Configure EJBCA for NXP EdgeLock 2GO Service Platform
NXP offers a wide range of Roots-of-Trust, including MCUs and secure elements, capable to handle x.509 certificates. Recognizing the complexities involved in factory provisioning of an Initial Device Certificate, NXP has has introduced a specialized service portal EdgeLock 2GO, dedicated to the definition, generation and over-the-air provisioning and management of secrets and x.509 certificates into their Roots-of-Trust.
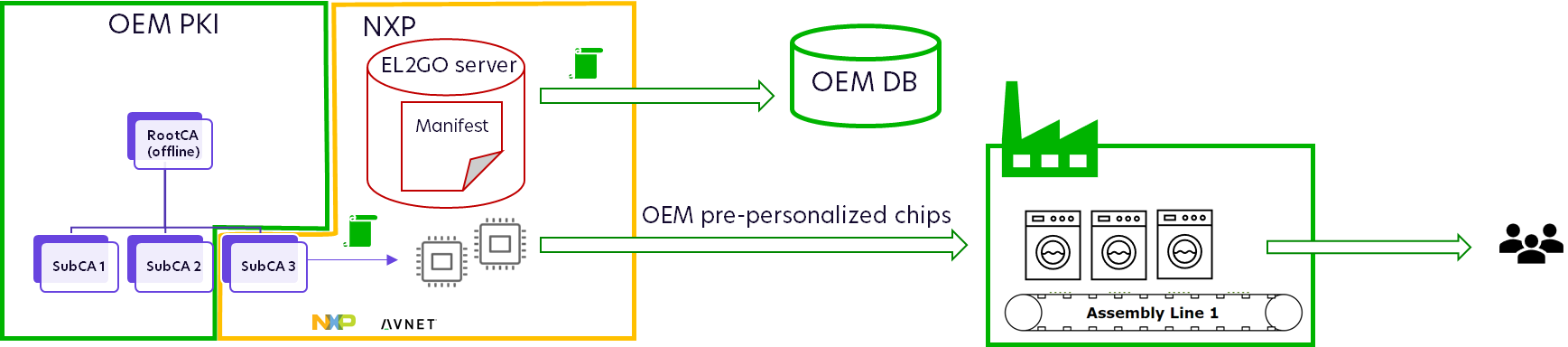
For instance, an original equipment manufacturer (OEM) can use the EdgeLock 2GO service to order secure elements which will be pre-provisioned with their certificates by an NXP factory or a distributor such as Avnet before shipment to the CEM. A Service Provider can use the portal to dynamically admin secrets and operational certs into devices with an NXP Root-of-Trust, provided that the embedded FW of the device runs adequate code.
But what if a customer wishes to utilize this service while still preferring certificates to originate from their own Public Key Infrastructure (PKI)? For practical reasons, the Intermediate Certificate Authority (ICA) generating the certificates must reside in the NXP infrastructure, but nothing prevents CAs above this ICA to live outside of NXP, which allows a customer to own most of his chain of trust whereas only delegating the lower level ICA to NXP when using their provisioning service. This allows customers to maintain ownership of most of their chain of trust while delegating only the lower-level Intermediate CA to NXP when utilizing their provisioning service.
This tutorial explains how to achieve such a setup with EJBCA:
PKI Structure
The objective of the setup is to enable attaching the NXP factory ICA certificates to your wider public key infrastructure (PKI), while not changing the way NXP issues device certificates and programs them into your Root-of-Trust.
