CrowdStrike Host Scan Guide
This guide provides end-to-end instructions for integrating host scan with CrowdStrike Falcon platform. It covers configuring the EDR ID, setting up host groups, and automating sensor package deployment using CrowdStrike Fusion workflows.
Set up EDR ID
An EDR ID is used by the Unified Sensor to obtain an access token for communicating with the AgileSec platform. This process is automatic: when the Unified Sensor runs, it presents the configured EDR ID to the Ingestion Service, which returns a Remote Sensor Token. The Unified Sensor stores this token locally and uses it for subsequent authenticated communication with the Ingestion Service.
EDR IDs provide an implicit trust mechanism that allows approved endpoints to obtain a Remote Sensor Token without embedding long-lived credentials on the host. EDR IDs can be revoked at any time to immediately block token issuance for endpoints using that ID.
You can generate multiple EDR IDs and assign them to specific deployments (for example, by environment, business unit, or endpoint group) rather than using a single EDR ID across all endpoints. This segmented approach is recommended because it limits blast radius and simplifies revocation and rotation when access needs to be restricted.
Generate an EDR ID
Step 1: Log in to the AgileSec Platform UI, navigate to EDR Management, then click Create EDR ID.
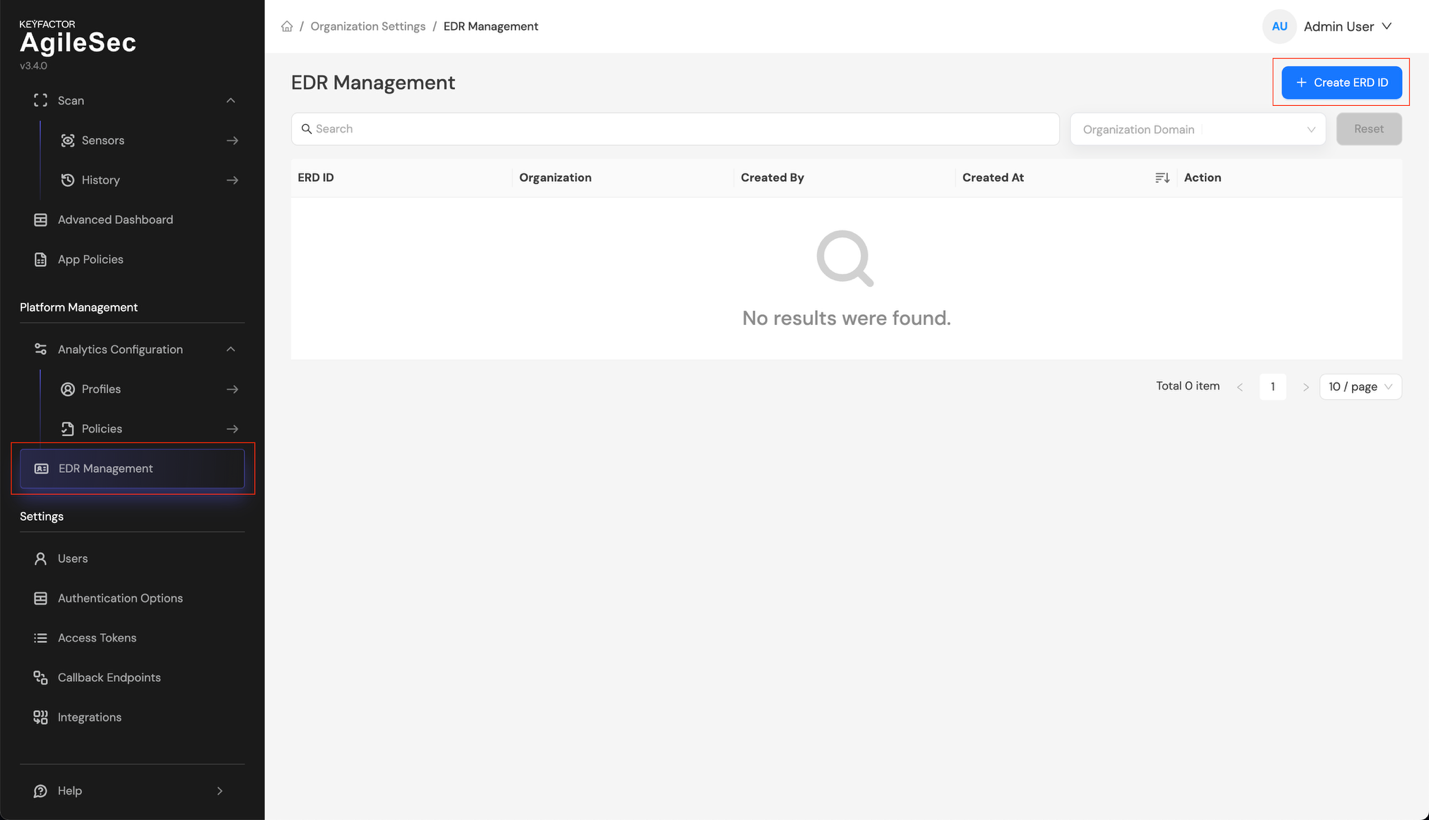
Step 2: In the Create EDR ID dialog, select your organization and click Generate.
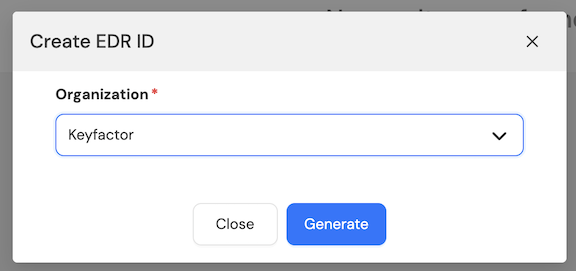
Step 3: Copy the newly generated EDR ID by clicking the copy icon before the EDR ID.
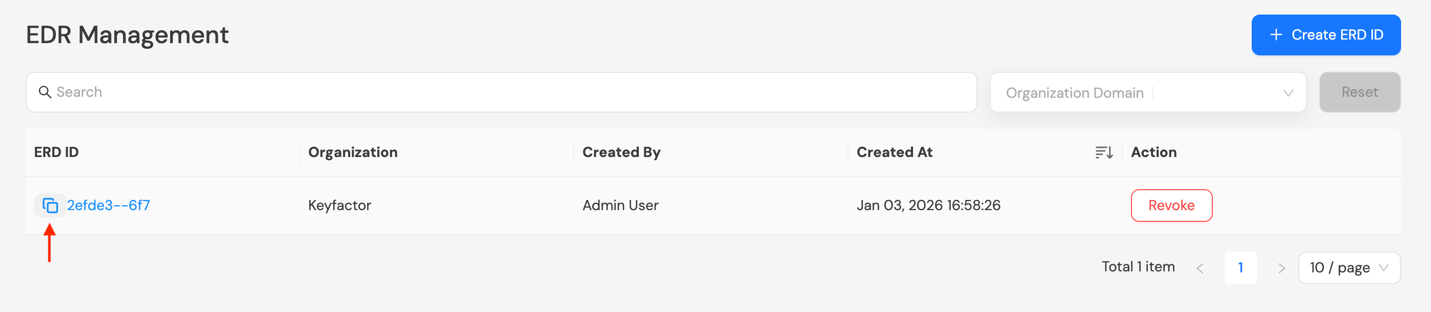
Set up Host Group
While this step is optional, it is recommended to create host groups to organize your hosts. This allows you to selectively target only the hosts where you want to run scans when configuring workflows, rather than scanning all hosts in your environment.
Add your Linux hosts in CrowdStrike
Add your Window hosts in CrowdStrike
Add your Mac hosts in CrowdStrike
Add your hosts to a host group
Upload Sensor Package
Download the latest sensor package from Keyfactor download portal
Note: There are separate .zip files for Linux, Windows and Mac
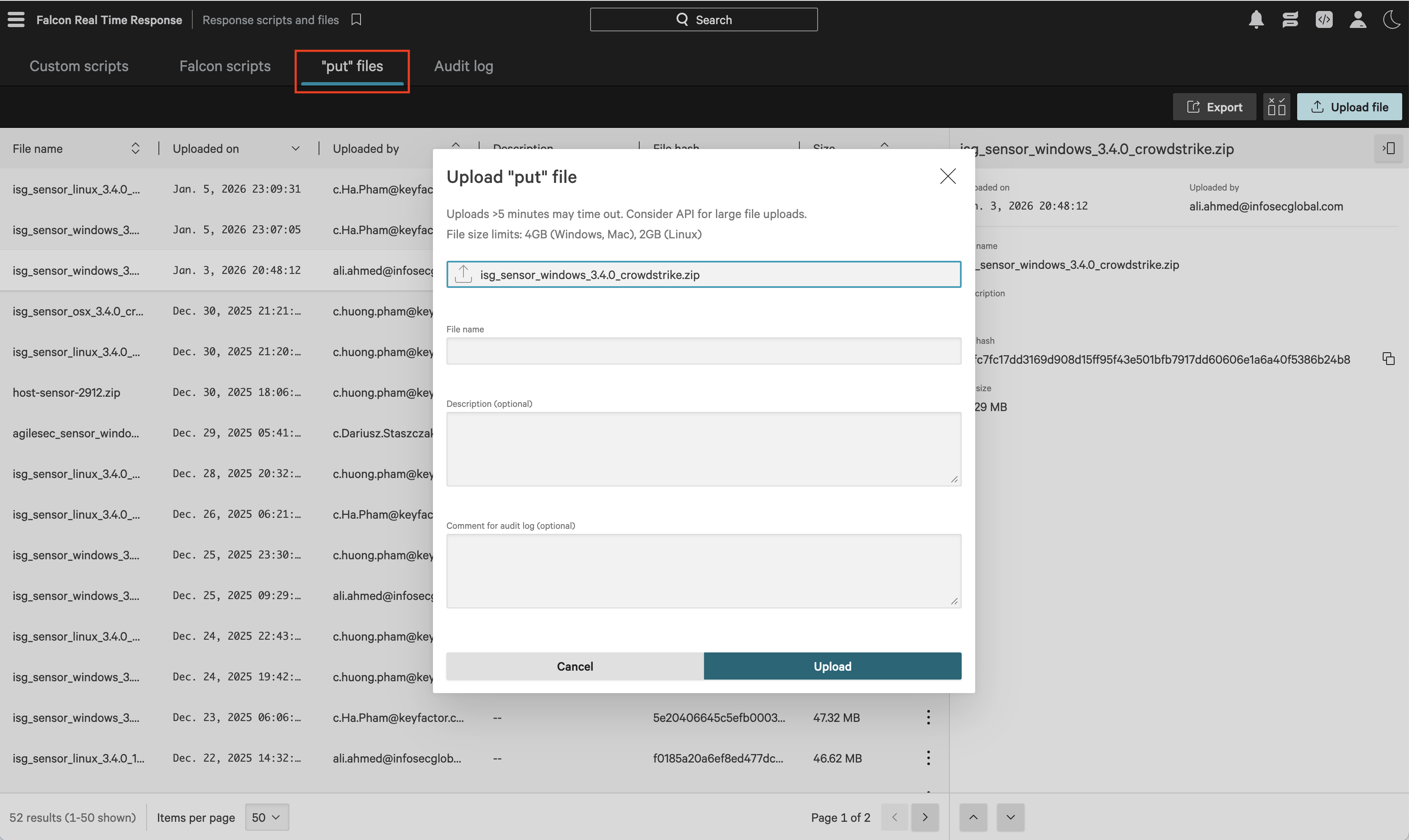
Log in to CrowdStrike and navigate to Host setup and management → Response scripts and files.
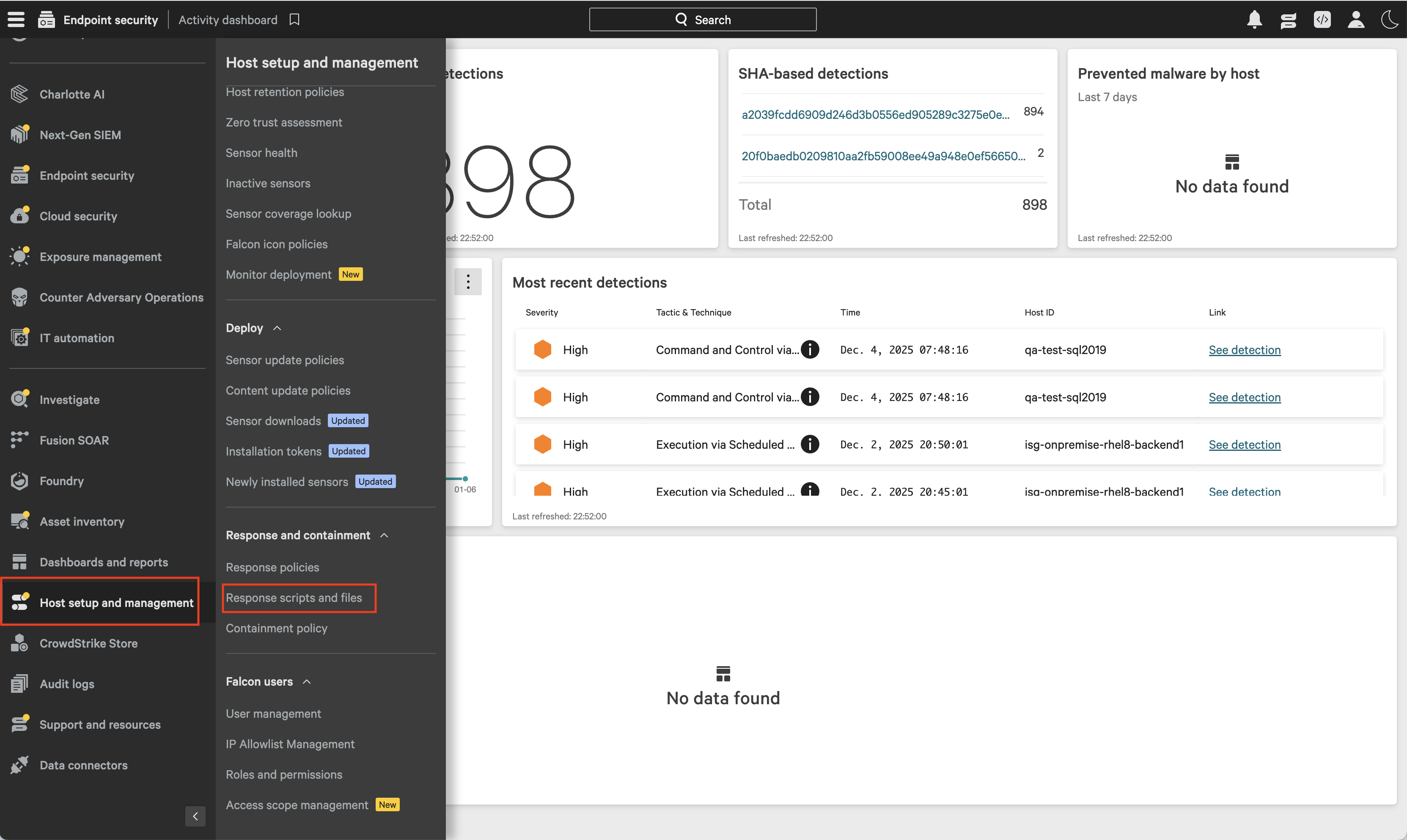
Select the "put" files tab and click Upload file. In the dialog, choose
isg_sensor_<platform>_3.4.0_crowdstrike.zip, then click UploadFor Linux:
isg_sensor_linux_3.4.0_crowdstrike.zipFor Windows:
isg_sensor_windows_3.4.0_crowdstrike.zipFor Mac:
isg_sensor_osx_3.4.0_crowdstrike.zip
Create Scripts
Create the following scripts, which will be required later for setting up the workflow.
