MPIC Validator
ENTERPRISE
The MPIC Validator allows a Multi-Perspective Issuance Corroboration, to facilitate Certificate Authority Authorization (CAA) from multiple network perspectives. The MPIC Validator is based on the specification for the Open MPIC Protocol, see Open Multi-Perspective Issuance Corroboration API Spec.
MPIC proposes a safer alternative to single perspective validation which might be vulnerable to DNS and BGP hijacks, MPIC allows corroboration of CAA validation over different network perspectives on different locations.
Note that the functionality was tested against the AWS MPIC Lambda implementation version 0.3.2 (up to the commit 9fe11198df804d97cbbe2e5f31a5fa7601edd280) and supports the API Spec from 2.7 to 3.3.
TLS Validation
A typical CAA record has the following format:
Command:
dig caa example.comResponse:
example.com. 243 IN CAA 0 issue "ca.org"For an MPIC request, this same record to a server configured to have two network perspectives, one in the US and one in Europe, would show as follows:
Request:
curl --location 'https://<your-mpic-server-url>/v1/mpic' \
--header 'Content-Type: application/json' \
--header 'x-api-key: ••••••' \
--data '{
"check_type": "caa",
"domain_or_ip_target": "example.com"
}'Response:
{
"request_orchestration_parameters": null,
"actual_orchestration_parameters": {
"perspective_count": 2,
"quorum_count": 1,
"attempt_count": 1
},
"is_valid": true,
"check_type": "caa",
"perspectives": [
{
"perspective_code": "eu-west-1",
"check_passed": true,
"errors": null,
"timestamp_ns": 1736247778402104091,
"check_type": "caa",
"details": {
"caa_record_present": true,
"found_at": "example.com",
"response": "example.com. 243 IN CAA 0 issue \"ca.org\""
}
},
{
"perspective_code": "us-west-1",
"check_passed": true,
"errors": null,
"timestamp_ns": 1736247778485125494,
"check_type": "caa",
"details": {
"caa_record_present": true,
"found_at": "example.com",
"response": "example.com. 243 IN CAA 0 issue \"ca.org\""
}
}
],
"caa_check_parameters": null
}For this example the response includes a convenient flag is_valid meaning that for both of the perspectives the ca.org is allowed to issue example.com certificates. And by observing the response we can conclude that the CAA query result is the same if done both in Europe and US. Note that this is an example with two perspectives and the recommended number of perspectives for a secure query is six.
S/MIME Validation
CA/B Forum specifies the criteria for allowing or rejecting an S/MIME certificate request based on a performed CAA check defined in the S/MIME Base Requirements document.
A typical S/MIME CAA record has the following format:
example.com. 243 IN CAA 0 issuemail "ca.org"For MPIC, a request would look as follows:
Request:
curl --location 'https://<your-mpic-server-url>/v1/mpic' \
--header 'Content-Type: application/json' \
--header 'x-api-key: ••••••' \
--data '{
"check_type": "caa",
"domain_or_ip_target": "example.com",
"caa_check_parameters" : {
"certificate_type": "s-mime"
}
}'Response:
{
"request_orchestration_parameters": null,
"actual_orchestration_parameters": {
"perspective_count": 2,
"quorum_count": 1,
"attempt_count": 1
},
"is_valid": true,
"check_type": "caa",
"perspectives": [
{
"perspective_code": "eu-west-1",
"check_passed": true,
"errors": null,
"timestamp_ns": 1736247778402104091,
"check_type": "caa",
"details": {
"caa_record_present": true,
"found_at": "example.com",
"response": "example.com. 300 IN CAA 0 issuemail \"ca.org\""
}
},
{
"perspective_code": "us-west-1",
"check_passed": true,
"errors": null,
"timestamp_ns": 1736247778485125494,
"check_type": "caa",
"details": {
"caa_record_present": true,
"found_at": "example.com",
"response": "example.com. 300 IN CAA 0 issuemail \"ca.org\""
}
}
],
"caa_check_parameters": {
"certificate_type": "s-mime",
"caa_domains": [
"example.com"
]
}
}To enable this type of validation, in addition to creating the MPIC validator, the certificate profile field Extended Key Usage option Email protection must be selected within the certificate profile.