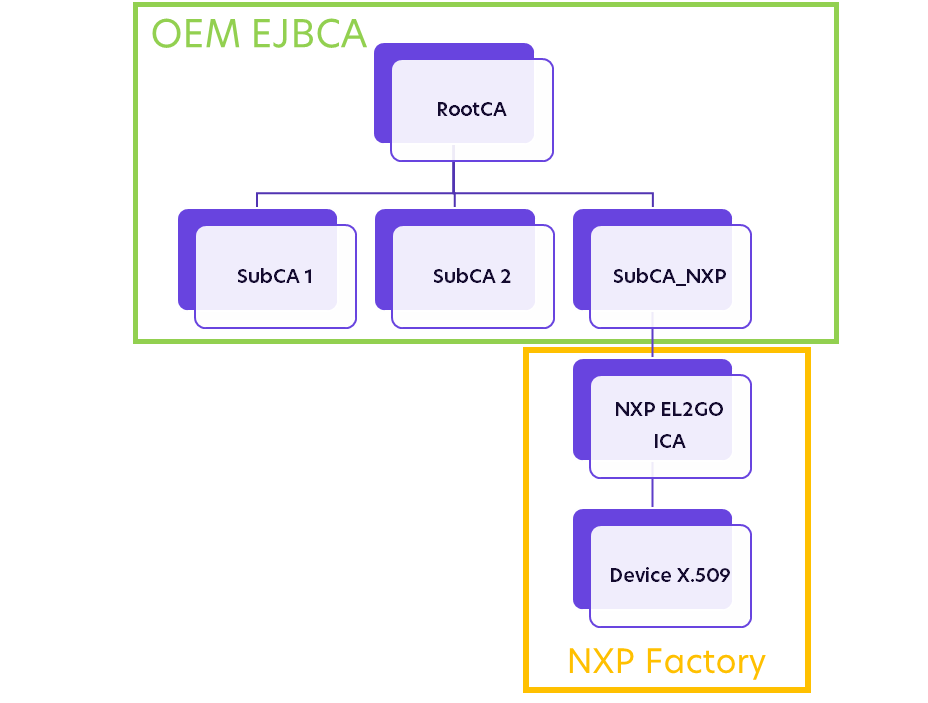
The example shows the EJBCA setup with a self-signed Root CA and a Sub CA NXP (SubCA_NXP) issuing the NXP EdgeLock 2GO ICA certificate. The ICA certificate will in turn produce the high number of device certificates that NXP injects into the secure elements to be shipped to your assembly line.
Configure EJBCA
The following sections cover the steps needed to configure EJBCA.
Step 1 - Create Crypto Tokens
Create tokens for the various certificates and label them explicitly.
In EJBCA, cryptographic keys are stored in a crypto token. For more information on crypto tokens and available fields, see the Crypto Tokens Overview. To learn how to create crypto tokens in EJBCA, you can follow the tutorial Create a PKI Hierarchy in EJBCA.
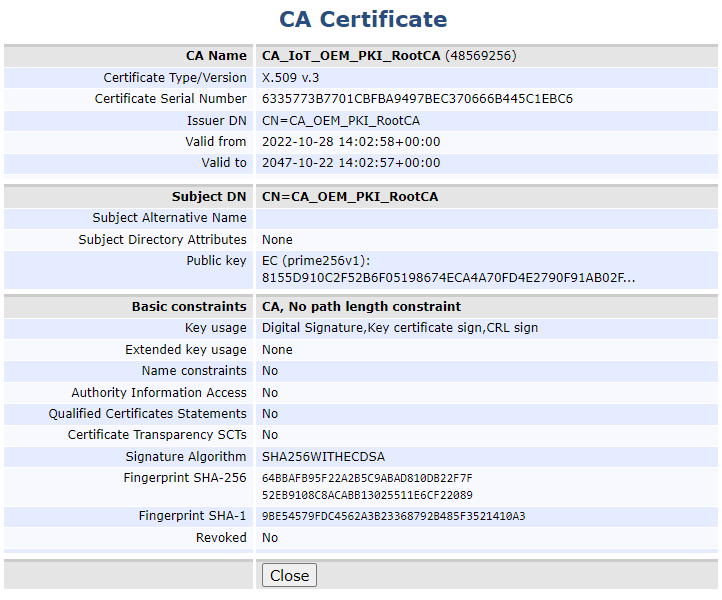
Step 2 - Create Root CA
Next, create a Root CA in EJBCA. To learn how to set up a Root CA in EJBCA, you can follow the tutorial Create your first Root CA using EJBCA.
To complete the steps in this guide for configuring EJBCA for NXP EdgeLock 2GO, it is mandatory to select the following:
Type: Root CA.
Available Key Algorithms: ECDSA or DSA.
