Check for Weak Debian Keys
Create Script on the Appliance
To create a script on the Hardware Appliance:
- Go to the Appliance WebConf, click Platform > Platform access and enable SSH.
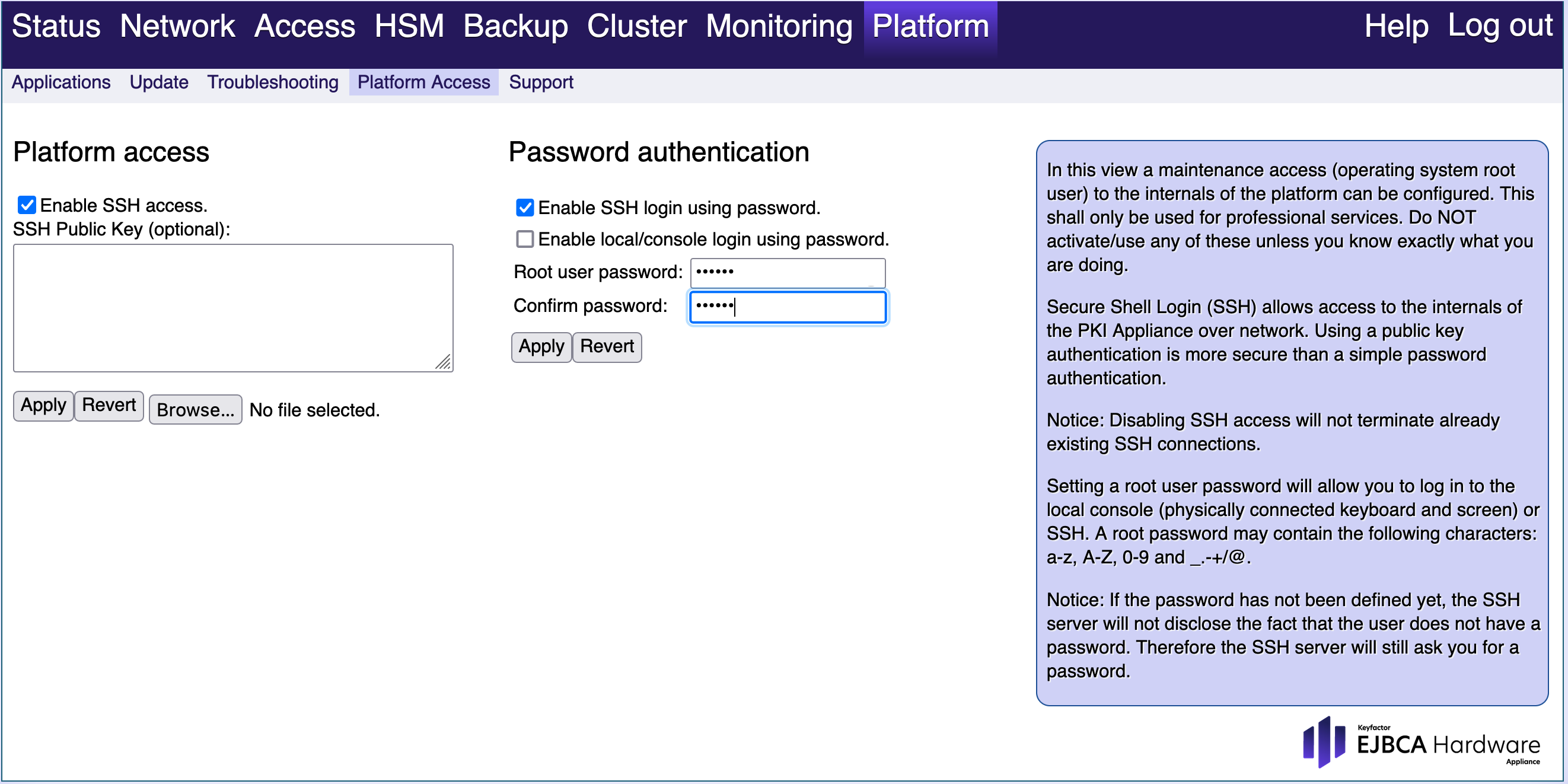
- Transfer the file
debian-weak-keys.tar.xzto the appliance using e.g. WinSCP. Log in using SSH and transfer the file
debian-weak-keys.tar.xztocos-ejbca.Replace
MGMT_IPwith the IP address of the management interface shown on the appliance front display.CODEssh root@MGMT_IP scp debian-weak-keys.tar.xz cos-ejbca:Jump to
cos-ejbca.CODEssh cos-ejbcaCreate directories in
/etc.CODEmkdir -p /etc/weak-keys/all-listsExtract the file with the Debian blacklists.
