VA Setup for CRL Downloader Service
In this VA setup, the CA Hardware Appliance publishes CRLs in an external server. The VA Hardware Appliance uses the CRL Downloader service to fetch CRLs from the external server.
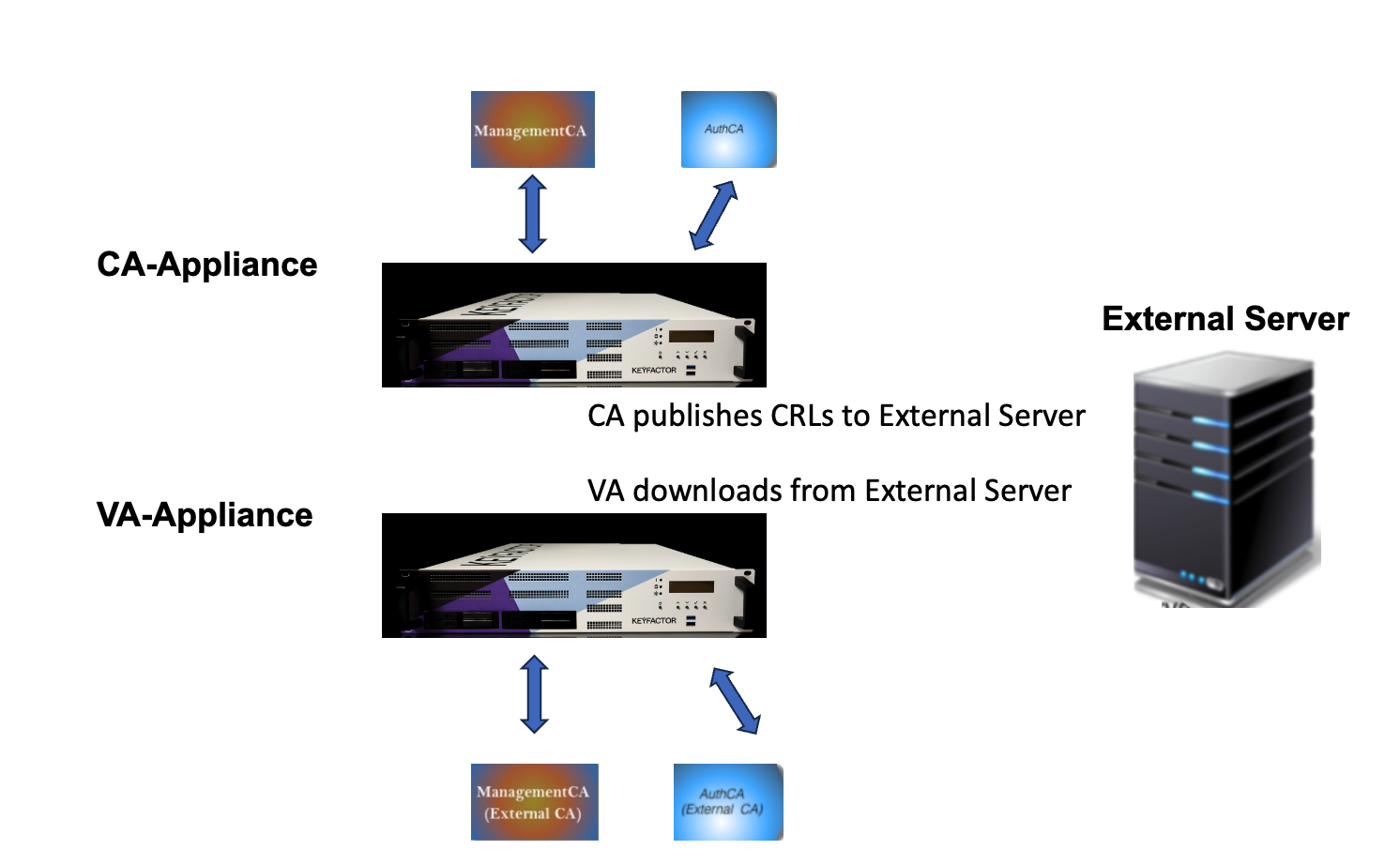
With the configuration described below, the VA can use the CRL Downloader service to fetch and store the CRLs. Precondition is that the CA is already publishing CRLs in the external server. Our example is based on the ManagementCA. However, it is also applicable to other CAs.
Configuring the CRL download service
- In the CA Hardware Appliance, import the ManagementCA as ExternalCA as described in the section Import RootCA as External CA in node A.
