Navigating EJBCA SaaS Portal
The EJBCA SaaS portal allows navigation of the EJBCA SaaS application and getting information regarding the EJBCA SaaS installation.
Access the portal at any time by navigating to https://portal.az.keyfactorsaas.com and logging in with the appropriate credentials.
Dashboard
The portal displays information relating to the customer installation and the EJBCA Dashboard shows essential information about the overall health of the EJBCA cluster.
Information is displayed pertaining to the installation and the Dashboard graphs and indicators include:
- System Health: Displays the system health status of EJBCA for the issuing CA cluster.
- We hope that this doesn't happen, but in the event it does this may mean that there could be an issue with your EJBCA SaaS installation. Should this icon turn red, please contact Keyfactor Support.
- Total Certificates: Overall certificates generated by the system during its lifetime.
- Today: Certificates generated in the last 24 hours displaying trends every two hours to detect when spikes in generation happen.
- Certificates By Profile: Shows the top three profiles that have generated certificates all time by percentage.
- Certificate Expiration Quantity: Shows the quantity of expiring certificates over the next 30, 60, and 90 days.
Profile Menu
Within this menu you will be able to view Profile details, switch between light and dark mode, and also Switch Deployments.
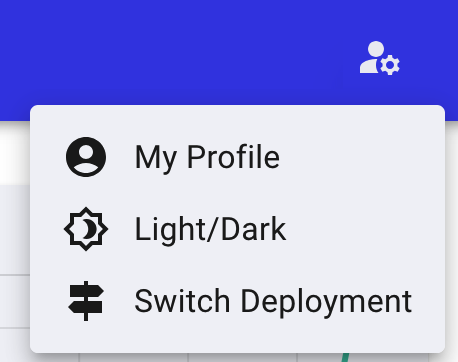
Viewing profile details will allow you to see the permissions you have within this specific deployment. To gain access to additional features, you will need to contact your organization administrator.
Switching deployments will take you back to the tiles for all the deployments within the organization. For more information, see Use the Organizations feature.
Announcements
The Announcements page provides access to any announcements that the Keyfactor team has deemed necessary for you to know. This could be for any planned maintenance, outages, or upgrades made available. Marking the announcement as read will do this only for the current logged in user.
Compliance
The Compliance page includes the necessary information to complete internal compliance questionnaires.
The FAQ tab provides some of the necessary information that internal compliance teams may need to perform compliance audits.
The CP and CPS tabs provide links to download a Certificate Policy (CP) and Certificate Practice Statement (CPS) template pack that can be used for writing company-specific versions of these documents. For assistance in writing these documents, please contact us at sales@keyfactor.com to start a Professional Services engagement.
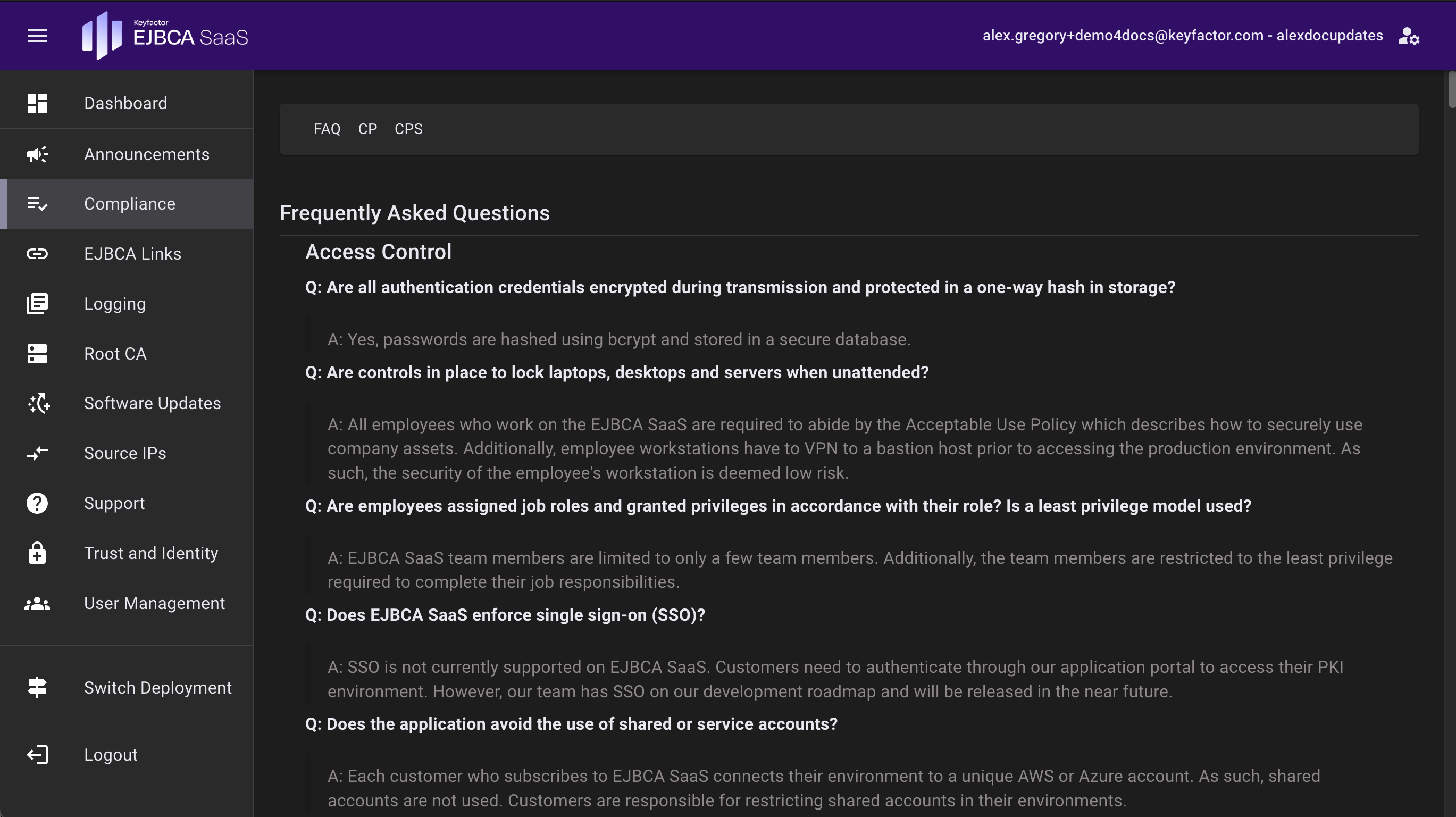
EJBCA Links
The links page will provide access to the EJBCA Administration Interface, RA Web, Root CA Admin Web, and other service links that will be useful for things like OCSP and CRL when configuring your EJBCA Certificate Authorities.