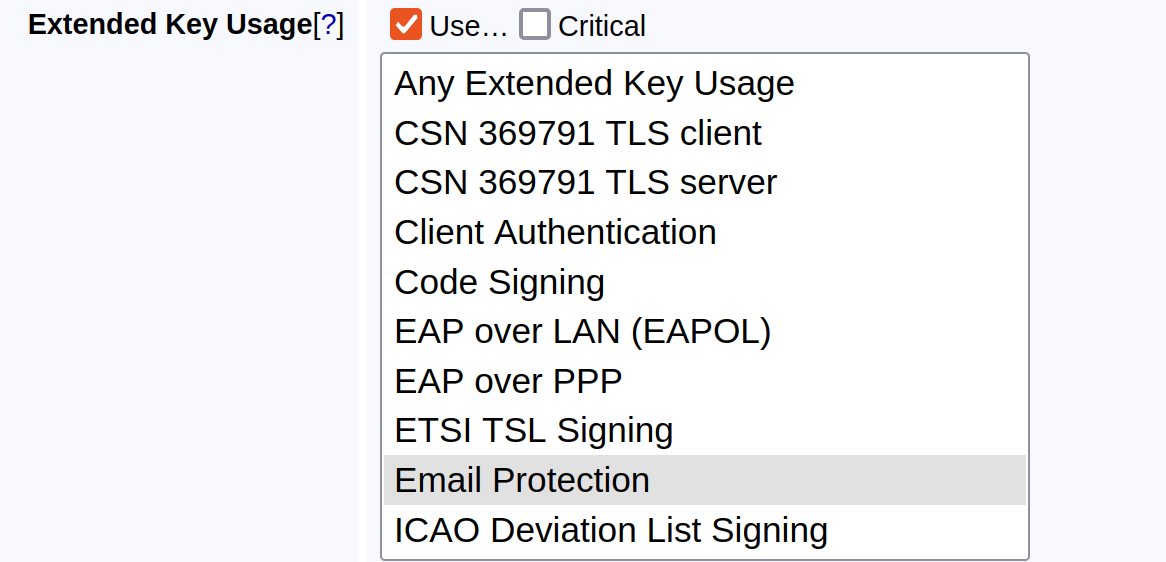
When using an MPIC Validator, you must select either Email Protection or Server Authentication in the certificate profile, but not both.
Configure MPIC Validator
Issuance Phase
Different validators are run at different phases of the issuance process. The MPIC Validator can only be run during the data phase. For descriptions of the different issuance phases, see Validators Overview.
Fields
The following displays the MPIC Validator settings.
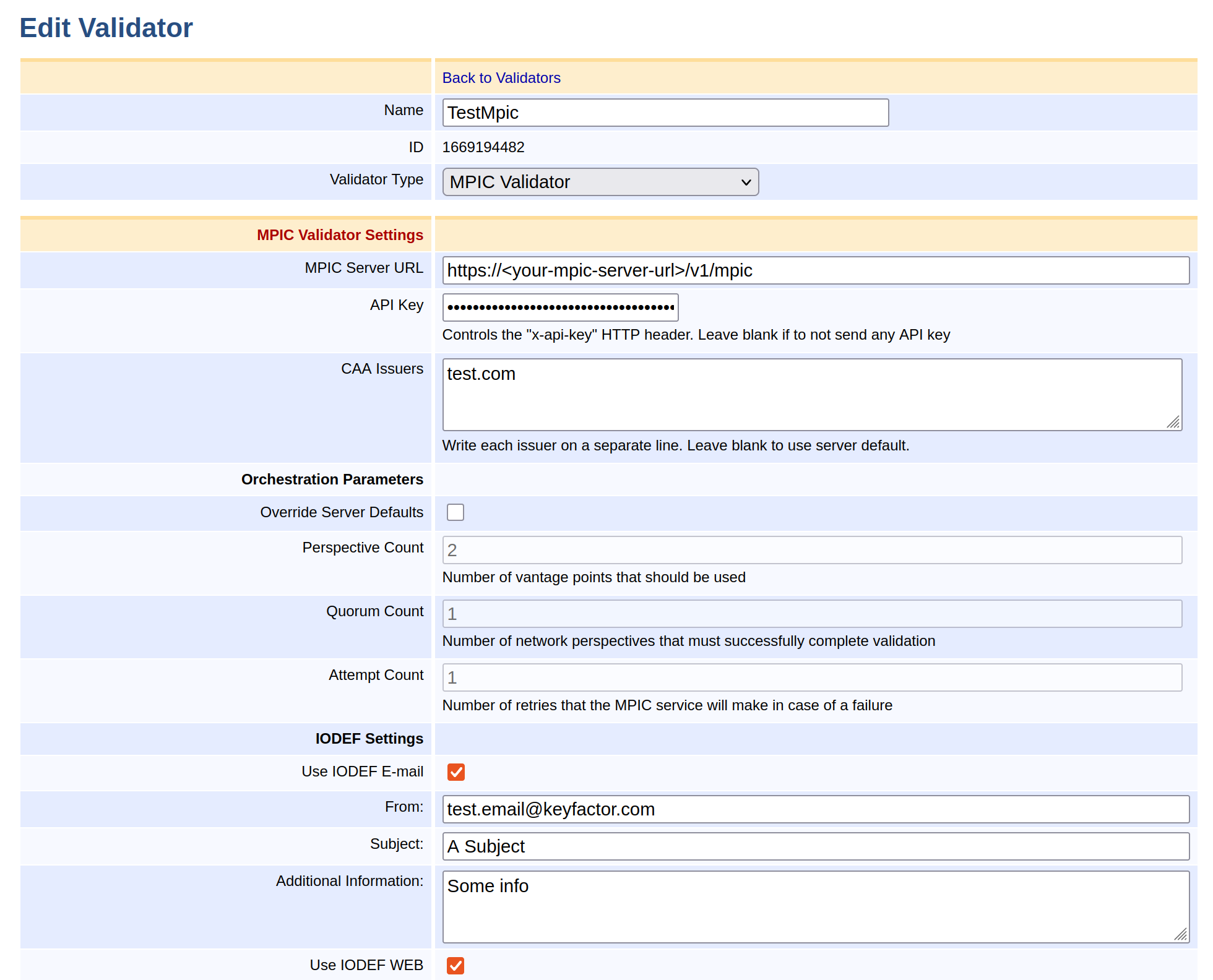
EJBCA allows the administrator to configure the following when setting up a CAA Validator:
Field Name | Description |
|---|---|
MPIC Server URL | The MPIC server URL. |
API Key | The API Key to be sent in the |
CAA Issuers | This value should match the value field in the CAA record of the DNS. |
Override Server Defaults | Select to override the default configuration for Perspective, Quorum, and Attempt counts. |
Perspective Count | The number of vantage points to use in the requests. Allows the implementing API endpoint flexibility in picking vantage points so long as vantage points are picked from at least two different Regional Internet Registry service regions if possible. |
Quorum Count | The number of network perspectives that must successfully complete the the validation methods specified. As long as this value is greater than 2, the API will enforce that successful network perspectives must be spread across two Regional Internet Registry service regions |
Attempt Count | The number of times validation or CAA checks has been retried to get the result of a single API POST request. |
IODEF Settings | |
Use IODEF E-mail | Select to enable sending e-mails to any mailto-links registered on the DNS as CAA IODEF records. |
From | The From field in the resulting e-mail. |
Subject | The Subject line in the resulting e-mail. |
Additional Information | Any additional information required, in addition to the following default message which will be appended at the end: A faulty Certificate Request was made for the domain 'http://example.com ' for the issuer http://ca.com which was rejected by the CA due to the issuer not having a CAA record on the domain's DNS. |
Use IODEF WEB | Enables sending IODEF incident reports to any http/s-links registered on the DNS as CAA IODEF records. |
MPIC Validator Logging
The MPIC validator logs both success and failure. Since success can be considered a security event, to be shown as evidence, this is logged in the security audit log. Failures are not security events per se and logged to the standard server log at info level.
Example failure:
