ICAO Upload LDAP Configuration
The ICAO Upload LDAP page allows Administrators to configure the connection to ICAO Upload PKD.
This following example page displays configuration values for the NPKD development environment connecting to the ICAO Pre-production Upload PKD.
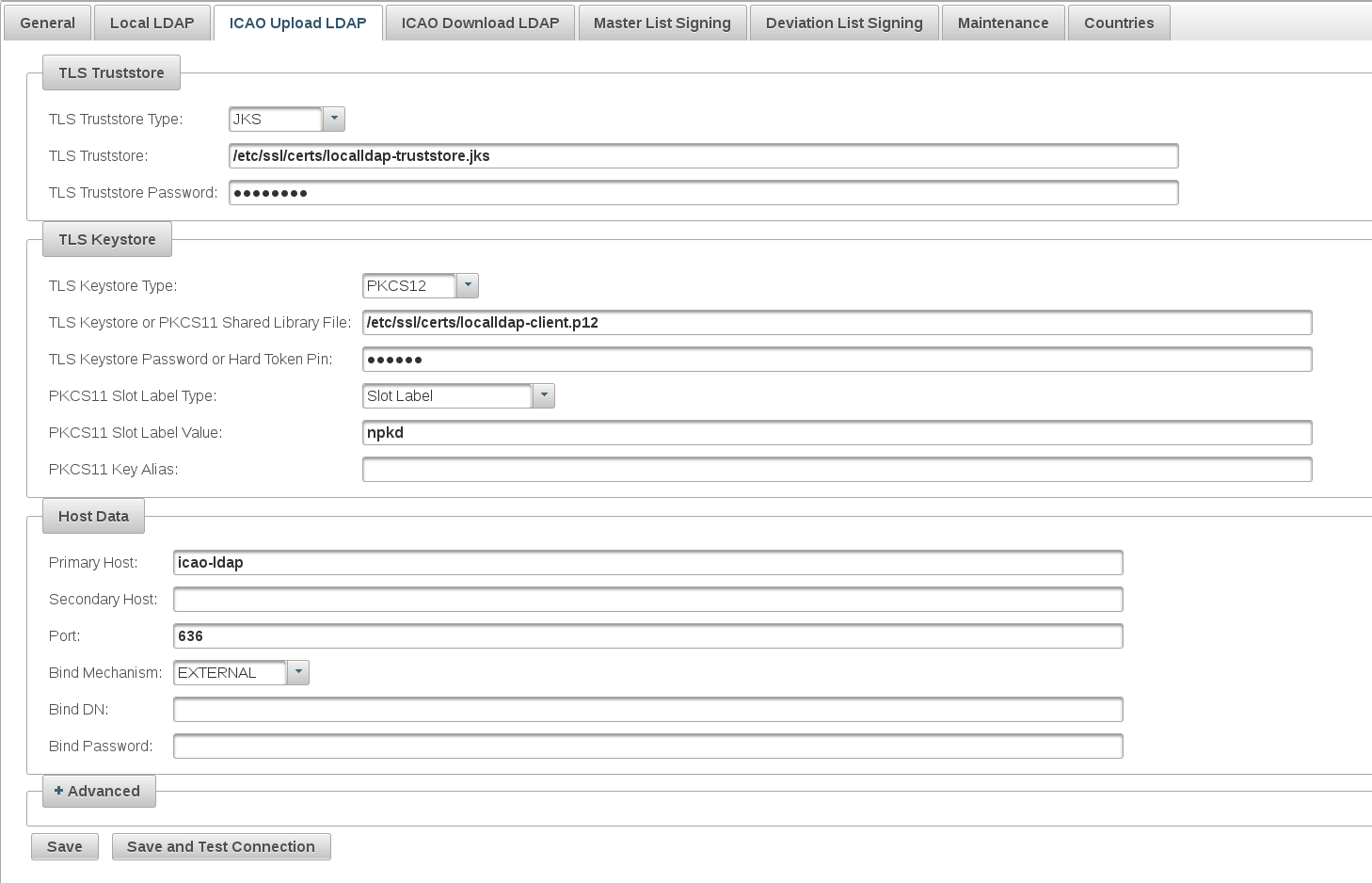
- TLS Truststore Type: The type of the truststore. If set to "PKCS12" or "JKS", the truststore will be loaded from the file specified in the TLS Truststore field.