Available curves: NIST ECC P-256 / P-384 / P-521 or RSA 2048 / 4096.
Signature Algorithm: SHA256withECDSA, SHA384withECDSA, SHA512withECDSA, SHA256withRSA, SHA384withRSA, SHA512withRSA.
Key Usage: Key certificate sign, at a minimum.
Step 3 - Create Sub CA
Next, create a Subordinate CA (Sub CA) in EJBCA. To learn how to set up a Sub CA in EJBCA, you can follow the steps in the tutorial Create a PKI Hierarchy in EJBCA.
The Sub CA NXP (SubCA_NXP) certificate will be used to sign the certificate signing requests (CSRs) that will be provided by the NXP EdgeLock 2GO portal. To comply with NXP EdgeLock 2GO, it is mandatory to specify the following:
Type: Sub CA.
Available Key Algorithms: ECDSA or DSA.
Available curves: NIST ECC P-256 / P-384 / P-521 or RSA 2048 / 4096.
Signature Algorithm: SHA256withECDSA, SHA384withECDSA, SHA512withECDSA, SHA256withRSA, SHA384withRSA, SHA512withRSA.
Key Usage: Key certificate sign, at a minimum.
Step 4 - Create End Entity
The ICA certificate needs to be generated for the NXP factory. The certificate signing requests (CSRs) will be provided by NXP EdgeLock 2GO and EJBCA then signs it with the Sub CA (SubCA_NXP) in this example.
In EJBCA, this can be accomplished by creating an End Entity for each CSR to sign (and ICA to issue). An End Entity relies on an End Entity Profile and in order for the End Entity to issue the ICA certificate according to NXP’s requirements, a specific Certificate Profile needs to be created.
Create Certificate Profile
The certificate profile defines the constraints of new certificates, for example, what keys it can use, and what the extensions will be. For an introduction to certificate profiles, see the Certificate Profiles Overview and for information on available Certificate Profiles Fields, see Certificate Profile Fields.
To create a certificate profile, follow these steps:
In EJBCA, under CA Functions, click Certificate Profiles.
Click Clone next to the SUBCA template to use that as a basis for creating your new profile.
Name the new certificate profile and click Create from template.
To edit the profile values to fit your needs, find the newly created profile in the list and click Edit.
On the Edit page, verify that the type is End Entity and update the following:
For Available Key Algorithms, select ECDSA or RSA.
For Available ECDSA curves, select P-256, P-384, P-521
For Signature Algorithm, select SHA256withECDSA, SHA384withECDSA, SHA512withECDSA, SHA256withRSA, SHA384withRSA or SHA512withRSA.
Enable Allow Validity Override.
Enable Allow certificate serial number override.
Enable Allow Subject DN Override by CSR.
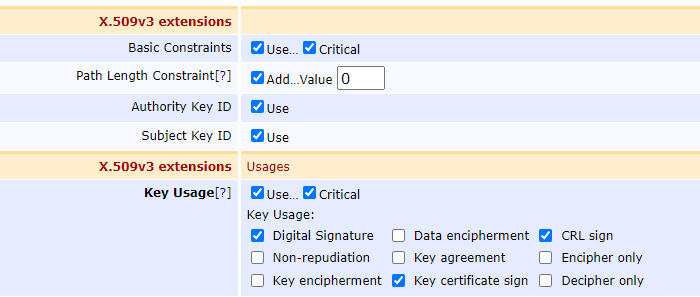
For Key Usage, select Critical, Digital Signature, CRL Sign, Key certificate sign.
X.509v3 extensions, None.
For Available CAs, select your Sub CA SubCA_NXP.
Click Save to store the certificate profile.
The newly created profile is displayed in the list of certificate profiles.
Create End Entity Profile
To create an end entity profile, follow these steps:
In EJBCA, under RA Functions, click End Entity Profiles.
In the Add Profile field, add a name for the new profile, and click Add profile.
Select the newly created profile and click Edit End Entity Profile to update the profile.
Edit the profile and update the following:
For Username, select Auto-generated.
For Password (or Enrollment Code): Specify a password.
For CN, Common name, verify that Required and Modifiable are selected.
