Using the Organizations feature
The following covers how to use the Organizations feature to edit deployment registration names and add users to deployments.
Organizations feature
The main screen of the Organizations feature allows you to access multiple deployments within your organization. When you first start with the Keyfactor SaaS Portal, you will have your first deployment tile.
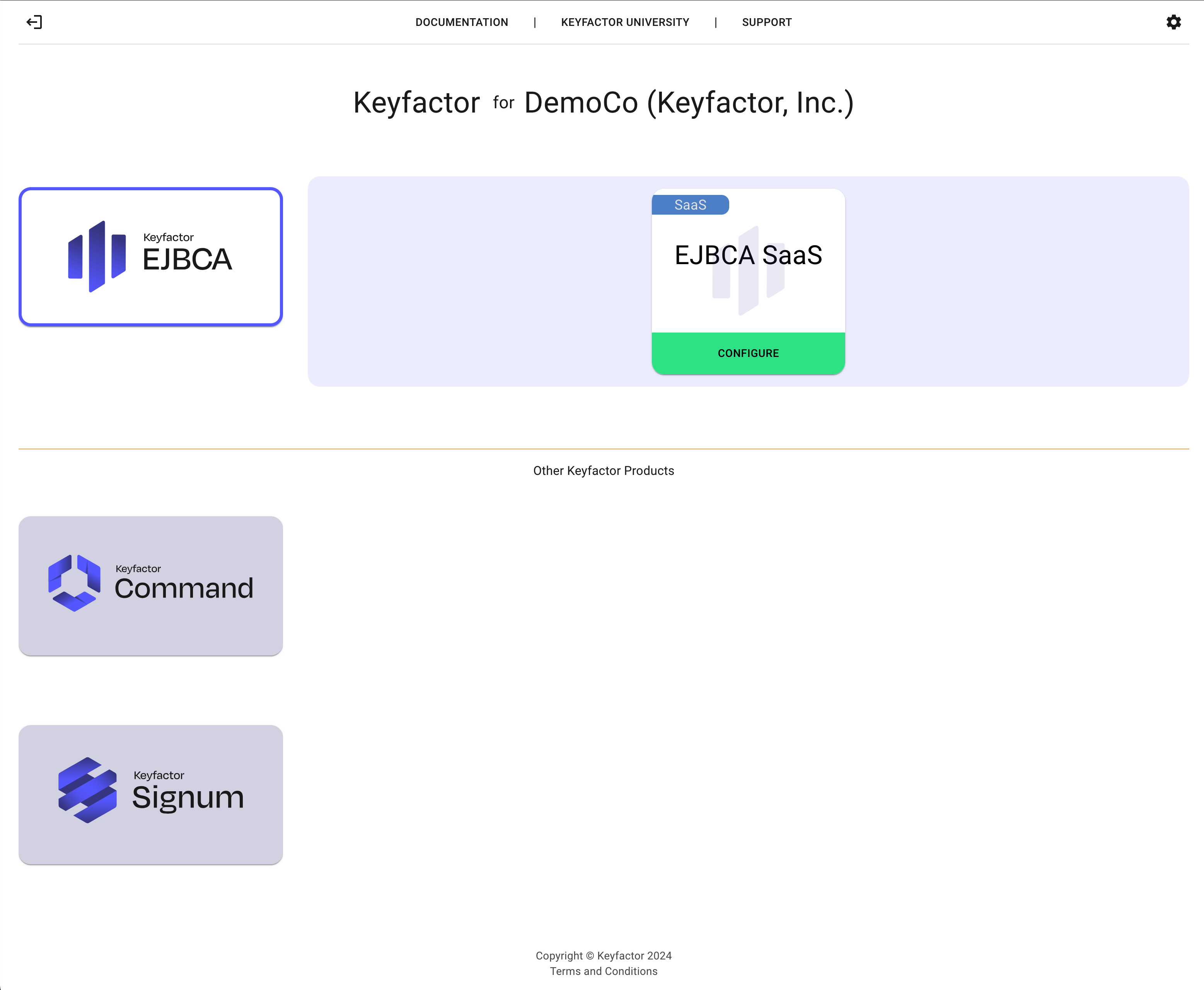
The following options are available:
A link to the SaaS Products Portal Web interface you deployed. This might be the Command, EJBCA or Signum Web Interface. Initially, until deployment, only a Configure option is displayed, allowing you to define options for your unique deployment covered in the next section Additional Product Tiles.
A link will take you to the SaaS Portal, where you can interact with your deployment via the self-service features.
For more information on the features of the Keyfactor SaaS Portal Deployment interface, refer to Navigating the SaaS Portal.
Additional Product Tiles
On the main deployments page, any products that your organization has not procured will be displayed below the current registrations.