CODEtar -C /etc/weak-keys/all-lists -xf debian-weak-keys.tar.xzCreate a script which can be attached to a validator in EJBCA.
/etc/weak-keys/weak-keys.sh
BASH#!/bin/sh output=`grep $(openssl x509 -noout -pubkey -inform DER -in $1 \ | openssl rsa -pubin -noout -modulus \ | sha1sum | cut -d ' ' -f 1 | cut -c 21-) \ /etc/weak-keys/all-lists/blacklist*` if [ -z "$output" ]; then logger "The public key in the certificate is not on a known weak Debian key." exit 0 else logger "Known weak Debian key was detected in certificate." logger "You can inspect the base64 encoded certificate shown below:" logger `cat $1 | base64` exit 1 fiSet permissions for WildFly.
CODEchown -R user:user /etc/weak-keys chmod +x /etc/weak-keys/weak-keys.sh
Create External Command Certificate Validator
To create an External Command Certificate Validator:
- Open the EJBCA Enterprise. In the sidebar, in the System Configuration section, select System Configuration.
In the window System Configuration chose External Scripts from the menu bar.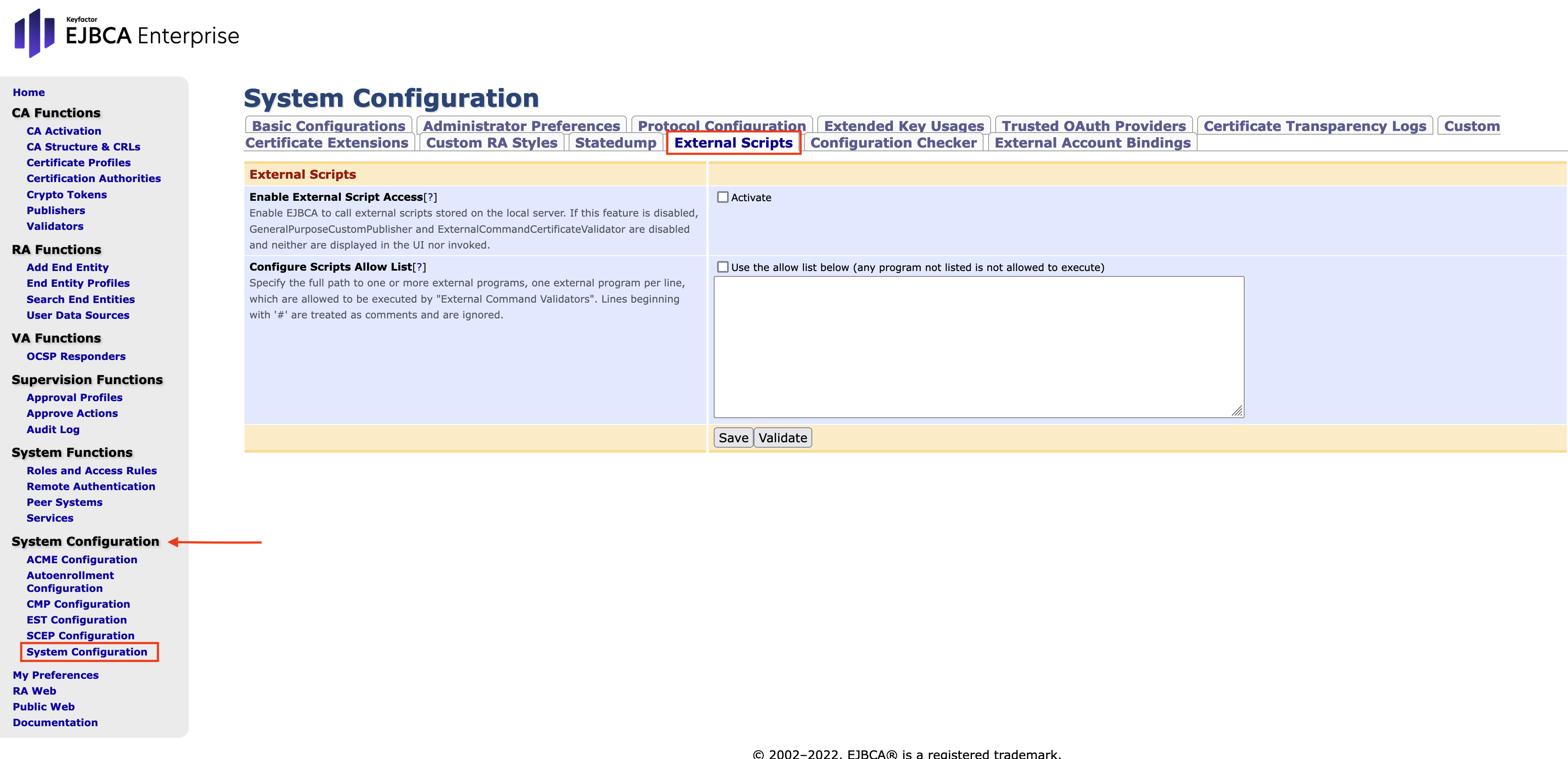
- Select Enable External Script Access by check marking Activate. Next configure the Configure Scripts Allow List according to the following example.
To ensure that the script path(s) is(are) correct and can be executed click Validate.
If no error message appears, click Save to save the configuration.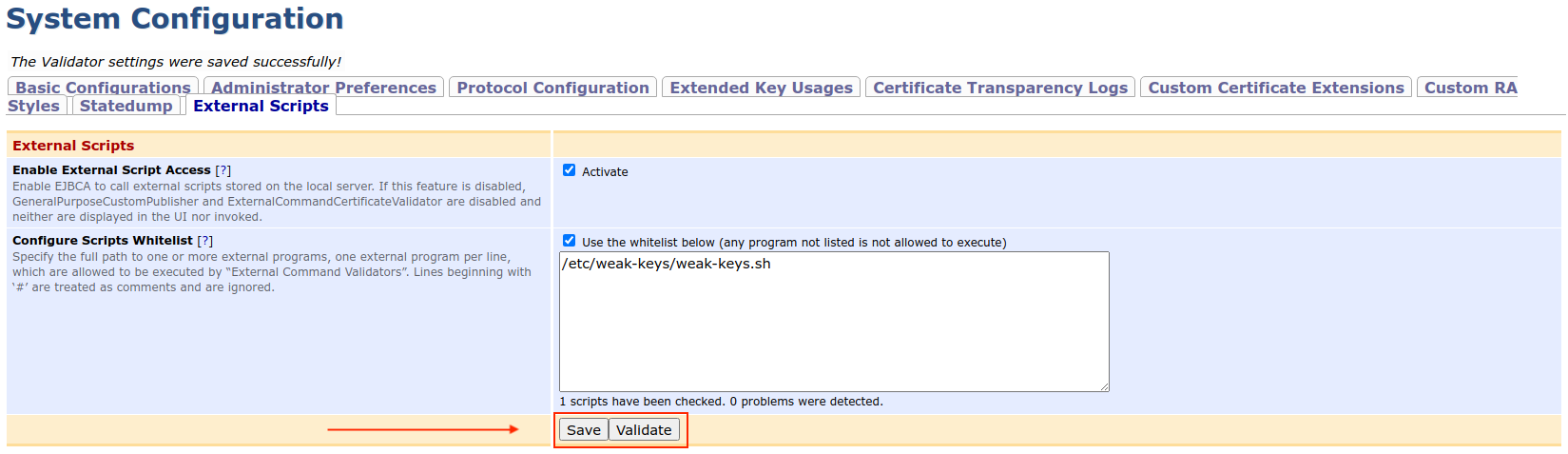
- Go to Validators and create an external command certificate validator with the following settings:
- Validator Type: External Command Certificate Validator.
