Certificate Field Validators
Certificate field validators are run on specific fields on the CSR, such as the dnsName SAN field.
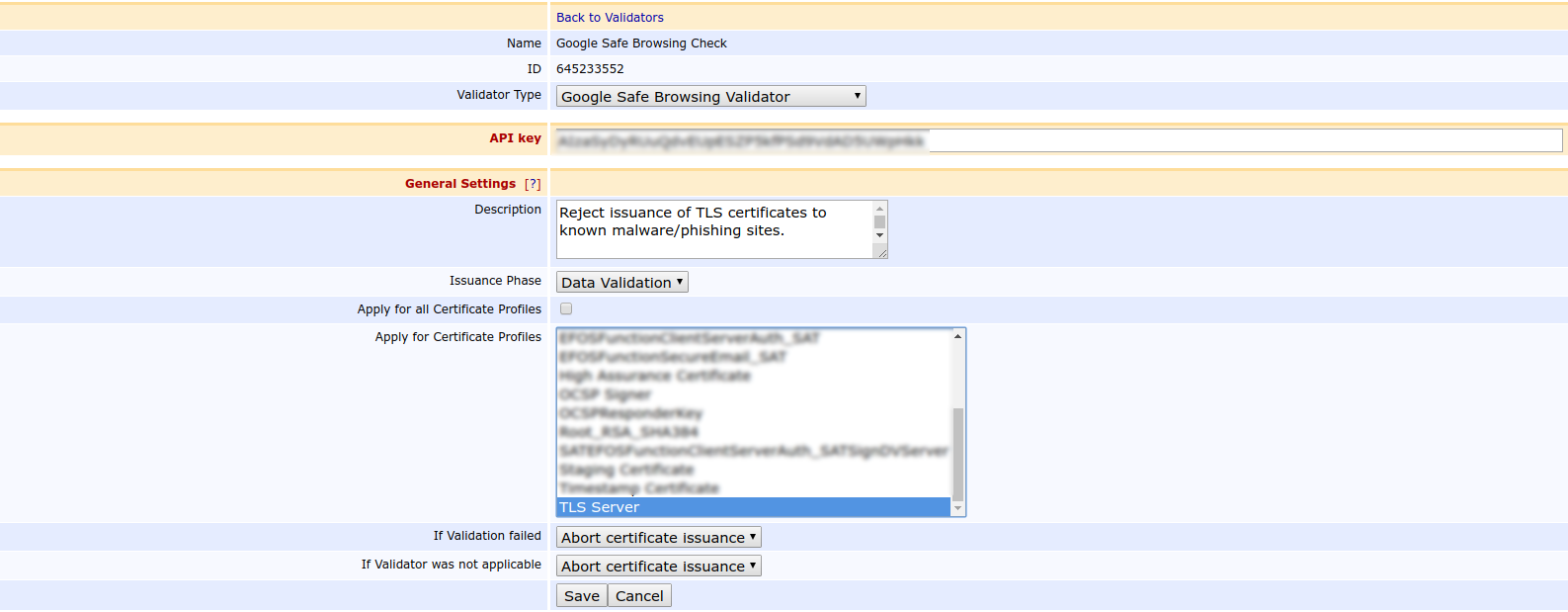
Google Safe Browsing Validator
The Google Safe Browsing Validator performs a lookup of the domains in the certificate against the Google Safe Browsing Lookup API v4. The Google Safe Browsing API is listing websites used for distribution of malware and phishing.
The Google Safe Browsing API should only be used for non-commercial purposes.
Before the validator can perform lookups against the API, you need to create an API key using the Google Developer Console, see https://console.developers.google.com/.
CAA Validator
ENTERPRISE
The Certificate Authority Authorization (CAA) validator is based on RFC 6844, erratum 5065, RFC 9495 and the CA/Browser Forum Baseline Requirements Certificate Policy for the Issuance and Management of Publicly-Trusted Certificates. For more information, see CAA Validator.
MPIC Validator
ENTERPRISE
The MPIC Validator allows a Multi-Perspective Issuance Corroboration, to facilitate domain control validation (DCV) from multiple network perspectives. Based on the https://open-mpic.org/documentation.html. For more information, see MPIC Validator.