Main Certificate Data allows you to map the profile to be used together with default certificate profiles and CAs:
For Default Certificate Profile, select the profile created in Create certificate profile.
For Available CAs, select your NXP SubCA created in Create Sub CA.
Specify Default Token options to define how the key pair generation should be implemented for the certificates:
For Available Tokens, select User Generated. User Generated means that the requester generates their own key pair and thus creates and provides a certificate signing request (CSR) for the certificate request to EJBCA.
Enable Custom certificate serial number.
For Certificate Validity Start Time, select Use.
For Certificate Validity End Time, select Use.
Click Save to store the end entity profile.
The newly created profile is displayed in the list.
Create End Entity
Next, a new end entity can be created based on the end entity profile. To learn how to add end entities in EJBCA, you can follow the steps in the Tutorial - Issue Matter IoT-compliant certificates with EJBCA.
To create an end entity, follow these steps:
In EJBCA, under RA Functions, click Add End Entity and specify the following:
In End Entity Profile, verify that the profile created in Create End Entity Profile is selected and update other settings as required.
To add the end entity, click Add.
The end entity is added.
NXP EdgeLock 2GO Configuration
For step-by-step instructions on how to set up your EdgeLock 2GO account and configure your secure objects, please follow NXP’s application note AN12691.
Step 5 - Create Intermediate CA on EdgeLock 2GO portal
Refer to NXP's application note AN12691, specifically chapter 6 titled "Create and manage ICAs," for guidance on establishing the connection with EJBCA.
To create the intermediate CA, follow the steps outlined in subsections 6.1 and 6.2 of the application note:
- When prompted to select a key type and size, ensure they are consistent with the trust chain created in EJBCA.
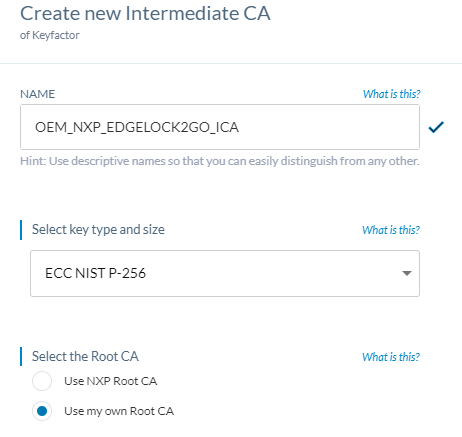
- For Select the Root CA, select Use my own Root CA.
Under provide CSR metadata, specify the DN fields which will be transmitted into the CSR.
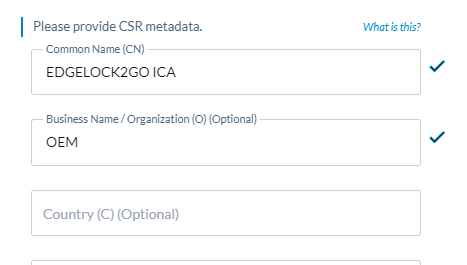
If using the optional fields, ensure the fields align with your trust chain previously defined in your EJBCA PKI.
Avoid using special characters such as '+' or '_', as they may lead to errors in the process later on.
- Click Create to create the intermediate CA.