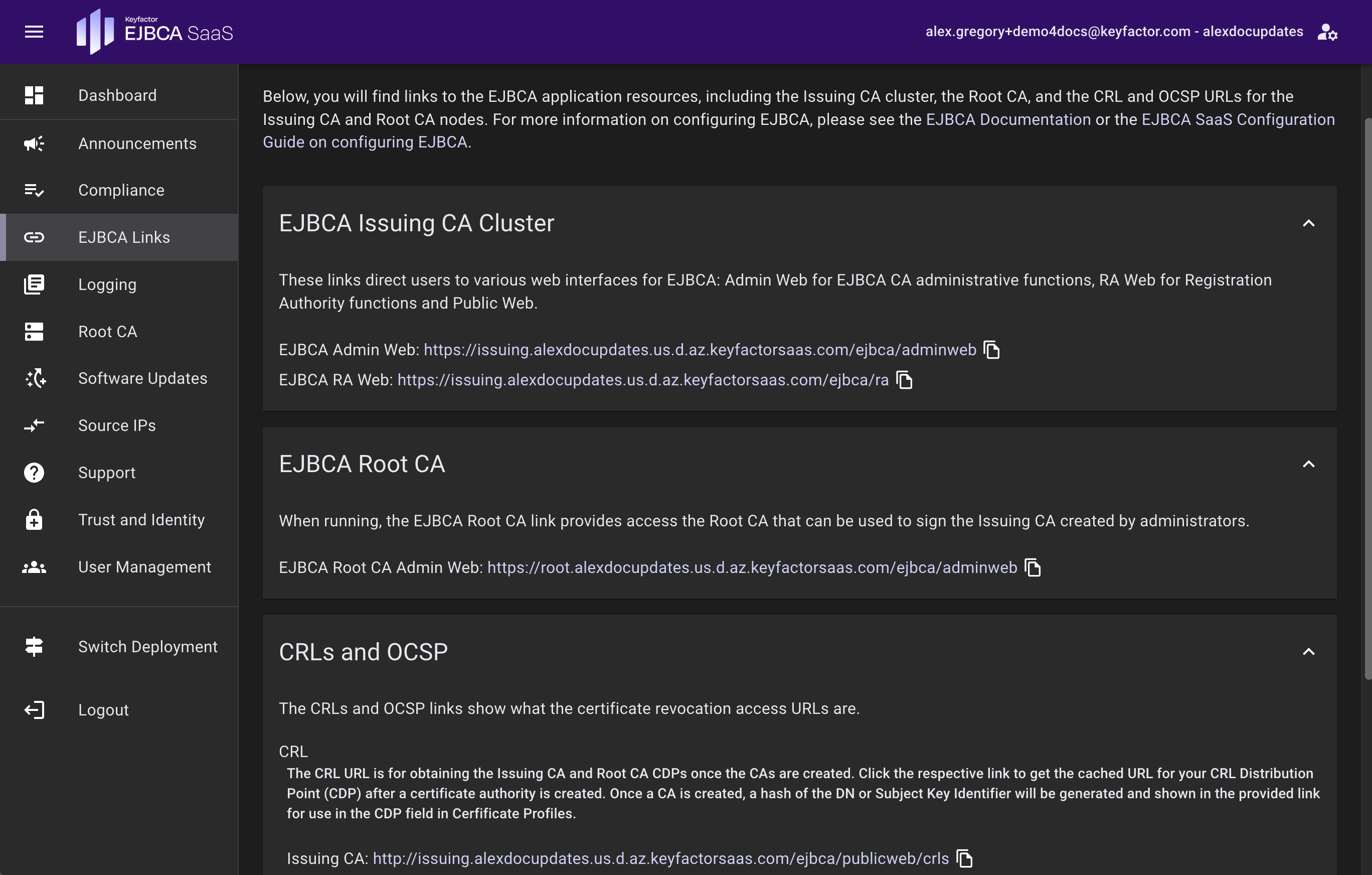
EJBCA Issuing CA Cluster Access
Access the EJBCA cluster at any time by bookmarking the link to the Issuing CA cluster in your web browser. The EJBCA Links page can also be used to access the EJBCA Issuing CA cluster and list relevant links. When running, the EJBCA Root CA link allows access the Root CA that can be used to sign the Issuing CA created by administrators.
