Configuration
The following describes how to integrate the EJBCA AWS instance with the AWS Key Management Service (KMS) and create keys in AWS KMS for use with an EJBCA CA.
AWS User Creation
To create a user that can access the KMS from the EJBCA host, do the following:
- Sign in to the AWS console, select the Services drop-down and search for "IAM".
- Select Users and then Add User.
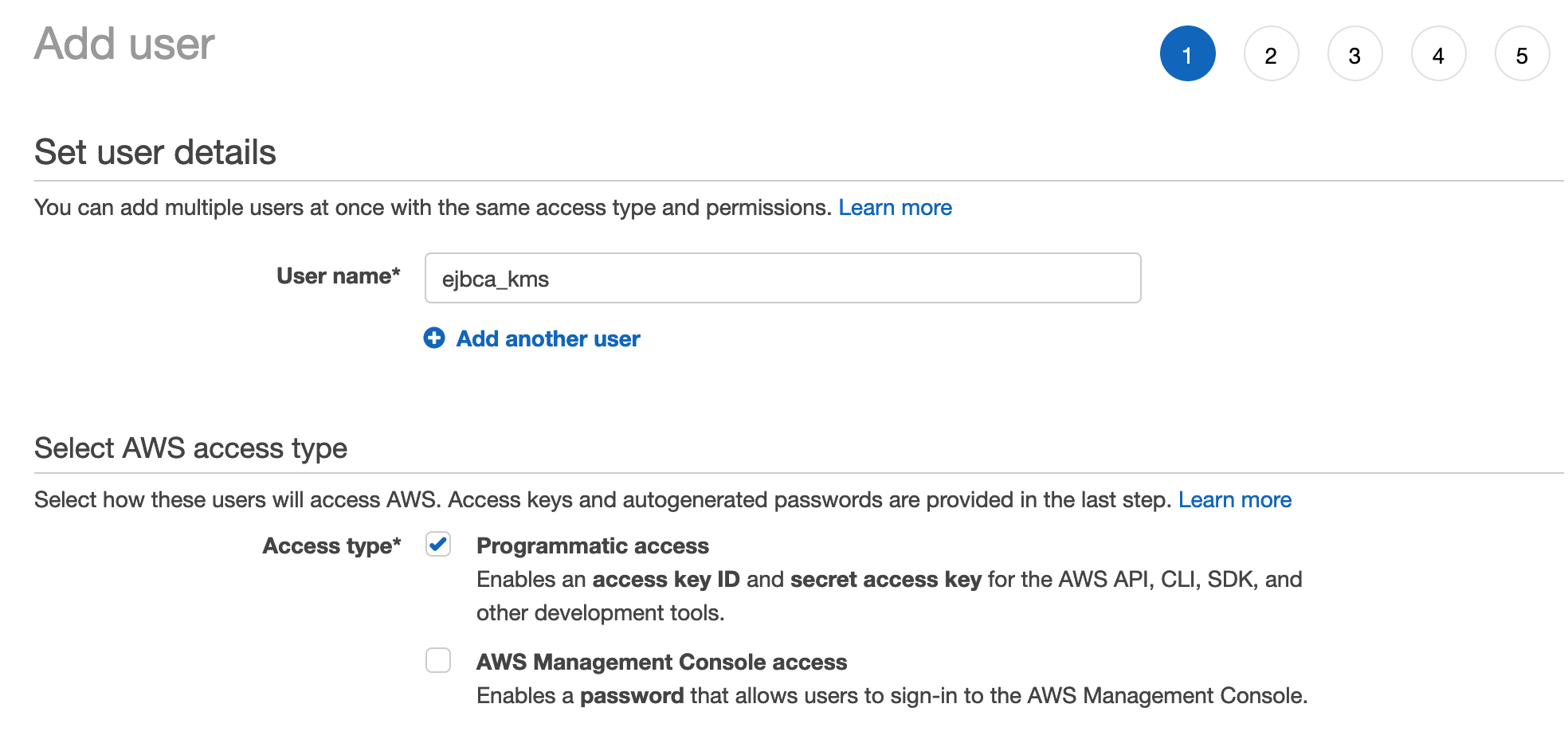
- Specify the following to add a user:
- Add a user with the name of "ejbca_kms" or any name you choose that describes the usage.
- Select Programatic access to allow the user to access the KMS API, but not log into the AWS console.
