12045 - Ensure all CA certificates are loaded into CaCertificateCache
ECA-12049 - EJBCA appears to leave PKCS#11 sessions around (CKR_SESSION_COUNT error)
ECA-12050 - CMP NestedMessageContent reading RA certs directory should ignore subdirectories
ECA-12051 - ant runweb misspells ocsp for included test
ECA-12057 - Ldap timeouts not saved properly in MSAE autoenrollment alias
ECA-12059 - CmpRevokeResponseMessage may be created with incorrect Sender in header in some cases
ECA-12060 - Sign CMPv2 responses with CA sigAlg when request uses HMAC - refactoring
ECA-12071 - Regression: rest api v2 certificate search broken in 8.2 when performing count
ECA-12077 - CMP Aliases in RA Mode doesn't survive upgrade to 8.2
ECA-12083 - Enroll with username/requestId incorrectly validations CSR fields
ECA-12085 - ejbca.cmd file does not work
ECA-12093 - Private keys without CKA_ID keys on an HSM gives NoSuchMethodError: 'boolean org.apache.log4j.Logger.isWarnEnabled()'
ECA-12105 - Regression: NPE in Admin UI when crypto token contains DSA key
ECA-12110 - OCSP Issuer URLs not showing on configdump export
ECA-12116 - Regression: ConfigDump fails with p11 error
ECA-12120 - Potential NPE when creating SSH CA, optimize usage of extgen.generate
ECA-12126 - SubCAs not provisioned with hybrid key
ECA-12129 - Unable to restart container when Security parameters are set
ECA-12130 - Regression: Community admin web for CMP aliases misses the 'Add' button
ECA-12131 - Username should come from changed DN in EST RA Vendor mode with Allow ChangeSubjectName enabled
ECA-12135 - Add back favicon to Admin UI Add End-Entity page
ECA-12137 - Error with focus and duplication in RA GU subject directory attributes
ECA-12139 - Review only: HealthCheckServlet query parameters dont work under load
ECA-12145 - Containerized installation issues - Public Access Member is not removed
ECA-12170 - Possible NPE in CAInterfaceBean
ECA-12172 - Compliance issue
ECA-12189 - Fortanix HSM Failures after idling without HSM activity
ECA-12196 - REST API Key Recovery endpoint doesn't work over Peers
ECA-12197 - Regression: DeltaCRLException trying to renew a CA
ECA-12204 - Regression: Un-revokation does not work when an invalidityDate is used
ECA-12215 - Regression: Community admin web for SCEP aliases - cannot delete alias
ECA-12223 - Regression: Order of Name and Id changed in WS API NameAndId object
ECA-12224 - Regression: Error revoking certificate when invalidityDate is null - Row was updated or deleted by another transaction
ECA-12227 - Merge DN function when merging SANs is case sensitive
ECA-12231 - Increase metaspace size
ECA-12233 - RaEndEntitySearchPaginationSummary does not implement Serializable
ECA-12238 - Speed up certificate search query
ECA-12246 - Regression: Order of ResponseType and Data changed in WS API CertificateRequestResponse object
ECA-12249 - Enroll EC certificate using MSAE protocol
ECA-12251 - Add new hard coded PQC key(s) for pre-signing validation
ECA-12253 - CRL store servlet shows CRL download links even if CRL is not present.
ECA-12255 - Log Redaction is not always performed in publishers
ECA-12256 - Ed25519 CSR in RA UI fails with NPE on Java 17
ECA-12264 - Regression: CertificateSamplerCustomPublisher can not be created
ECA-12278 - Incorrect alter table SQL for MS-SQL in post-upgrade scripts
ECA-12291 - Configdump export for Roles considers only internal CAs
ECA-12306 - Fix stack overflow while storing Validation Authority Publisher
ECA-12312 - Remove duplicates in RA Web field 'Key Algorithms'
ECA-12313 - Not possible to change key type or size when reissuing a certificate.
ECA-12335 - PKCS#12 files from key recovery through the WS API uses legacy certificate bag algorithm
ECA-12338 - Admin Web - Rename approval profile - error message to be improved
ECA-12375 - Handle AWS KMS disconnects without errors
ECA-12386 - Fix YamlWriterUnitTest
ECA-12391 - Fix usage of imagePullSecrets in EJBCA Helm Chart
ECA-12392 - Missing 'VA Functions' menu in VA builds
ECA-12393 - Security issue
ECA-12396 - CLI - gencsr - Could not create key: Key Algorithm DILITHIUM5 was unknown
ECA-12399 - RA Web CSR enrollment with Dilithium as primary algorithm only works when all EC curves allowed
.png)