CRLs and OCSP
The CRLs and OCSP section shows what the CRL URL is for the Issuing CA and Root CA clusters. Click the respective link to get the cached URL for your CRL Distribution Point (CDP) after a certificate authority is created. Once a CA is created, a hash of the DN or Subject Key Identifier will be generated and shown on the provided link.
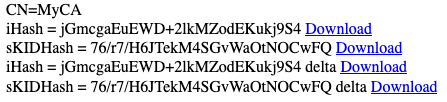
The example above shows the iHash (the ASN1 encoded DN of the issuer in a certificate) and the sKIDHash (the ASN1 encoded hash of the CA subjectKeyIdentifier). Links to both the full CRL and the delta CRL are displayed and can be used as a CDP for CAs. This URL will hold the cached URL to the CRL for better performance. For more information, refer to the EJBCA Documentation on CRL Distribution Points.
Logging
The Logging page allows users to configure external syslog destinations for getting the EJBCA and Apache logs from the Root and Issuing CA deployments. External logging can be beneficial when troubleshooting things like certificate enrollments.
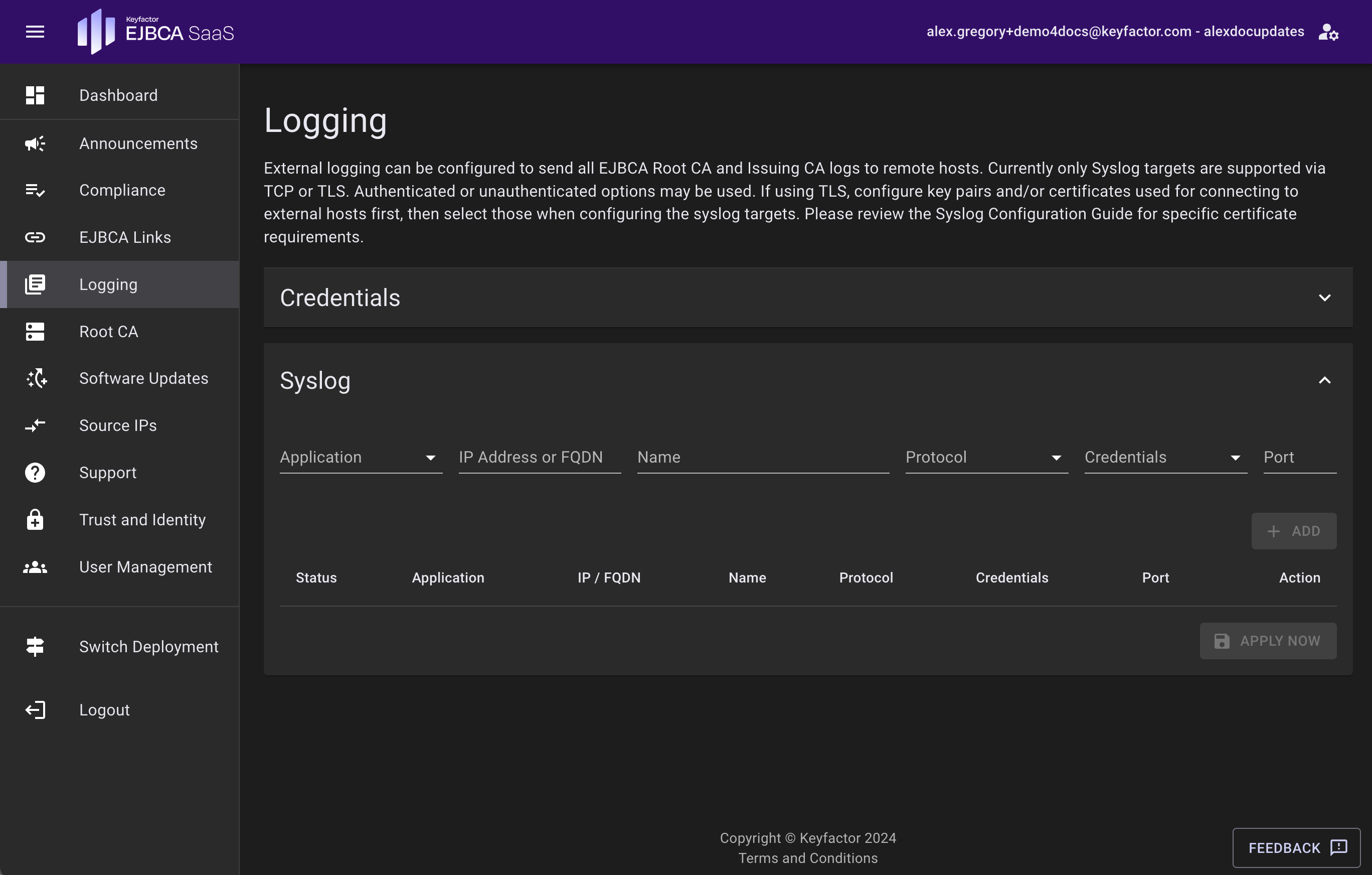
The following types of syslog streaming methods are allowed: Authenticated, Unauthenticated, and Unencrypted. For more information, see Enable Syslog Log Streaming.
Root CA
EJBCA Root CA Control and Access
The Root CA page allows for controlling the Root CA. Click Start Root CA to start the EJBCA Root CA node for 12 hours. This allows ample time to perform actions such as Signing a Sub CA, Updating a CRL, or other PKI functions. This page will be disabled during the provisioning process.