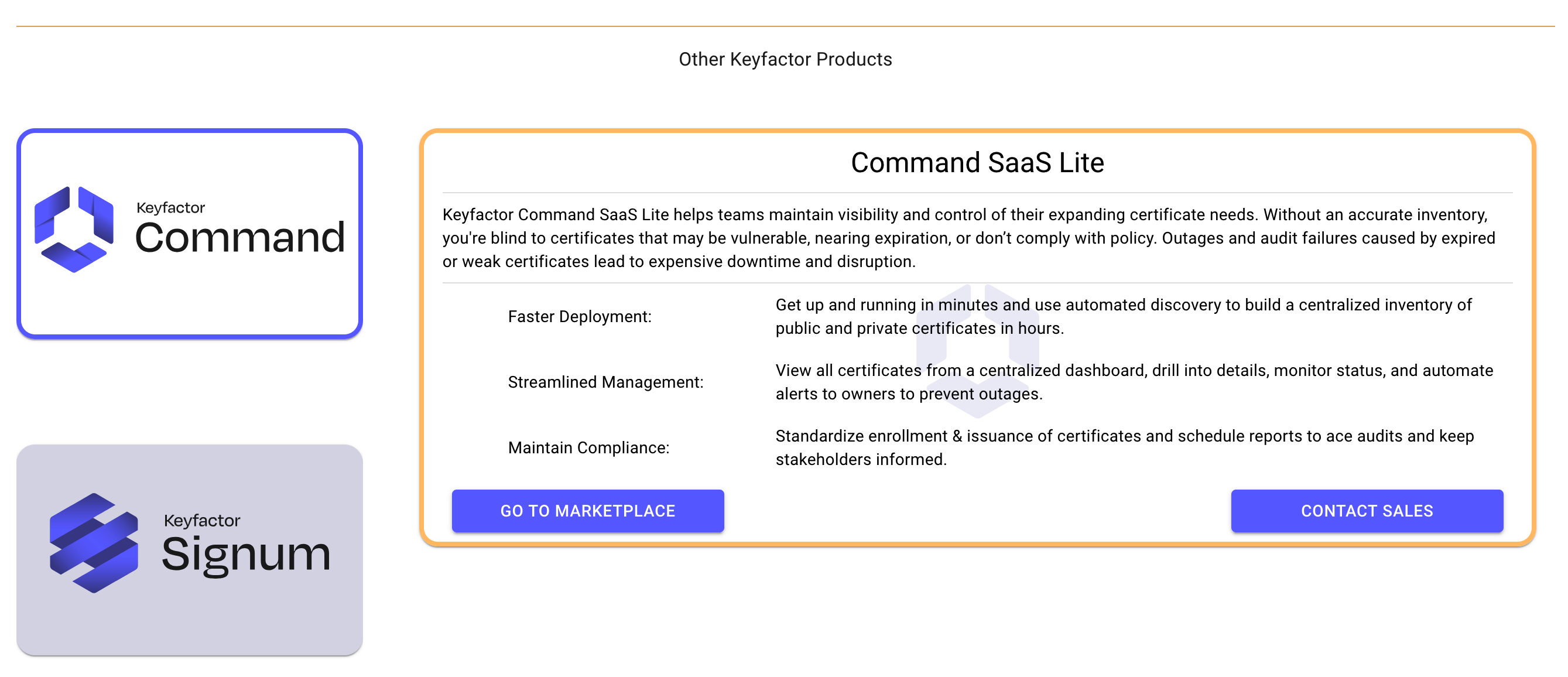
In the following example, EJBCA SaaS is the active registered product and other product tiles for additional Keyfactor products are displayed in the Other Keyfactor Products section. Select a product tile to view information about the additional product.
The following displays information about Command:
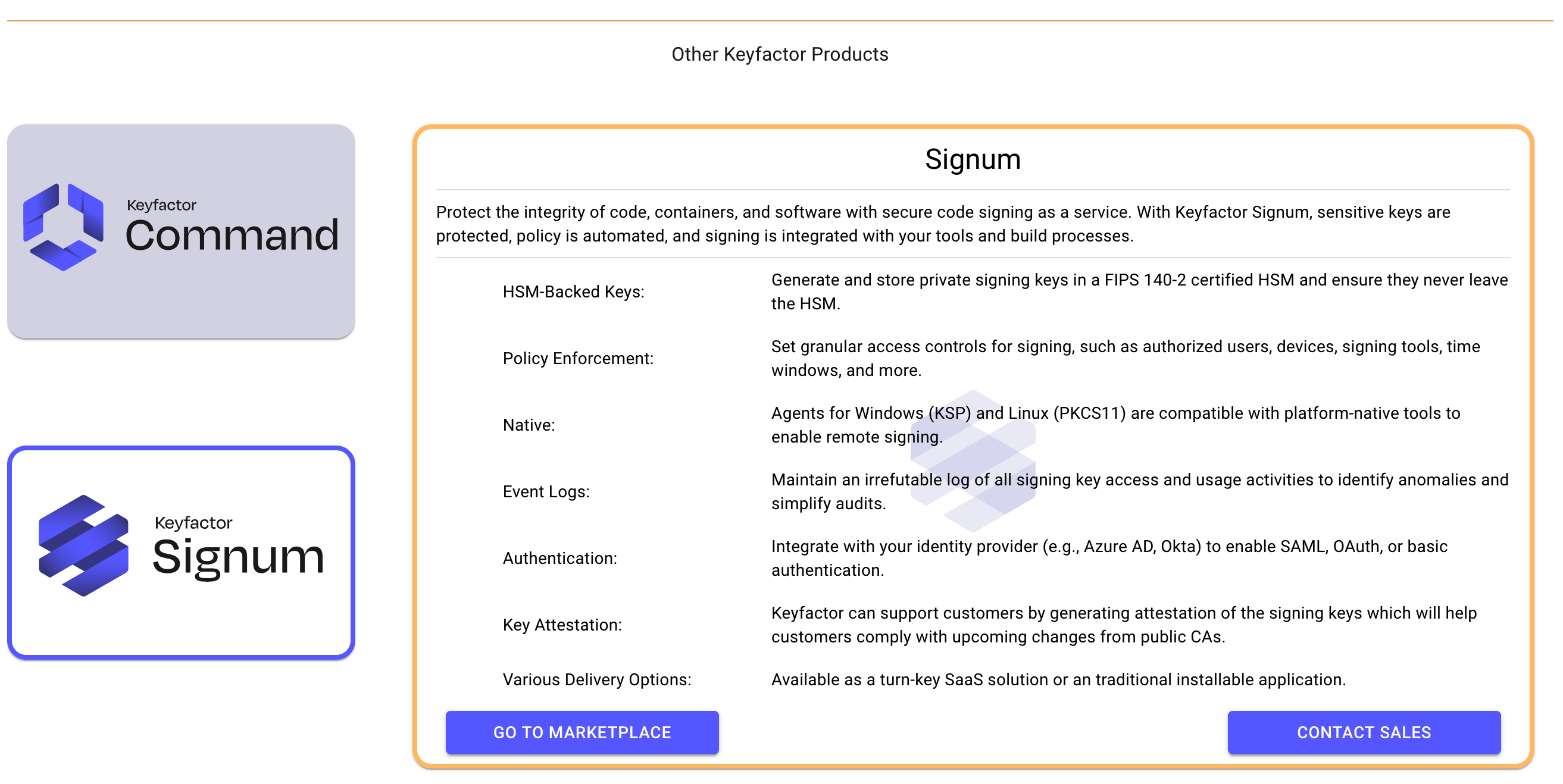