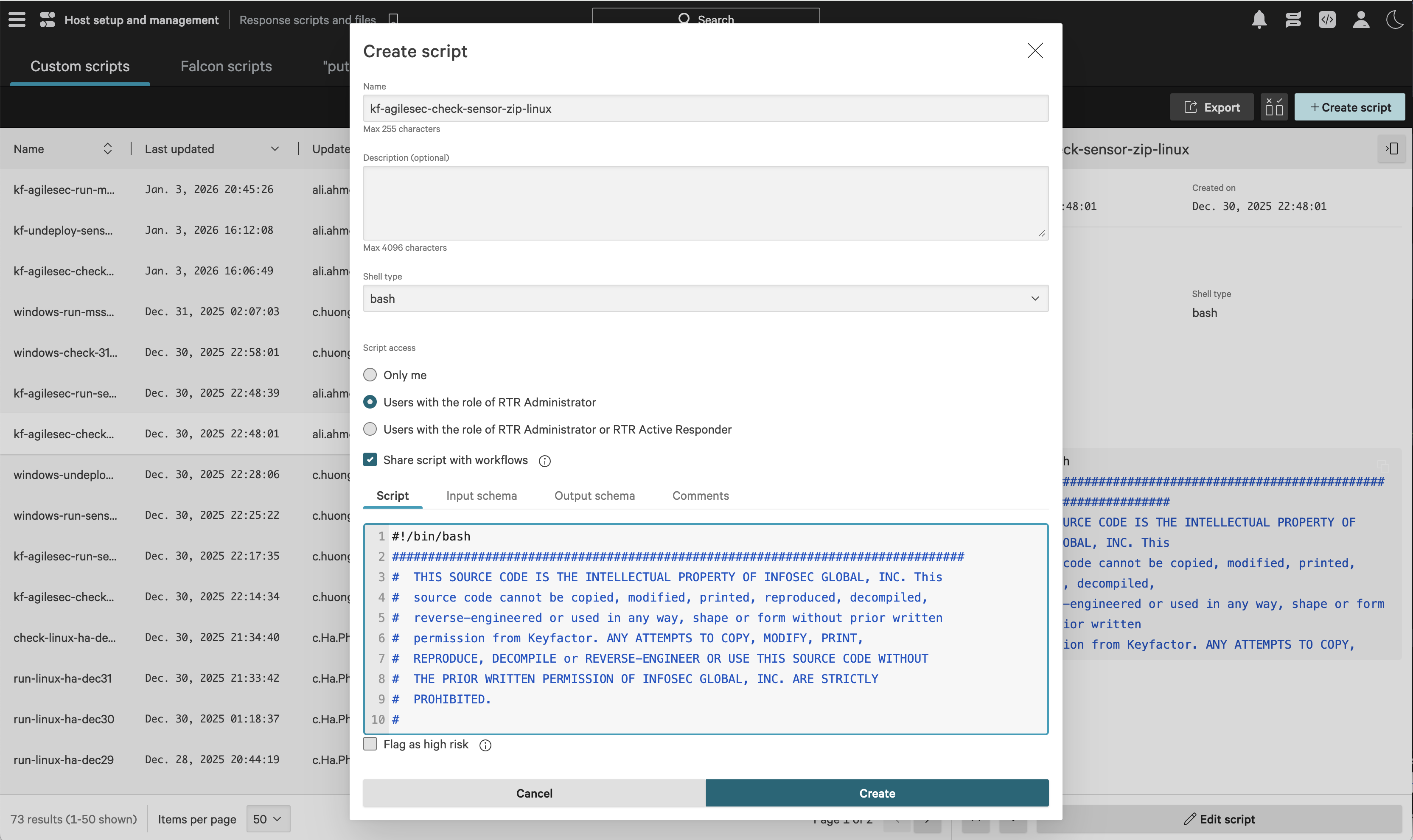
Check Sensor Zip Script
On the Response scripts and files screen, select the Custom scripts tab, then click Create script.
In the Create script dialog, complete the following fields:
Name:
For Linux:
kf-agilesec-check-sensor-zip-linuxFor Windows:
kf-agilesec-check-sensor-zip-windowsFor Mac:
kf-agilesec-check-sensor-zip-osx
Shell type:
bashFor Linux:
bashFor Windows:
PowerShellFor Mac:
bash
Script access: Users with the role of RTR Administrator
Share script with workflows: Enabled
Script: Copy the contents of file:
For Linux:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-zip-linux.shfrom the extracted ZIPFor Windows:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-zip-windows.ps1from the extracted ZIPFor Mac:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-zip-osx.shfrom the extracted ZIP
Input schema: Copy the contents of file:
For Linux:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-input-linux.jsonfrom the extracted ZIPFor Windows:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-input-windows.jsonfrom the extracted ZIPFor Mac:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-input-osx.jsonfrom the extracted ZIP
Output schema: Copy the contents of
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-check-sensor-output.jsonfrom the extracted ZIP
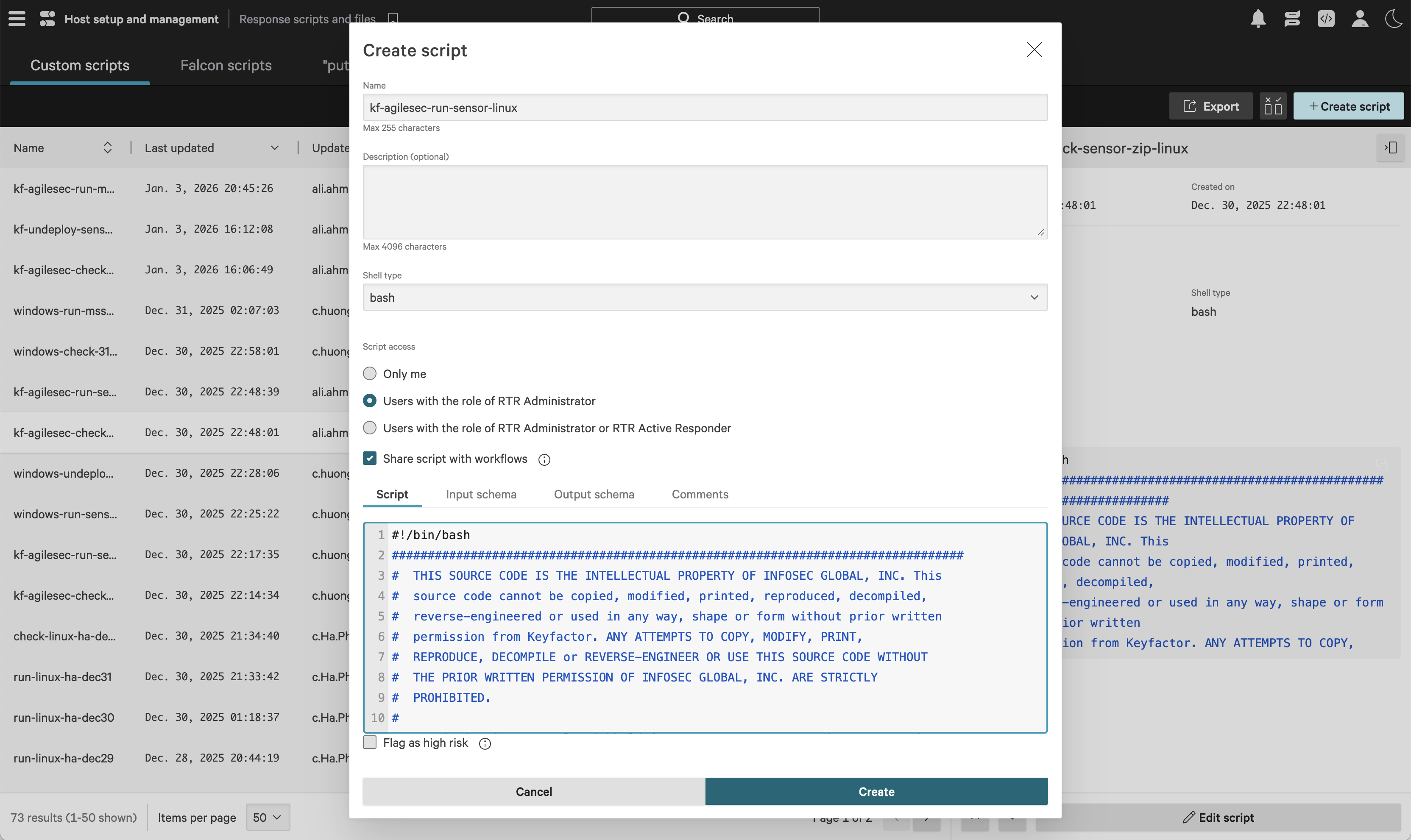
Run Sensor Script
On the Response scripts and files screen, select the Custom scripts tab, then click Create script.
In the Create script dialog, complete the following fields:
Name:
For Linux:
kf-agilesec-run-sensor-linuxFor Windows:
kf-agilesec-run-sensor-windowsFor Mac:
kf-agilesec-run-sensor-osx
Shell type:
For Linux:
bashFor Windows:
PowerShellFor Mac:
bash
Script access: Users with the role of RTR Administrator
Share script with workflows: Enabled
Script: Copy the contents of file
For Linux:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-run-sensor-linux.shfrom the extracted ZIP.For Windows:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-run-sensor-windows.ps1from the extracted ZIP.For Mac:
isg_agilescan_linux_sensor\crowdstrike\scripts\kf-agilesec-run-sensor-osx.shfrom the extracted ZIP.
Input schema: Copy the contents of file:
For Linux:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-run-sensor-input-linux.jsonfrom the extracted ZIP.For Windows:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-run-sensor-input-windows.jsonfrom the extracted ZIP.For Mac:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-run-sensor-input-osx.jsonfrom the extracted ZIP.
Undeploy Sensor Script
On the Response scripts and files screen, select the Custom scripts tab, then click Create script.
In the Create script dialog, complete the following fields:
Name:
For Linux:
kf-agilesec-undeploy-sensor-linuxFor Windows:
kf-agilesec-undeploy-sensor-windowsFor Mac:
kf-agilesec-undeploy-sensor-mac
Shell type:
bashFor Linux:
bashFor Windows:
PowerShellFor Mac:
bash
Script access: Users with the role of RTR Administrator
Share script with workflows: Selected
Script: Copy the contents of file:
For Linux:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-undeploy-sensor-linux.sh from the extracted ZIP.For Windows:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-undeploy-sensor-windows.ps1 from the extracted ZIP.For Mac:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-undeploy-sensor-osx.sh from the extracted ZIP.
Input schema: Copy the contents of file:
For Linux:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-undeploy-sensor-input-linux.json from the extracted ZIP.For Windows:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-undeploy-sensor-input-windows.json from the extracted ZIP.For Mac:
isg_agilescan_windows_sensor\crowdstrike\scripts\kf-agilesec-undeploy-sensor-input-osx.json from the extracted ZIP.
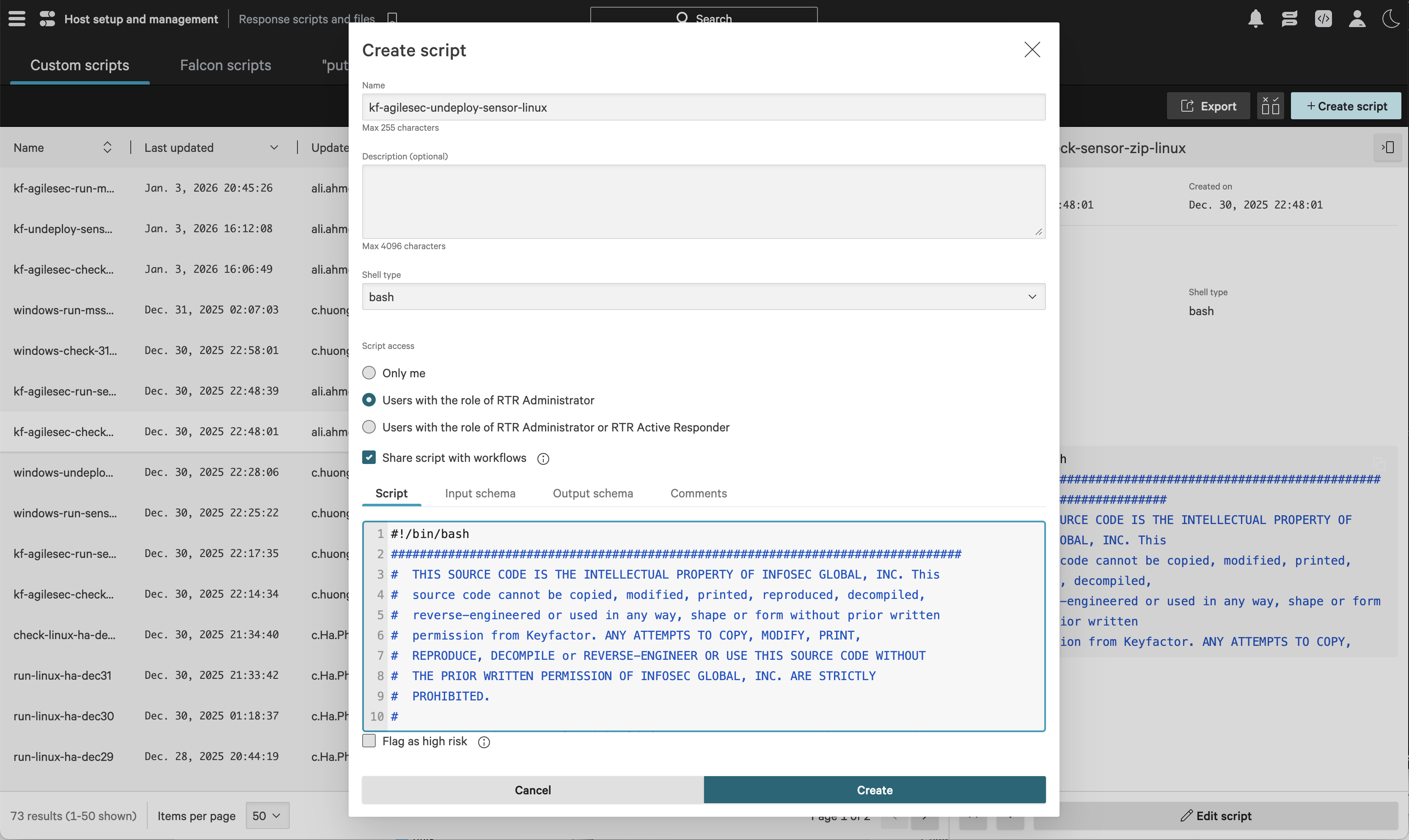
Note: For windows select Shell type as PowerShell
Workflow To Run Host Scan Sensor
Use this workflow to scan and endpoint host using Keyfactor Agilesec Host Scan sensor.
Follow these steps to create the workflow:
Navigate to Fusion SOAR -> Workflows, then click Create workflow to open then CrowdStrike workflow builder interface.