Go to the EJBCA Enterprise Administration
In the sidebar, in the CA Functions section, select Certification Authorities.
Select ManagementCA, (External CA), and click Edit CA:
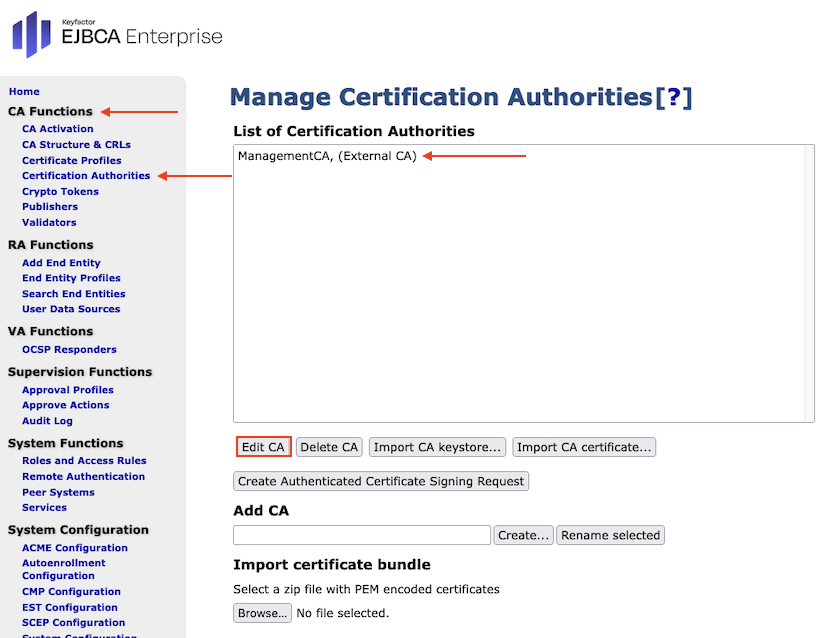 Edit ManagementCA
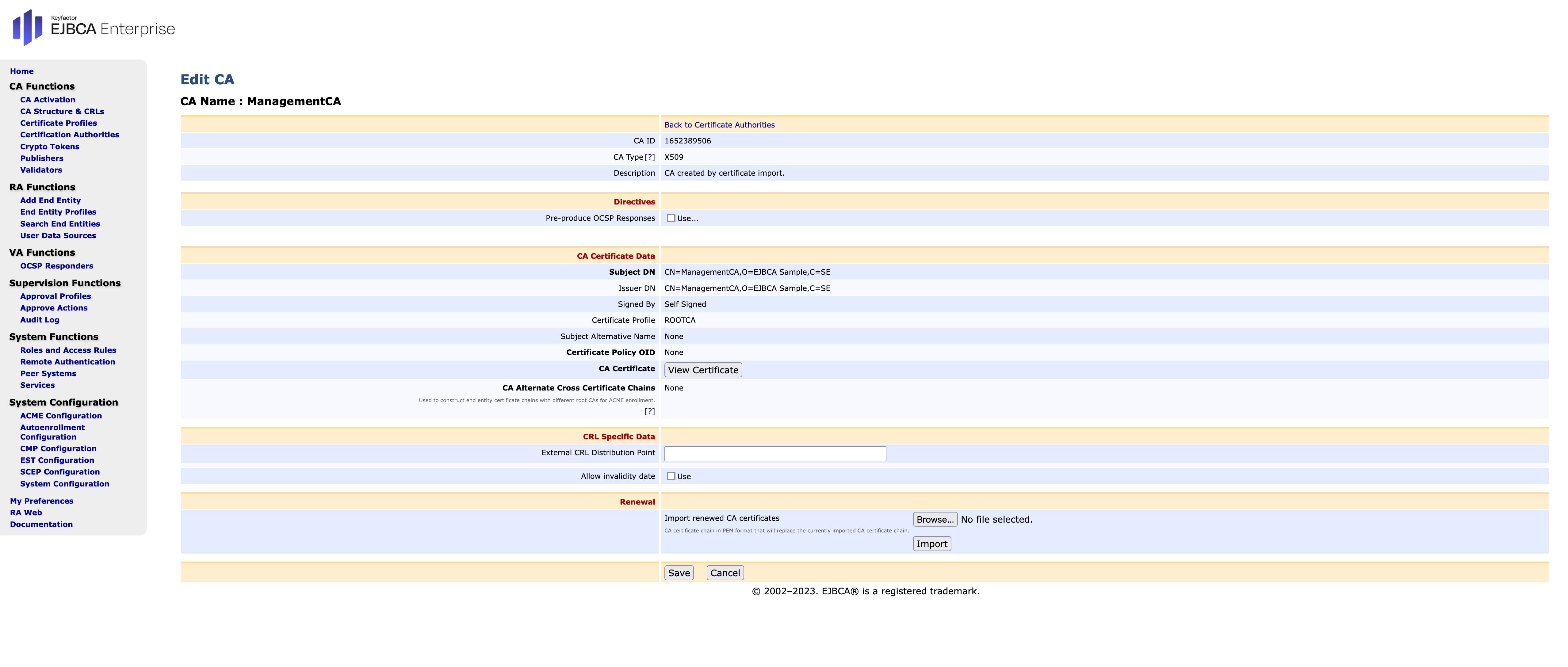
Edit ManagementCA- The Edit CA form opens.