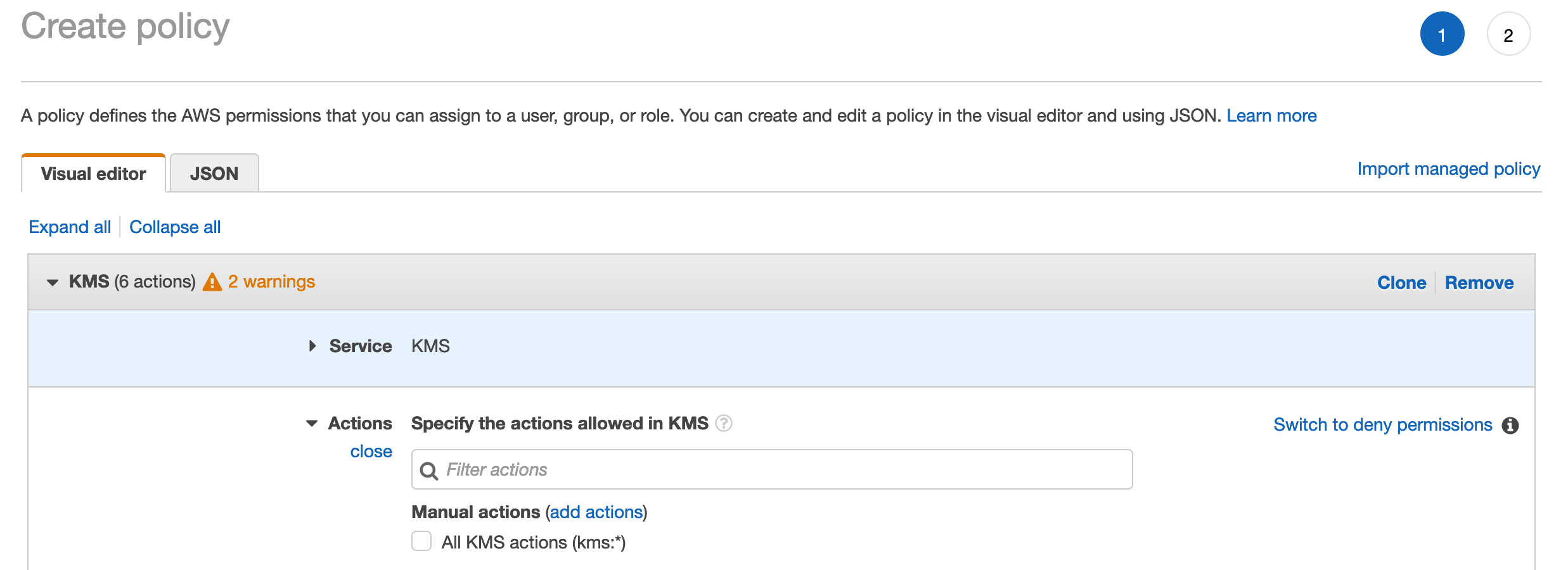
- Select Attach existing policies directly under Set permissions and then click Create policy.
- In the opened browser tab Create policy, search for KMS in the product search field and select KMS.
- Select the following permissions from the Access level selection:
- List
- ListAliases
- Read
- GetPublicKey
- Write
- CreateAlias
- CreateKey
- ScheduleKeyDeletion
- Sign
- List
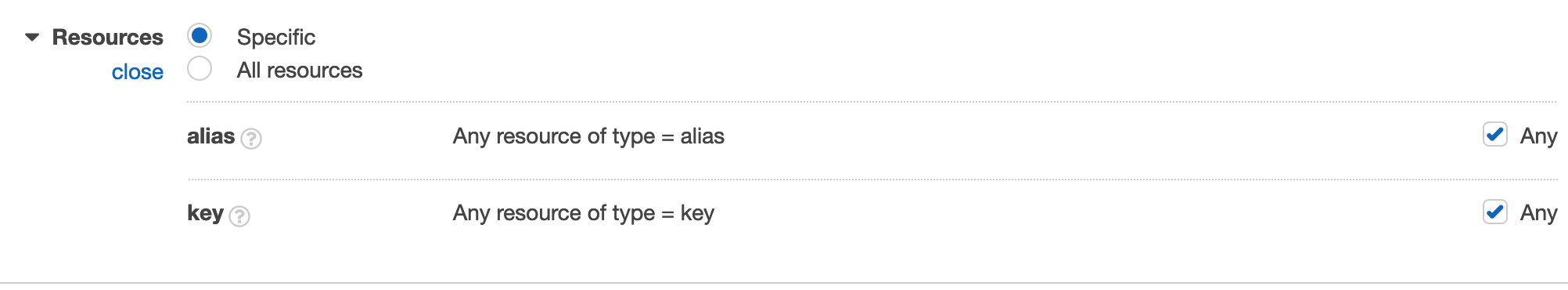
- Under Resources, select Any for both alias and key resources.