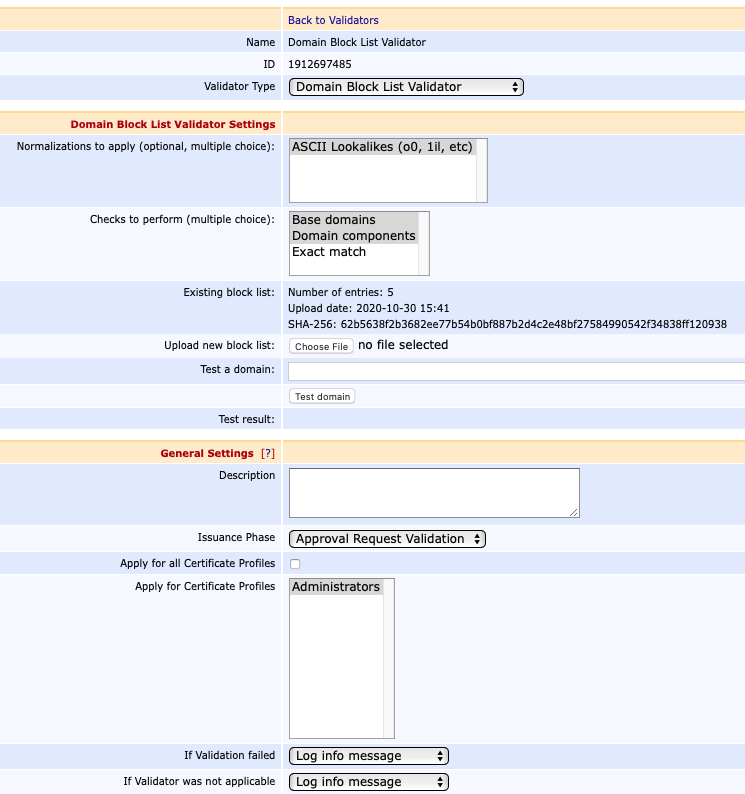
Domain Block List Validator
Domain Block List Validators allow DNSNAME attributes in Subject Alternative Name to be checked before issuance.
The intended use case is to require confirmation during the approval process for certain high-value domains (provided that approvals are enabled), but Domain Block List Validators can also be used for blocking known fraud sites, for example.
You can configure multiple validators with different settings. The following example shows a validator configured to allow validation while warning the administrator during the approval process.
Issuance Phase
The Domain Block List Validator can be run during the data or approval phase. If configured to run during the approval phase, and validation fails, a confirmation message will be shown in the RA Web for the approving administrators.
If the validator has been set to run during the approval phase and no approval requirements exist for the CA or Certificate Profile, then it will have no effect.
Fields
The following lists available Domain Block List Validator fields:
Field Name | Description | ||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Normalizations to apply | The normalization to be performed against the domains before comparing against the block list. Only one normalization is currently available: ASCII Lookalikes: This normalizes character or character sequences that look similar. IDN/Punicode characters of domains are not changed. The following characters and character sequences are normalized:
| ||||||||||||||||||||||||||||||||||||||||||
Checks to perform | The checks control how domains are compared against the entries in the block list. At least one must be selected. Base domain: All base domains will be compared against the block list. If issuing a certificate for "a.b.example.com", then "a.b.example.com", "b.example.com", "example.com", and "com" will be checked against the block list. Domain component: All domain components will be checked, individually. So for "a.b.example.com", the block list will be searched for "a", "b", "example", and "com". Exact match: Domains that match exactly will be matched. Note that this check is included with "Base domain". For "a.b.example.com", it will only search the block list for "a.b.example.com". | ||||||||||||||||||||||||||||||||||||||||||
Existing block list | Shows information about the currently active block list and only displays once a block list has been uploaded. Number of entries: Number of domains in the block list. The effective number of block listed domains may be greater due to normalization and the checks performed. Upload date: Time when the block list was uploaded. Shown in UTC timezone. SHA-256: Hash of the entire file, as uploaded (i.e. including comments and whitespace). | ||||||||||||||||||||||||||||||||||||||||||
Upload new block list | Click Browse to upload a block list. Any existing block list will be replaced when a new one is uploaded. For information on syntax, see Certificate Field Validators#Block List File Syntax. Depending on your configuration, there may be a file size limit. With a limit of 1 MB, you will be able to put around 50 000 domains in your block list. To work around this limit, you can split the block list and use several validators. |
Block List File Syntax
Block list text files contain one block listed domain per line:
IDN domains must be Punycode encoded
Empty lines are ignored
Leading and trailing whitespace is ignored
Text after a # is considered a comment and is ignored.
