Tutorial - Issue TLS server certificates with EJBCA
Learn how to manually issue end entity certificates with EJBCA.
In this tutorial, you will learn how to:
- Create a certificate profile for server TLS certificates
- Create an end entity profile
- Create a certificate signing request (CSR)
- Issue certificate based on a CSR
Prerequisites
Before you begin, you need a running EJBCA instance with an active Certificate Authority (CA).
To learn how to configure a certificate profile template and CA-defined default values, see the tutorial Create a PKI Hierarchy in EJBCA.
Step 1 - Create certificate profile
The first step is to create a certificate profile for server TLS certificates. The certificate profile defines the content and constraints of new certificates. For example,you can define which keys types are allowed and what extensions to use in certificates. For an introduction to certificate profiles, see the Certificate Profiles Overview.
To create a certificate profile for server TLS certificates, do the following:
- In EJBCA, under CA Functions, click Certificate Profiles.
The Manage Certificate Profiles page displays a list of available profiles. - Click Clone next to the SERVER template to use that as a basis for creating your new profile.
- Name the new certificate profile TLS Server Profile and click Create from template.
- To edit the profile values to fit your needs, find the newly created TLS Server Profile in the list and click Edit.
- On the Edit page, verify that the type is End Entity and update the following:
- For Available Key Algorithms, select ECDSA to only allow elliptic curve keys.
- For Available ECDSA curves, select P-256 / prime256v1 / secp256r1.
- For Signature Algorithm, verify that Inherit from Issuing CA is selected.
- For Validity or end date of the certificate, specify 1y.
- Expiration Restrictions: Enable to only allow certificates to expire on Tuesdays, Wednesdays, and Thursdays to avoid certificates expiring close to a weekend.
- For Available Key Algorithms, select ECDSA to only allow elliptic curve keys.
- Under Permissions, you can allow the requester of the certificate to override certain default values of the profile that you are configuring, thus overriding profile defaults such as validity or extensions and setting their own values. By default, EJBCA does not allow any overrides and thus the certificate issued will be defined by what is configured in this profile.
- The X.509v3 extensions section allows you to define the extensions added to the certificate:
- Clear Basic Constraints since this constraint defines that this is an end entity certificate and not a CA certificate, and you want this to be optional.
- For Key Usage, verify that Digital Signature and Key encipherment is selected.
For Extended Key Usage, verify that Server Authentication is selected.
Extended key usages define how the certificate and the key pair can be used. If you need a key usage that is not available by default, you can add additional extended key usages in the EJBCA System Configuration, see Extended Key Usages.- For X.509v3 extensions - Names, verify that Subject Alternative Name is selected and clear the Issuer Alternative Name extension as the CA does not have an alternative name.
- Under X.509v3 extensions - Validation data:
Enable CRL Distribution Points to allow validation later on.
Enable Use CA defined CRL Distribution Point to use the value pre-configured in the CA.
Enable Authority Information Access to use the locations configured in your CA settings:
Enable Use CA defined OCSP locator for where the OCSP services are available
Enable Use CA defined CA issuer for where the issuing CA certificate can be retrieved from.
Under Other Data, update the following:
Clear LDAP DN order to disable the LDAP ordering of the DN attributes and use the standard X.509 ordering instead.
For Available CAs, select your Sub CA MyPKISubCA-G1.
Click Save to store the certificate profile.
The newly created TLS Server Profile is displayed in the list of certificate profiles.
Step 2 - Create end entity profile
Next, create an end entity profile that allows you to define what information about holders of certificates EJBCA keeps track of and adds as subject information.
An End Entity is a user of the PKI, like a device, person, or server. It is called the end entity as, in a hierarchy of certificates in the PKI, it is the endpoint and not authorized to issue any certificates of its own.
The end entity profile is used to define what subject information (e.g. subject DN and subject alternative name) to add to certificates. It is always used together with a certificate profile for certificate issuance. You can for example make it so that certificate requests are only allowed to contain certain values, otherwise they are reject, while some fields are free for the requestor to choose.
Attribute values specified in end entity profiles are used either for validating requests, as optional default values or can be combined with values provided in a certificate request. For instance, if you make the country attribute non-modifiable and required, and specify SE as the country code, that means that certificates should only be issued to end entities from Sweden.
Additionally, end entity profiles controls if the issuing CA should generate key pairs together with certificates or allow issuance based on certificate signing requests (CSRs) created by the end entity.
To create an end entity profile, follow these steps:
- In EJBCA, under RA Functions, click End Entity Profiles.