- Full pathname of script:
/etc/weak-keys/weak-keys.sh. - Fail on script error code: Enabled.
- Fail on output to error out: Enabled.
- Issuance Phase: Pre-certificate Validation.
- If Validation failed: Abort certificate issuance.
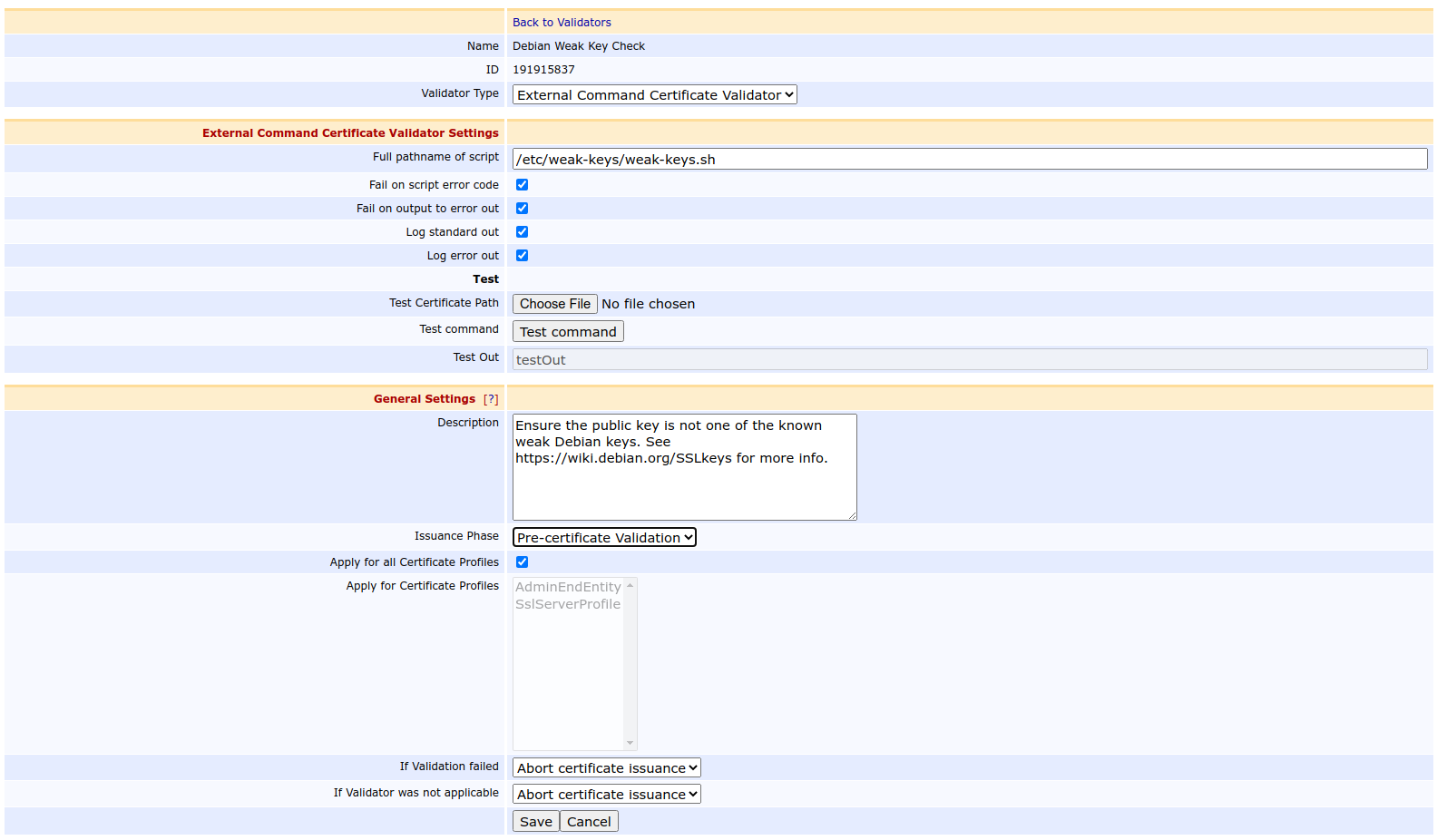
- Save the validator.