Step 6 - Finalize Intermediate CA
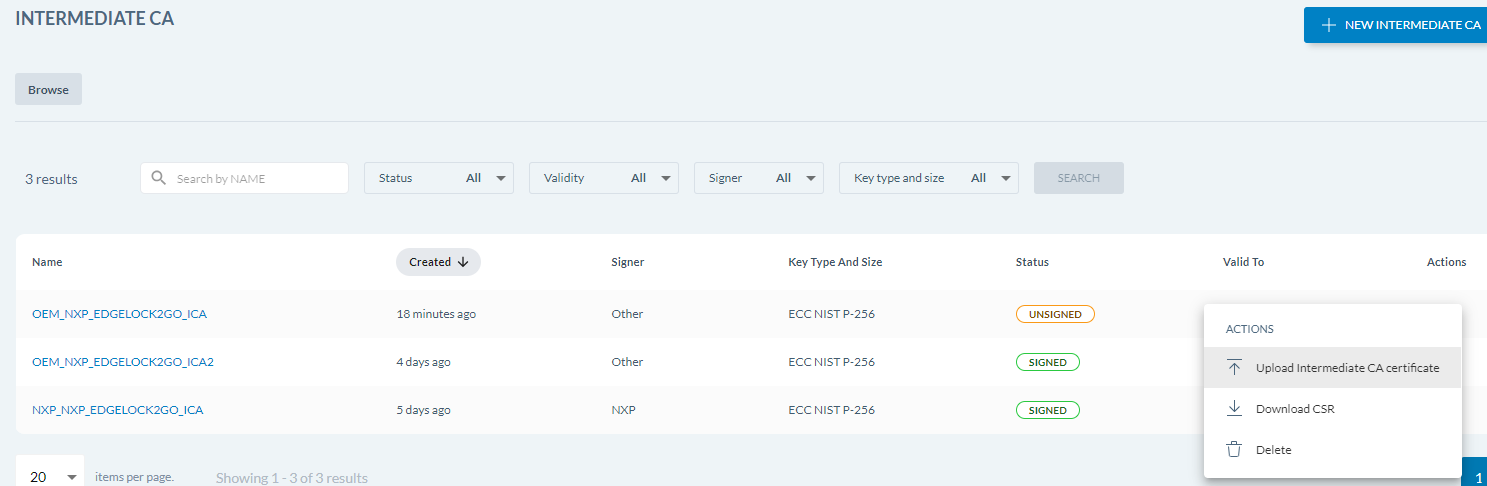
The ICA is now created on the portal, but it is not yet signed and is listed with status Unsigned.
To download the CSR from the portal and upload it to EJBCA RA web to download a generated certificate, do the following:
- Download the CSR for the ICA and save it to your working directory:
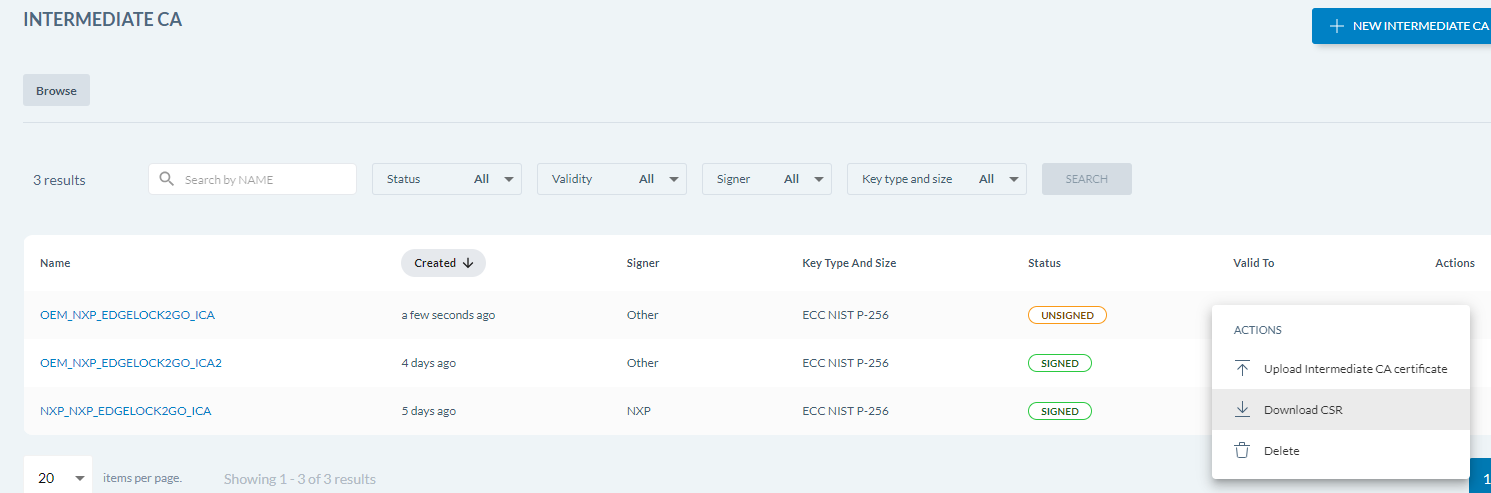
- In EJBCA, click RA Web to access the EJBCA RA UI.
