pkimetal Validator
ENTERPRISE
The pkimetal meta linter is a tool developed by Sectigo that combines all extant linters behind a REST API and packages them in a container.
About Linters
Certificate Linters (and linters in general) are a tool used by various public certificate issuers, normally trusted by the browser root stores and members of CA/Browser Forum in order to guard against accidental misissuance. A linter contains profiles which match as closely as possible to the CA/Browser Forum Baseline Requirements, as well as the ancillary requirements defined by the various root programs. When a certificate is passed in through a linter along with a specified profile, the linter can answer whether a certificate matches that profile or not, allowing CAs to roll back issuance (or revoke after the fact) if a certificate is found to be faulty.
The pkimetal meta linter
pkimetal combines all extant linters into a single package behind a unified REST API, and deploys them in a simple container. While linting has been available in EJBCA prior to version 9.2 through the External Command Validator, use of this validator has required the linter to be present locally in script form on the local machine. For such a secure environment as a public CA, having your CA software call to hardware local scripts is far from optimal. Additionally, placing and maintaining such a script on certain deployment environments (such as containers, the Keyfactor Appliance, or on the cloud) can be challenging.
Using the pkimetal Validator
The pkimetal Validator connects to pkimetal through its REST API
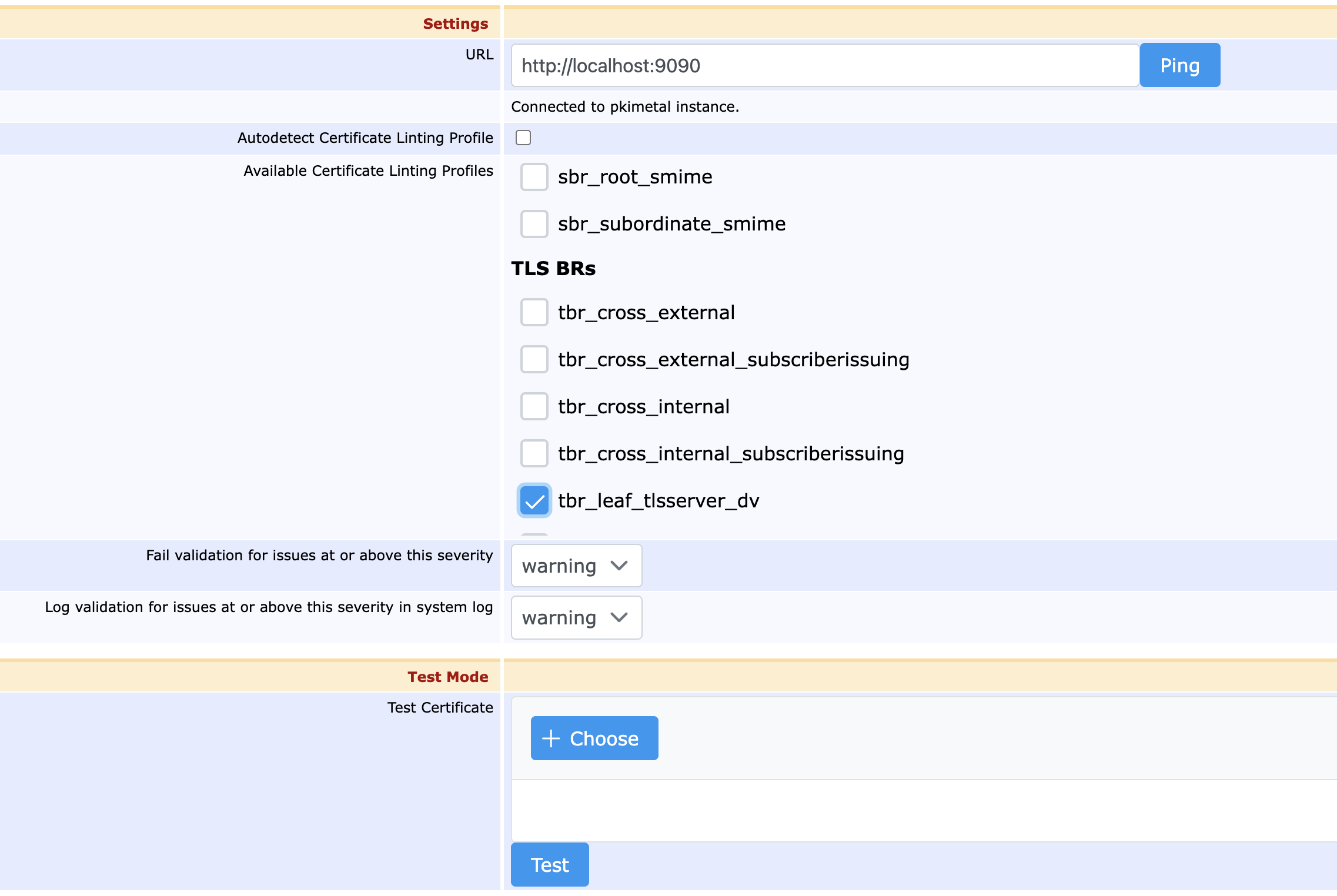
The available fields cover the following:
Field | Description |
|---|---|
URL | The URL to the pkimetal container, in the format <hostname>:port. The Ping button verifies the connection and retrieves transitive values from it, such as available profiles. |
Autodetect Certificate Linting Profile | Selecting this option allows pkimetal to select the most likely profile on its own. |
Available Certificate Linting Profiles | Sorted by category, this lists what profiles pkimetal is able to check for. |
Fail validation for issues at or above this severity | If pkimetal returns any errors, errors mapped to this severity level will cause issuance to roll back. |
Log validation for issues at or above this severity in system log. | While some issues returned by pkimetal may not be severe enough to warrant a rollback, others might want to be noted by CA administrators in order to amend for future issuance. Such output will be written to EJBCA’s log. |
Test | Allows for the upload and test of a certificate, to verify functionality. |
Output
As it may be of interest to administrators to directly be informed of the reason for a rollback, the results of a validation fail are written to the EJBCA RA UI, as well as returned through EJBCA’s REST API.
.png)