Test Validator
To test the validator:
- To test if your setup works, edit the validator created in the previous section.
Copy-paste the PEM certificate shown below and save it as a file called
test-blacklist.pem.CODE-----BEGIN CERTIFICATE----- MIIFzDCCA7SgAwIBAgIQB66bp3FYMWG3OiIbZKgNPzANBgkqhkiG9w0BAQsFADBp MQswCQYDVQQGEwJVUzEOMAwGA1UECAwFVGV4YXMxEDAOBgNVBAcMB0hvdXN0b24x GDAWBgNVBAoMD1NTTCBDb3Jwb3JhdGlvbjEeMBwGA1UEAwwVU1NMLmNvbSBSU0Eg U1NMIHN1YkNBMB4XDTIwMDMwNDAwMjczNVoXDTIwMDYwMjAwMjczNVowFzEVMBMG A1UEAwwMbGViZXJnZXIuYml6MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC AQEA+TYH57WzTTfARNmo/Vx8/TGHD774iWbQoglRH+RGeFjgjoDGongoYr9jDwwX c1QxK36fojJ5zmDxIsvn/CsIRBj1aWCWvJons4LGfvEEmnZWuyhWleLKxmTvgbFb VMyLe+3fsuKjrktntuhpK75GXkpcErKS/3aGFY3UbMDp5qmGTZfZbXUAOTBq6Uvj 6SyyeGrxrR+xRFAYCrB80ilLL2XlZ9hjqXge7qhhSxP5JYcVG4Fr8BvwhzoQ9zV1 tdEuU6E+nZlvA6m4Qm4pQByCMMRH2BoqBL4n1aR1fNu+WdWHMC3uVmq2P5WZNsYK gdccVMmlHGVfRbhC1wuCty4QUwIDAQABo4IBwDCCAbwwHwYDVR0jBBgwFoAUJhR+ 4NzXpvfi1AQn32HxwuznMsowfAYIKwYBBQUHAQEEcDBuMEoGCCsGAQUFBzAChj5o dHRwOi8vd3d3LnNzbC5jb20vcmVwb3NpdG9yeS9TU0xjb20tU3ViQ0EtU1NMLVJT QS00MDk2LVIxLmNydDAgBggrBgEFBQcwAYYUaHR0cDovL29jc3BzLnNzbC5jb20w KQYDVR0RBCIwIIIMbGViZXJnZXIuYml6ghB3d3cubGViZXJnZXIuYml6MFEGA1Ud IARKMEgwCAYGZ4EMAQIBMDwGDCsGAQQBgqkwAQMBATAsMCoGCCsGAQUFBwIBFh5o dHRwczovL3d3dy5zc2wuY29tL3JlcG9zaXRvcnkwHQYDVR0lBBYwFAYIKwYBBQUH AwIGCCsGAQUFBwMBMDoGA1UdHwQzMDEwL6AtoCuGKWh0dHA6Ly9jcmxzLnNzbC5j b20vU1NMY29tUlNBU1NMc3ViQ0EuY3JsMB0GA1UdDgQWBBTCxWii5RK9474UxOJB wLerjO2QbTAOBgNVHQ8BAf8EBAMCBaAwEwYKKwYBBAHWeQIEAwEB/wQCBQAwDQYJ KoZIhvcNAQELBQADggIBAA+2tsRNgQIQMs93Q+NNCQgzj+9avNUbT8s1hZHBkoyf 3zGgMRJgZkJ/xSEG/www/0SXKhhg8Bnp6r4PfpGn5t+T1XkZz8PhMvQlCT/zPBqC 8W7voCSMdG0klWqz2hBJ3lNzEmHLKrkp63SM17xE8rGDd0oMfjKwxZKwb7z40jrA isEUWNq6FzSPiNllNJq7IbOffEuR0/oz21a3vruPJGB0opWYPBqQcLzemnEXDPEZ R2NzfSZB5UzZfAtGLbjxYoMXK+7JLoQjsPpQWlJqGjVaHd9K+Lthg1THwYtdMekK Flobw8WirkmuKBZEmo8x6nobfFh2VaBOjA8AXRr6jEO3EjwKvCHDm32td9SkDXe7 tP4IO/gJma4dxWKV1Hyu/1/6qPUVn55XCCAiuyZcDo3A0t0nSIR8iGbyBtQb0OJH SzOyGFJ2SLM8lmyl3eJzXc5YLcJso4S2ZVgZQ9KVApitjvlBvgL7BPskNZxI/c0T ISPlOeYtD0O/rxQuQakWOqal9hk+l4Rrd7O+UguXijB92h/40AfLsaLUCRxBZgXA tSMLQNleqFMpxIwA93Ybm+iT3FmBqqDNZ2cJ77NTVL3sKeF77b0Xdppn+93Rz51z K9UmDRX973f9qi9p/1PbofcOBKZnMaFp7O7kXfdBRaXzslhSLDE2/X+Kx7SVe0GV -----END CERTIFICATE-----Upload test-blacklist.pem and click Test command.