The following displays information about Signum:
Organization Settings
To access the Organization settings, click the gear icon.
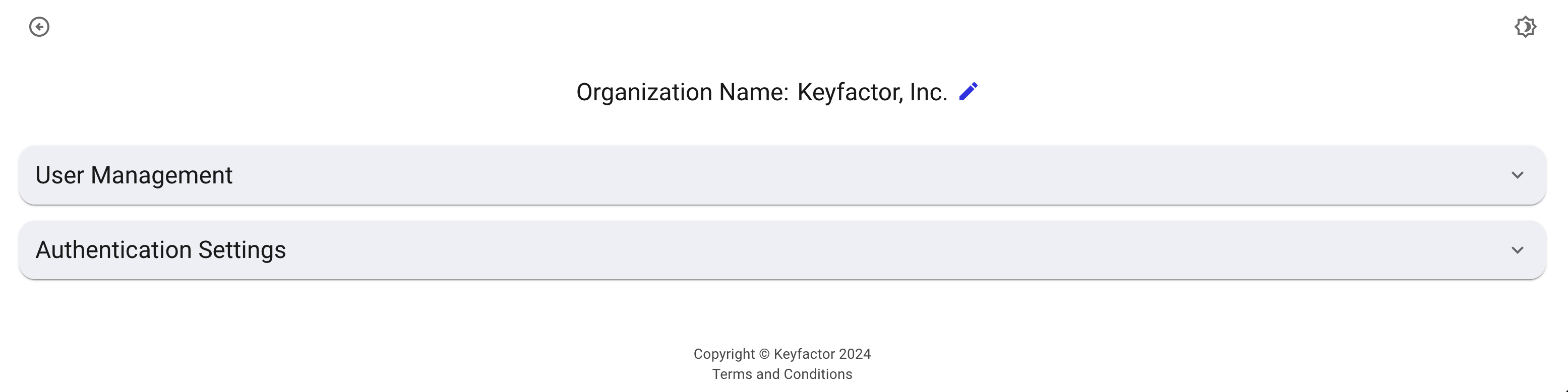
The Organization settings allow you to manage certain aspects of your organization. The name at the top of the screen is the name that appears at the top of the main page below the Keyfactor logo.