- Click Review policy.
- In the Create policy screen, specify a Name and Description for the policy and click Create policy.
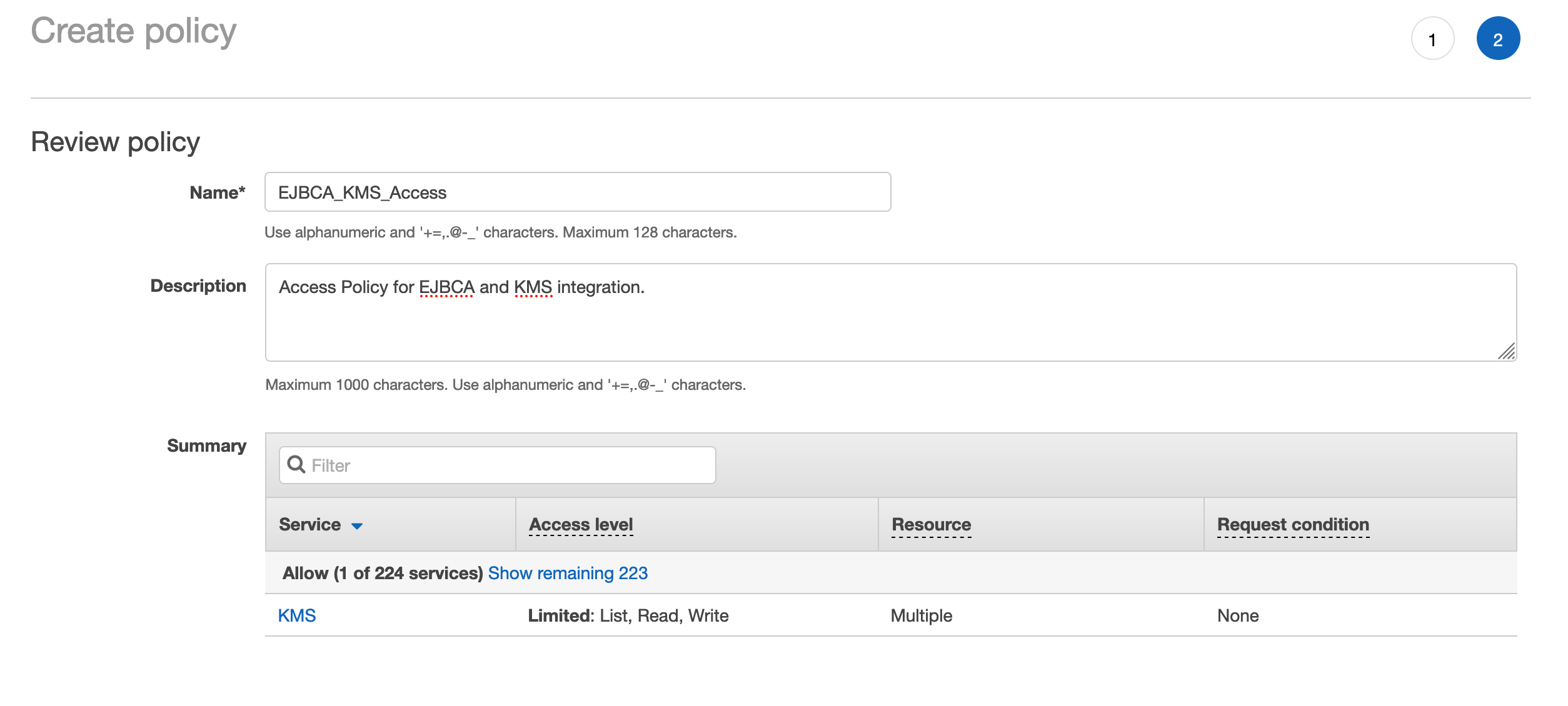
- A confirmation message confirms the successful creation of the policy.
- Go back to the Add user tab and click the refresh button.