Expected log output in the syslog of
cos-ejbca:CODE> tail -f /var/log/sys.log Jun 24 17:29:16 cos-ejbca root: Known weak Debian key was detected in certificate. Jun 24 17:29:16 cos-ejbca root: You can inspect the base64 encoded certificate shown below: Jun 24 17:29:16 cos-ejbca root: <base64 encoded certificate>Expected output of the WildFly log file:
CODE17:29:16,247 INFO [org.cesecore.keys.validation.ExternalCommandCertificateValidator] (ajp--0.0.0.0-8009-4) Test external command certificate validator Debian Weak Key Check 17:29:16,295 INFO [org.cesecore.keys.validation.ExternalCommandCertificateValidator] (ajp--0.0.0.0-8009-4) Could not call external command '/etc/weak-keys/weak-keys.sh' with arguments [/tmp/org.cesecore.keys.validation.ExternalCommandCertificateValidator-1593012556248505049562192935548.tmp] sucessfully: Detected errors while running the external application /etc/weak-keys/weak-keys.sh.The message Could not call external command means that the script returned a non-zero exit status, which is the expected behavior when the certificate contains a weak Debian key.
Enable Validator for a CA
To enable the validator for a CA:
- Go to Certification Authorities and select the CA for which you want to enable the validator.
- In the Other Data section, select the validator you just created and click Save. The validator will now run every time you issue a certificate from this CA.
Maintenance Notes
The script and the blacklists will be wiped after a factory reset of the appliance. If you perform a factory reset and restore a backup, you must add the script and the blacklists again. If you forget to do so, the validation will fail.
If you have a CA cluster, you need to add the script and the blacklists to all nodes in the cluster. The files in /etc are not automatically synchronized between the nodes.
.png)