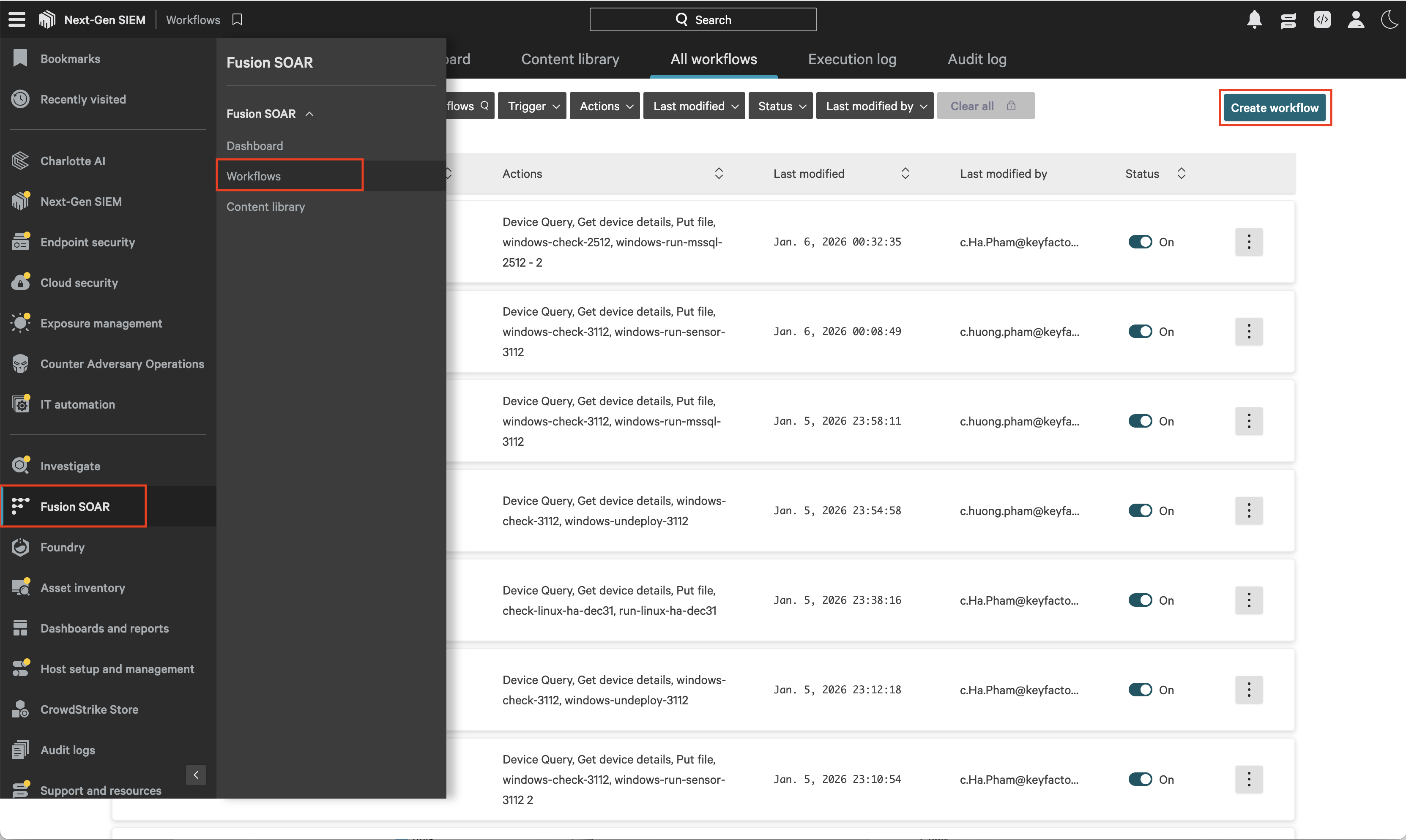
In the Create workflow dialog, select Create workflow from scratch.
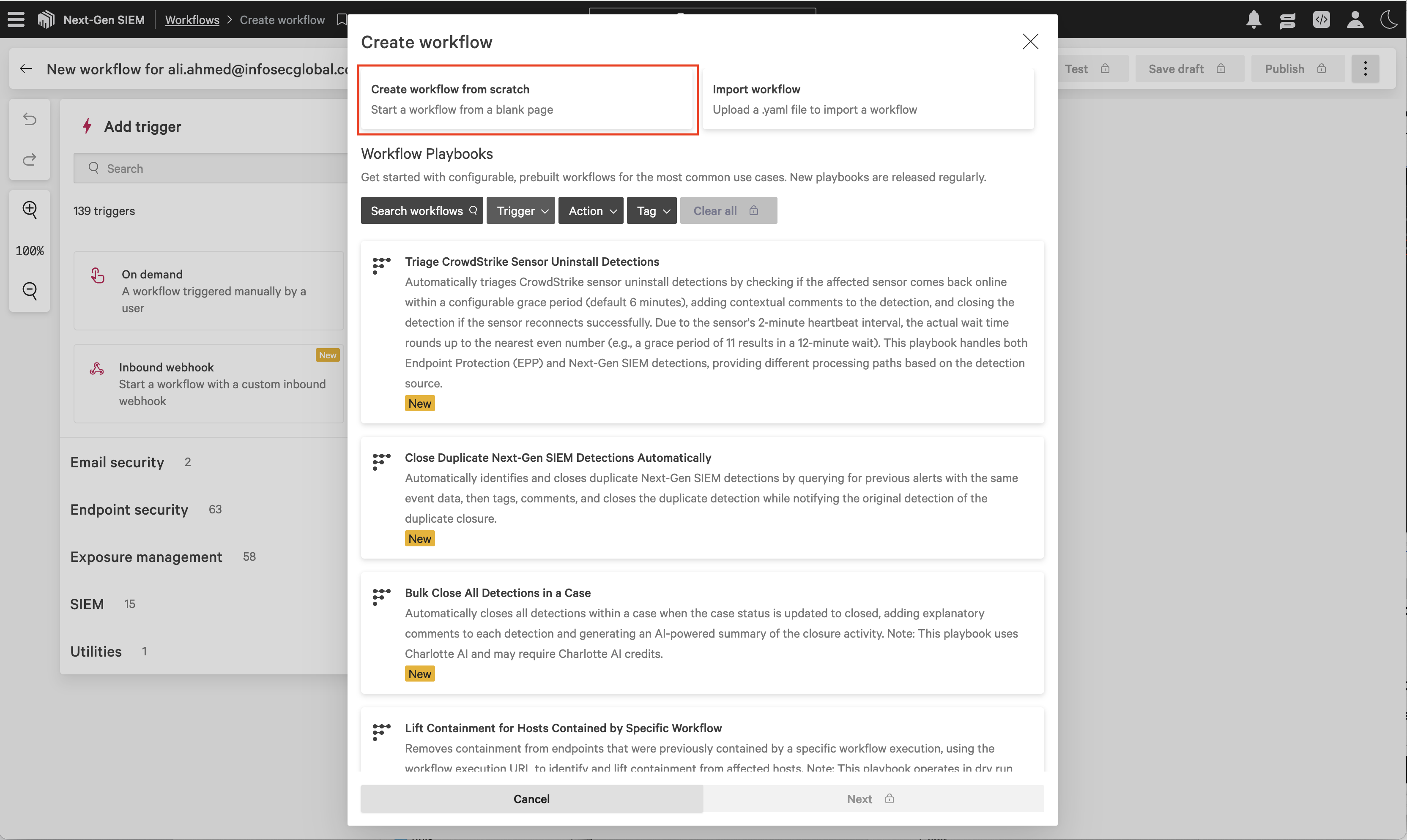
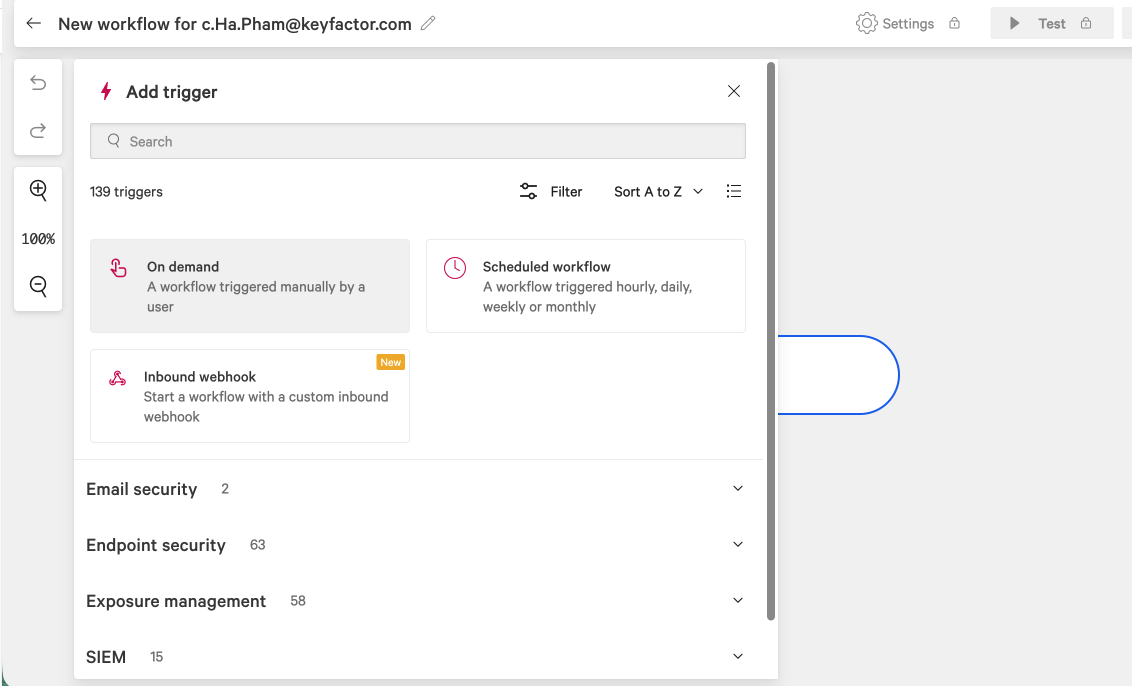
In the Add trigger dialog, select Scheduled workflow and configure the execution schedule.
On-demand: The workflow is triggered manually by the user.
Scheduled: The workflow is triggered automatically at the selected time.
On the workflow builder, click Action.
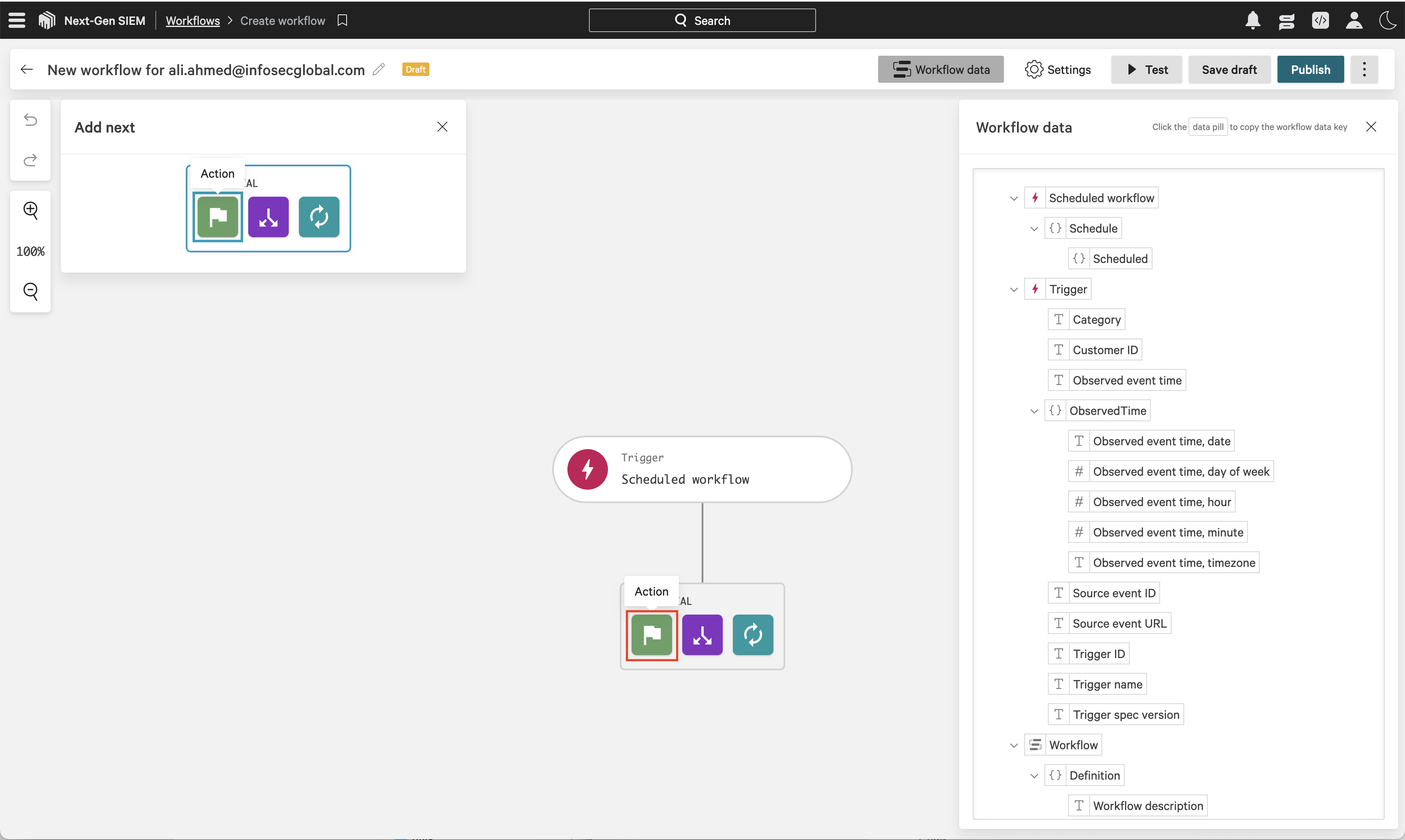
In the Add action dialog, search for and select Device Query.
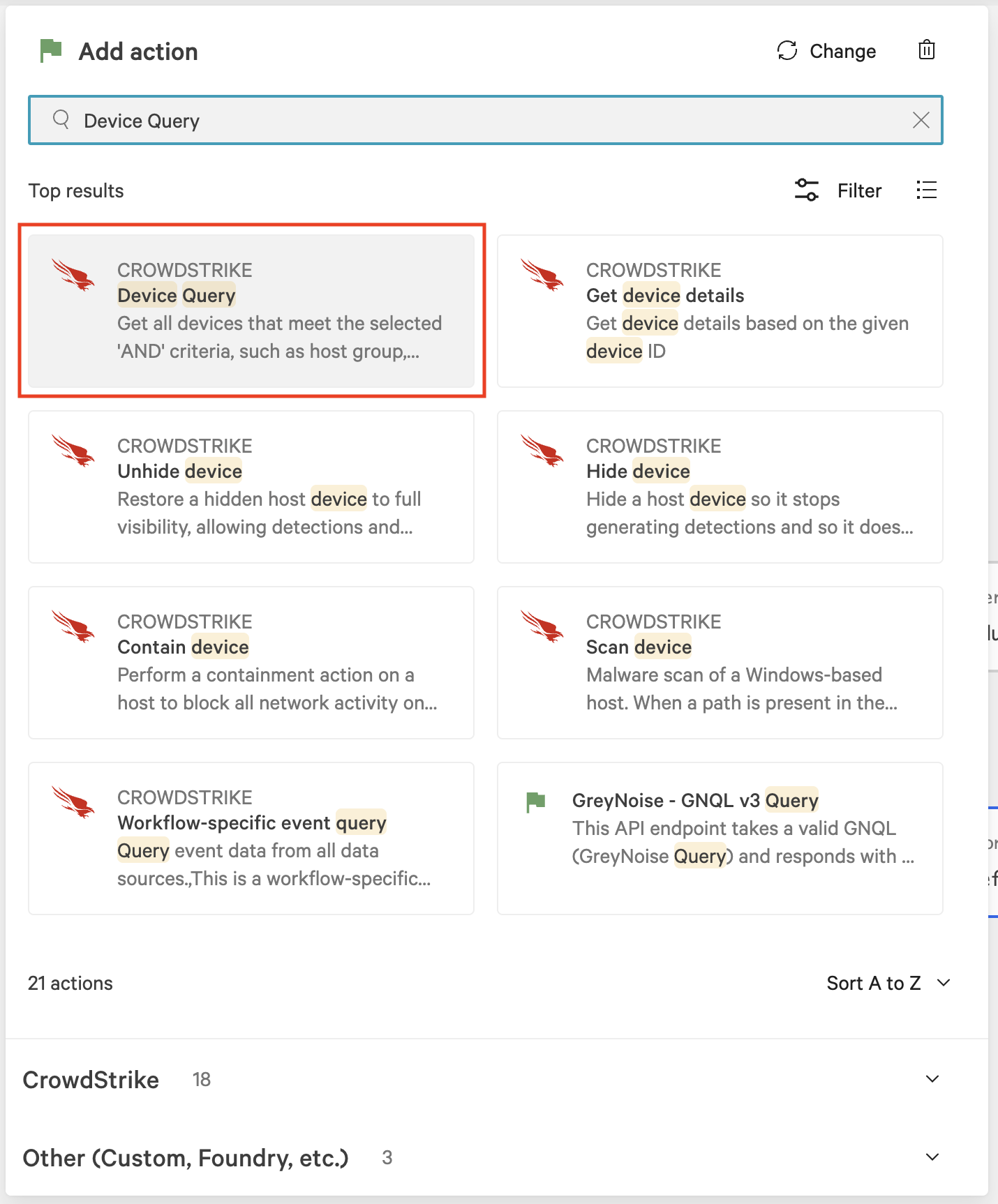
In the Device Query dialog, configure fields specific to your environment to select the devices where the host scan sensor should run. At a minimum, set Device status and either Host group or Host names:
Device status: all
Host group: Select the host group created earlier. (The workflow will be triggered to run on all target hosts within this group)
Host names: The workflow will be triggered to run on specified host names.