To edit the Organization name:
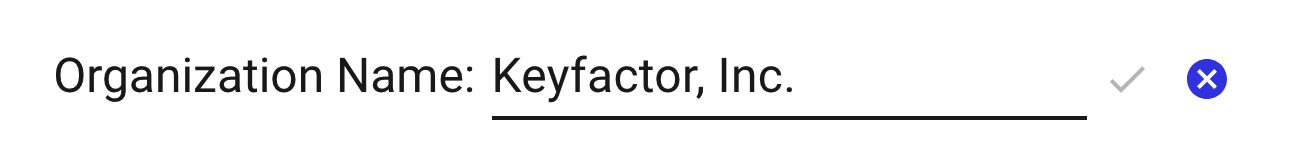
Click the pencil icon to change the Organization Name for all users of the Portal.

Edit the name and click the check mark to save.
The change will be reflected on the main screen where deployments are selected.
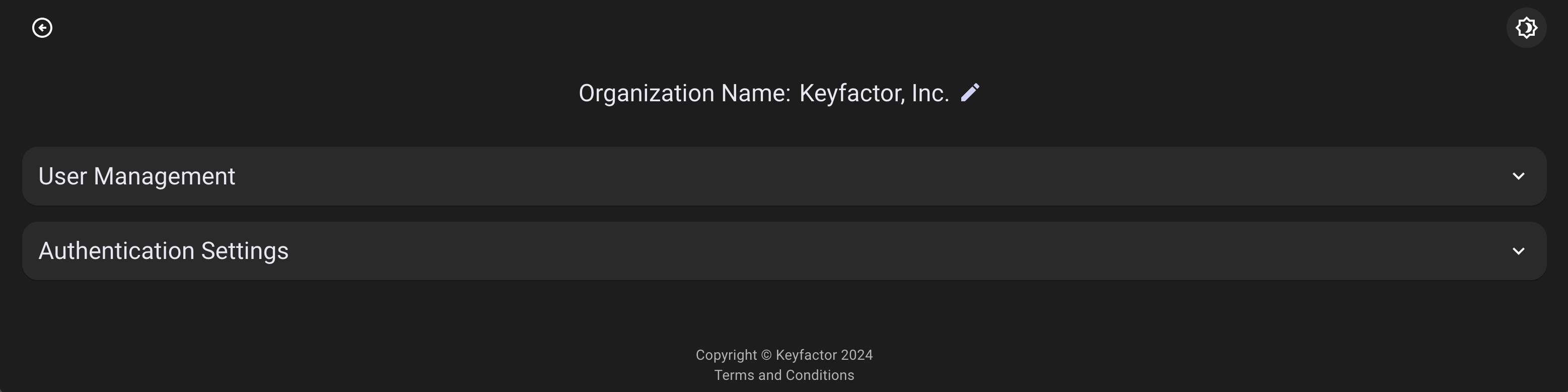
Toggle Light and Dark Mode
In the top right corner of the screen, when in the organizations setting, there are two user interface modes depending on user preference.
To toggle between the light and dark mode, click the light icon ![]()
Edit Deployment Display Names
Clicking the pencil icon next to a deployment name will allow you to change the registration name (display name) that displays on the tile screen.
Changing the registration name does not change the name of the deployment. The deployment name is not changeable due to its link to DNS.
Click the pencil icon to edit the registration name.
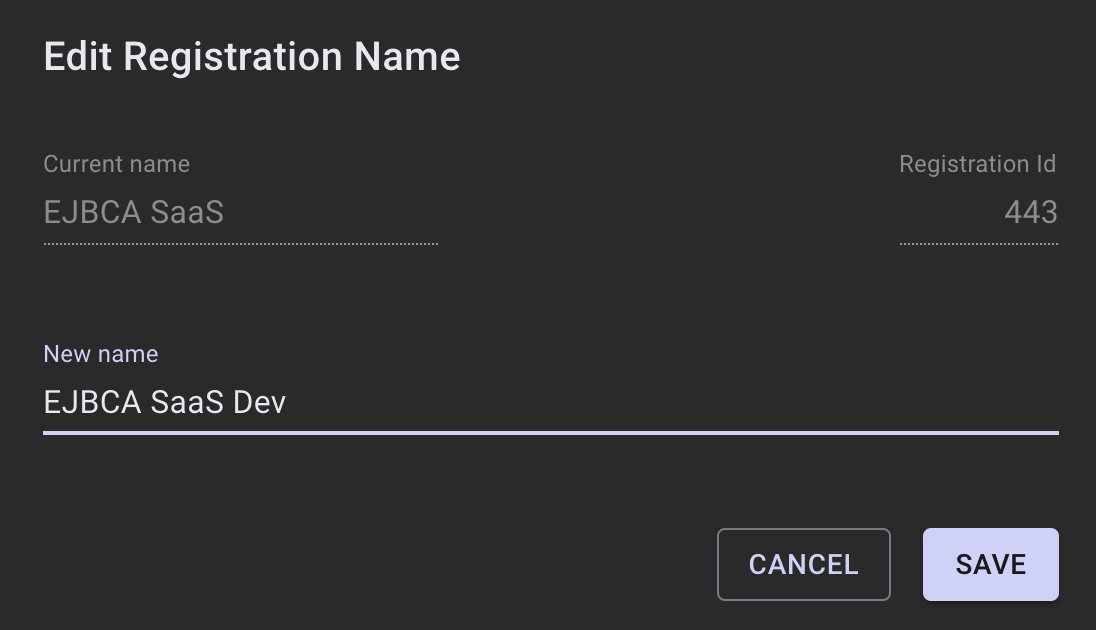
Once the name is changed, the tile on the main screen will be updated.