- External CRL Distribution Point: Enter the URL from the external server where the CLR is located.
- Click Save to continue.
- In the EJBCA Enterprise Administration
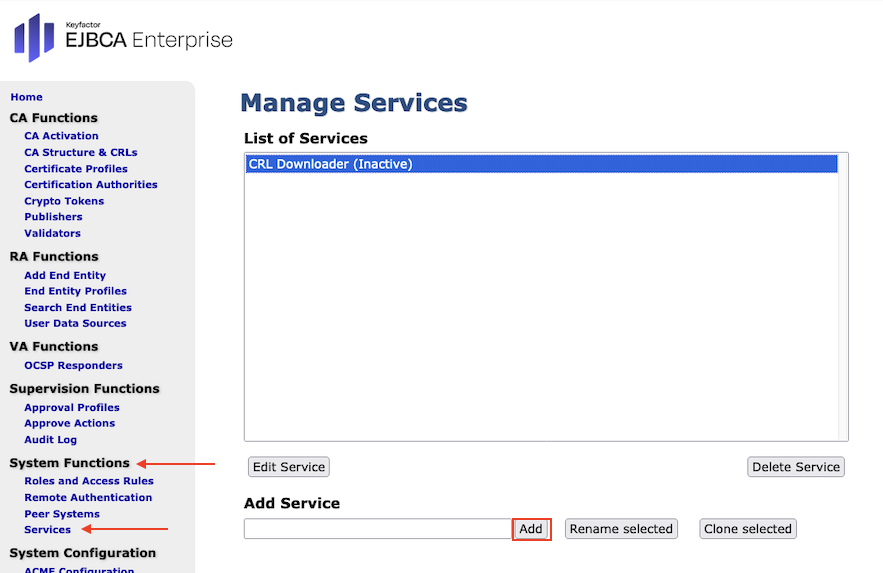
- In the sidebar, in the System Functions choose Services.
- In the field Add Service enter CRL Downloader and select Add.
Select CRL Downloader (Inactive) and click Edit Service:
 Add CRL Downloader service
Add CRL Downloader serviceSelect Edit Service to open the form Service: CRL Downloader and enter the following values.
Confirm with Save.
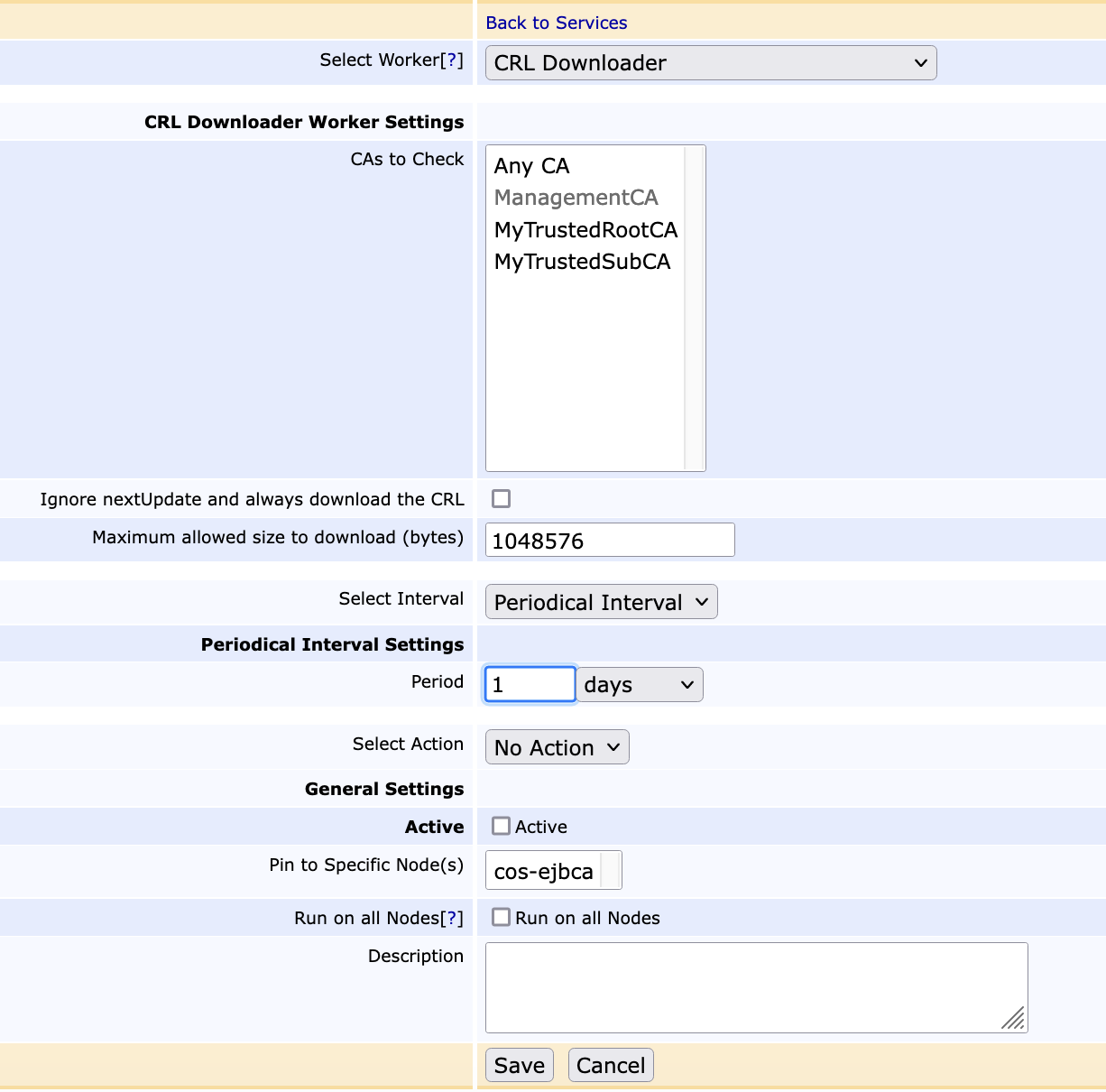
- Select Worker: Select CRL Downloader
- CAs to Check: Select ManagementCA
- Ignore nextUpdate and always download the CRL: Enable this option.
When this option is enabled, the CRL will be downloaded and the nextUpdate
values configured in the CA are ignored. - Period: Specify 1 Days
- Active: Enable this option.
- Pin to Specific Node(s): Enter cos-ejbca
 Configure CRL Downloader service
Configure CRL Downloader service
The service to download CRLs from the external server is now configured.
Configuring OCSP binding