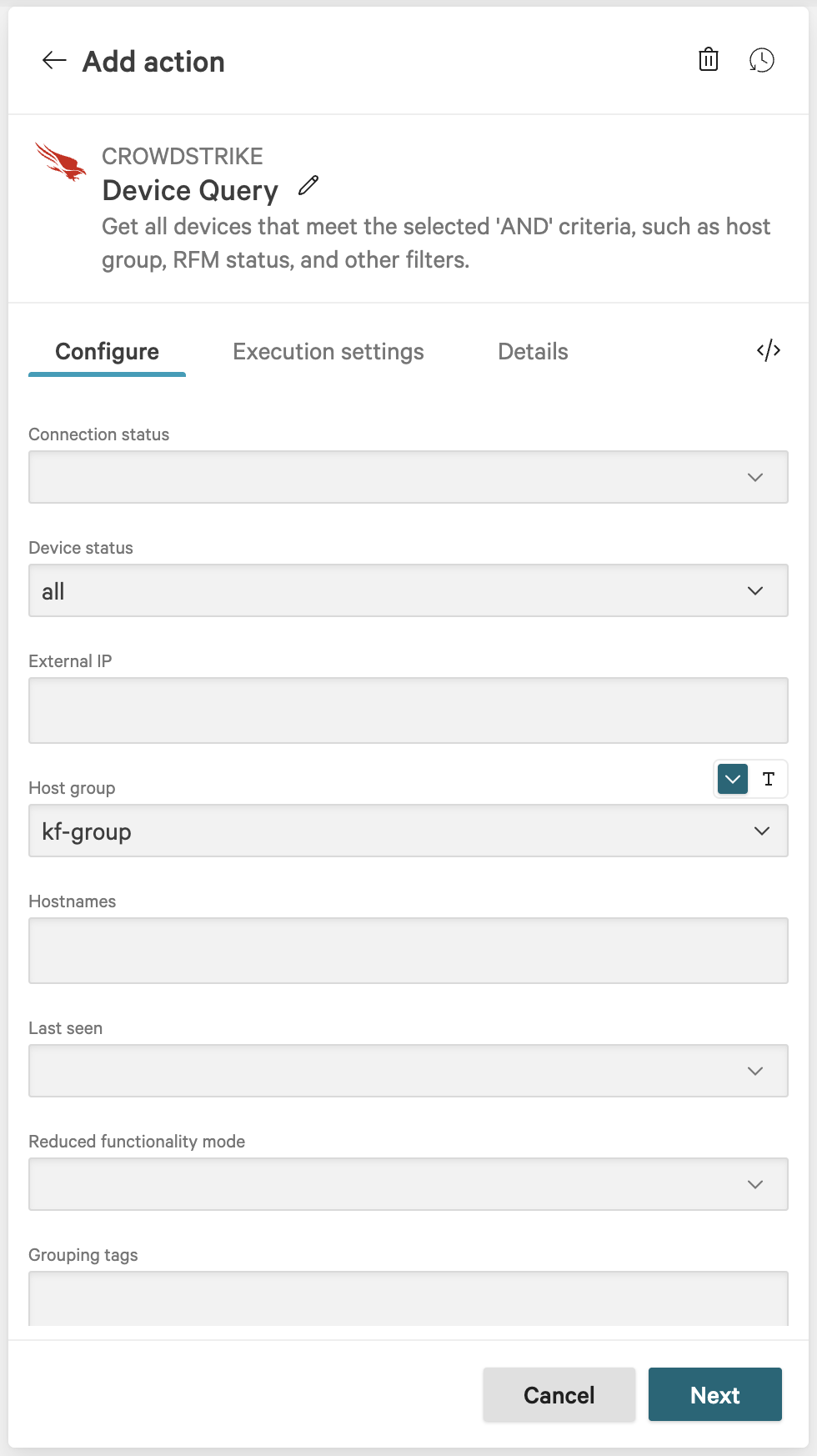
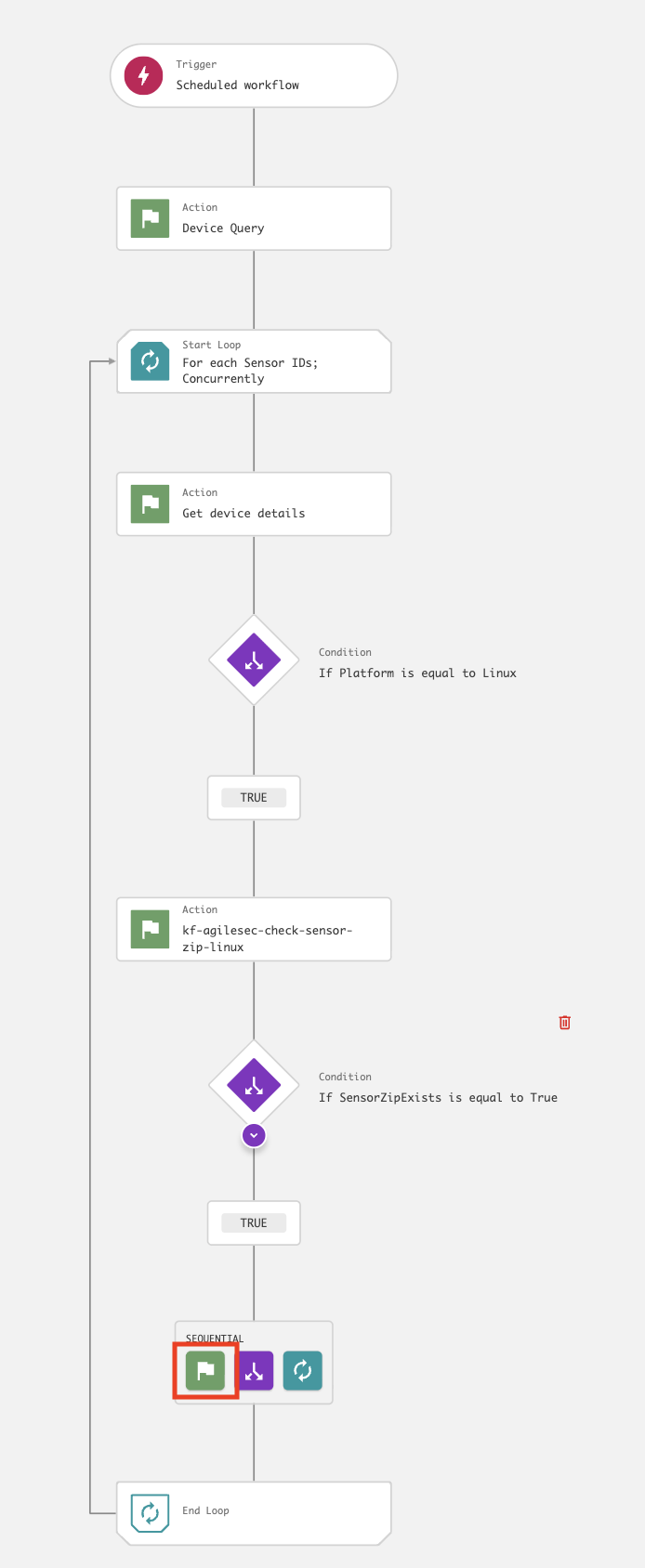
On the workflow builder, add a Loop after Device query.
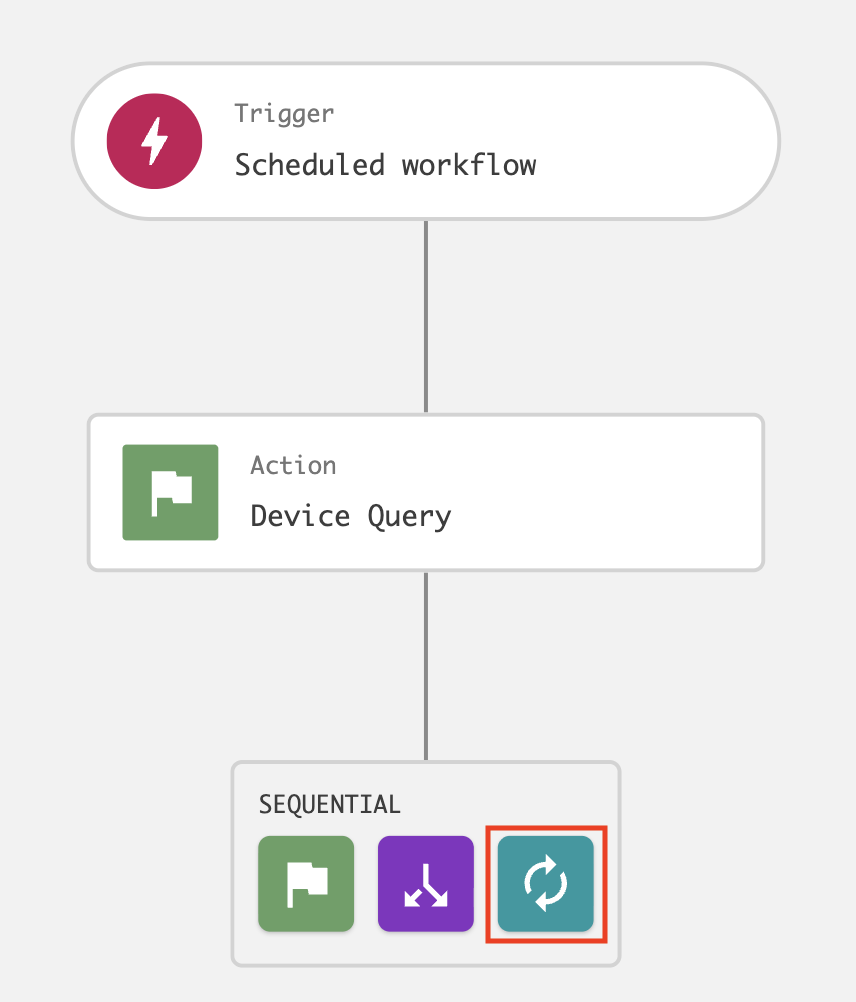
In the Start loop dialog, enter the following and click Next:
Loop type: For each
Loop source: Sensor IDs
Processing order: At the same time/concurrently
Continue workflow on loop iteration failure: Enabled
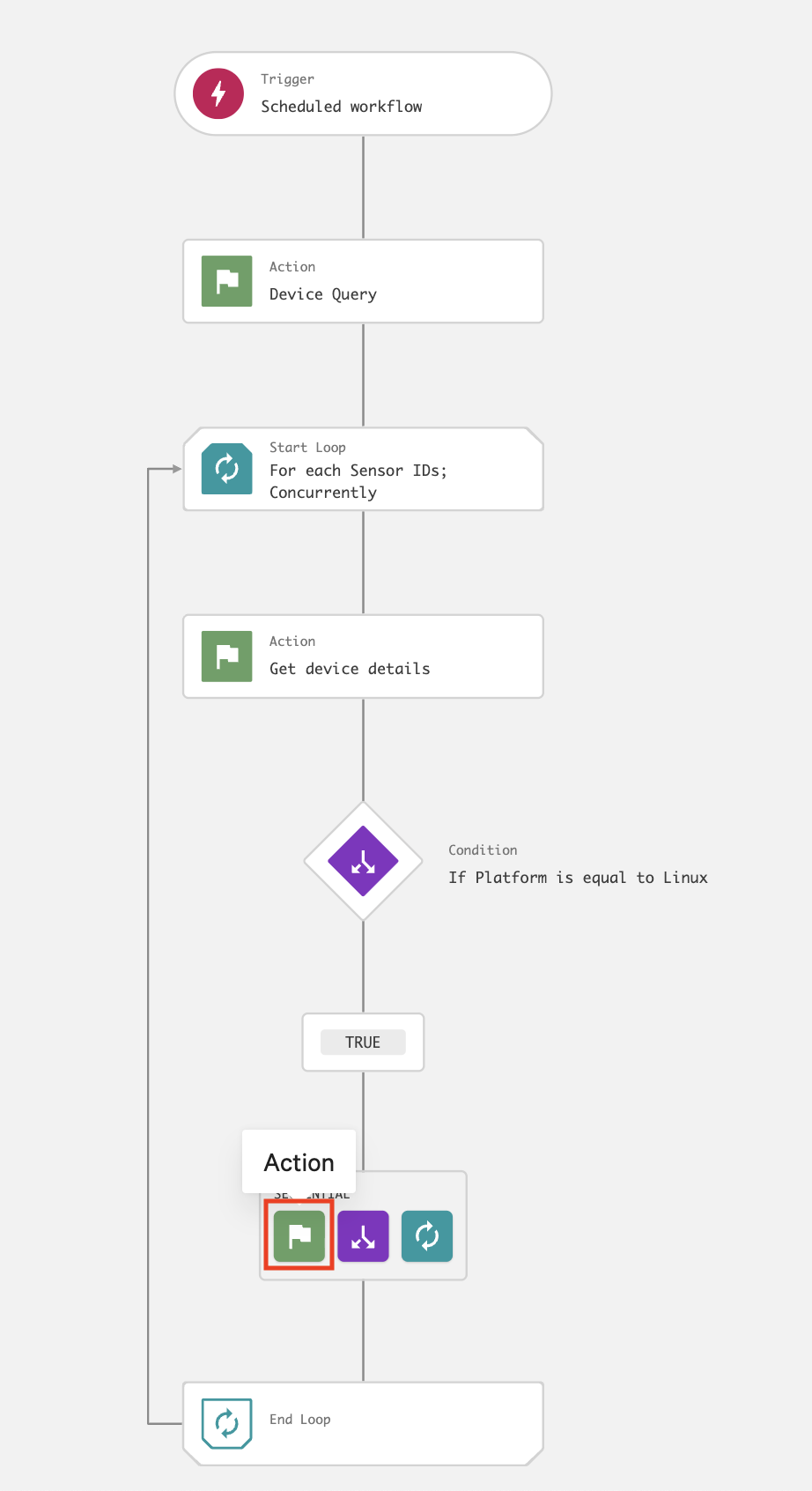
On the workflow builder, add an action inside the loop.