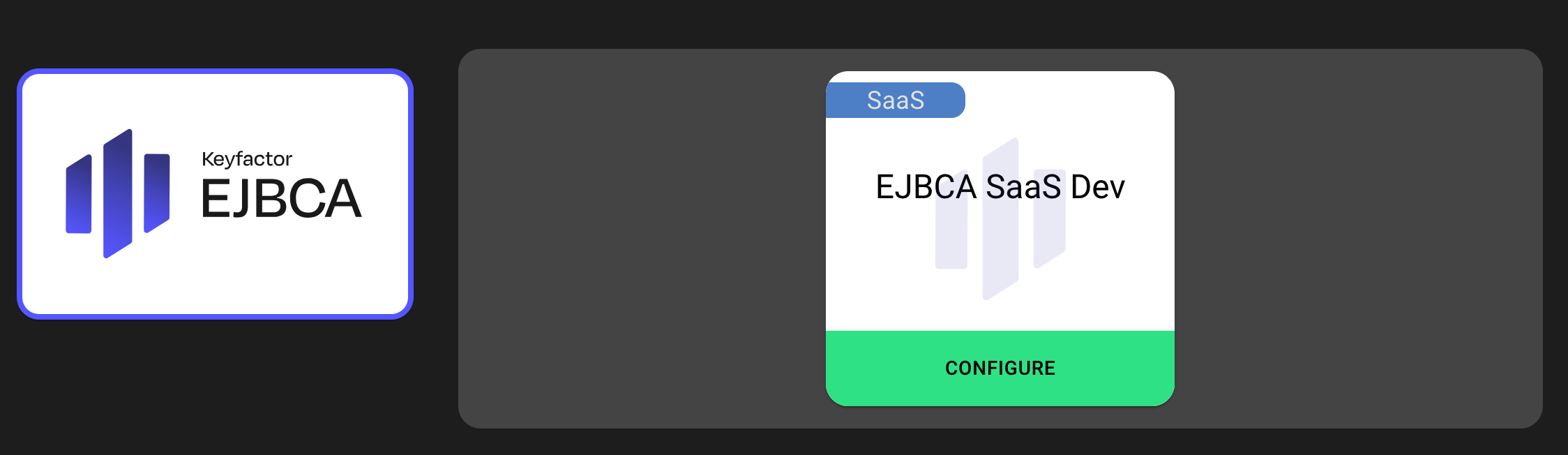
Add Users to Deployments
Step 1 - Create User
Expand the User Management accordion and click Create User to add a user to the organization.

Step 2 - Create Organization User
In the Create Organization User section, enter the name and email address of the new user.
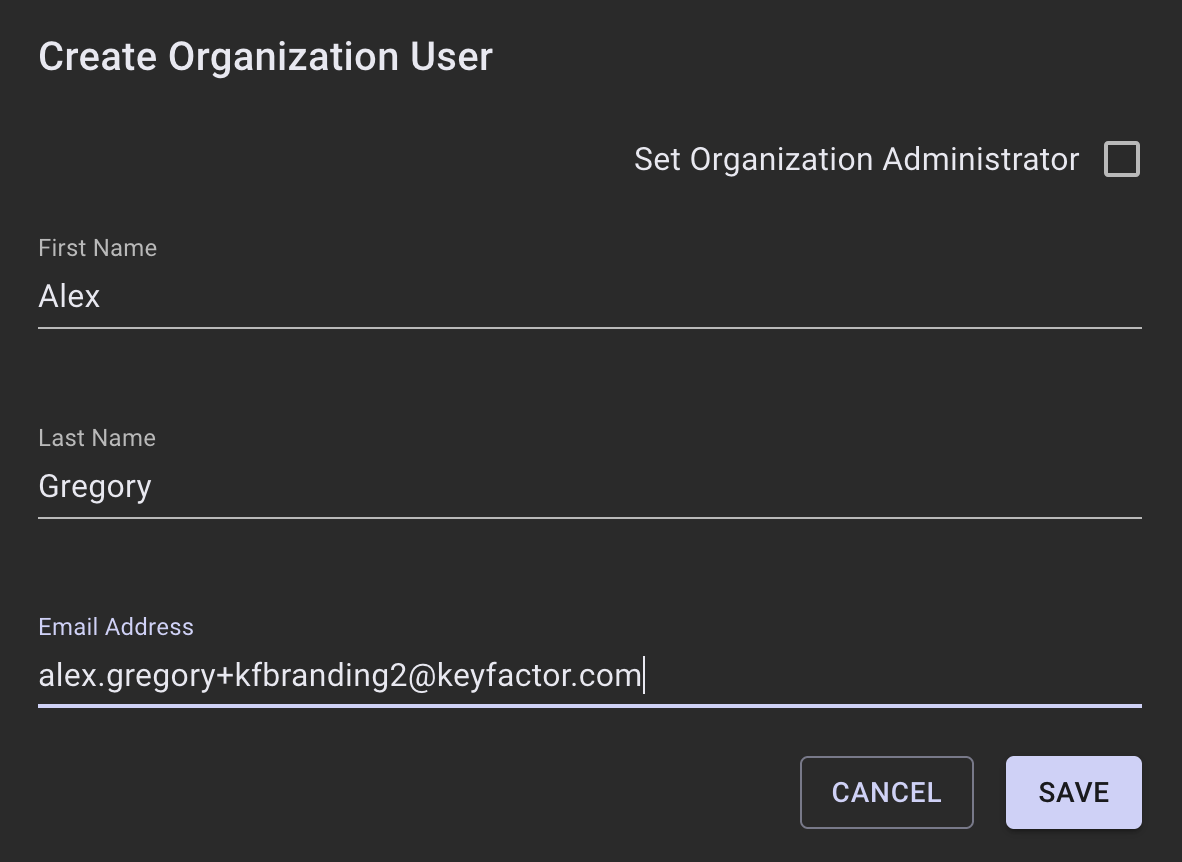
Click Save to send an email to the address entered, which will include a link to register and set a password.
