OAuth Providers
OpenID Connect (OIDC) is an extension of the OAuth 2.0 protocol used for authentication through an Identity Provider (IdP). EJBCA supports OIDC authentication using the OAuth 2.0 authorization code flow.
OIDC authenticationcan be used alongside or instead of client certificate authentication (see Authentication Methods) and provides a powerful tool for managing all users of a PKI from a single source (the IdP).
OIDC authentication is configured using a Trusted OAuth Provider (“provider”) in EJBCA.
The following page provides an overview of OAuth providers in EJBCA. For instructions on setting up OAuth providers, see OAuth Provider Management.
Supported Providers
EJBCA has been tested against Keycloak, Microsoft EntraID, Okta and PingID. For detailed instructions on how to integrate against one of these IdPs, see OAuth Provider Management.
Other OIDC-compatible IdPs may work with EJBCA, but these have not yet been tested and evaluated by Keyfactor.
Provider Configuration Overview
Providers can be configured under the Trusted OAuth Providers tab in System Configuration.
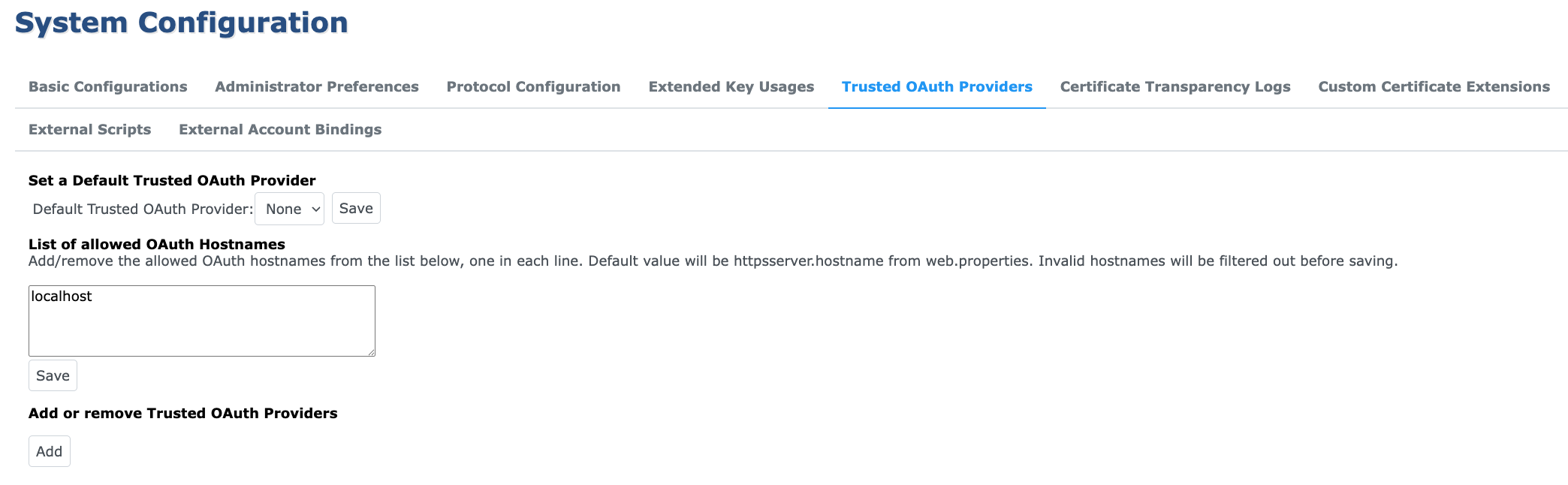
Value | Description |
|---|---|
Default Trusted OAuth Provider | If the received JWT does not have a Key ID, the Default Trusted OAuth Provider may be used to verify the signature. |
List of allowed OAuth Hostnames | Defines which hostnames EJBCA will consider valid during OAuth-based login. It acts as an allowlist for redirect URL generation. |
Prior to EJBCA 9.4.0 the redirect URL was constructed based only on the httpsserver.hostname value in web.properties. Since then the redirect URL is built dynamically based on the inbound hostname if the hostname is in the list of allowed hostnames. For backwards compatibility, the hostname defined in web.properties is still considered valid in addition to the ones configured in the allowlist.