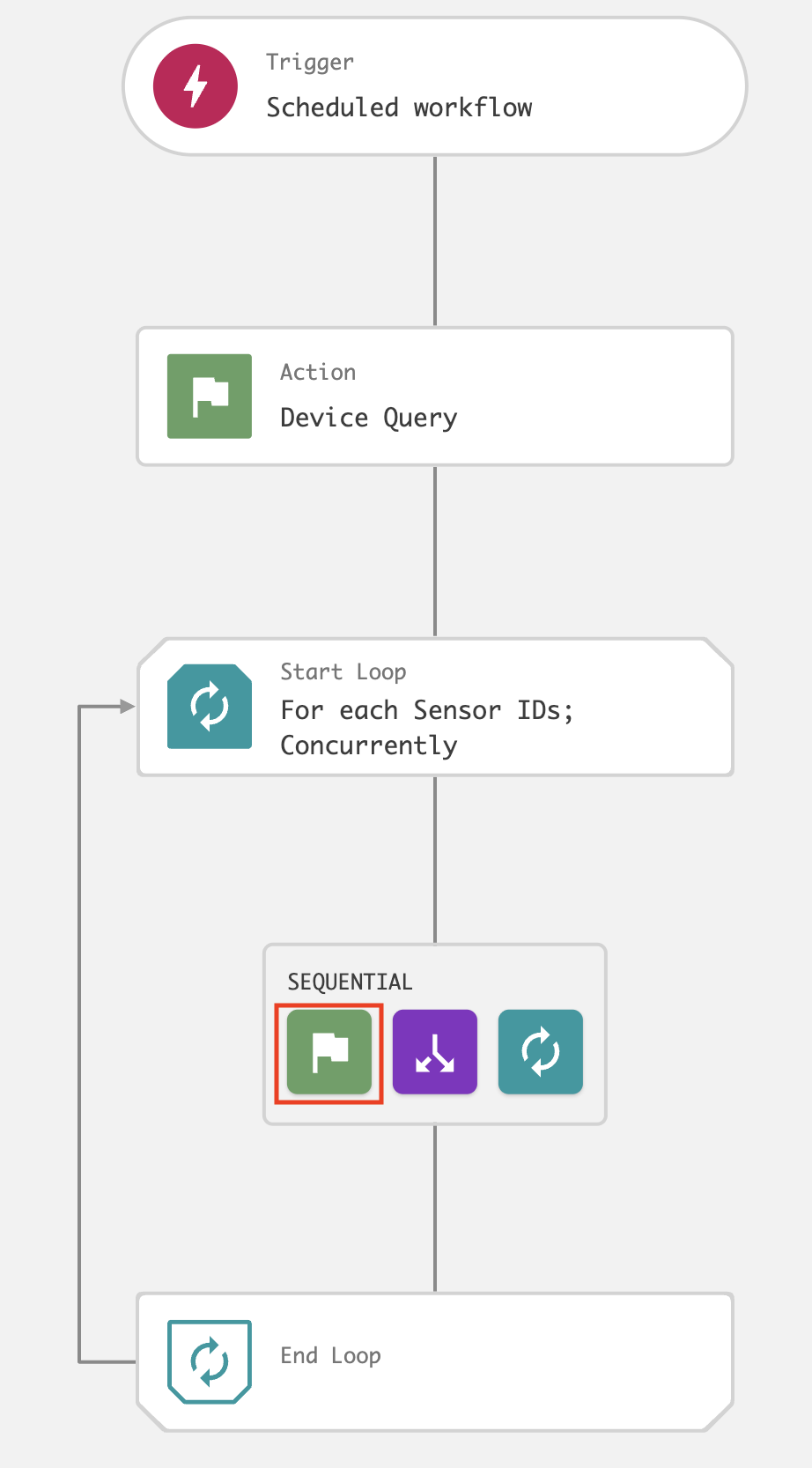
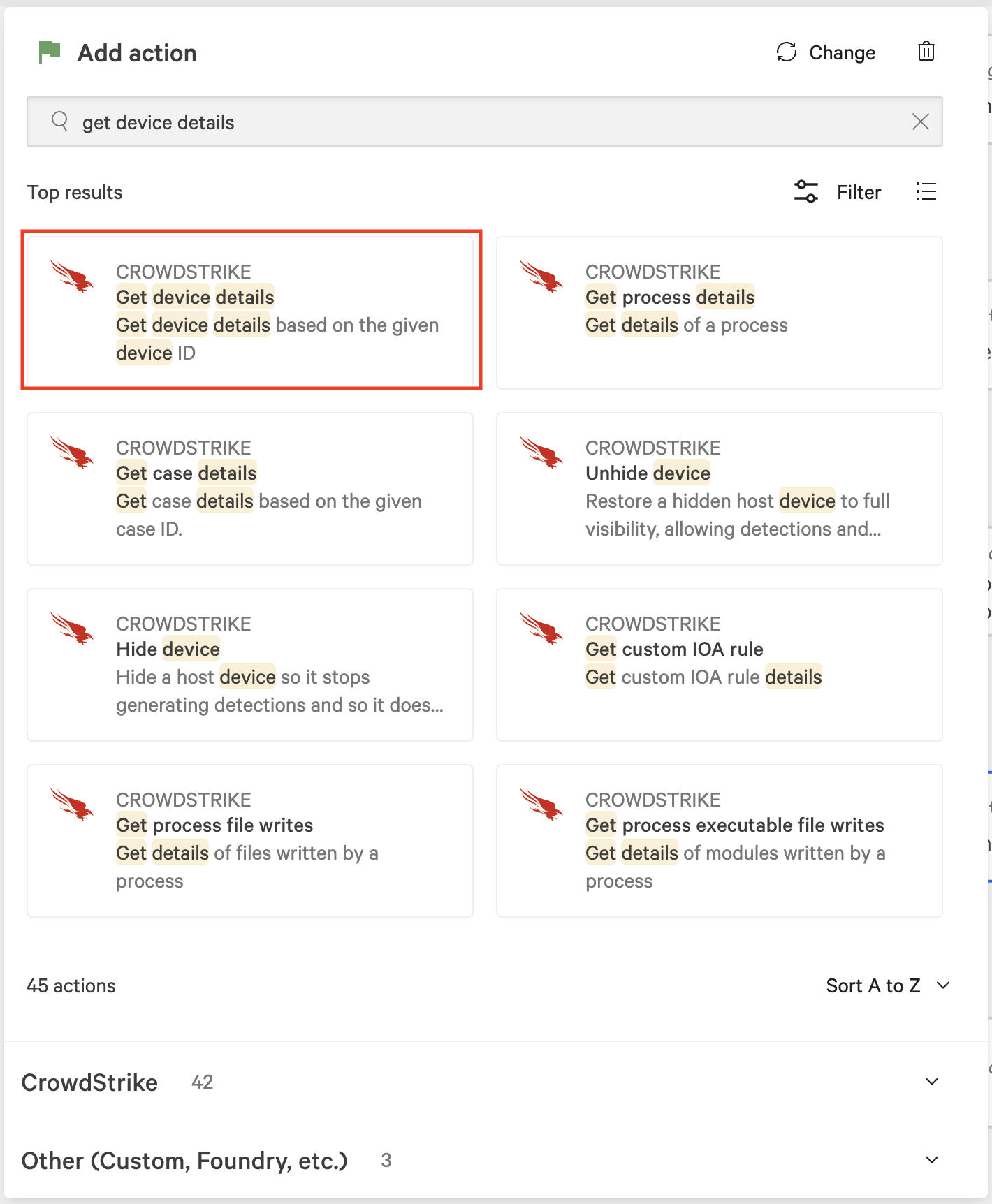
In the Add action dialog, search for and select Get device details.
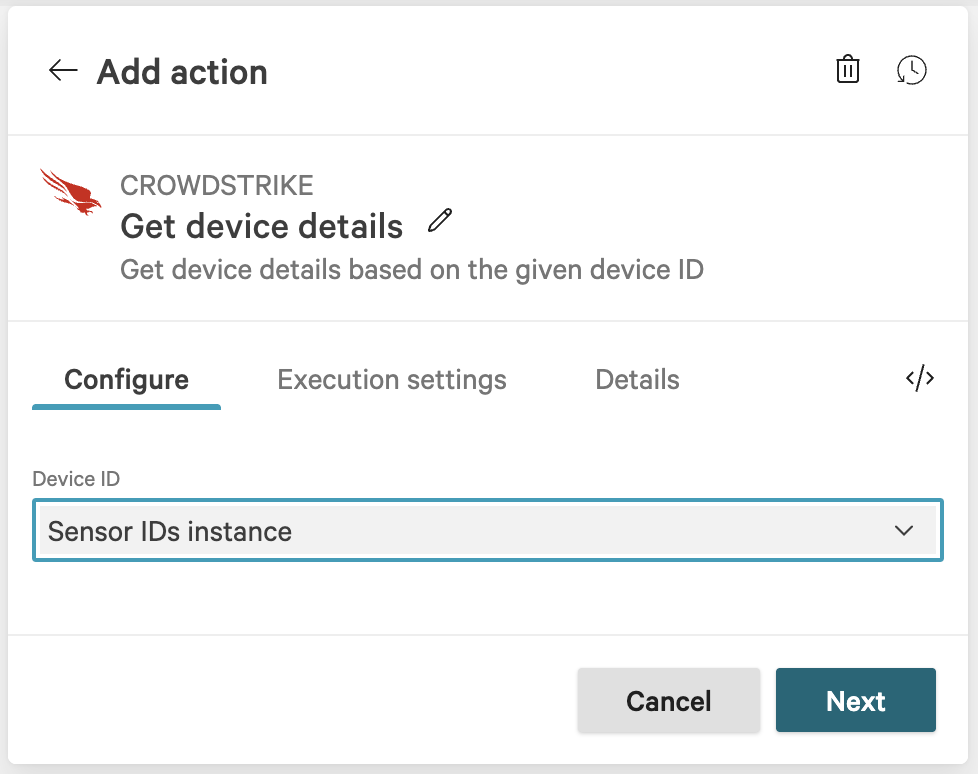
In the Device details dialog, set Device ID to Sensor IDs instance, then click Next.
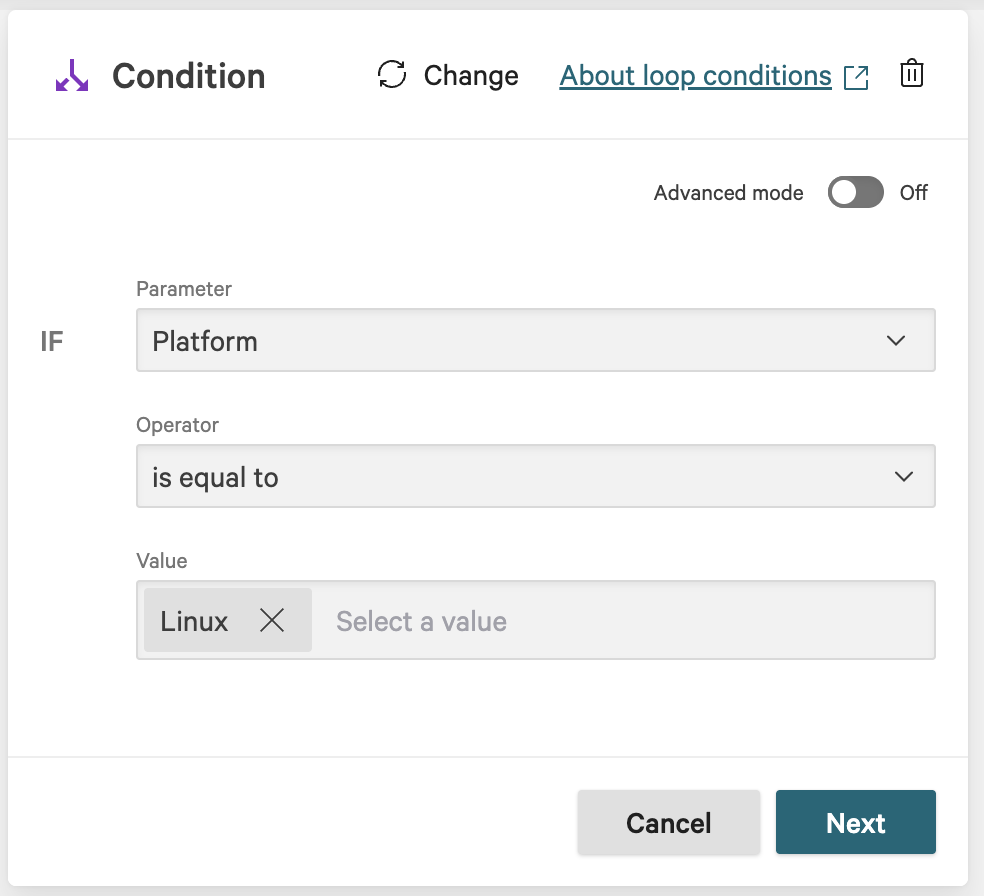
On the workflow builder, add a Condition after Get device details.
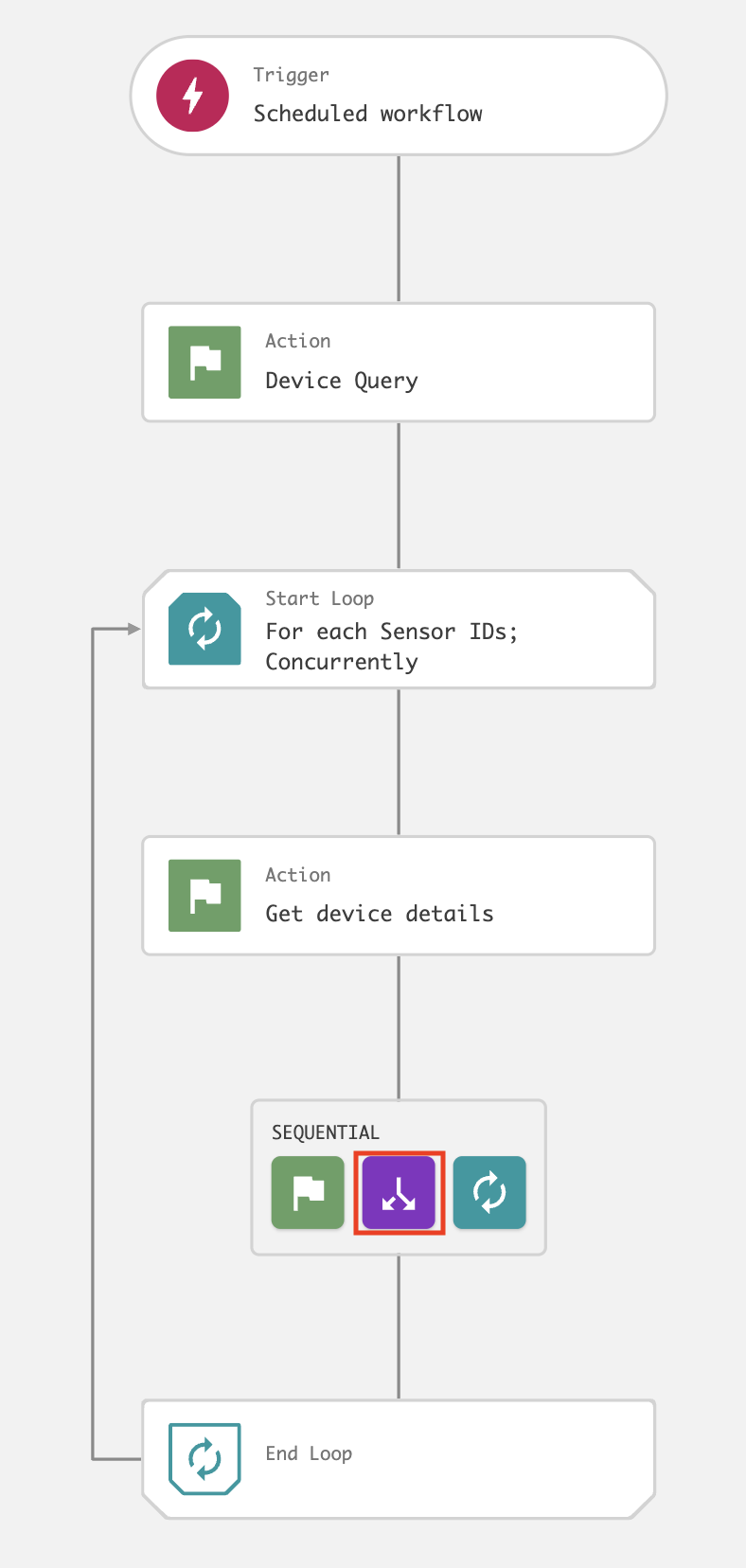
In the Condition dialog, enter the following and click Next:
Parameter: Platform
Operator: is equal to
Value: Windows, Linux or Mac
On the workflow builder, add an action under the TRUE branch.
