Authenticode Code Signing
Microsoft Authenticode is a digital signature format used to determine the origin and integrity of software binaries. Using Authenticode, the signature is embedded within Portable Executable (PE) files, (typically file types like .exe, .dll, .sys, .ocx, and so on), Windows Installer packages (.msi), Windows PowerShell scripts (.ps1, .psm1, and .psd1), Microsoft Catalog files (.cat), or Cabinet archives (.cab). For more information, refer to the Microsoft documentation on Windows Authenticode Portable Executable Signature Format.
The SignServer Authenticode signer is configured just like any other signer in SignServer and the only special requirement for this signer is to use a code signing certificate.
If your organization already has a Certificate Authority, such as Keyfactor EJBCA, configured to be trusted by your users, you can use that CA to issue the certificate. Otherwise, you could buy a certificate from one of the CAs already trusted by default in Windows.
For testing purposes, and also for test environments in general, you can issue the certificate yourself. Remember to have the extended key usage Code Signing set and to install the CA certificate in your test environment.
The following sections describe the steps required to configure and sign using the SignServer MS Authenticode signer MS Auth Code Signer:
Add MS Authenticode Signer
To add and configure the MS Authenticode signer, do the following:
Go to the SignServer Admin Web Workers page and click Add to a new worker.
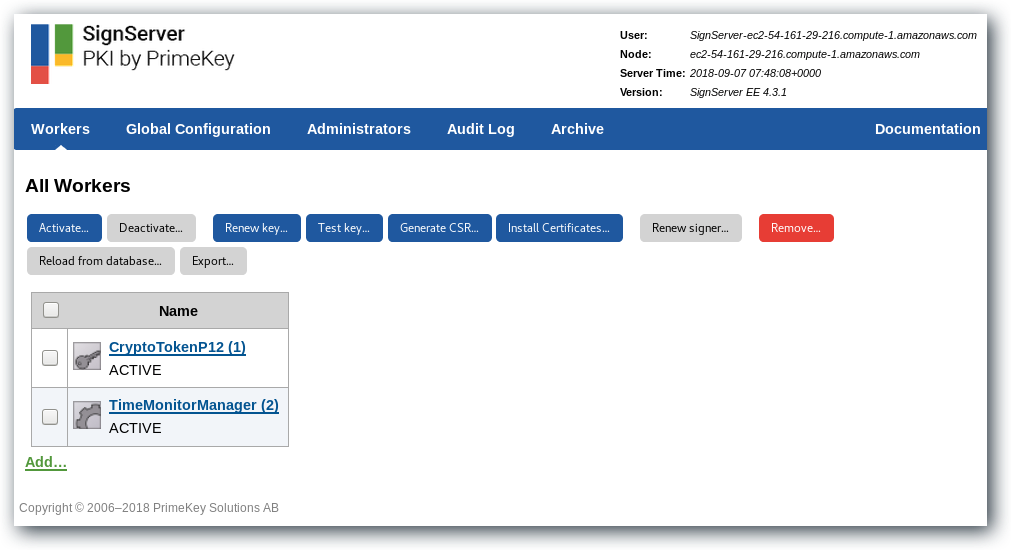
Add MS Authenticode Signer
On the Add Worker / Load Template page, choose the method From Template.
In the Load From Template list menu, select ms_authcode_signer.properties and click Next.
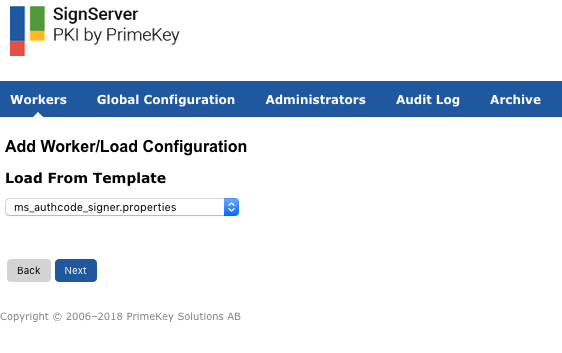
Load from Template
On the Configuration page, click Apply to load the sample MS Authenticode signer configuration.