Generic Values
When adding a provider, the following values exist as general options:
Value | Description |
|---|---|
OAuth Provider Name | The human-readable name of the provider, chosen by the administrator. This shows up when the user wants to log in. |
URL | The base URL of the IdP. |
Fetch UserInfo | If checked, EJBCA makes a request to the |
Skew Limit | The allowed clock difference, in milliseconds, between the EJBCA and the IdP. |
Scope | The scope used when requesting claims. |
Client Name | The client name EJBCA uses for access to the IdP. |
Client Secret | The client secret EJBCA uses for access to the IdP. |
At the bottom of the page is a form for providing OAuth public key(s):
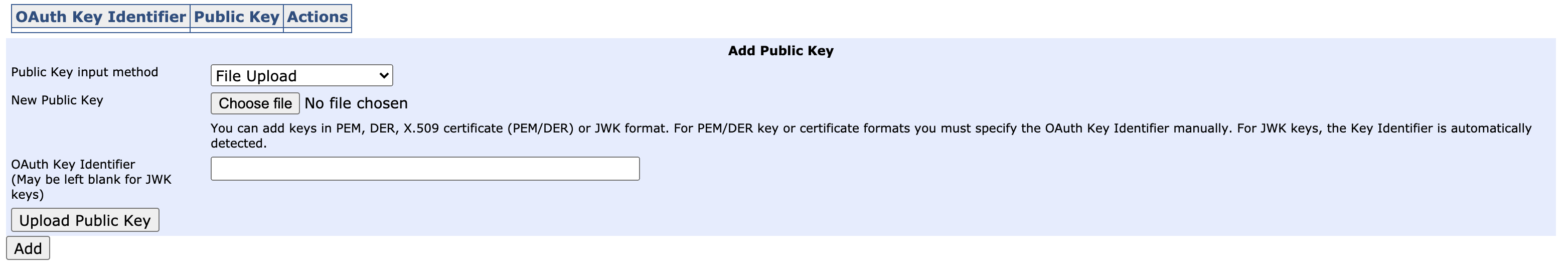
The key(s) may be provided using three methods:
File Upload
Upload as text
Providing a Key Configuration URL
Implementation Specific Values
Besides the generic values, each Trusted OAuth Provider implementation may support additional vendor specific configuration values.
Role Member Configuration Overview
Claims in JWTs may be mapped to roles in EJBCA. A claim can represent a group of users or an individual user. EJBCA allows any combination of claims and even different authentication methods in a single role.
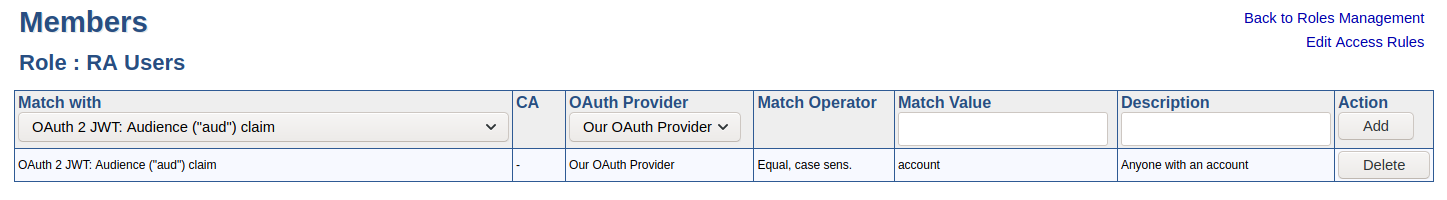
The following claims are supported. Exact usage depends on the provider, see OAuth Provider Management for details.
Claim | Description |
|---|---|
sub | Permanent unique identifier of the subject. |
iss | Issuer of the token. |
aud | Audience. |
oid | Microsoft EntraID-specific claim that represents a user. |
roles | |
kf.roles | Our vendor-specific claim for role assignment. |
name | The user’s name. |
.png)