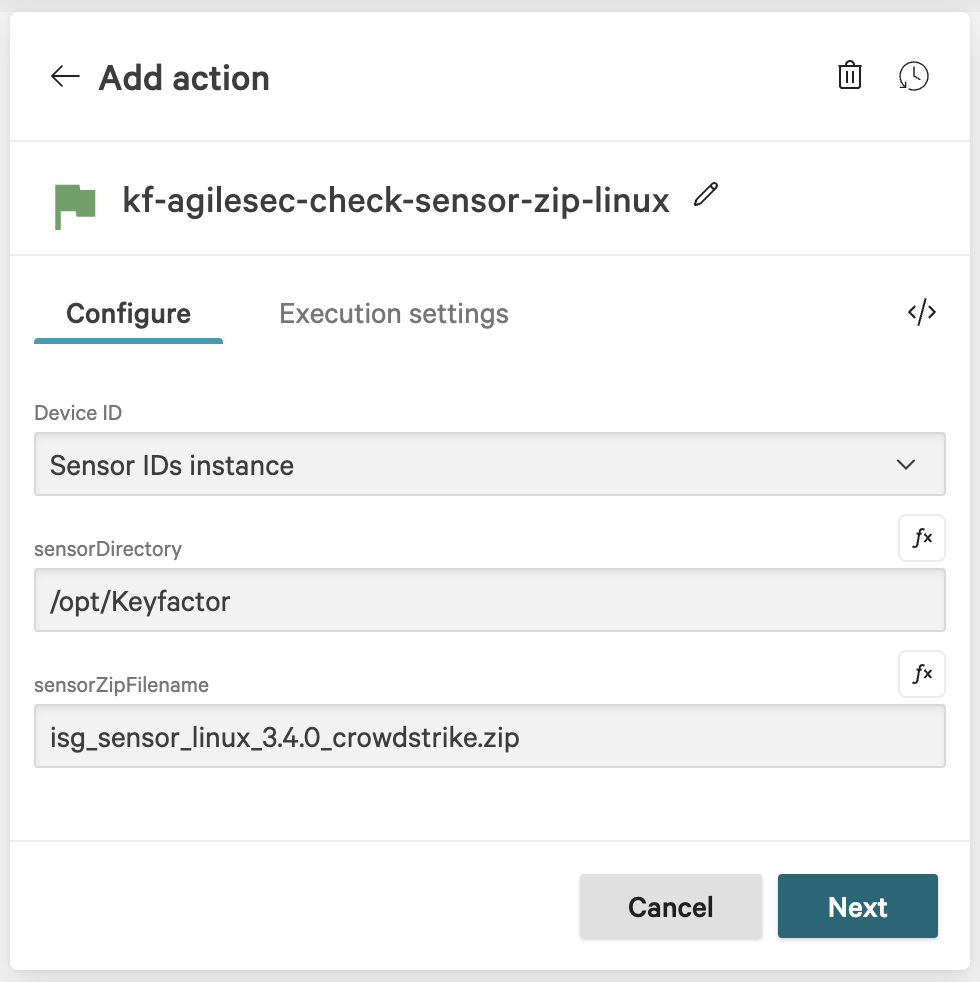
In the Add action dialog, search for and select the script
kf-agilesec-check-sensor-zip-linux.In the action configuration for kf-agilesec-check-sensor-zip-windows, enter the following recommended values and click Next:
Device ID: Sensor IDs instance
sensorDirectory:
For linux:
/opt/KeyfactorFor windows:
C:\Program Files\KeyfactorFor Mac:
/opt/Keyfactor
sensorZipFilename:
For linux:
isg_sensor_linux_3.4.0_crowdstrike.zipFor Windows:
isg_sensor_windows_3.4.0_crowdstrike.zipFor Mac:
isg_sensor_osx_3.4.0_crowdstrike.zip
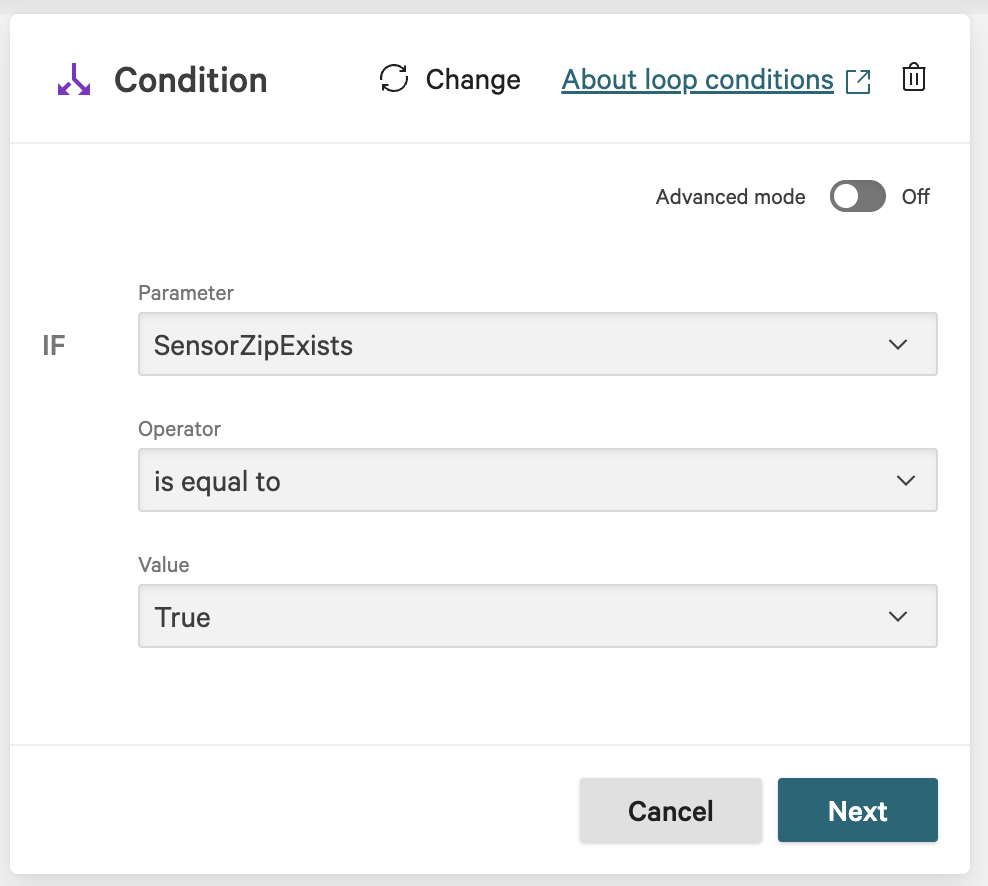
On the workflow builder, add a Condition after action kf-agilesec-check-sensor-zip-linux.
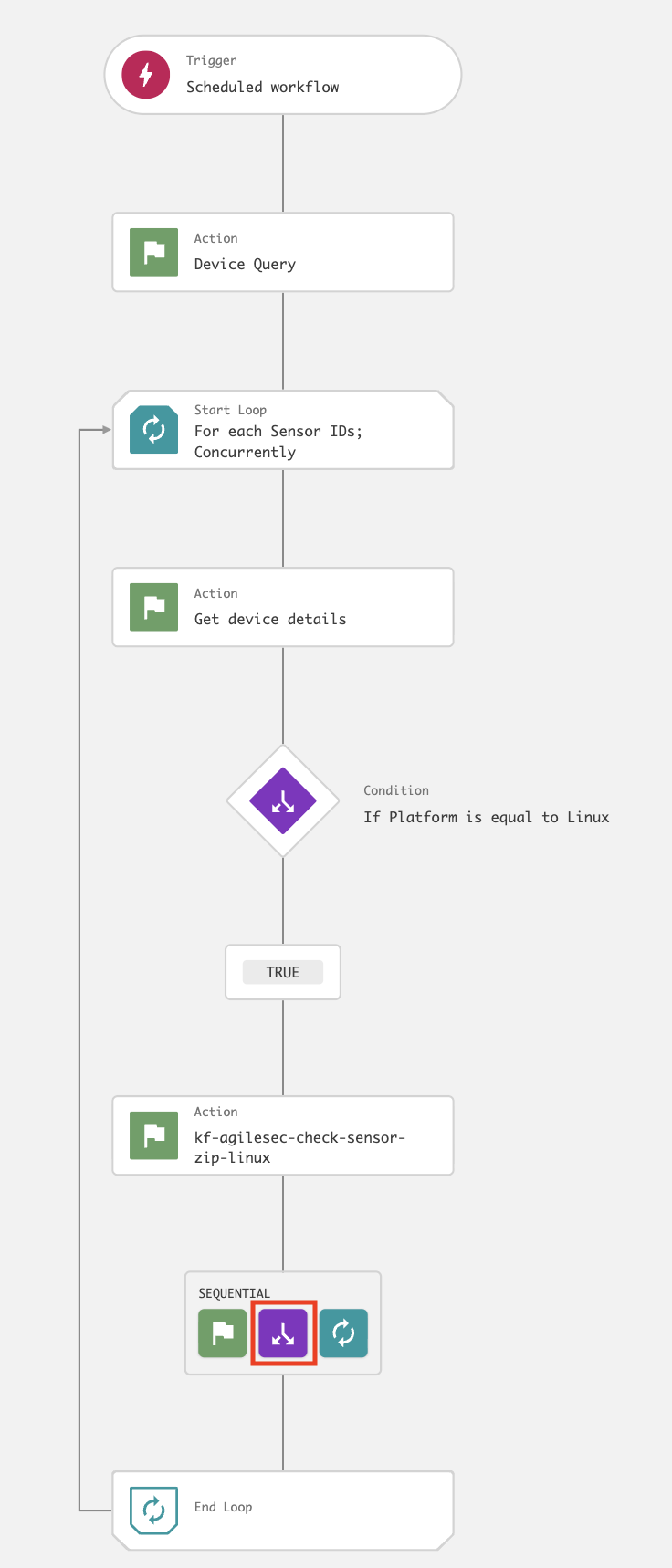
In the Condition dialog, enter the following and click Next:
Parameter: SensorZipExists
Operator: is equal to
Value: True
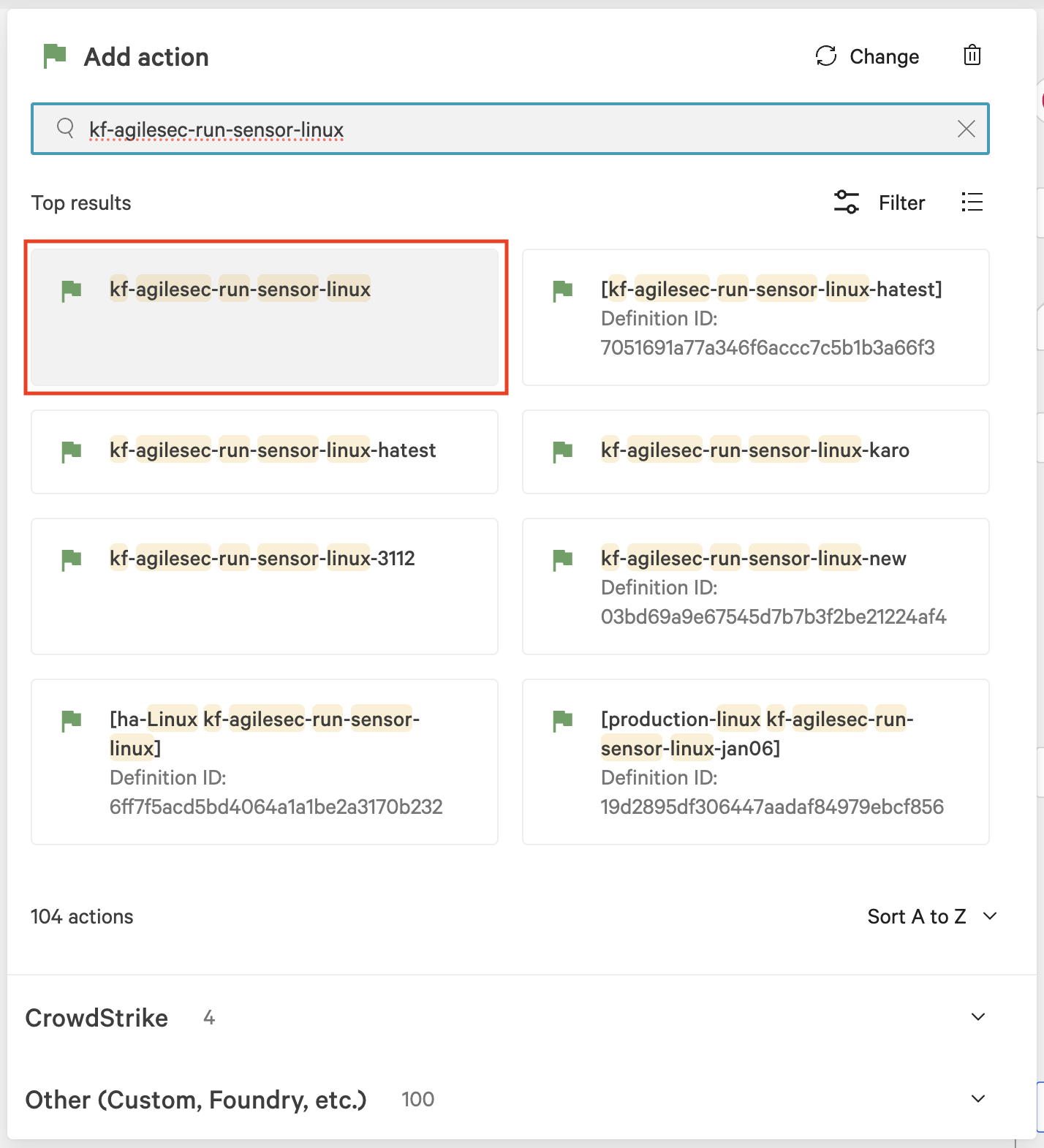
On the workflow builder, add an action under the
TRUEbranch.
In the Add action dialog, search for and select the script
kf-agilesec-run-sensor-linux.