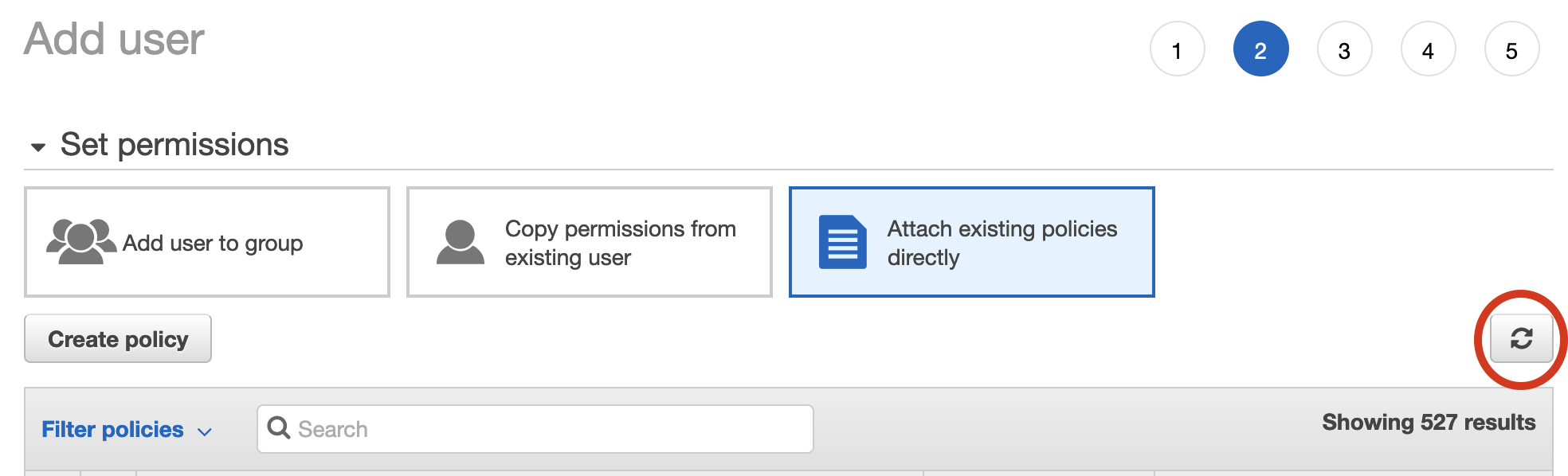
- Search for the policy created above and select it.
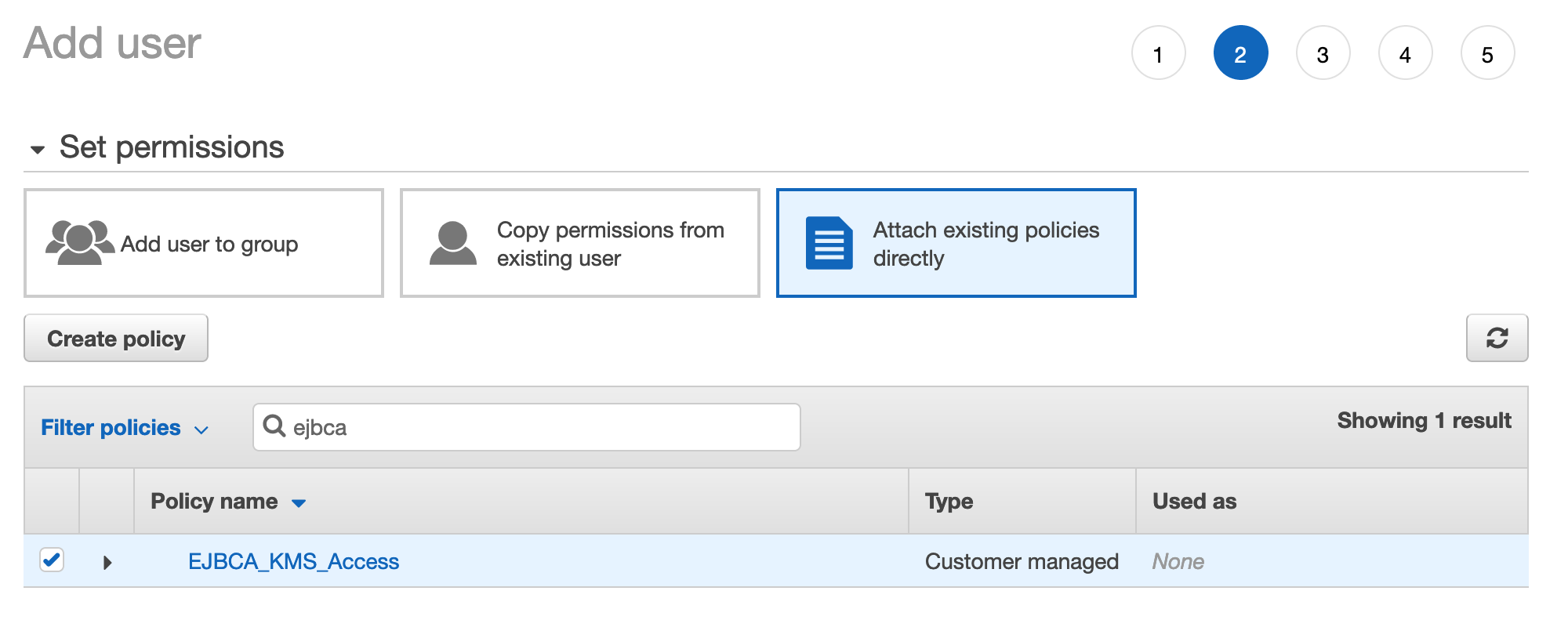
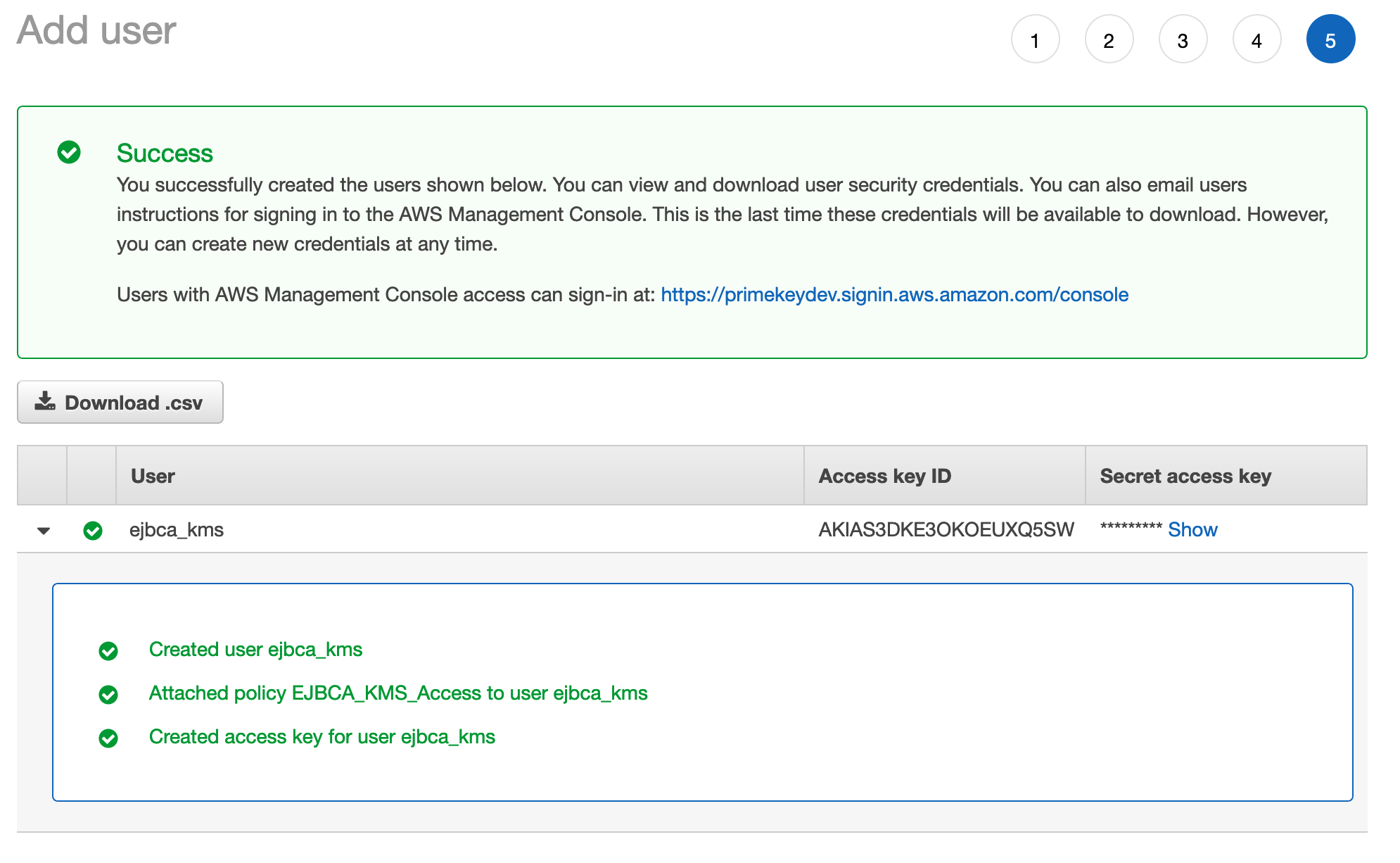
- Click Next to add tags if desired through step 5 to Create user. A successful creation message displays the Access key ID and the Shared access key. Note these credentials down or download the .csv file with the credentials since the Access key ID and the Shared access key will later be used in the EJBCA Crypto Token to access the KMS.