The OCSP key binding must be configured for authenticating the VA Hardware Appliance to sign the responses of OCSP requests. This is described in the section Create OCSP Key Binding in VA and publisher in CA Hardware Appliance, subsection Creating a key binding in the VA Hardware Appliance. Follow these steps and make the following changes in naming references:
- ManagementCA instead of PeerMgmtCA
- The CA Hardware Appliance is analogous to the CA where ManagementCA is installed.
When OCSP key binding is configured, the VA Hardware Appliance is ready to respond in OCSP requests like the following. Note that <unknown_status_certificate>.pem is a certificate signed from ManagementCA:
Run as user:
openssl ocsp -issuer ManagementCA.pem -CAfile ManagementCA.pem -cert <unknown_status_certificate>.pem -req_text -url http://<VA_application_interface>:80/ejbca/publicweb/status/ocspThe output looks like the following:
OCSP Re que s t Data : V e r s i o n : 1 ( 0 x0 ) R e q u e s to r L i s t : C e r t i f i c a t e ID : Hash Alg o r i th m : s ha 1 I s s u e r Name Hash : C45788773EDFD1434ED1D8A3C6E3CF176D78B82A I s s u e r Key Hash : 320 A617F62005EF984C12ADA0D981A899A300F68 S e r i a l Number : 0758 A7080983F917 Re que s t E x te n s i o n s : OCSP Nonce : 04106 C08FFAF175C99CC261E9543CBA525C3 Re s pons e v e r i f y OK <u n k n o w n _ s ta tu s _ c e r t i f i c a te >.pem : good This Update : Dec 18 1 0 : 3 7 : 2 2 2014 GMT
.png)