- Under Request new certificate, select Make New Request.
- For Certificate Type, select the relevant End Entity profile for the ICA certificate.
- For Key-pair generation, select Provided by user.
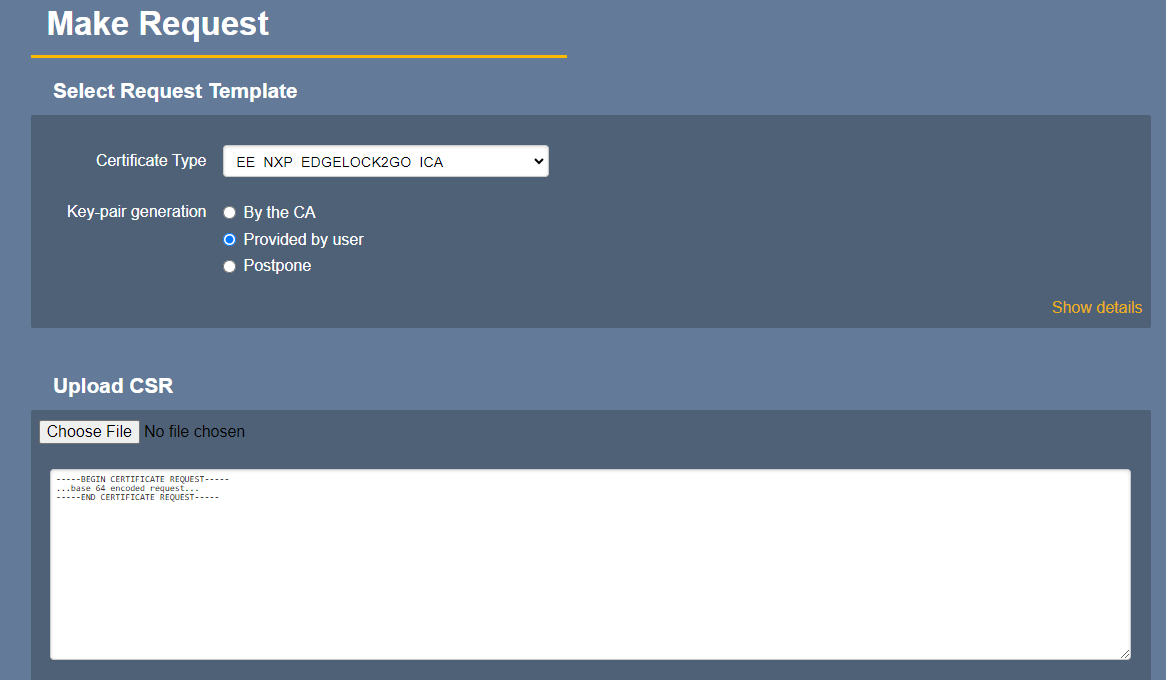
- Click Upload CSR to upload the CSR file previously downloaded from the EdgeLock 2GO portal to EJBCA.
- In the Provide request info section, you can verify that EJBCA picked up the common name from the CSR and that the information added to the profile are shown.