- In the Add Profile field, add a name for the new profile, in this example TLS Server Profile, and click Add profile.
- Select the newly created TLS Server Profile, and click Edit End Entity Profile to update the profile.
- Edit the profile and update the following:
- Clear End Entity E-mail to not save any email addresses.
- Under Subject DN Attributes, specify the following:
- For Subject DN Attributes, add an Organization field and a Country field.
- For CN, Common Name, verify that Required and Modifiable are selected to allow the value to be used when a new request is made. You can optionally add a Validation with a regex to restrict what values are allowed.
- For O, Organization, verify that Required is selected and clear Modifiable and enter "Keyfactor Community" to be used as the organization.
- For C, Country, verify that Required is selected and clear Modifiable and enter "SE" to use Sweden as the country.
- Under Other Subject Attributes, you can specify options for Subject Alternative Name (SAN). Some browsers require this field and it should be implemented for server certificates:
- In the Subject Alternative Name list, select DNS Name and click Add. For the displayed DNS Name field, select Use entity CN field to add a DNS name that is the same as your common name field.
- Add additional optional DNS names to allow more than one DNS name in the certificates. Select DNS Name and click Add. For the displayed DNS Name field, leave the default Modifiable option selected. Repeat to add additional optional DNS names.
- Main Certificate Data allows you map the profile to be used together with default certificate profiles and CAs:
- For Default Certificate Profile, select the TLS Server Profile you created in Step 1 - Create certificate profile).
- For Default CAs, select the MyPKISubCA-G1 to restrict this profile to only be usable by your Sub CA (created in Create a PKI Hierarchy in EJBCA).
- Specify Default Token options to define how the key pair generation should be implemented for the certificates:
- Select User Generated and CA-side key pair generation in PEM file format to allow the CA to generate the key pair together with the certificate.
User Generated means that the requester generates their own key pair and thus that the user creates and provides a certificate signing request (CSR) for the certificate request to EJBCA. The other file options allow the CA to generate the private key and certificate and return those to the requester as a single file in the selected format.
- Select User Generated and CA-side key pair generation in PEM file format to allow the CA to generate the key pair together with the certificate.
- Click Save to store the end entity profile.
Step 3 - Issue server certificate
To issue a server certificate, use the EJBCA RA web interface to make a new request and enroll using your new profiles.
- In EJBCA, click RA Web to access the EJBCA RA UI.
- Select Make New Request from the Enroll menu.
- For Certificate Type, select your TLS Server Profile (created in Step 1 - Create certificate profile).
- For Key-pair generation, select Provided by user to allow you to upload a certificate signing request (CSR).
- To create a CSR, open your terminal and follow these steps:
Use the text editor of your choice to create a simple configuration file (in this example named tls_cert_req.cnf) with the following information to be added to your request:
CODE[ req ] default_md = sha256 prompt = no distinguished_name = dn [ dn ] CN = test.my.pki O = Keyfactor Community C = SEGenerate an elliptic cure key with OpenSSL using the prime256v1 curve as defined in the certificate profile:
CODEopenssl ecparam -genkey -name prime256v1 -out tls_server.keyUse the OpenSSL req command to combine the key and the configuration to create a CSR and your certificate request:
CODEopenssl req -new -key tls_server.key -config tls_cert_req.cnfYou should receive an output looking something like the following:
CODE-----BEGIN CERTIFICATE REQUEST----- fyGCAkd/ToIBPV8pAQBCDVNFQ1ZDQVBLMDAwMDF/SYIBFQYKBAB/AAcCAgIBAoGC AQDJuBLa1iFXD7WWK6614RvtmiZpgFXiTWkznp5MfusJuNqBuz46zeFAIJcerEtK xcHtbOppA5U2FwOtqit0yhkg2XLTEf9zh5ewchSGWujG9yY77BPXfLg3a3iwVyBW sED4z4L71hfvByTtkBpz90BFjwMUsiSzkuRwM/2PeThJNm5yDZVjLNFfN7Vdibi6 7PRh77oQkofk/FvMNVa60u6RsT1urJdM7+5mCvGOs0KoWzFMCdm3rZrIIvWmQBSx MPRL42AVDgY/G7df27YMHJZ -----END CERTIFICATE REQUEST-----
- Copy the certificate request and go back to the EJBCA Make Request page.
- Paste the copied CSR and click Upload CSR to upload it to EJBCA.
- In the Provide request info section, you can verify that EJBCA picked up the common name from the CSR and that the optional DNS Name fields added to the profile are shown.