Optional: Select Set Organization Administrator to allow the user to access the organization settings and perform these steps.

The new user will be added with the status of Unverified until the user registers and sets a password in the Keyfactor SaaS Portal.
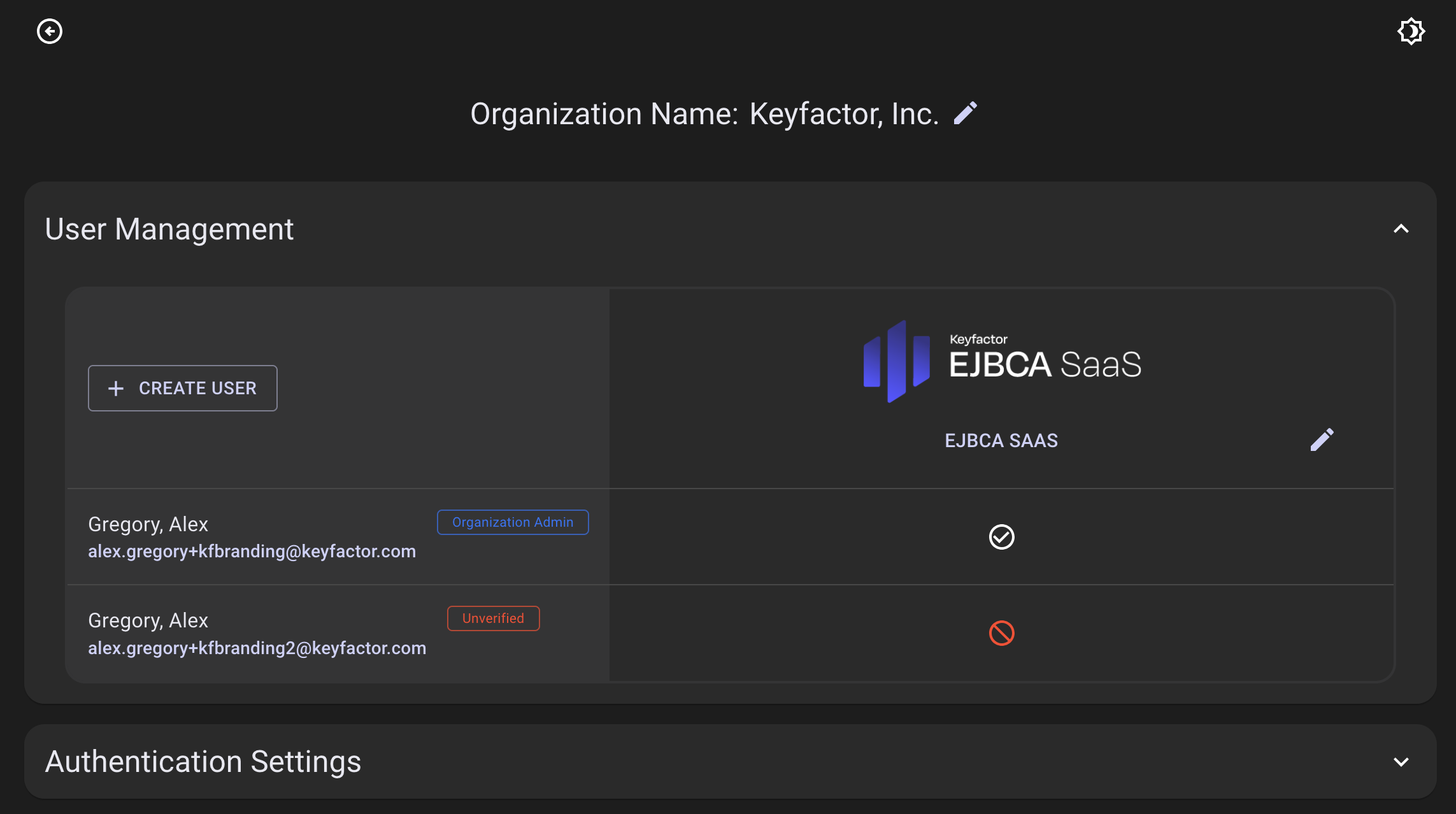
Step 3 - Provide Registration Access
Provide the user permissions by clicking the 🚫 icon.