EJBCA Configuration
Note that the following configuration is supported as of EJBCA 7.4.0.
To configure EJBCA, do the following:
- Edit the /opt/ejbca/conf/web.properties file and uncomment the following property (on EJBCA Enterprise Cloud from the AWS Marketplace this is done for you):BASH
awskms.cryptotoken.enabled=true - If you are running EJBCA Enterprise software, redeploy.BASH
ant clean deployear - Click Create new in the EJBCA Crypto Token screen and select AWS KMS as the Type.
- Enter the credentials for the user, including the region the KMS resides in, and use the following attributes:
- Authentication code: IAM Users Secret access key
- Region: The region the KMS keys will reside
- Access KeyID: IAM users Access key ID
- Enable Auto-activation to allow the Crypto Token to activate on system restart (for an issuing CA for example).
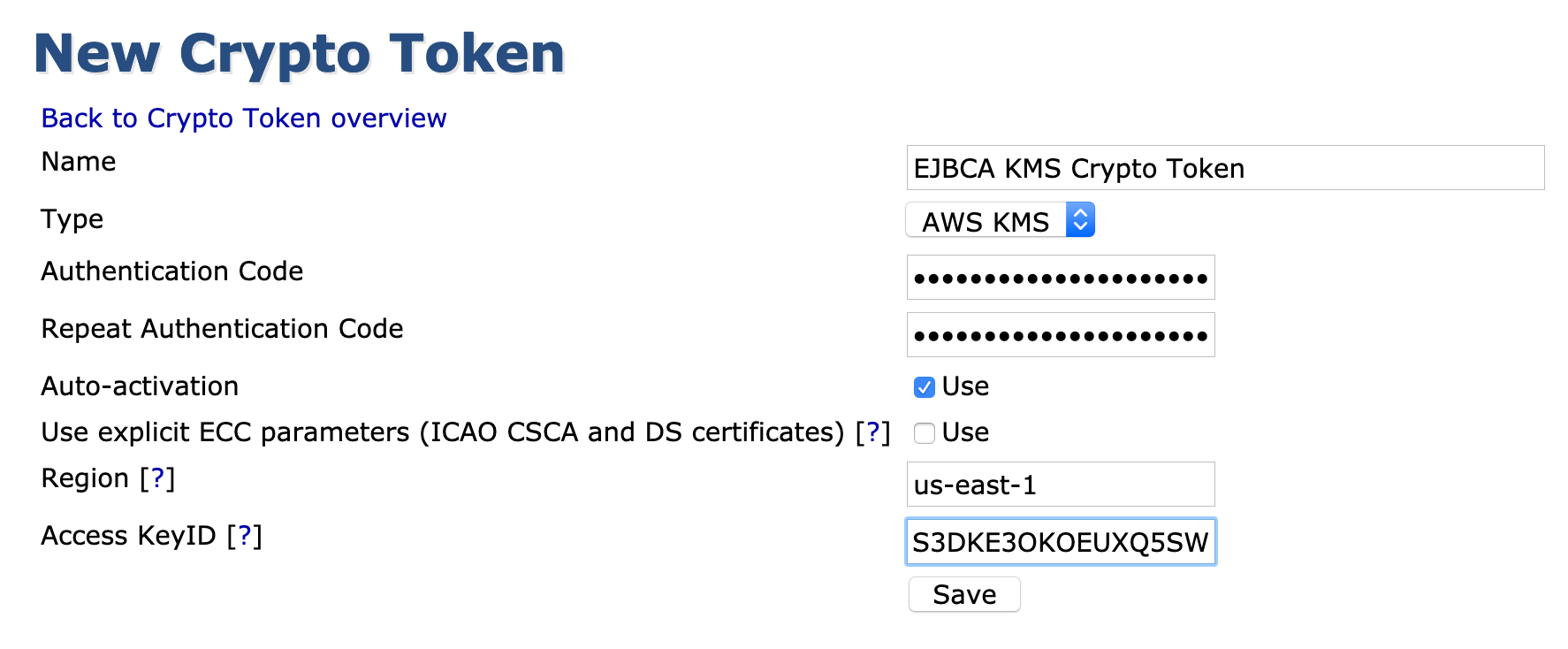
- When it successfully connects to the KMS, the notification Crypto Token created successfully is displayed at the top of the page.