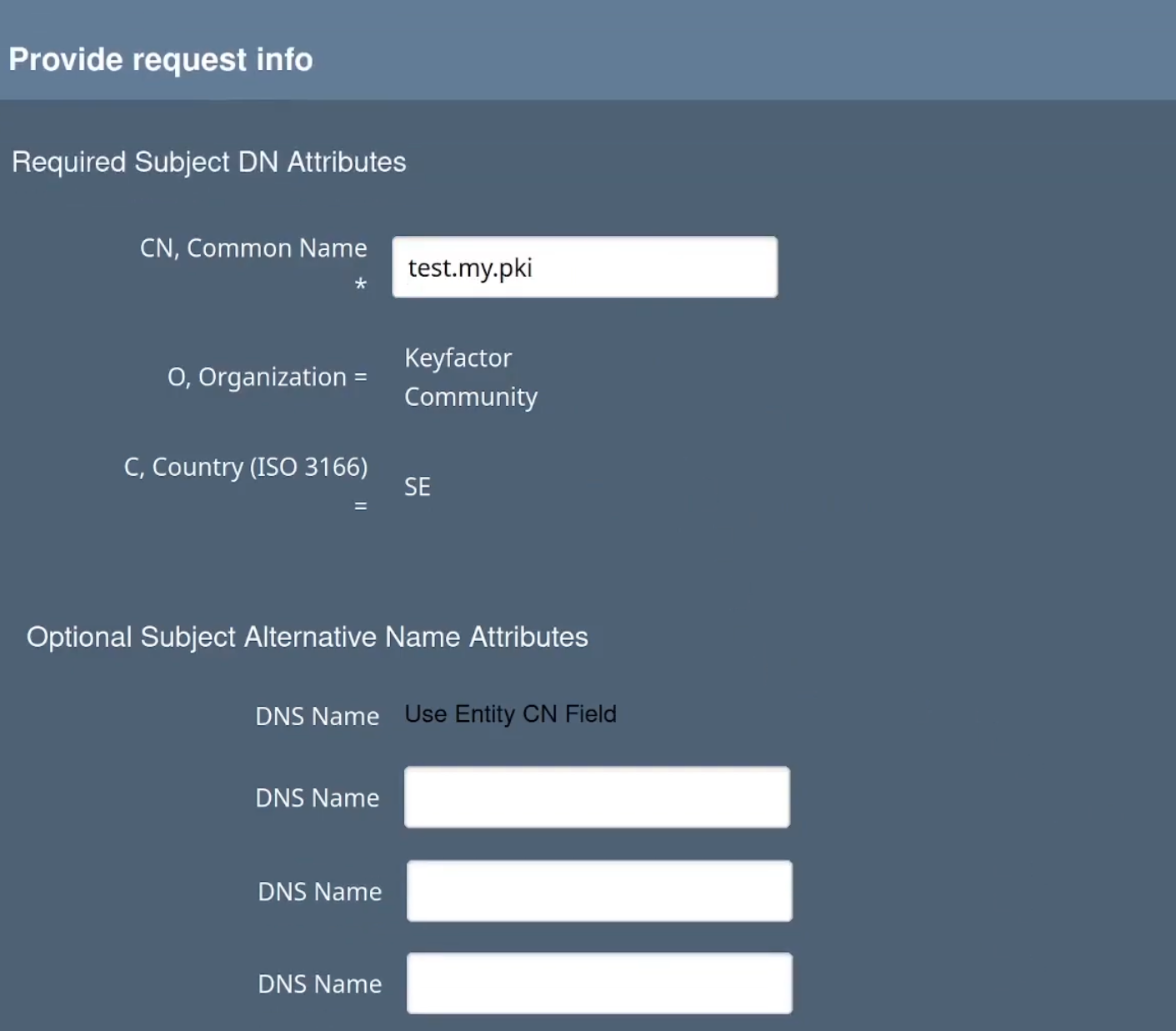
- For Username, add test.my.pki to register the user under the username identical to the common name. The Username is the name that will go into the database and is often the same as the Common Name.
- Click Download PEM full chain to download the generated certificate together with the CA certificates in a PEM chain.
The downloaded test.my.pki.pem file includes your certificate test.my.pki and CA certificates for the Root CA and Sub CA.
Next steps
In this tutorial, you learned how to create a certificate profile for server TLS certificates, create an end entity profile for keeping information about certificate holders, and issue a TLS server certificate based on a certificate signing request (CSR).
To learn more about issuing client TLS certificates in EJBCA with CA-side key pair generation, you can follow the tutorial Issue TLS client certificates with EJBCA.
.png)