A dialog will appear, confirming whether you would like to provide the user access to the Keyfactor SaaS Portal.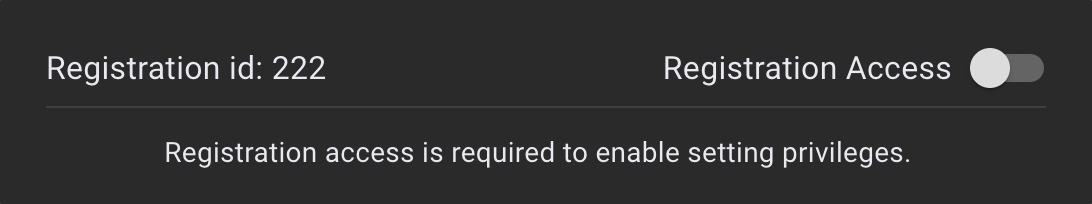
Click the Registration Access toggle to provide the user access to the deployment that is identified in the selected column.
Providing registration access gives the user access to the following permissions.
Manage Users: Allows the user to see the Manage Users feature (read) or add users (write) to the deployment. These users must exist at the organization level and be added by an organization administrator before being added to individual deployments.
Source IP: Allows the user to see the list (read) or edit the list (write) of IP addresses that are allowed to access the deployment.
Software Update: Allows the user to see the Software Update feature (read) or perform a software update (write) in the deployment.
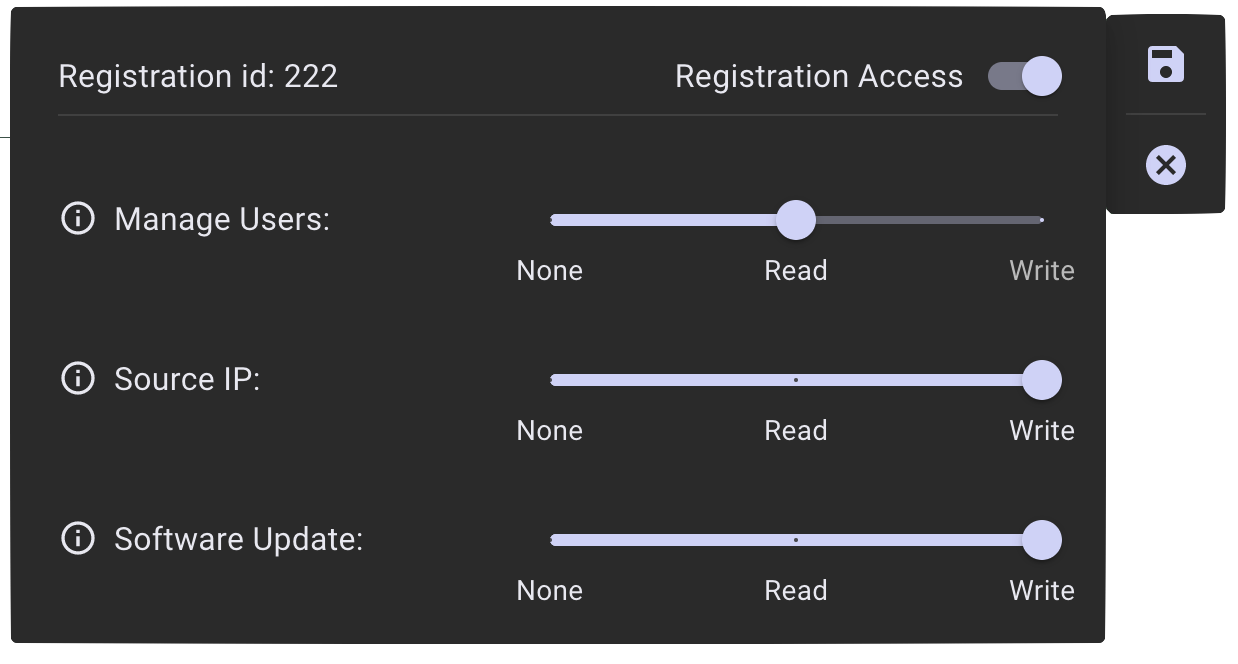
In this example, we gave this user Read permission to Manage Users, but Write permission to IP Changes and Software Updates.
