Authentication Methods
This page describes the available authentication methods for accessing the EJBCA Certification Authority (CA) and Registration Authority (RA) user interfaces. It explains how administrators and end users authenticate to EJBCA, when each method is appropriate, and the security considerations associated with each option.
EJBCA provides two primary authentication mechanisms for access to the CA and RA user interfaces (UIs):
Client certificate authentication
OAuth-based authentication
In addition, the RA UI can be configured for public access without requiring any authentication token. This option is intended for controlled and trusted environments only.
Client Certificate Authentication
Client certificate authentication is the classic method for accessing the EJBCA user interface. The client certificate is typically issued by the Management CA.
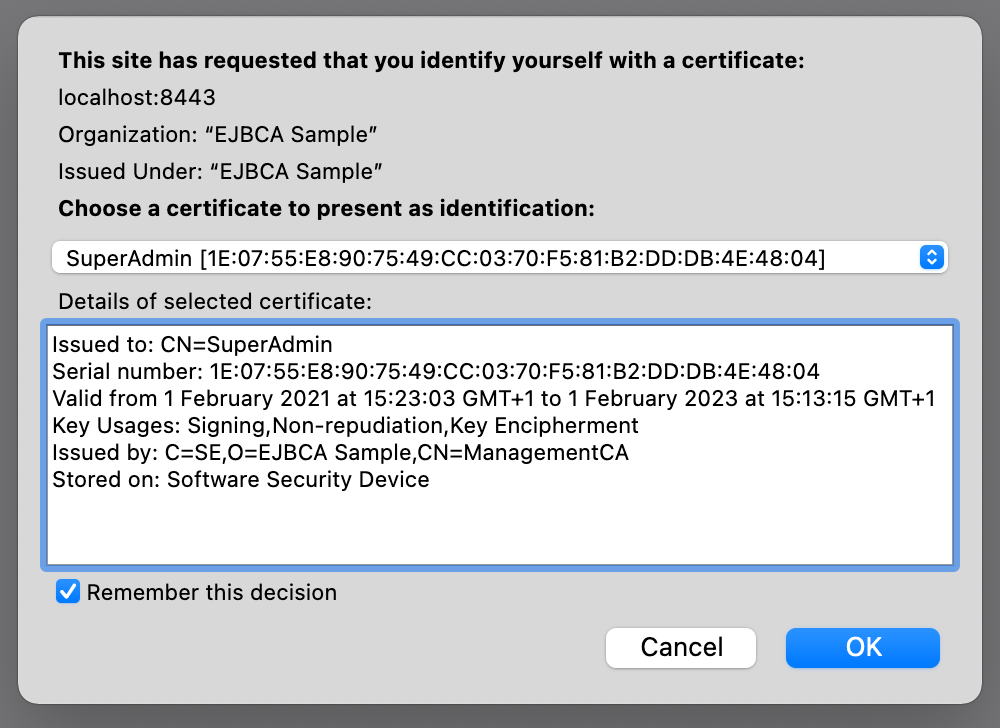
The associated key pair can be created using one of the following approaches:
User-generated key pair: The end user generates the key pair manually and enrolls the certificate through the RA.
CA-generated key pair: The key pair is generated by the CA during enrollment. This approach is recommended when key recovery is required.
EJBCA also supports authentication using client certificates stored on USB tokens and smart cards. These hardware-backed credentials provide stronger protection for private keys. For a complete list of supported devices and detailed integration workflows, see Access EJBCA using USB Tokens and Smart Cards for a complete list of supported devices and workflows to integrate them.
OAuth Authentication
EJBCA can authenticate users via an external OAuth provider, allowing integration with existing identity and access management solutions.
OAuth authentication is suitable when:
Centralized identity management is already in place
Users authenticate through a corporate IdP or cloud-based IAM service
Certificate-based authentication is not desirable for UI access
EJBCA supports both locally hosted and cloud-based OAuth providers. For a list of tested providers and step-by-step integration instructions, see OAuth Providers.
Public Access to the RA UI
In trusted environments, the RA UI can be configured for public access to support initial user enrollment without requiring client certificates or OAuth authentication.
This configuration is commonly used for first-time enrollment scenarios or user-initiated certificate requests.
For instructions on setting up the EJBCA RA for public access, see Configure EJBCA for Public Access.
Although it is technically possible to configure the CA UI for public access, this configuration is strongly discouraged. Exposing the CA UI significantly increases security risk and public access to the CA UI should only be considered in exceptional circumstances and with a full understanding of the security implications.
.png)