When running, the status will display when the 12-hour automatic shutdown of the Root CA will occur as well as a link to access the Root CA. The Superadmin credential issued from the ManagmentCA on the issuing CA cluster is used to access the Root CA Administrative interface. To change who can access the Root CA, navigate to the Root CA Admin Web and configure the Super Administrator Role as needed. For more information, refer to the EJBCA Documentation on EJBCA Roles and Access Rules. The Root CA is provisioned in a running state for the initial deployment and will shut itself down within 12 hours after the initial launch.
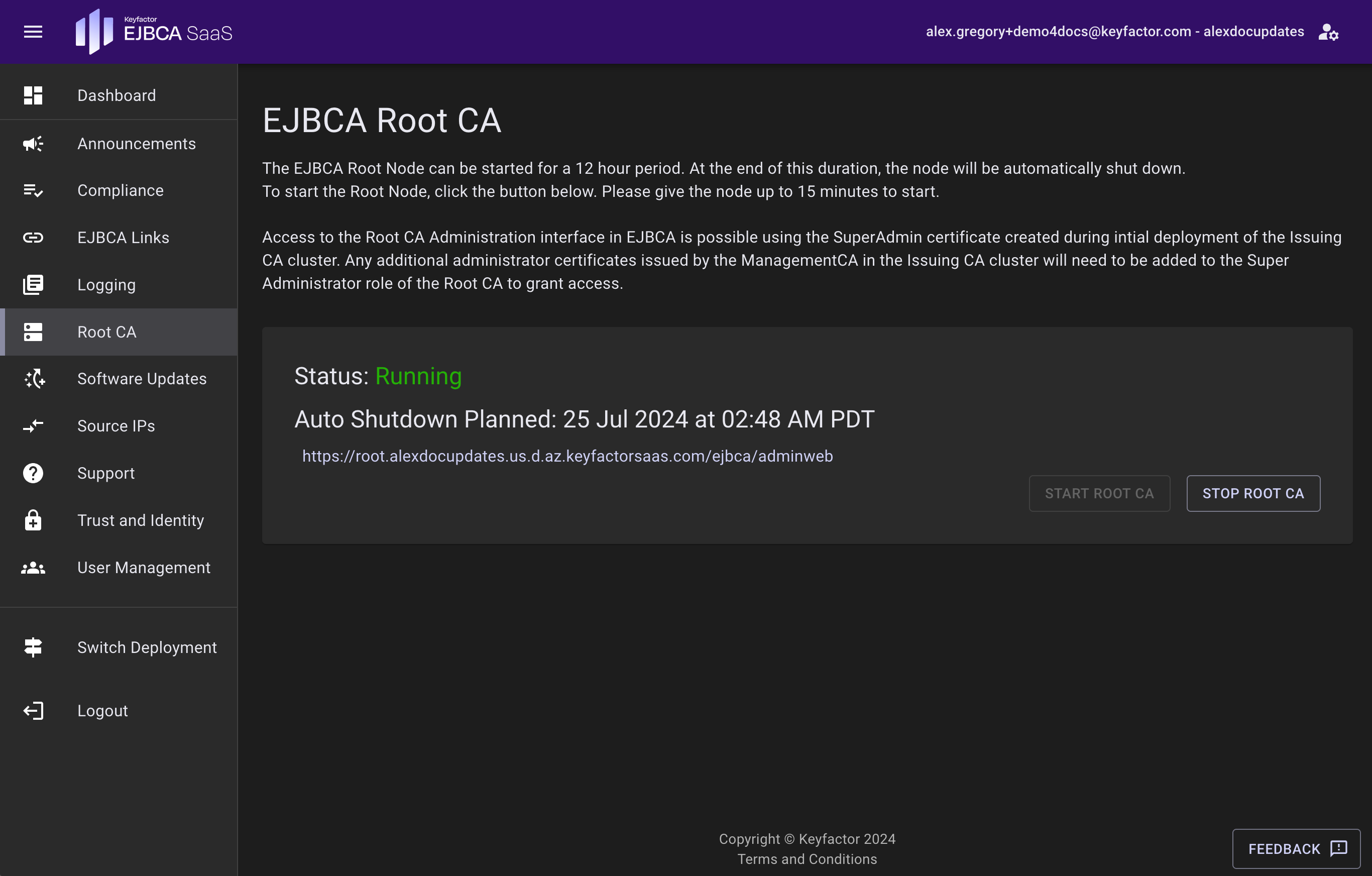
To shut down the Root CA before the planned shutdown time, click Stop Root CA.