Click the disk icon to save your changes.
The options shown here will be different depending on if you are managing access to EJBCA, Command, or Signum.
You can see these changes on the User Management tab of the specific deployment.
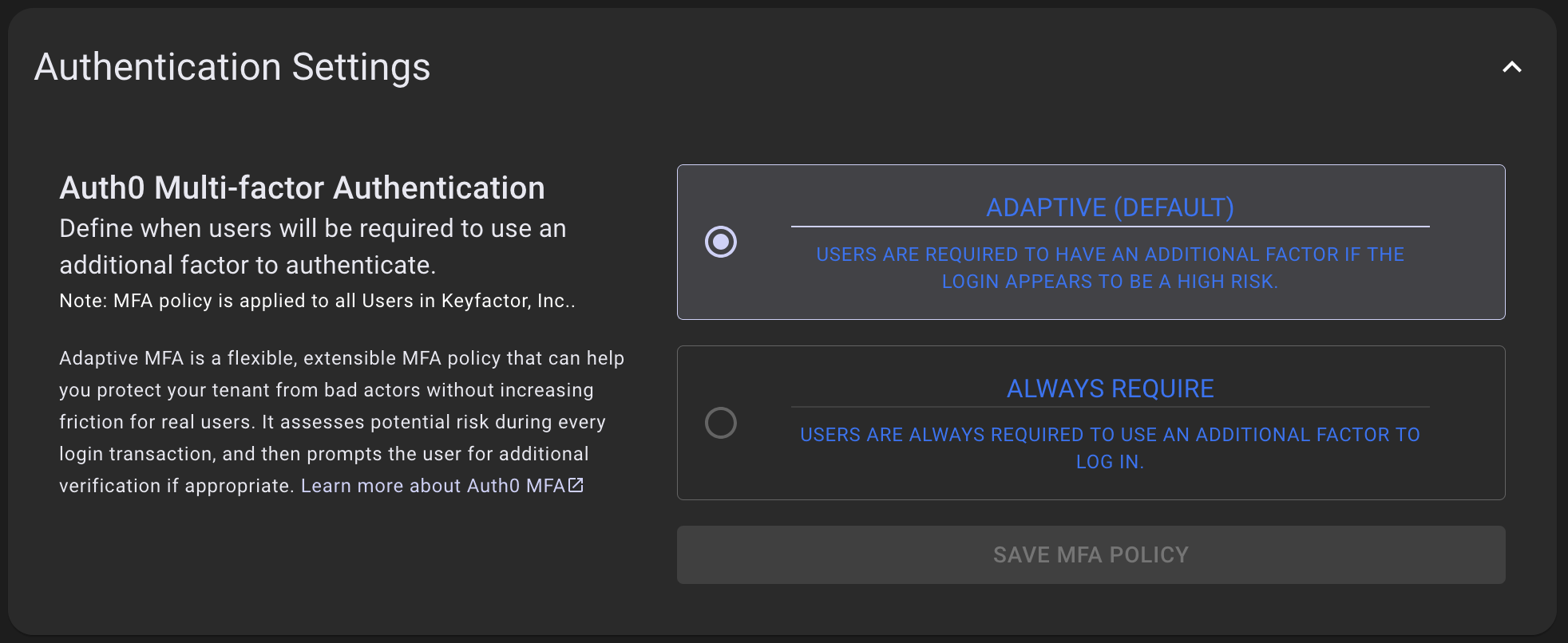
Authentication Settings
Keyfactor SaaS Customer Portal leverages 2FA as mandatory. There following settings that can be selected depending on the level of security desired.
Adaptive MFA: Adaptive MFA is a flexible, extensible MFA policy that can help you protect your tenant from bad actors without increasing friction for real users. It assesses potential risk during every login transaction, and then prompts the user for additional verification if appropriate. For more information, refer to the Auth0 by Okta documentation on Adaptive MFA.
Always Require: MFA is required for all logins every time a successful password is entered.
Expand the Authentication Settings accordion to access the settings.
During a login transaction, Adaptive MFA calculates an overall confidence score based on analysis of three risk assessments:
Assessor | Risk Signal | How it is computed |
|---|---|---|
| User attempts to sign in from a device that has not been used to access the account in the last 30 days. | User agent and browser cookies identify a device. At login time, the device information is compared to the list of devices for the account. |
| User attempts to sign in from a geolocation that indicates an impossible travel situation when compared to the last login. | The distance between the last valid location and the location of the attempted sign in is computed; the time difference between the sign in attempt is used to compute a hypothetical travel velocity. Velocity is compared to a reasonable travel velocity. |
| User attempts to sign in from an IP address known to be associated with suspicious behavior. | Auth0 uses intelligence from traffic events to determine the likelihood that the IP address has been used by bad actors to perpetrate high velocity attacks. |
Overall Risk Score | A combination of all 3 factors above. | Auth0 uses all 3 scores to assign an overall score. Use Actions if you want to implement your own business logic. |
.png)