Access: Managing Trusted CAs
It is possible to add certificates of trusted CAs to the Software Appliance. This allows you to log in via a certificate and add client certificate accounts with matching rules based on a certificate.
Proceed as follows to add and use a trusted CA:
Log in to your Software Appliance and open the Access page.
In the section Trusted CA, click the button Upload Certificate to search for and upload the certificate for the Trusted CA.
Log out of the Software Appliance.
Log in again using the client certificate you uploaded for the Trusted CA.
Open the Access page and add a new client certificate account with a matching pair of Match Value and Match Type for the logged in user.
It is possible to add multiple Trusted CAs. By adding a Trusted CA the owner is granted access to the Software Appliance.
The TLS Verification depth is used to determine the length of the certificate chain. The maximum number for the TLS Verification depth is limited to 10.
To create a 3-tier CA hierarchy means 3 Trusted CAs, as shown below. If you want to use a 4-tier CA hierarchy, there should be 4 Trusted CAs. For more information please refer to: Part 3a: EJBCA Configuration
The following is an example of a 3-tier CA hierarchy:
Root CA,
Intermediate CA,
and Issuing CA
The TLS Verification depth is set to four. In this case, no further Trusted CAs can be added.
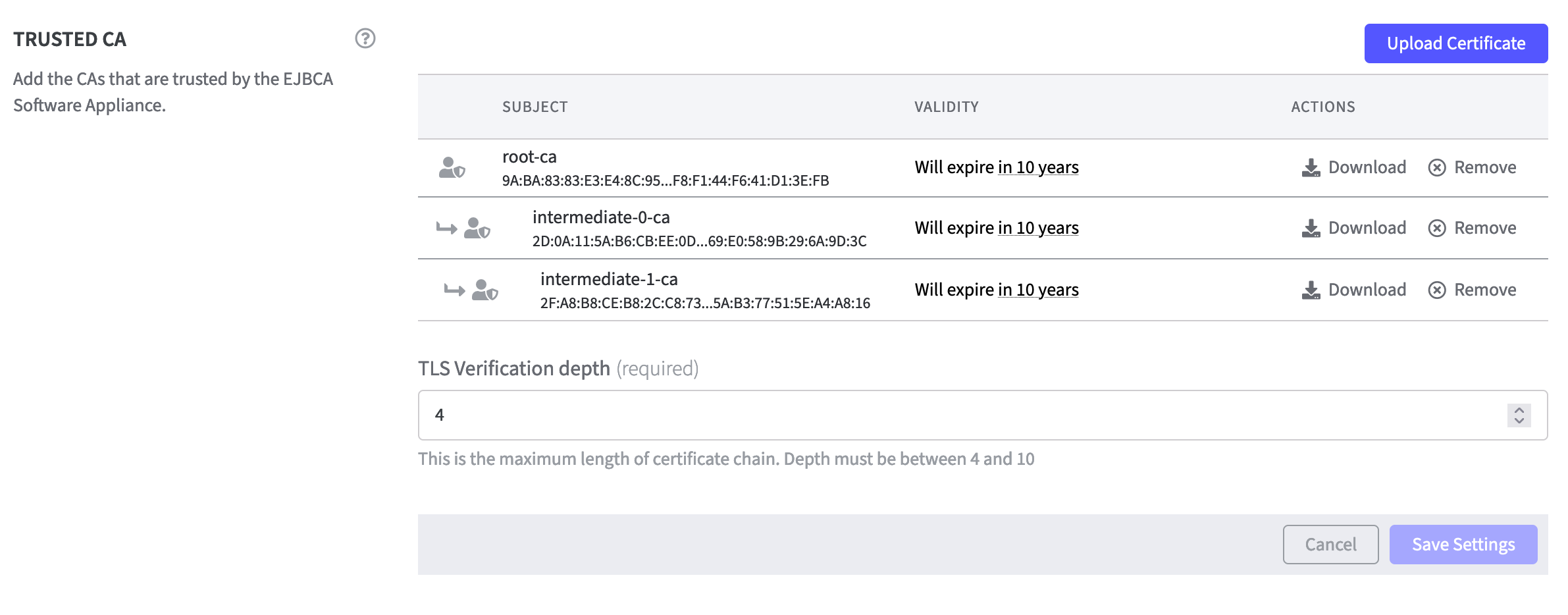
If you want to add more Trusted CAs, you must increase the TLS Verification depth.
If you want to reduce the TLS Verification depth, the surplus Trusted CAs must first be removed.
.png)