Access
The Access tab and subtabs offer the following access configuration options.
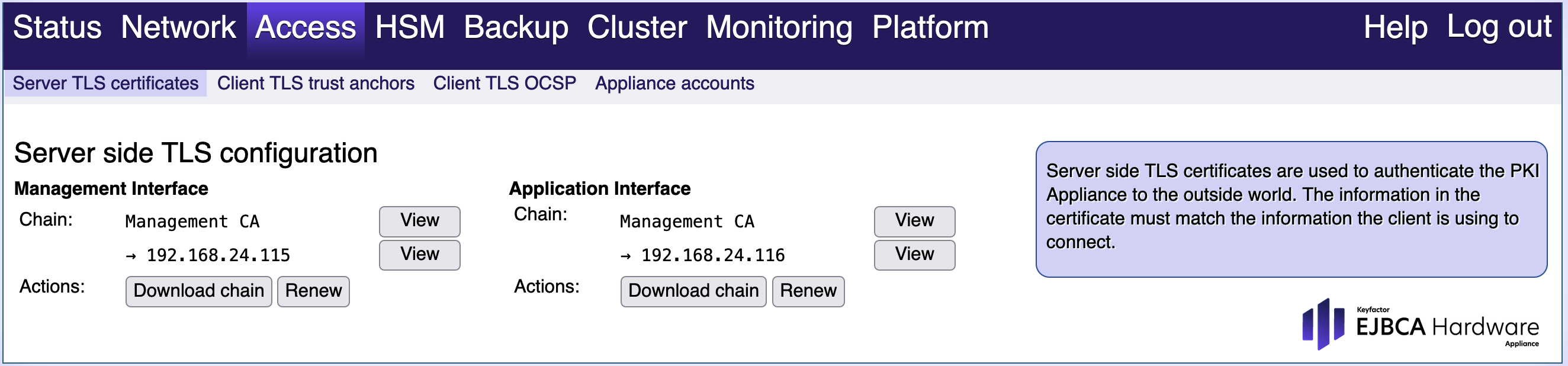
Server TLS Certificates
Server side TLS certificates are used to authenticate the Hardware Appliance to the outside world. The information in the certificate must match the information that the client uses for the connection. The client must trust the issuer of the certificate.
The following values are normally set in an TLS certificate (assuming that the host is hostname.example.com and the IP is always 10.10.10.10):
Subject Distinguisher Name: CN=hostname.example.com ... Subject Alternative Names: DNSName=hostname.example.com IPAddress=10.10.10.10 ... Key Usage: Digital Signature, Key Encipherment Extended Key Usage: TLS server authentication (OID 1.3.6.1.5.5.7.3.1)
Setting the hostname to an IP address will also work.
The initial certificates issued for the network interfaces are self-signed. During the installation they are replaced with certificates issued by the initial Management CA.
If you already have an existing TLS CA that is trusted by browsers in your organization, you can replace the certificates in this view.
- Select Renew.
- To create a Certificate Signing Request select Download CSR.
- Send the CSR to your CA together with the information you would like to have in the certificate. Note that some implementations (e.g. Java) require a matching IP address or DNS entry in the certificate.
- Upload the issued certificate in PEM format with full certificate chain.
Client TLS Trust Anchors
Client side TLS certificates are used to authenticate users or external systems to the Hardware Appliance. For a client certificate to even be considered by the Hardware Appliance for authentication it must be issued by a CA that is trusted by the Hardware Appliance. If the client certificate is trusted, the Hardware Appliance or application firmware will try to match the information in the certificate to a list of rules (accounts).
Note that no revocation checking has been implemented yet.