Comments may contain ASCII or UTF-8 text, but the file may not contain a byte order mark (BOM). If in doubt, save the file in plain ASCII format.
The following shows an example of a block list text file:
sample_blocklist.txt
# Sample block list file. Created 2019-03-01
bank # If domain component blocking is enabled, then this will block "bank.com", "bank.example.com" but NOT "memorybank.com"
example.com # With base domain blocking one can block a domain including subdomains.
net # ...or entire TLDs (Top Level Domains)
evil.example.edu # It is possible to block a specific subdomain only
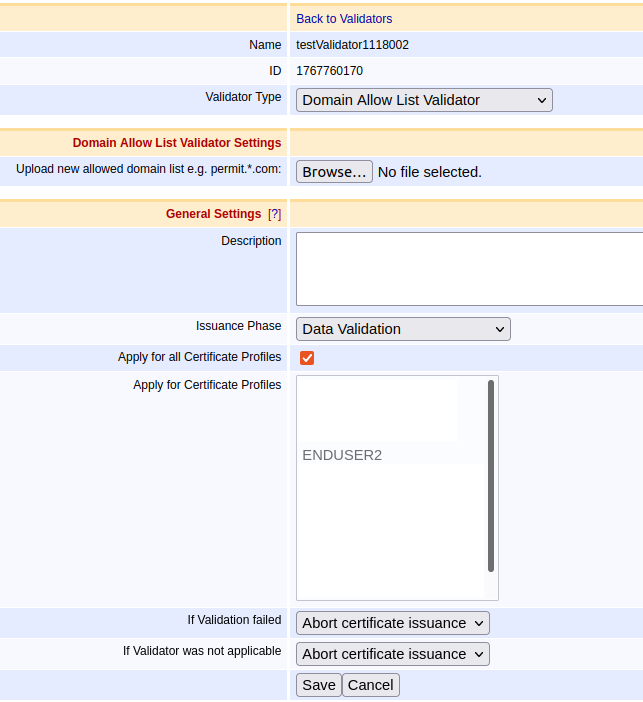
xn--rvare-jua.example.com # This is an IDN domain "rövare.example.com"Domain Allow List Validator
Domain Allow List Validators allow DNSNAME attributes in Subject Alternative Name to be checked before issuance.
The intended use case is to relax the validation process for a few selected domains. The validator supports wildcard(*) for easier configuration.
Fields
The Domain Allow List Validator Settings contains one field that accepts a configuration file with allowed domain names. The syntax of the file is described below. Click Browse to upload an allowed domain list. Any existing list will be replaced when a new one is uploaded.
The allowed domain list follows similar rules as the Block List Validator:
IDN domains must be Punycode encoded with the exception of the asterisk character (*) to indicate wildcards.
Empty lines are ignored.
Leading and trailing whitespace is ignored.
Text after a # is considered a comment and is ignored.
Comments may contain ASCII or UTF-8 text, but the file may not contain a byte order mark (BOM). If in doubt, save the file in plain ASCII format.
The following shows an example of a allow list text file:
sample_allowed_domains.txt
permit.com
permit.example.com
#good.example.com
permit2.example.com # this is a comment
permit3.example.com
permit4.example.com# comment
permit5.*.example.com # allows: 'permit5.abc.example.com' and 'permit5.*.example.com' but blocks: 'permit5.example.com' or 'permit5..example.com'
*.permit6.*.example.com # allows: 'abc.permit6.xyz.example.com' or '*.permit6.xyz.example.com' or 'abc.permit6.*.example.com' but blocks: 'permit6.xyz.example.com' or 'abc.permit6.example.com'
permit7.example.* # allows: 'permit7.example.io' or 'permit7.example.com' but blocks: 'permit7.example'.png)