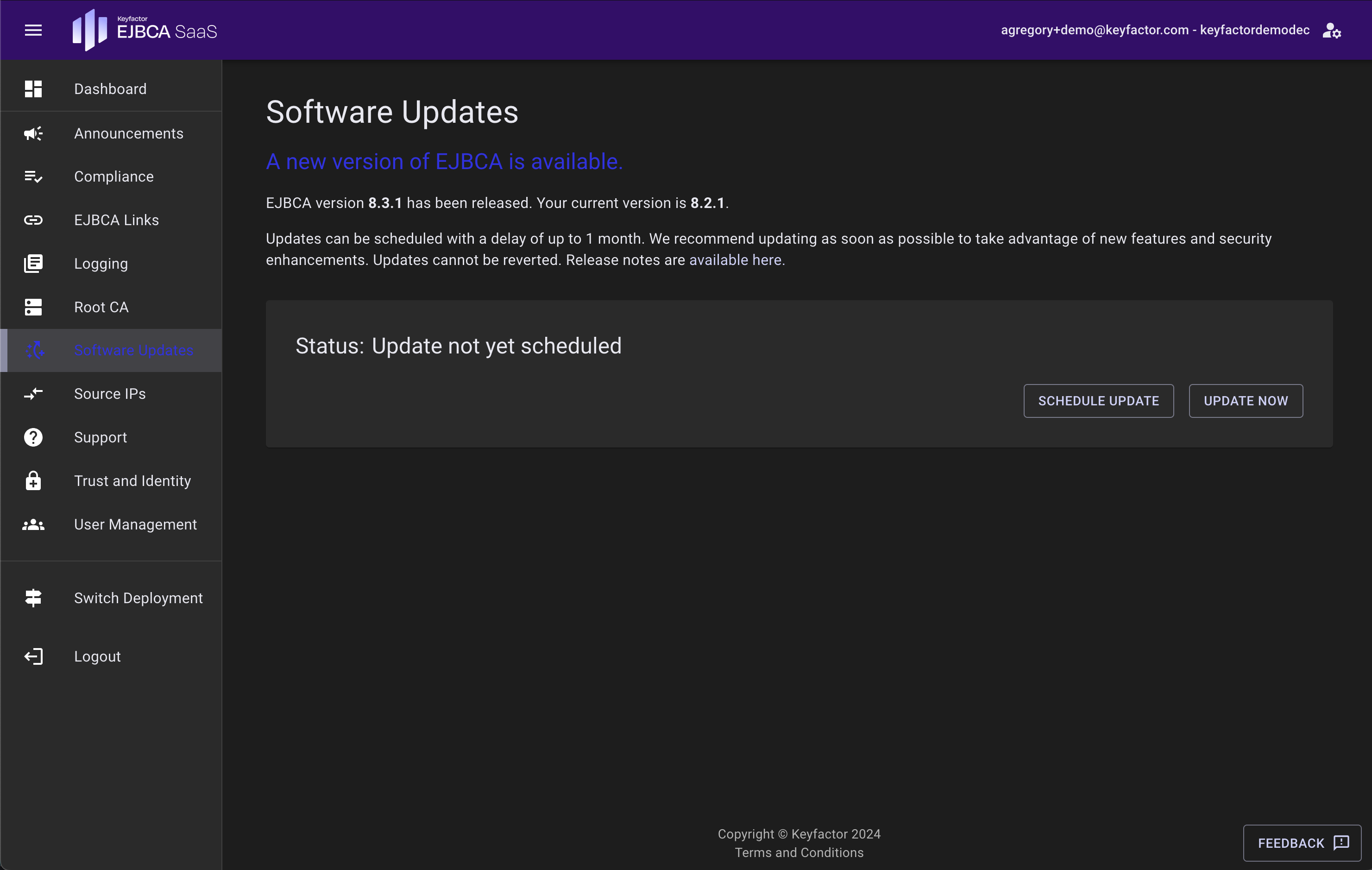
Software Updates
Any available upgrades to the EJBCA Software will be listed here. For more information on applying and scheduling upgrades to EJBCA, see EJBCA Upgrades.
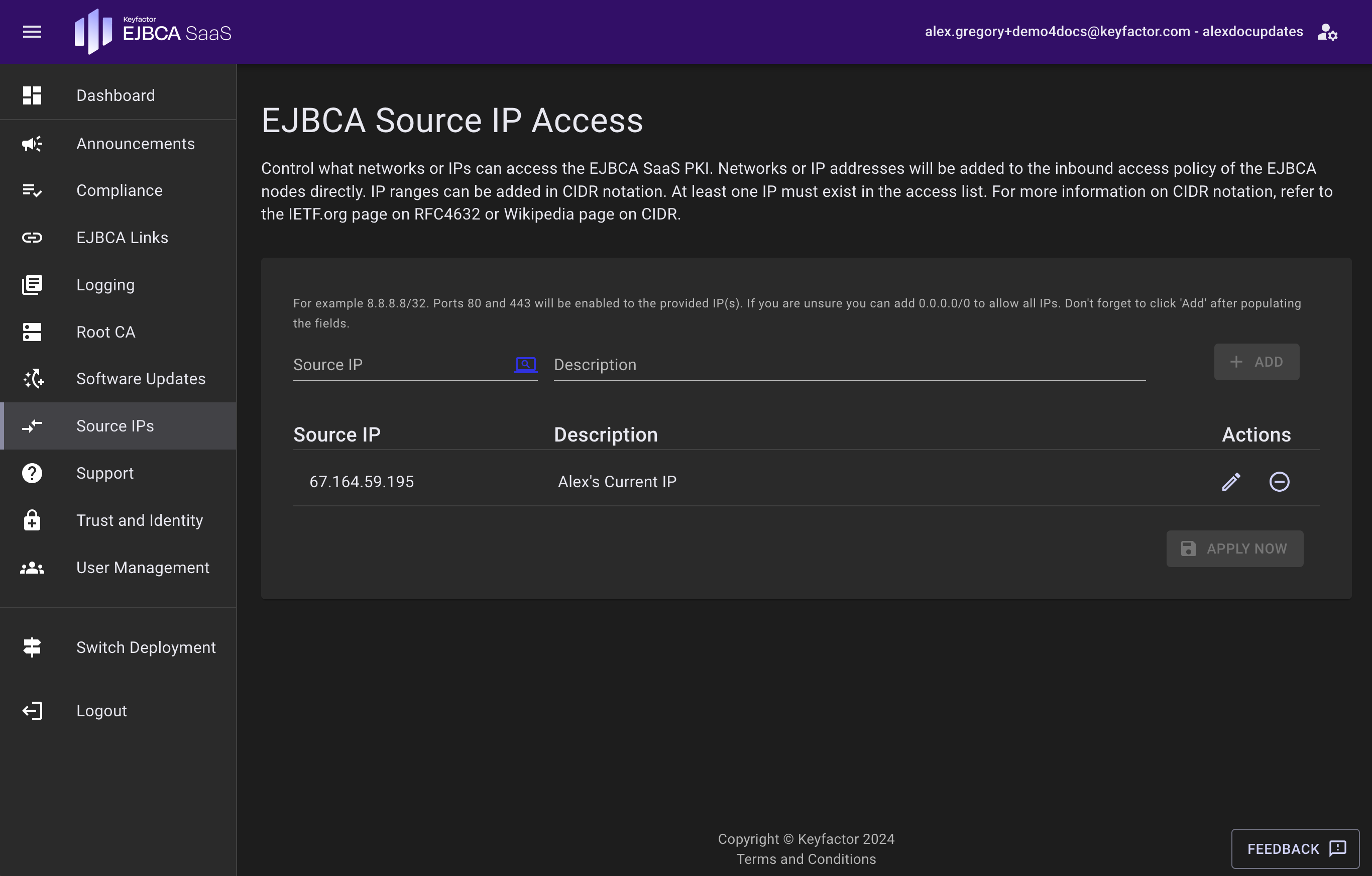
Source IPs
The Source IPs page allows control over what IPs can access the EJBCA Clusters. IP addresses here will be added to the inbound access to the EJBCA Clusters directly, and need to be added in the CIDR notation. For more information on CIDR notation, refer to the IETF.org page on RFC4632 or Wikipedia page on CIDR. This page will be disabled during the provisioning process.