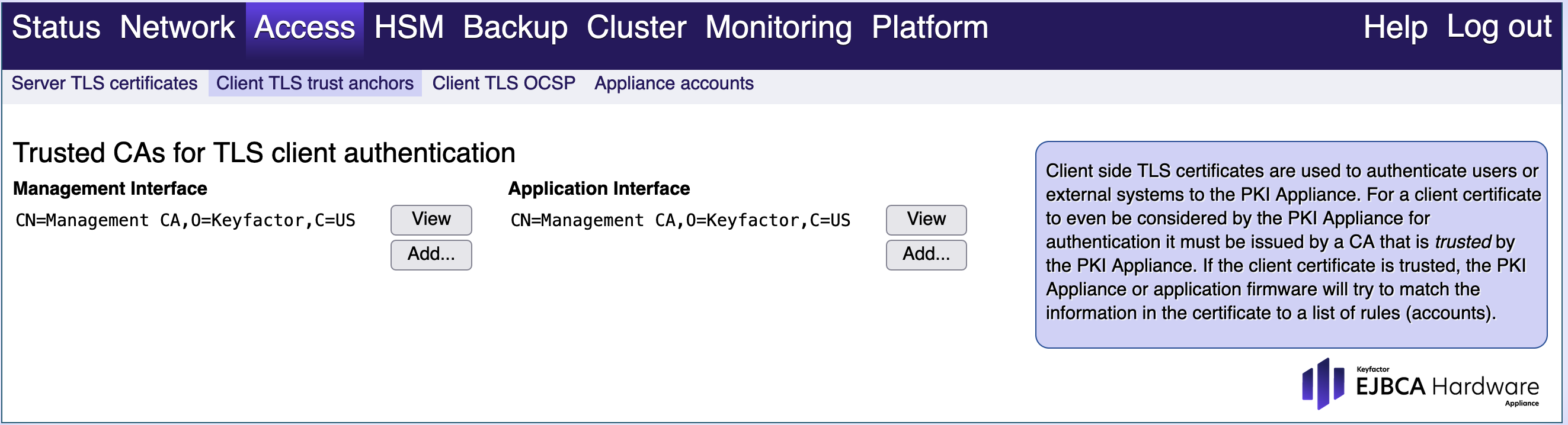
Trusted CAs for client authentication
You can configure different trusted certificates (trust anchors) for each network interface. If you want to use client TLS certificates from an external CA, you need to replace the trusted certificate. To avoid locking yourself out of the Hardware Appliance, first add the appropriate matching rules in the sub tab Access > Appliance accounts, so that you can reconnect and continue to administer the Hardware Appliance after the trusted certificate is replaced.
To configure a new trusted certificate, simply upload the CA certificate (in PEM format) and confirm the change. After a short delay, you will be able to reconnect using the client TLS certificate issued by this trusted CA.
Client TLS OCSP
Use this tab to configure whether and how the Hardware Appliance performs OCSP verifications on TLS client certificates of incoming connections. Currently, the options are available for the Application interface only. The configuration for the Management interface is currently disabled. This way you avoid the risk of locking yourself out.
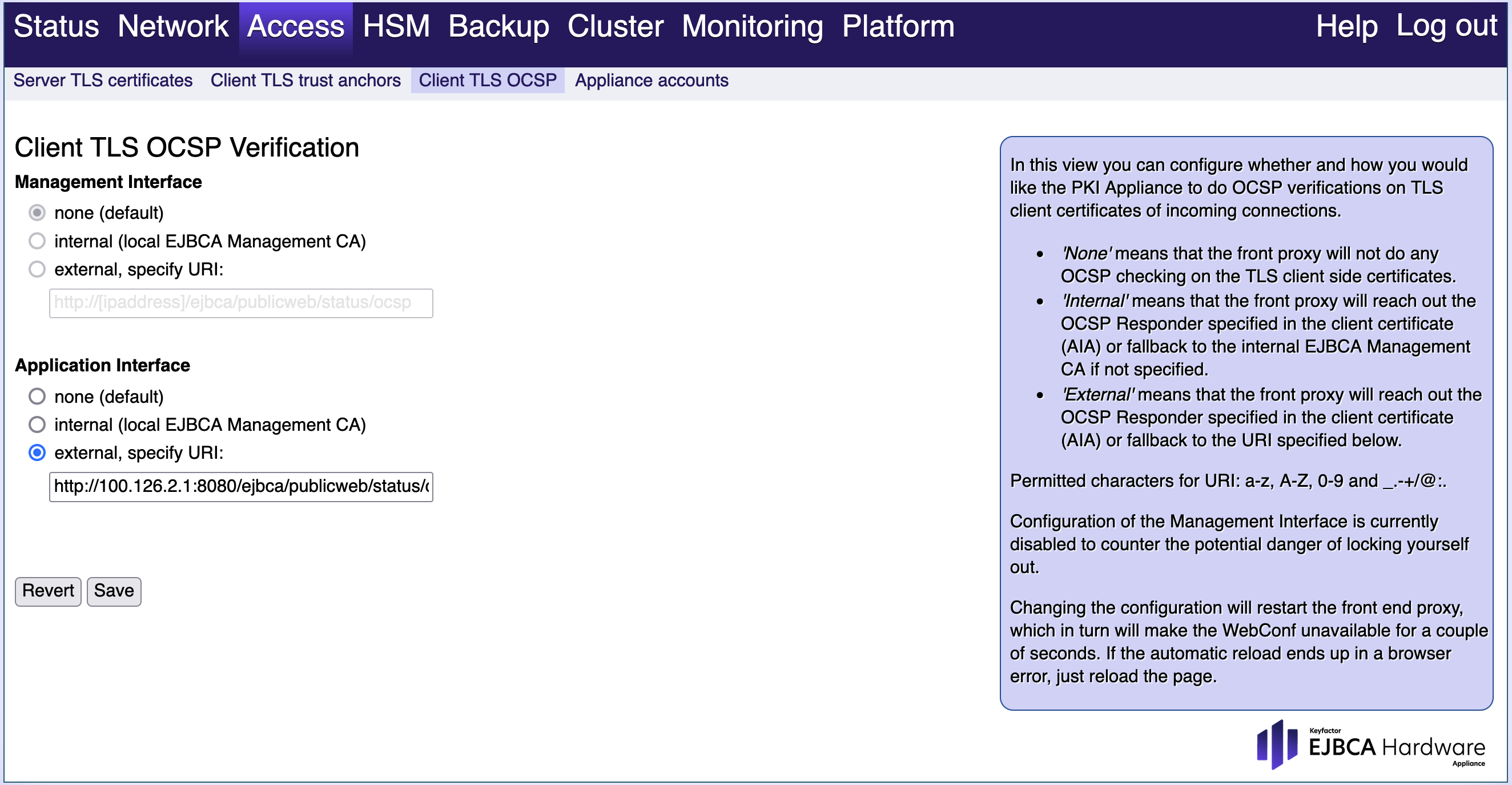
You have the following options:
None:
The front proxy will not do any OCSP checking on the TLS client side certificates.