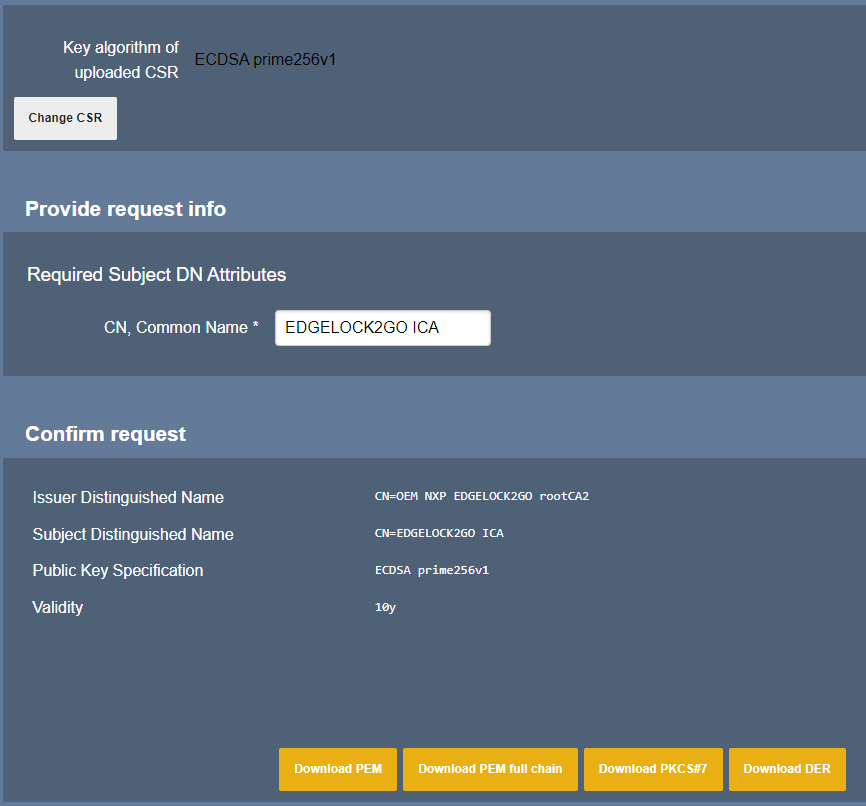
- Download the PEM file and save it to your working directory.
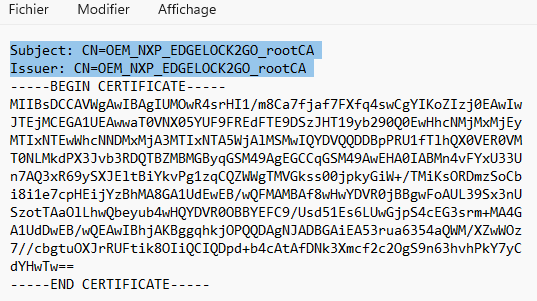
- Also download the SubCA_NXP certificate which was used to sign this ICA certificate into the same directory.
- Edit both files with a text editor to remove the Subject and Issuer headers (since EdgeLock 2GO does not parse this information), and save the files.
- Go back to the EdgeLock 2GO portal and click Upload ICA certificate to finalize the creation of your ICA:
- Upload the certificates you have just edited:
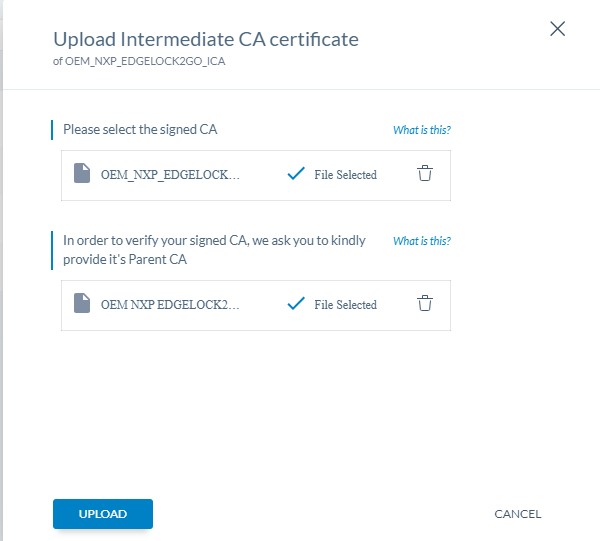
- The ICA now appears as Signed in the portal.
Generate and provision device certificates
For step-by-step instructions on how to generate and provision device certificates, please follow chapter 7 of the NXP’s application note AN12691.
When naming device certificates in the CN field, avoid using special characters as they may prevent the issuance of the device certificate by the EdgeLock 2GO server later on.
EdgeLock 2GO also provides APIs to automate the generation and issuance of certificates, refer to NXP’s information about EdgeLock 2GO for more information.
Next steps
This guide has demonstrated how you can set up EJBCA for NXP’s service platform EdgeLock 2GO for provisioning and managing IoT devices.
For more tutorials for trying out and evaluating EJBCA, see Tutorials and Guides.
.png)