Note that adding a single IP without a CIDR notation will result in it being added with /32 (single IP).
Click the get current IP button next to Source IP to populate the current IP address that the EJBCA SaaS Portal sees you coming from. This button will also populate your name in the Description field.
At least one IP must be added to the access list. A description can be added to the IP so that it can be referenced by something meaningful.
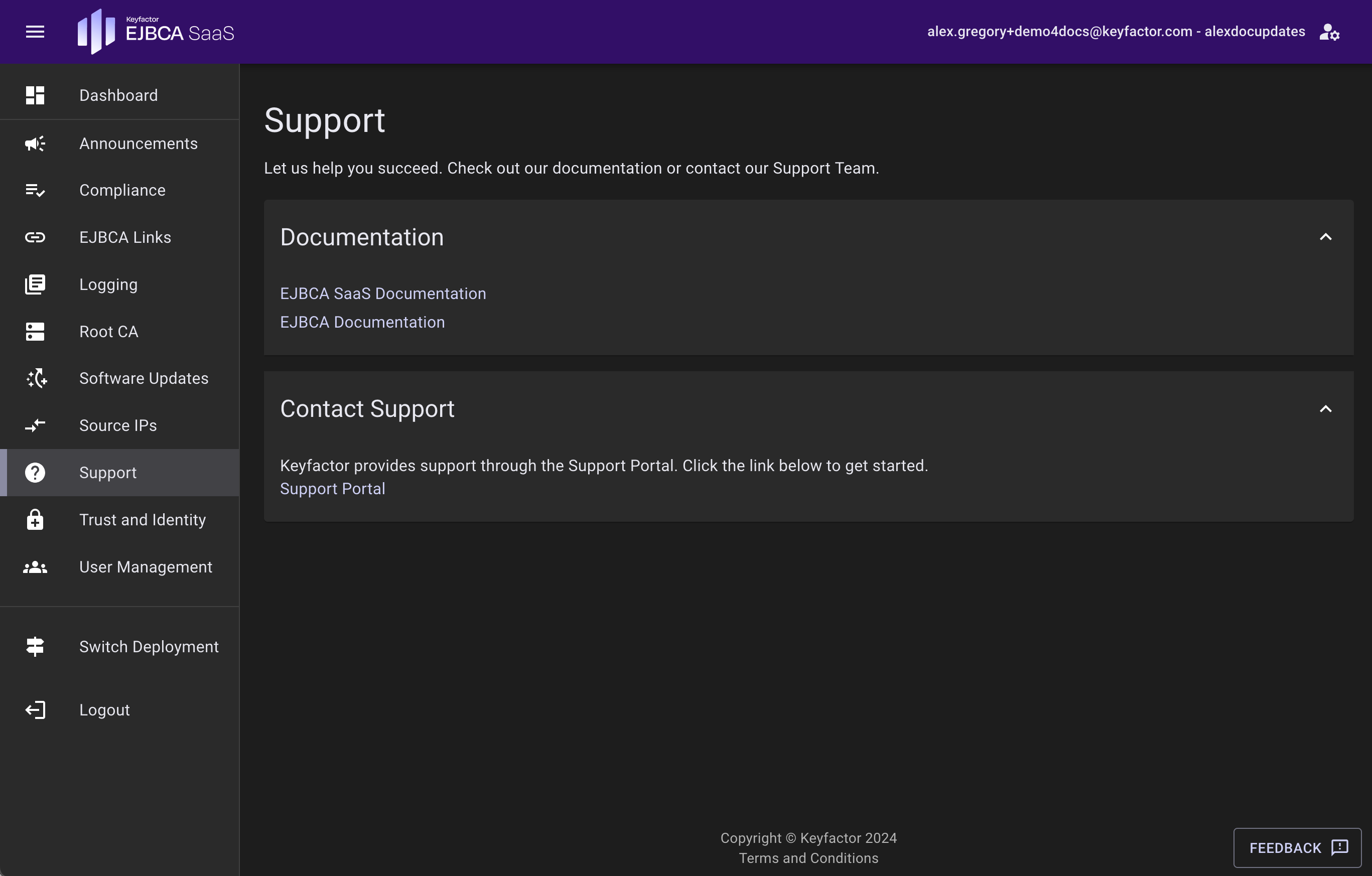
Support
The Support page provides resources for users to gain help while using EJBCA SaaS.