Internal:
The front proxy will reach out the OCSP Responder specified in the client certificate (AIA). If that is not specified, it will fallback to the internal EJBCA Management CA.
External:
The front proxy will reach out the OCSP Responder specified in the client certificate (AIA). If that is not specified, it will fallback to the specified URI.
These are valid characters for the URI:
- a-z
- A-Z
- 0-9
- Special characters _ . - + / @ : .
Save / Revert:
Select Save to confirm your changes, Revert to undo them.
Changing the configuration results in a restart of the front end proxy. WebConf will then be unavailable for a few seconds.
If the automatic reload ends up in a browser error, just reload the page.
Appliance Accounts
Hardware Appliance management accounts are matching rules that will be processed when a user tries to log in.
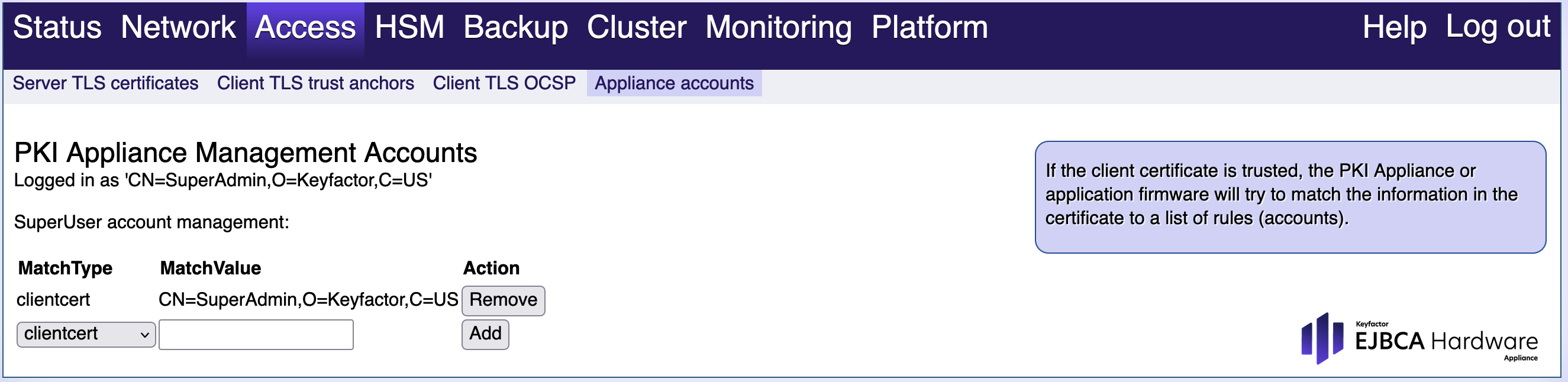
You have the following options:
MatchType:
Select the desired rule from the drop-down menu. These options are supported:
clientcert: Client TLS certificates authentication
sharedsecret: Shared secret (password) authentication
MatchValue:
The required MatchValue depends on the selected MatchType:
MatchValue for clientcert: The match value is the entire subject distinguisher name of the certificate., as for example "CN=SuperAdmin,O=Keyfactor,C=US".
MatchValue for sharedsecret: The match value is the shared secret.
We strongly recommend to use the clientcert option. Authentication via sharedsecret might disappear in future releases of the Hardware Appliance.
Add:
Select Add to add the rule with the specified MatchType and MatchValue.
Remove:
Select Remove to remove the rule in that line.
.png)