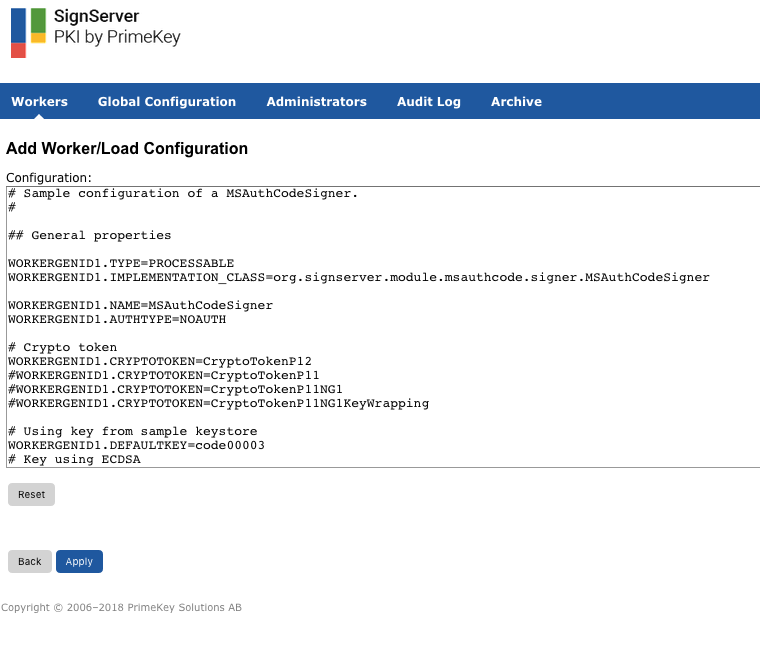
Add MSAuthCodeSigner Configuration
The MSAuthCodeSigner is now added to the listed workers in state ACTIVE.
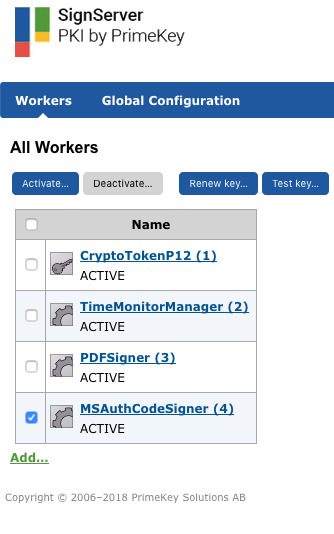
Submit and Sign File Using MS Authenticode Signer
The following describes how to submit and sign an executable file with the MS Authenticode signer either using the SignServer Client Web or the SignServer SignClient:
You can use any unsigned executable file or use the provided example file HelloPE.exe.
Sign Using Client Web
To download an example executable file and then submit and sign the EXE using the Client Web, do the following:
Download the HelloPE.exe to test EXE Signing.
Go to the SignServer Client Web page on https://<yourawsinstancepublicdns>/signserver/clientweb/.
Under File Upload, specify MSAuthCodeSigner as the Worker name.
Click Browse next to File, select HelloPE.exe and click Submit.
You will be prompted to save the signed EXE file HelloPE.exe.
Sign Using SignClient
To download an example executable file and then submit and sign the file using the SignServer SignClient, do the following. Note that the SignClient requires Java.
Download the SignServer SignClient from the location: https://<yourawsinsancepublicdns>/signserver/clientcli-dist/signserver-clientcli.zip.
Unzip signserver-clientcli.zip to the
signserver-clientclidirectory.Copy HelloPE.exe to the bin directory inside the
signserver-clientclidirectory.Open a command (cmd) window if on a Windows system, or a terminal on Linux or Mac and change directory (cd) to the
bindirectory.Sign HelloPE.exe using SignClient:
If you are on a Windows system, use the following command:
CODE# signclient.cmd signdocument -host yourawsinsancepublicdns -port 80 -workername MSAuthCodeSigner -infile HelloPE.exe -outfile HelloPESigned.exeIf you are on a Linux or Mac system, use the following command:
CODE./signclient signdocument -host yourawsinsancepublicdns -port 80 -workername MSAuthCodeSigner -infile HelloPE.exe -outfile HelloPESigned.exe
Verify the Signature
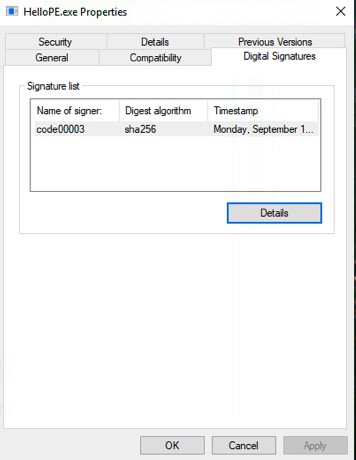
Verify that the file is signed by inspecting the signature attached to HelloPE.exe in the Windows environment.
To view the signature details, do the following:
Right-click the file and select Properties.
Click the Digital Signatures tab.
Select the signature in the Signature list and click Details.
.png)