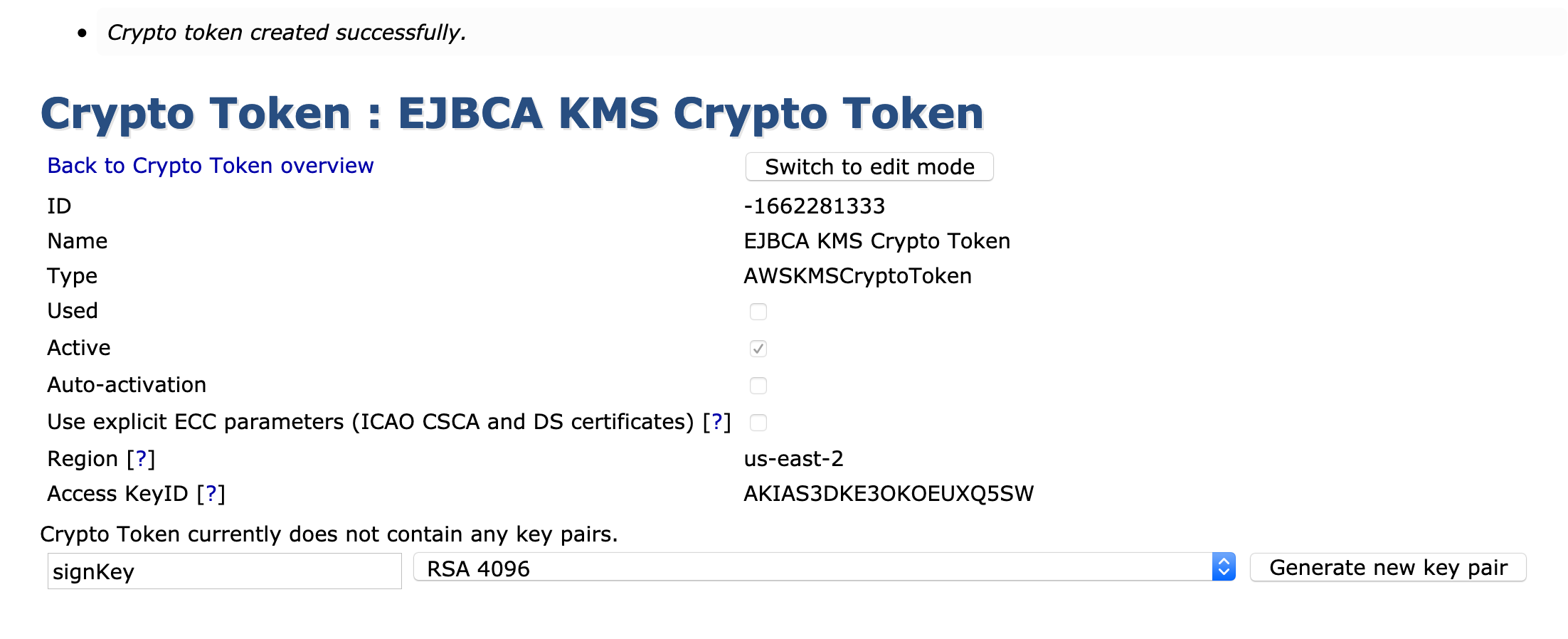
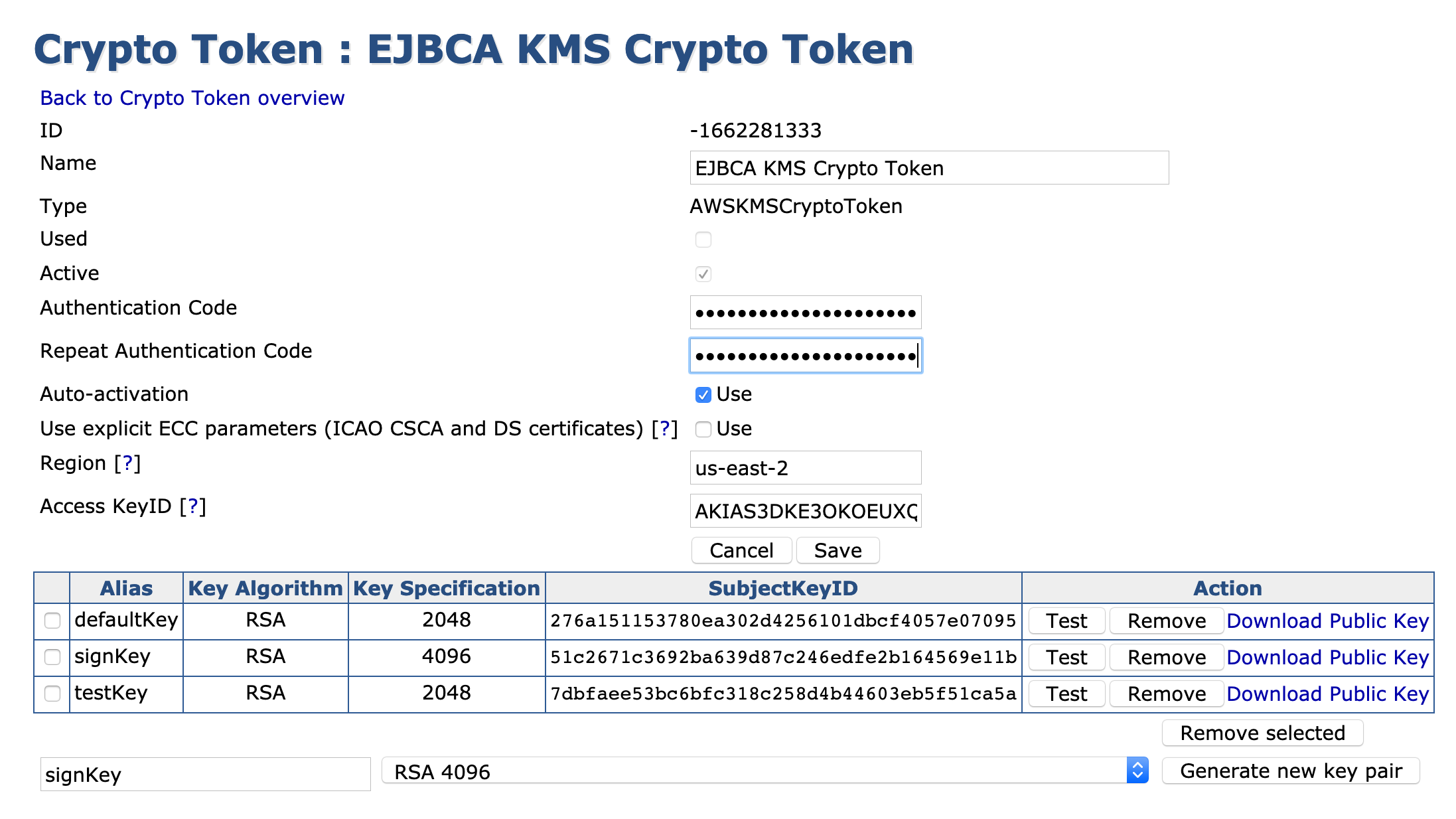
- Generate the following keys for an EJBCA CA:
- defaultKey
