Creating an App Registration in Active Directory
The following shows you how to add and register an application using App registrations in the Azure portal and then how to generate a secret (password), needed when obtaining tokens.
Registering the App in Active Directory and Generating Secret
- Login and access your Azure portal at https://portal.azure.com.
- Select the Azure Active Directory service in the left-hand navigation pane, and then select App registrations > New registration.
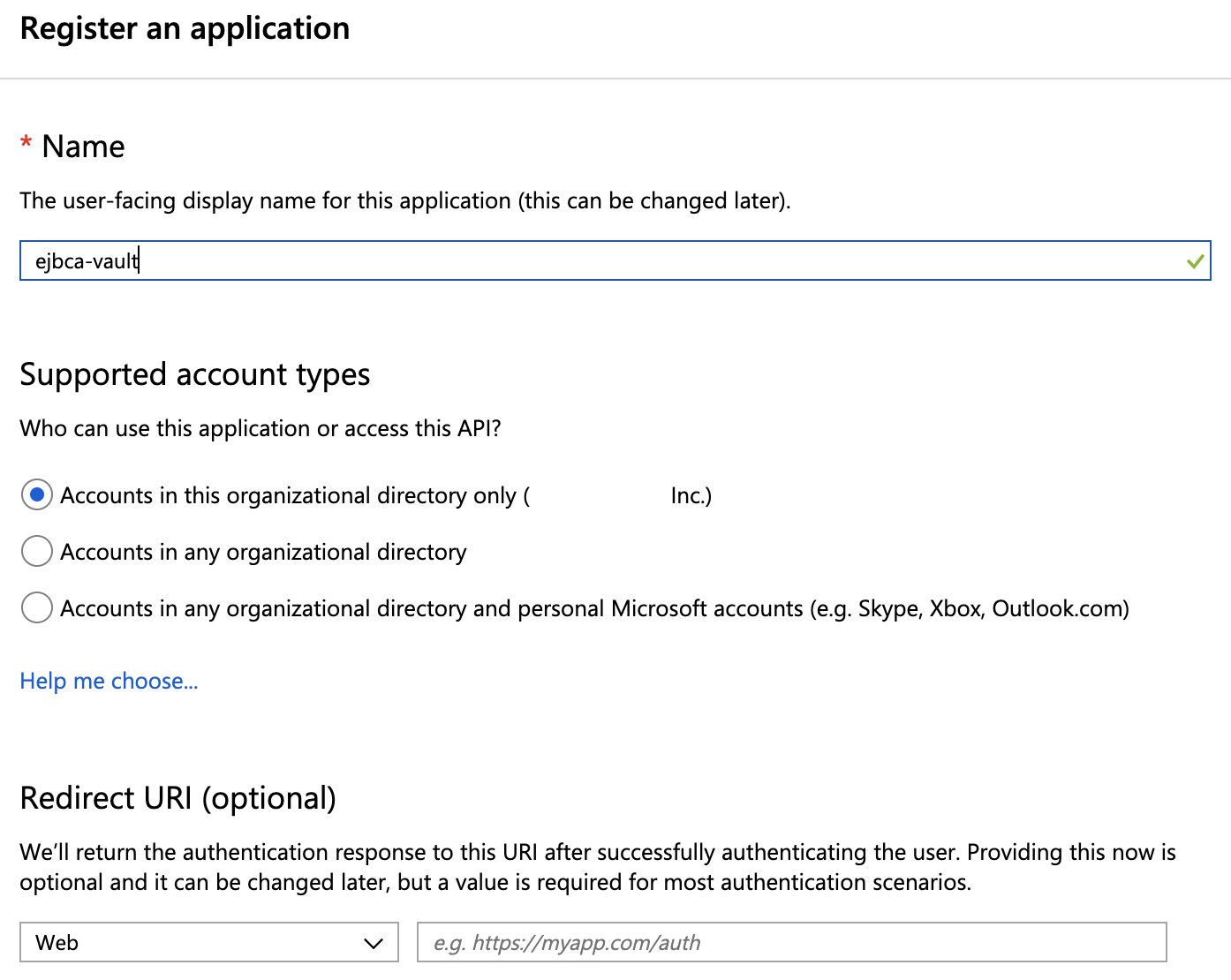
Specify an app name (that will be displayed to users of the app), for example "ejbca-vault", and then click Register.
Azure AD assigns a unique application (client) ID to your app and displays your application's Overview page.- On the Overview page, make a note of the Application (client) ID. This value will be required in EJBCA when creating a Crypto Token.

- Click Certificates & secrets to add a secret (password).
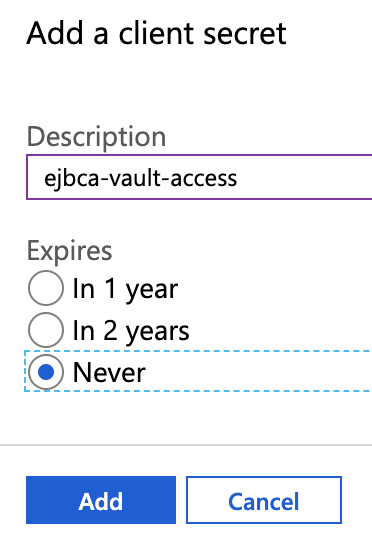
- Click New client secret in the Client secrets section.
- Enter a name for the secret, such as "ejbca-vault-access". Set the expiration if desired. In this example, the expiration is set to Never expire to allow the CA to always have access to the keys in the HSM. Click Add once done.
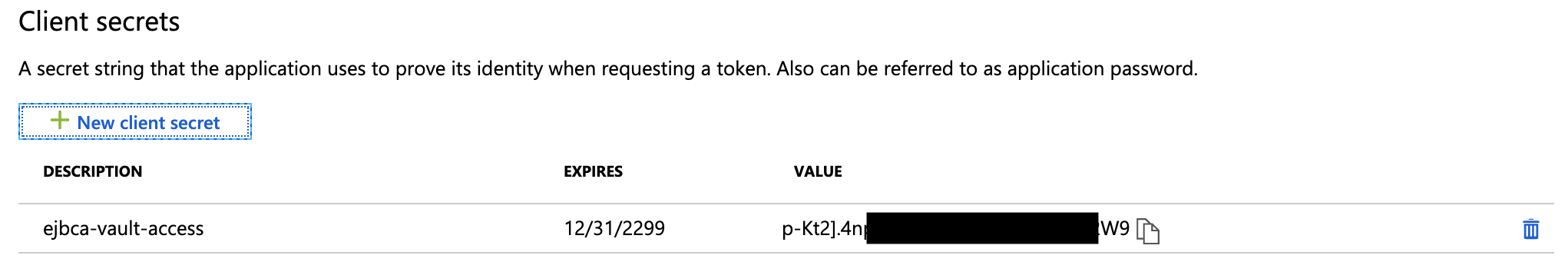
- A secret is generated and displayed. Note this secret down in a password manager such as Last Pass as it will only be displayed once in the portal. The secret will also be required in EJBCA when creating a Crypto Token in the later step Creating an Azure Key Vault Crypto Token in EJBCA.
Next, continue with Creating the Azure Key Vault.
.png)