For helpful links to EJBCA and EJBCA SaaS documentation, expand the Documentation section.
To contact support, expand the Contact Support section and use the links provided to access support.
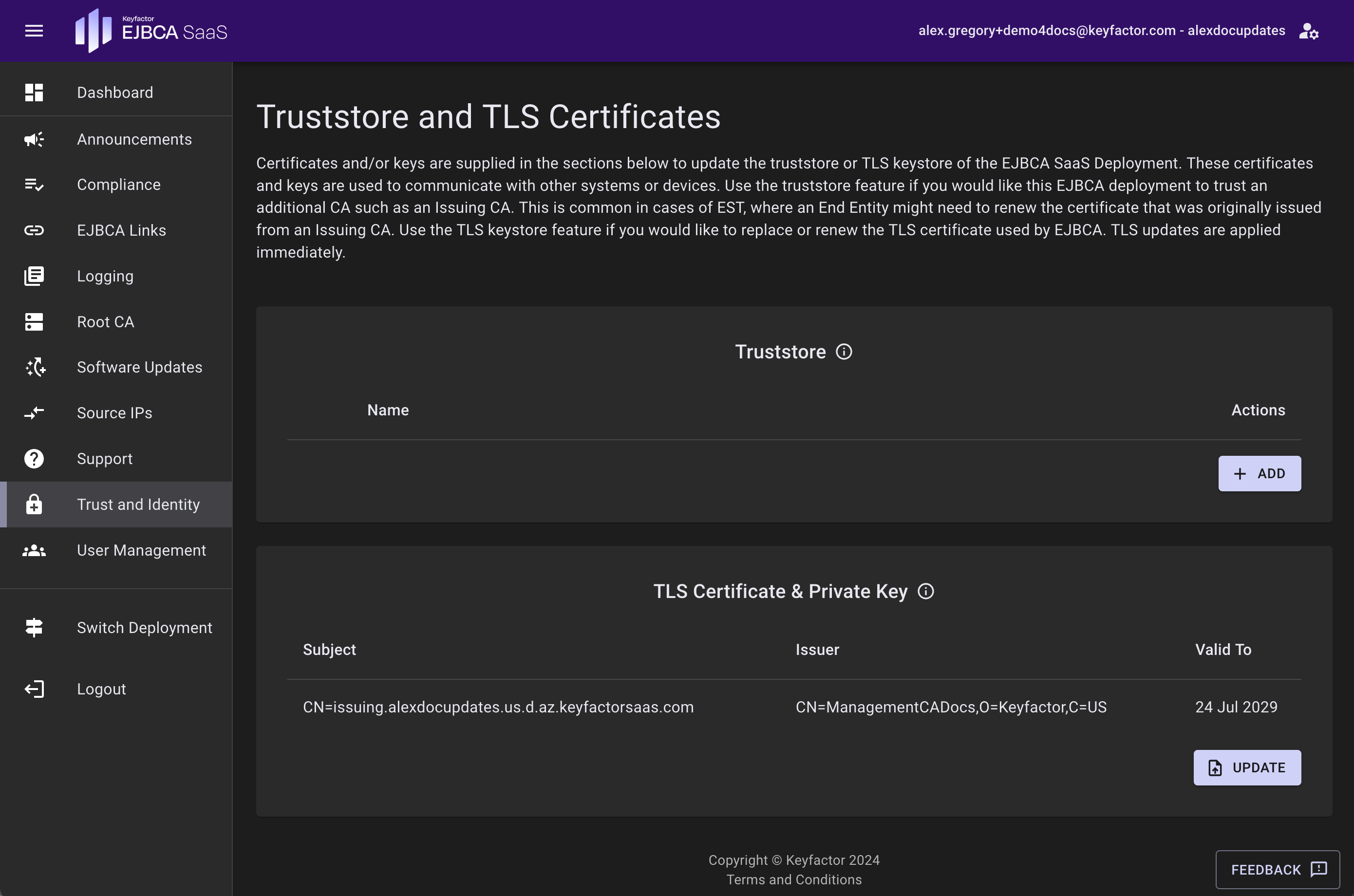
Trust and Identity
Certificates and/or keys are supplied here to update the truststore or keystore of the EJBCA SaaS Deployment. These certificates and keys are used to communicate with other systems or devices. Use the truststore feature if you would like this EJBCA deployment to trust an additional CA such as an Issuing CA. This is common in cases of EST, where an End Entity might need to renew the certificate that was originally issued from an Issuing CA. Use the TLS keystore feature if you would like to replace or renew the TLS certificate used by EJBCA. TLS updates are applied immediately.
The truststore contains the certificate authority certificates trusted by EJBCA. Updating the truststore here adds to the truststore in the deployment and does not replace the existing truststore that was provisioned with the system. Note: the full chain is required.