- signKey
- testKey
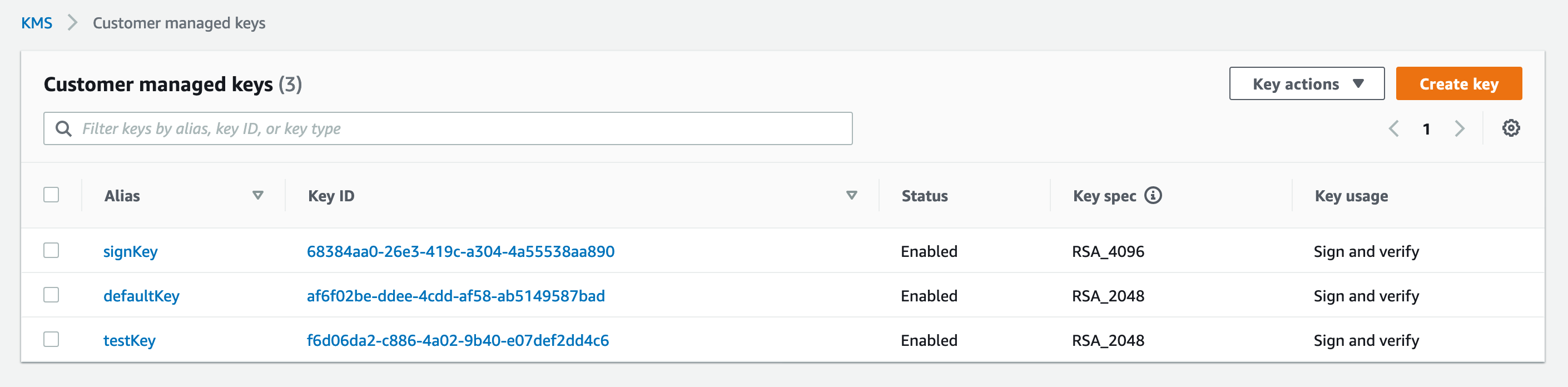
- Go to the KMS console and confirm that the keys created in EJBCA are listed.
.png)