10:29:09,060 INFO [org.ejbca.core.model.validation.MpicValidator] (default task-6) MPIC CAA validation failed for domain 'test.globalsign.com' with type 'tls-server'. JSON response from MPIC server: {"request_orchestration_parameters":null,"actual_orchestration_parameters":{"attempt_count":1,"perspective_count":2,"quorum_count":1},"perspectives":[{"check_passed":false,"check_type":"caa","details":{"response":"globalsign.com. 300 IN CAA 0 issuemail \"globalsign.com\"\nglobalsign.com. 300 IN CAA 0 iodef \"mailto:report-abuse@globalsign.com\"\nglobalsign.com. 300 IN CAA 0 issue \"globalsign.com\"\nglobalsign.com. 300 IN CAA 0 issue \"letsencrypt.org\"","caa_record_present":true,"found_at":"globalsign.com"},"perspective_code":"eu-west-1","timestamp_ns":1736238548872449850,"errors":null},{"check_passed":false,"check_type":"caa","details":{"response":"globalsign.com. 300 IN CAA 0 iodef \"mailto:report-abuse@globalsign.com\"\nglobalsign.com. 300 IN CAA 0 issue \"globalsign.com\"\nglobalsign.com. 300 IN CAA 0 issue \"letsencrypt.org\"\nglobalsign.com. 300 IN CAA 0 issuemail \"globalsign.com\"","caa_record_present":true,"found_at":"globalsign.com"},"perspective_code":"us-west-1","timestamp_ns":1736238548832234721,"errors":null}],"is_valid":false,"check_type":"caa","caa_check_parameters":{"caa_domains":null,"certificate_type":"tls-server"}}Example success:
15:30:41,883 INFO [org.cesecore.audit.impl.log4j.Log4jDevice] (default task-9) 2025-01-07 15:30:41+02:00;VALIDATOR_VALIDATION_SUCCESS;SUCCESS;VALIDATOR;CORE;CN=diegows;278366771;;atest123;msg=MPIC Validator 'TestMpic' has permitted issuance of certificates to issuer , with messages: [Allowed to issue for for domain 'test.google.com' with type 'tls-server'. JSON response from MPIC server: {"request_orchestration_parameters":null,"actual_orchestration_parameters":{"attempt_count":1,"perspective_count":2,"quorum_count":1},"perspectives":[{"check_passed":true,"check_type":"caa","details":{"response":"google.com. 47663 IN CAA 0 issue \"pki.goog\"","caa_record_present":true,"found_at":"google.com"},"perspective_code":"eu-west-1","timestamp_ns":1736256641635312259,"errors":null},{"check_passed":true,"check_type":"caa","details":{"response":"google.com. 86400 IN CAA 0 issue \"pki.goog\"","caa_record_present":true,"found_at":"google.com"},"perspective_code":"us-west-1","timestamp_ns":1736256641692320803,"errors":null}],"is_valid":true,"check_type":"caa","caa_check_parameters":{"caa_domains":null,"certificate_type":"tls-server"}}].For more general information about validators and common validator settings, see the Validators Overview.
.png)