A keystore is used to store private keys and identity certificates that EJBCA SaaS should present for verification. This can be a CA certificate, key and issued certificate bundle. Please have the CA and issued certificate in a single chain file.
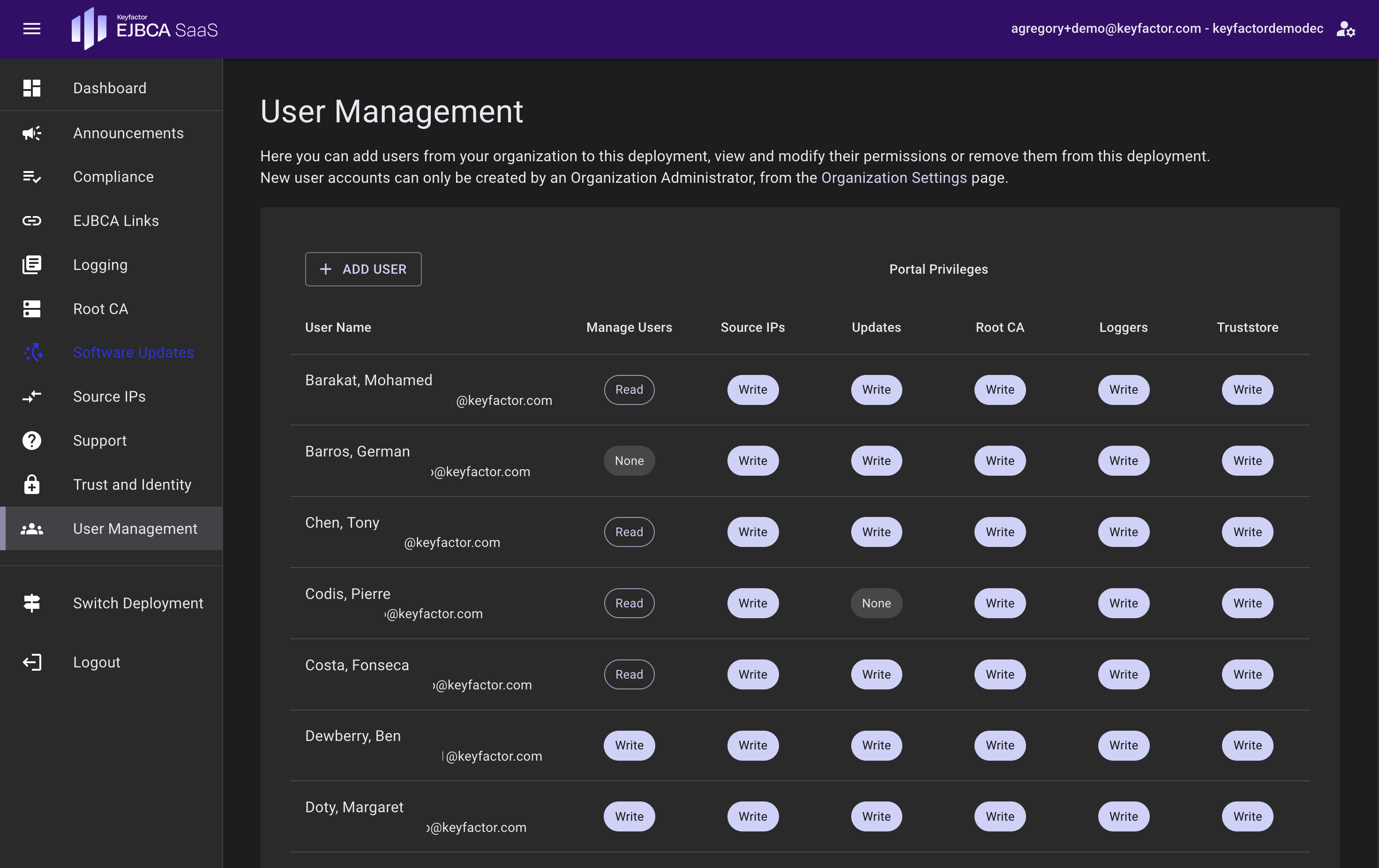
User Management
The User Management page allows for the management of users that have access to and can perform actions in the EJBCA SaaS Portal. Permissions can be granted to view, edit or restrict access to the Source IP, Root, and Logging pages. Users will appear here only after being added at the Organization level.
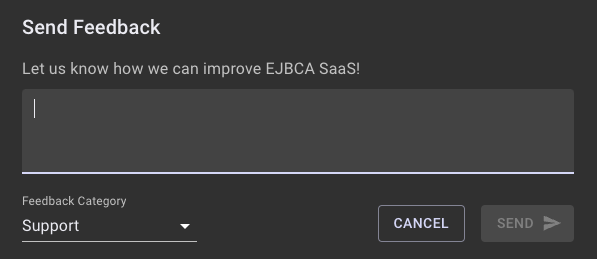
Providing Feedback
Please let us know how we can improve EJBCA SaaS. Whether it is something not behaving as expected, or a feature request, please let us know. To send feedback, click the Feedback button at the bottom right of the portal page. The feedback category should be aware of the current page, but an alternate page can also be selected from the Feedback Category list.
Switch Deployment
This option takes you back to the deployment selection tiles.
Next - EJBCA SaaS Configuration
The EJBCA SaaS portal allows navigation of the EJBCA SaaS application and getting information regarding the EJBCA SaaS installation.
Next, for information on configuring EJBCA SaaS and setting up Certificate Authorities, see EJBCA SaaS Configuration Guide.
.png)