In the action configuration for
kf-agilesec-run-sensor-linux, enter the following recommended values for your environment:
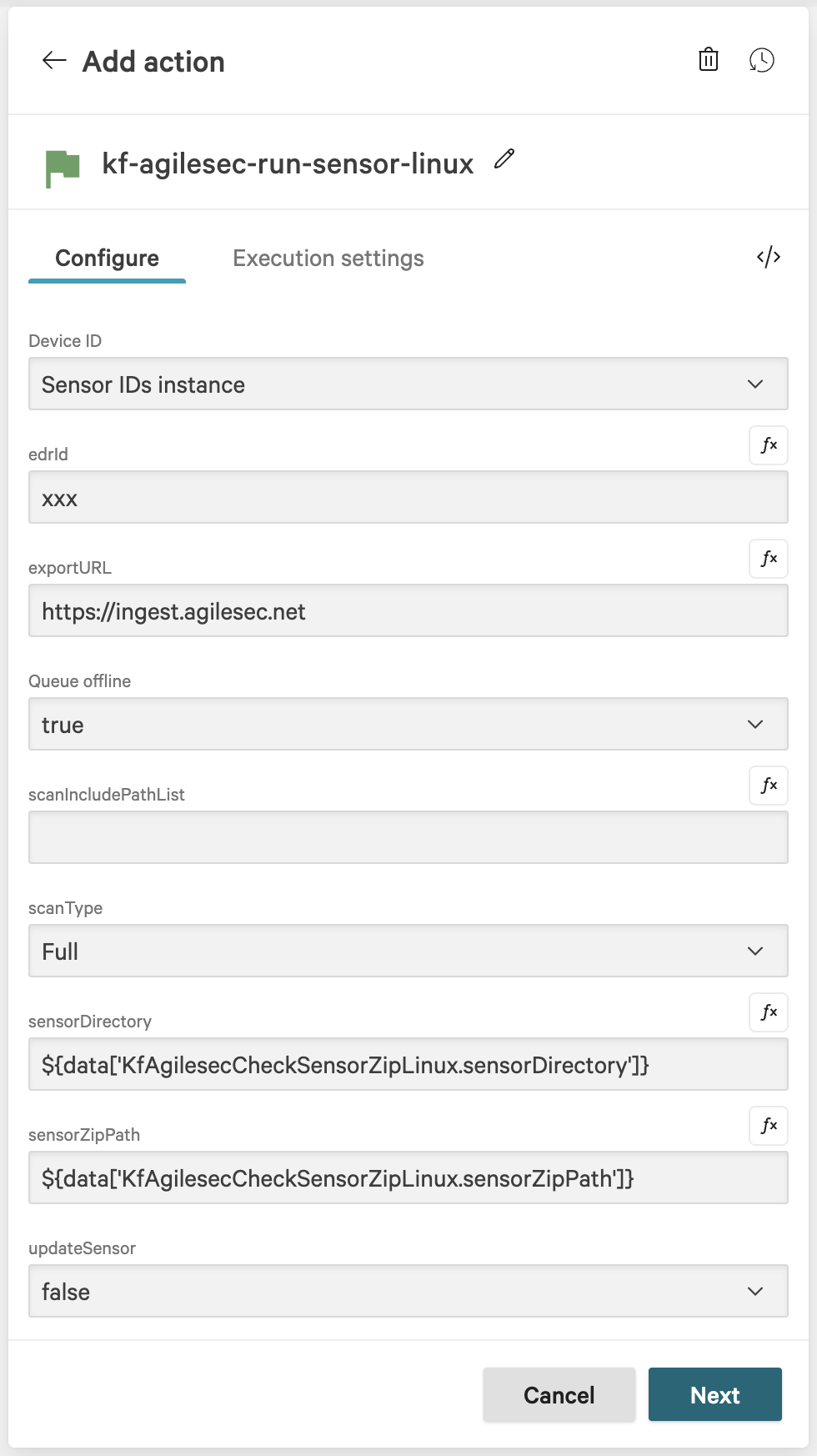
Field | Value | Description |
Device ID | Sensor IDs instance | Device ID provided by CrowdStrike |
edrId |
| Used to obtain an access token from AgileSec Platform. This access token is used for authenticating with the ingestion service. See Generate an EDR ID |
exportURL | https://<analytics server fqdn>:<port> | External facing AgileSec platform URL. |
Queue offline | true | Queues the action when the device is offline. |
scanType | Full | Type of scan to perform:
|
sensorDirectory | | Sensor install directory. Use the default value to use the output from check sensor zip action. |
sensorZipPath | | Path to the sensor ZIP. Use the default value to use the output from check sensor zip action |
updateSensor | false | Set to true to reinstall/upgrade the sensor |
On the workflow builder, add an action under the
ELSEbranch forsensorZipExists.
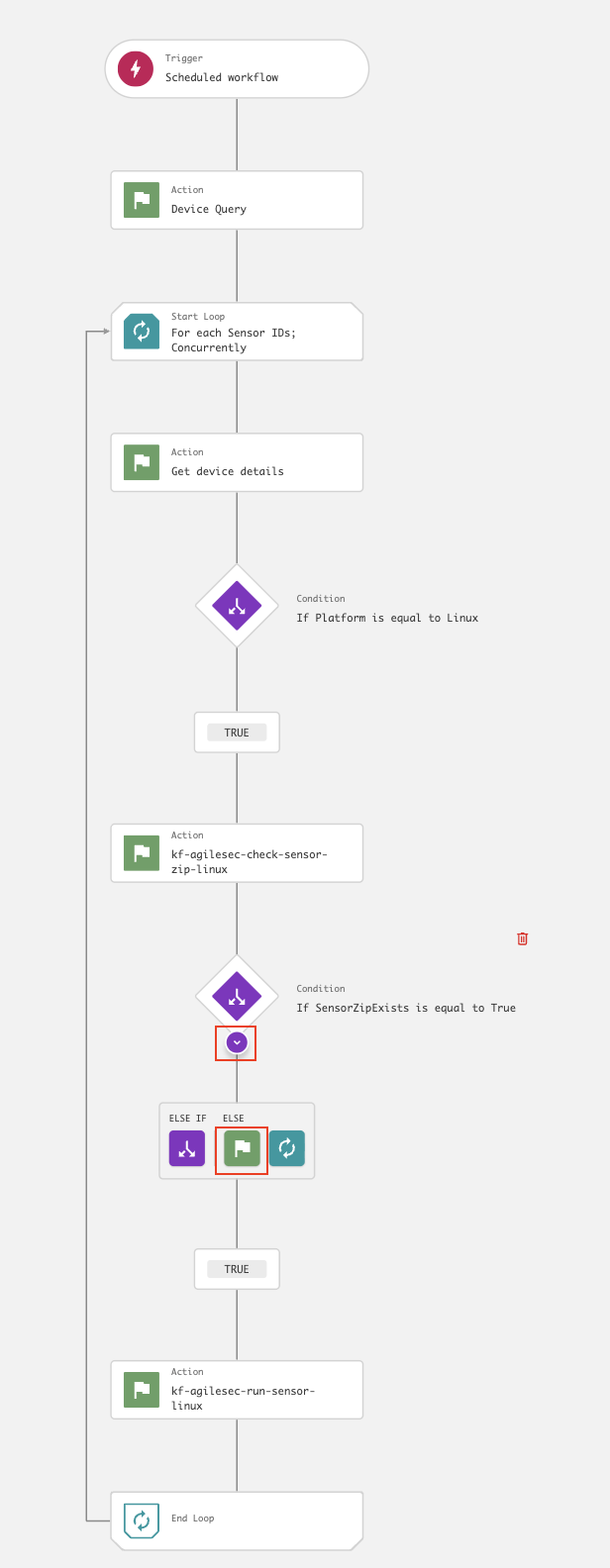
In the Add action dialog, search for and select Put file.
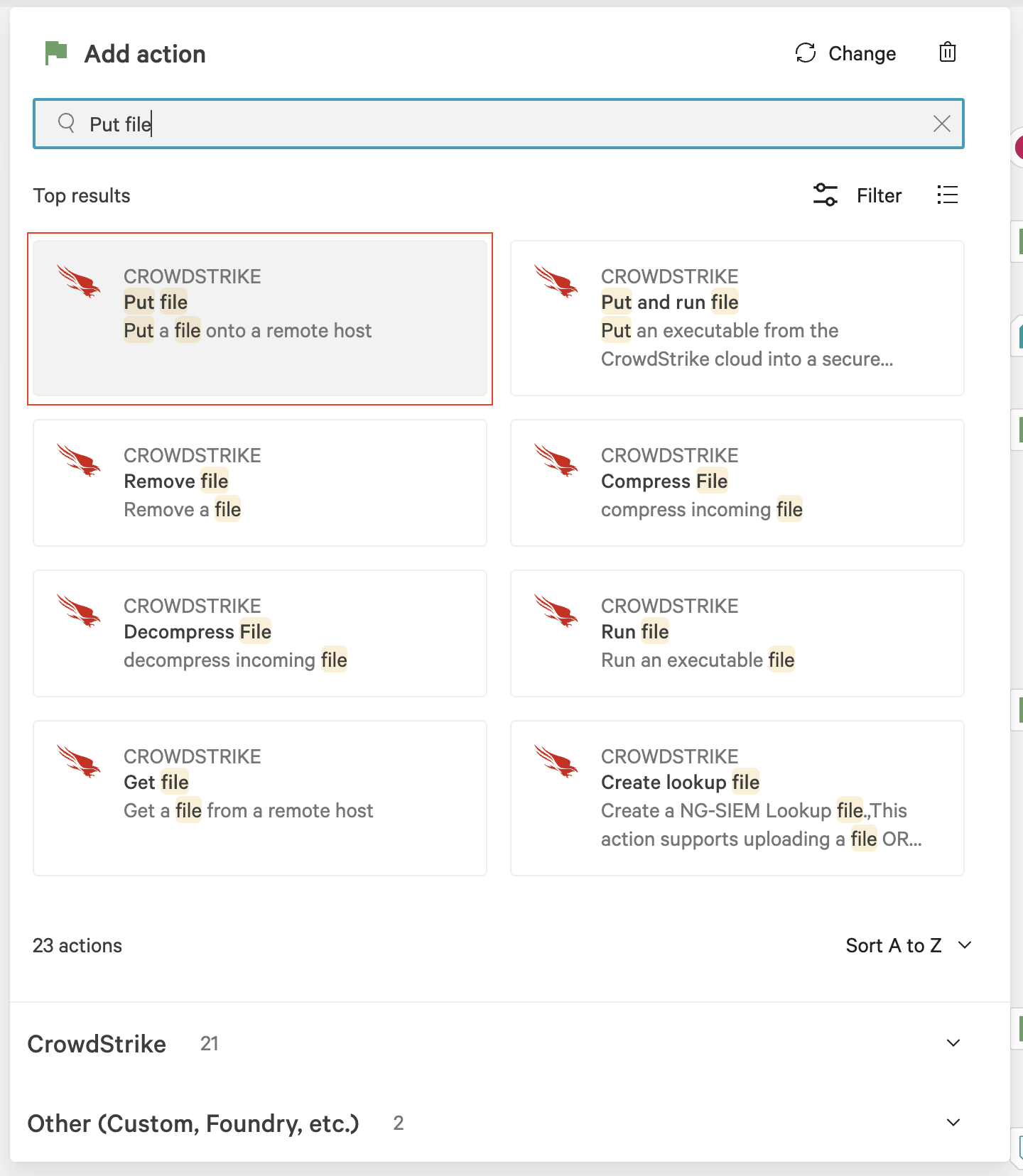
In the Put file dialog, enter the following values and click Next:
Device Id:
Sensor IDs instanceFile name:
For Linux:
isg_sensor_linux_3.4.0_crowdstrike.zipFor Windows:
isg_sensor_windows_3.4.0_crowdstrike.zipFor OSX:
isg_sensor_osx_3.4.0_crowdstrike.zip
Destination directory path:
For Linux:
${data['KfAgilesecCheckSensorZipLinux.sensorDirectory']}For Windows:
${data['KfAgilesecCheckSensorZipWindows.sensorDirectory']}For OSX:
${data['KfAgilesecCheckSensorZipOSX.sensorDirectory']}
Queue offline: true
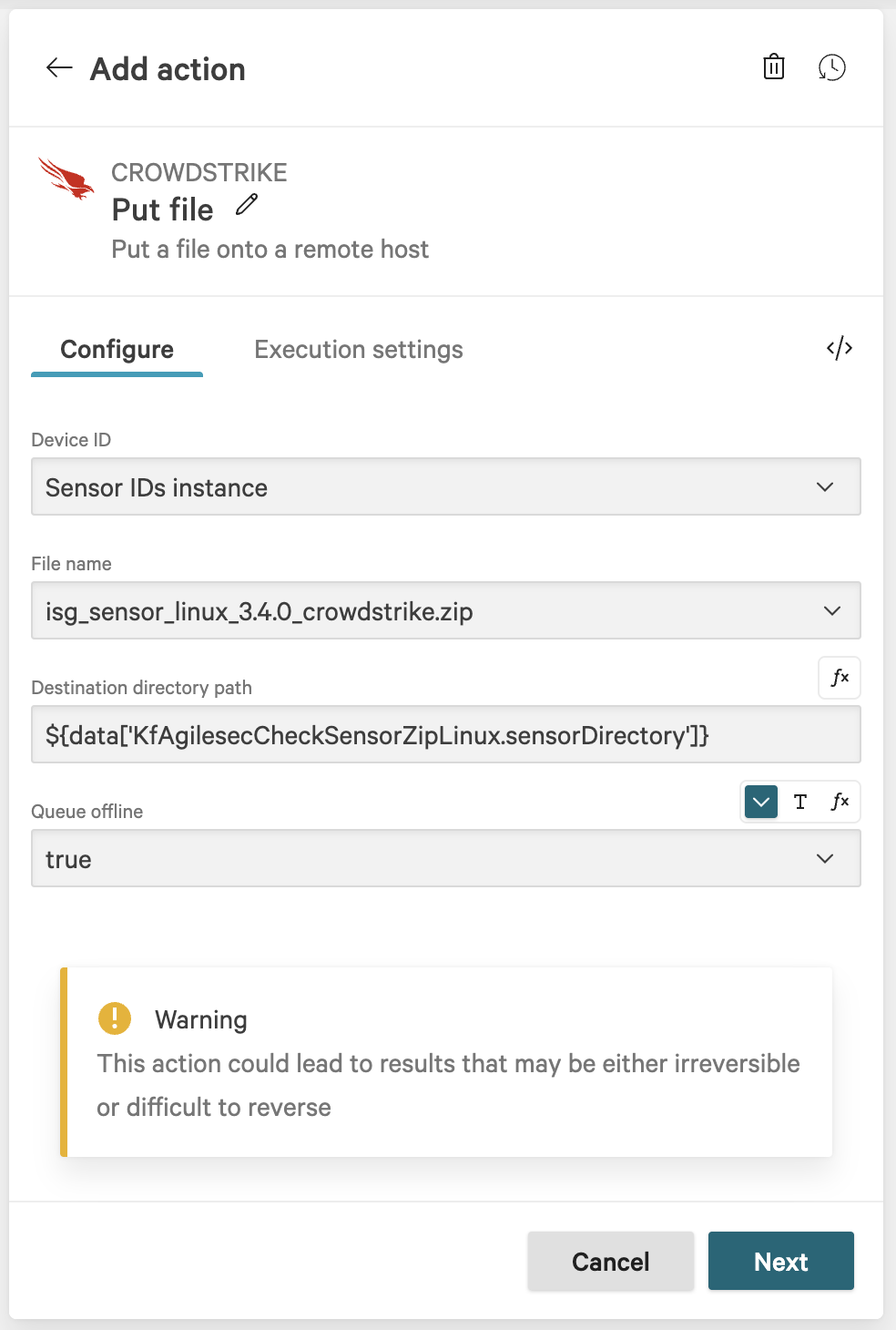
On the workflow builder, add action
kf-agilesec-run-sensor-<platform>(same as Step 18) under the Put file.Configure the action
kf-agilesec-run-sensor-<platform>using Step 19The workflow is now complete and should resemble the following:
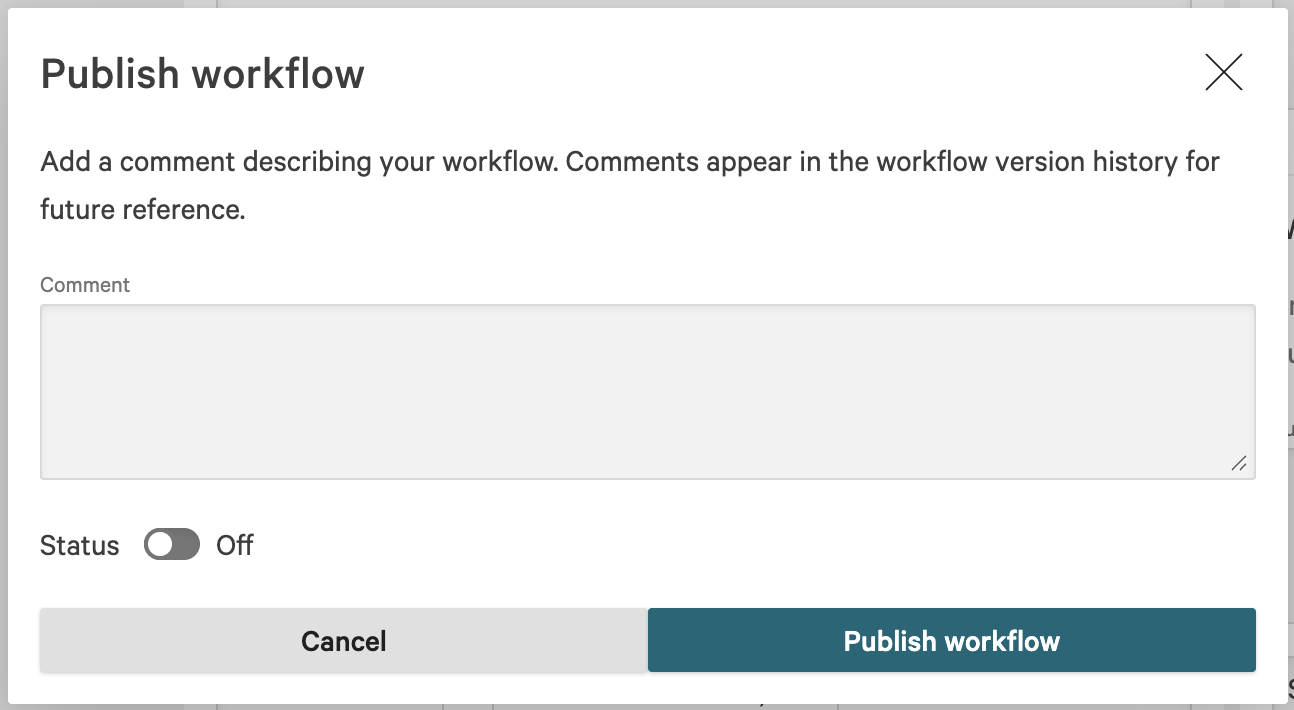
Click Publish, then in the Publish workflow dialog click Publish workflow. Toggle Status to on now or later to activate the workflow.