- TLS Truststore: The full path of the truststore file that is going to contain the CA certificate chains trusted.
- TLS Truststore Password: The password to be used for opening the protected truststore file specified in the TLS Truststore field.
- TLS Keystore Type: The type of keystore. If set to "PKCS12" or "JKS", the keystore will be loaded from the file specified using in the field TLS Keystore or PKCS11 Shared Library File. If set to "PKCS11", the keys stored in the HSM configured with the property TLS Keystore or PKCS11 Shared Library File are used.
- TLS Keystore or PKCS11 Shared Library File: The full path of the keystore file to be used as client for establishing TLS to ICAO Upload LDAP, or the path to the shared library file (.so file) specific for the installed HSM; or a SUN configuration file.
- TLS Keystore Password or Hard Token Pin: The password to be used for opening the protected keystore file, or the pin to be used for the keys stored on the HSM
- PKCS11 Shared Library File: The path to the shared library file (.so file) specific for the installed HSM, or a SUN configuration file.
- PKCS11 Slot Label Type: The method used to identify the HSM's slot containing the key to be used, or "SUN Configuration File" if a SUN configuration file is specified in the TLS Keystore or PKCS11 Shared Library File field. Used only if TLS Keystore type is set to "PKCS11".
- PKCS11 Slot Label Value: The HSM's slot containing the key to be used. Used only if TLS Keystore type is set to "PKCS11"
- PKCS11 Key Alias:
- Primary Host: The primary host of the ICAO Upload LDAP.
- Secondary Host: The secondary host of the ICAO Upload LDAP. Used only if the host specified as the Primary Host is failing.
- Port: The port of the ICAO Upload LDAP. The same value is used for both Primary Host and Secondary Host.
- Download Bind Mechanism: The LDAP binding mechanism to be used for the connection to ICAO Upload LDAP. Can be "EXTERNAL" or "SIMPLE". If set to "SIMPLE", the binding will use the values specified as Bind DN and Bind Password. The ICAO Upload currently only supports EXTERNAL binding to ICAO Upload LDAP.
- Bind DN: The Bind DN to be used for LDAP binding if Download Bind Mechanism is set to "SIMPLE".
- Bind Password: The password to be used for LDAP binding if Download Bind Mechanism is set to "SIMPLE".
The following advanced options are displayed by selecting Advanced button. The values represent the DN values standardized by the ICAO PKD specification and it is thus not recommended to edit these values:
- Base DN: The base DN with the default value "dc=data,dc=upload,dc=pkd,dc=icao,dc=int".
- Upload Master List DN: The upload master list DN with the default value "o=ml,c=<c>,dc=data,dc=upload,dc=pkd,dc=icao,dc=int".
- Upload Deviation List DN: The upload deviation list DN with the default value "o=dl,c=<c>,dc=data,dc=upload,dc=pkd,dc=icao,dc=int".
- Upload DS Certificate DN: The upload certificate DN with the default value "o=dsc,c=<c>,dc=data,dc=upload,dc=pkd,dc=icao,dc=int".
- Upload CRL DN: The upload CRL DN with the default value "o=crl,c=<c>,dc=data,dc=upload,dc=pkd,dc=icao,dc=int".
- Upload Registry DN: The upload registry DN with the default value "o=<o>,c=<c>,dc=data,dc=upload,dc=pkd,dc=icao,dc=int".
Click Save to save all configuration options on the page.
To test the configured connection, click Save and Test Connection. The connection and binding are then tested against the ICAO Upload LDAP when the configuration options are stored.
When connection to the actual ICAO (Production or Staging), the default LDAP DNs work fine
.png)