Execute Workflow to Run Host Scan Sensor
If your workflow trigger is on-demand, execute the workflow to test the sensor.
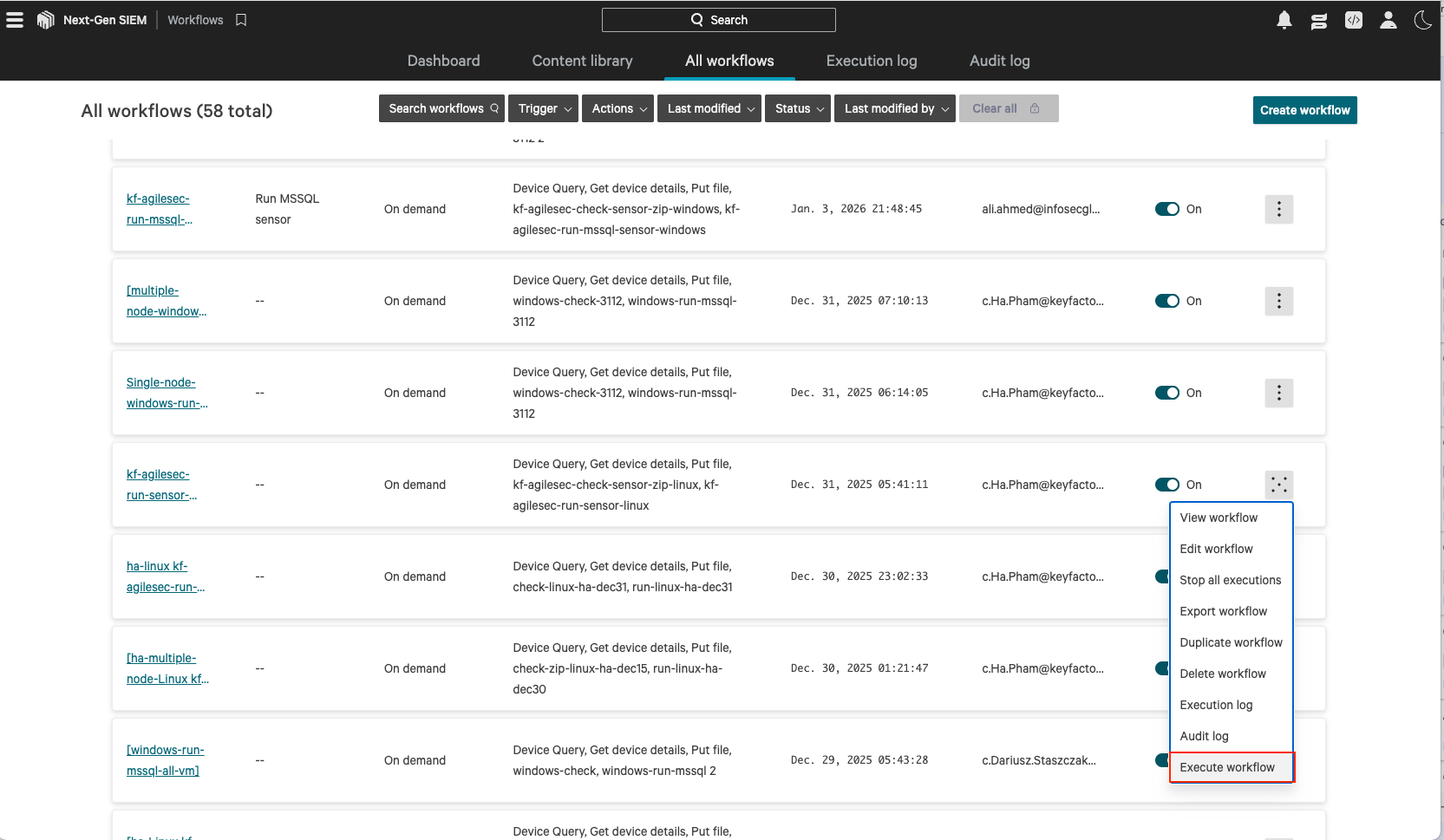
If your workflow trigger is scheduled, wait for the configured interval for the sensor to run.
Check the scan output data on AgileSec Platform UI
A host sensor scan is initiated on all machines included in “Device Query” action.
Findings found by the scan are exported to the ingestion service.
View scan history and results on the Keyfactor AgileSec Platform UI
Workflow To Undeploy Sensor
You may need to un-deploy the sensor to upgrade to a newer version or to remove it from an endpoint. The un-deployment workflow cleanly removes the deployed sensor components and associated execution artifacts so the sensor can be reinstalled or upgraded as needed.
Follow the same instruction used to create the "Run host sensor" workflow, but:
Use Trigger On-demand only
Use specific actions and script file
kf-agilesec-undeploy-sensor-<platform>for true branch of checksensorExistscondition
Create a new workflow following same steps as Workflow to Run Host Scan Sensor, but after the sensorZipExists condition:
For Linux: add action
kf-agilesec-undeploy-sensor-linuxFor Windows: add action
kf-agilesec-undeploy-sensor-windowsFor Mac: add action
kf-agilesec-undeploy-sensor-osx
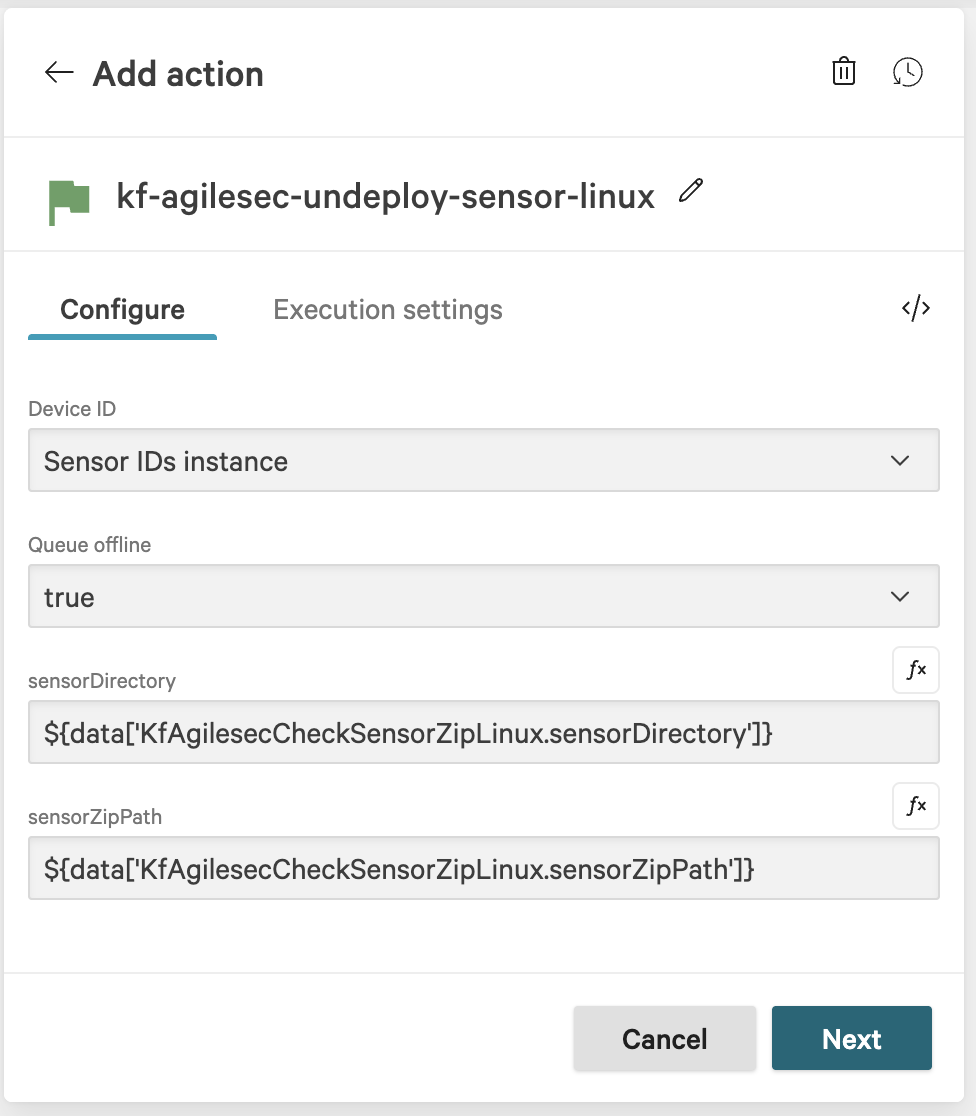
In the action configuration, enter the following recommended values for your environment:
Device Id:
Sensor IDs instanceQueue Offline:
truesensorDirectory:
For Linux:
${data['KfAgilesecCheckSensorZipLinux.sensorDirectory']}For Windows:
${data['KfAgilesecCheckSensorZipWindows.sensorDirectory']}For Mac:
${data['KfAgilesecCheckSensorZipOSX.sensorDirectory']}
sensorZipPath:
For Linux:
${data['KfAgilesecCheckSensorZipLinux.sensorZipPath']}For Windows:
${data['KfAgilesecCheckSensorZipWindows.sensorZipPath']}For Mac:
${data['KfAgilesecCheckSensorZipOSX.sensorZipPath']}
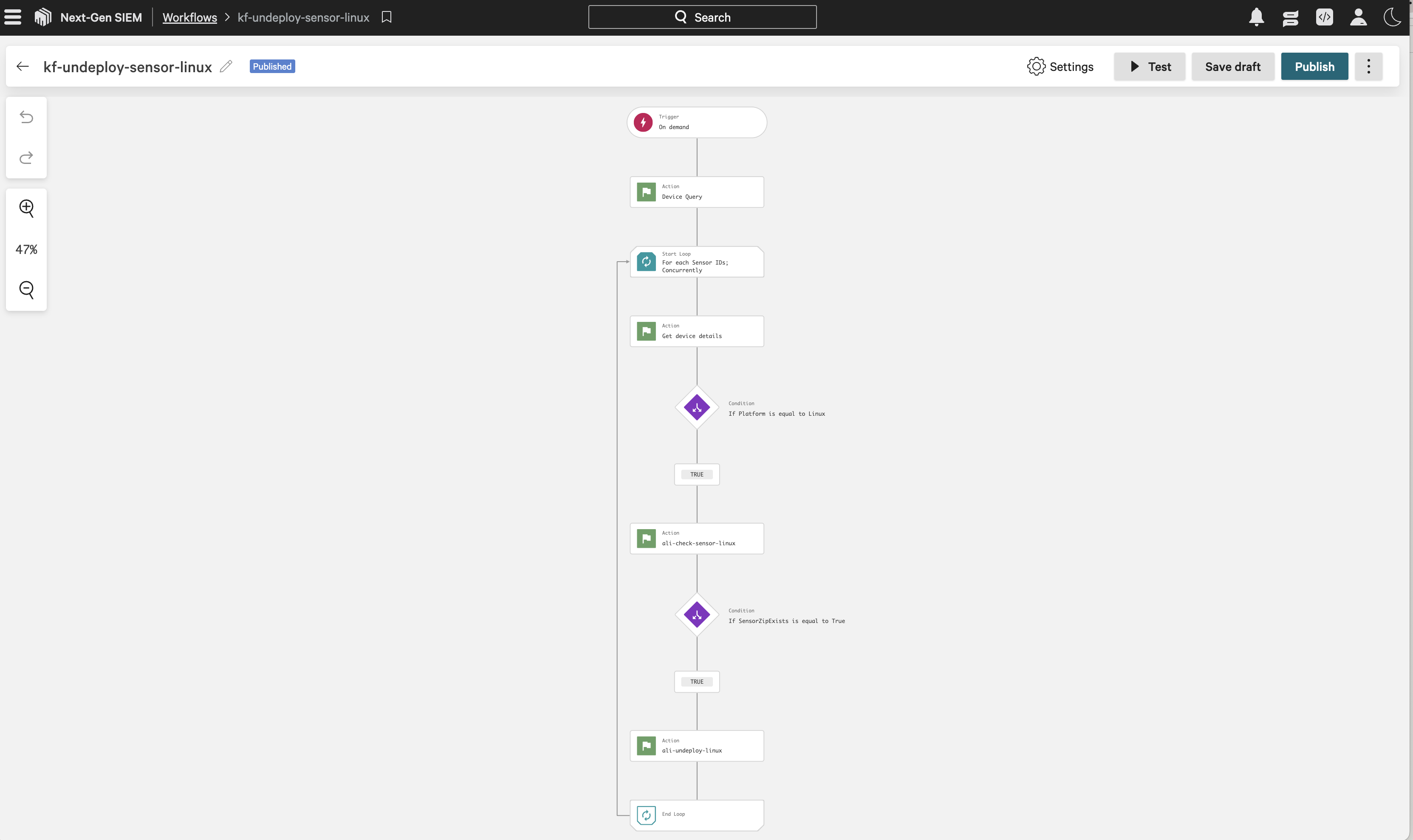
The undeploy sensor workflow should resemble the following:
Deploy New Sensor Package
Updating the Sensor Package When a new version of the sensor package is released, follow these steps to deploy the update:
Execute the "Un-deploy Sensor" workflow to remove the old version.
Execute the "Run Host Sensor" workflow to install the new version.
.png)