Step 6: Create the AuthCA as SubCA in Node A
Here we create the second of the SubCAs, namely AuthCA. This CA is installed along with the other SubCAs in the EJBCA Hardware Appliance (Node A) and is signed by RootCA.
The following sections describe the actions you have to perform.
Create a Crypto Token for AuthCA in Node A
At this point, we will create a Crypto Token and generate public keys that will be used by AuthCA.
- Open the EJBCA Administration.
- In the sidebar, in the CA Functions section, select Crypto Tokens.
- Click Create New....
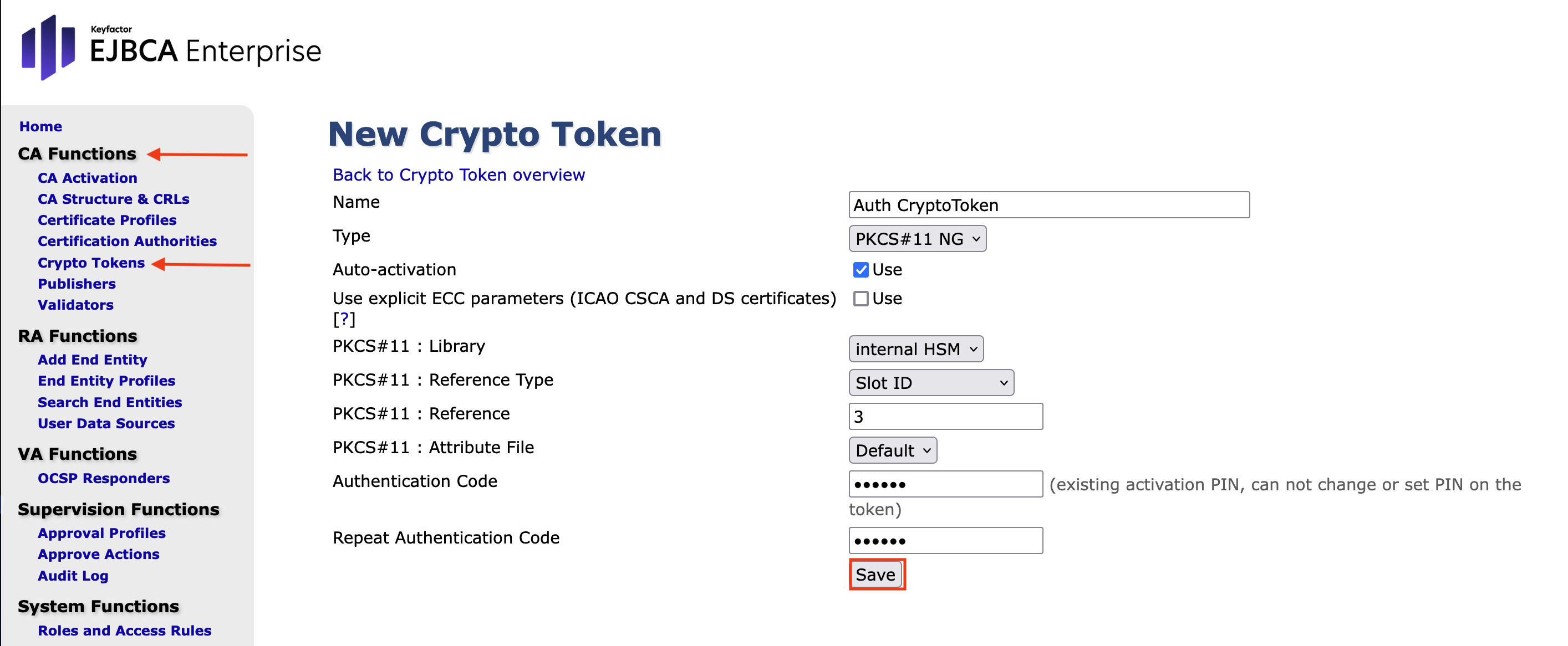
New Crypto Token
Name: Auth CryptoToken
Type: set to PKCS#11NG
Click the Auto-activation box
PKCS#11 Reference Type: set to Slot ID
PKCS#11 : Reference: set to 3 (The index numbers will be different depending on the installation.)
Authentication Code : foo123 (Use an existing activation PIN. This can not be changed or set PIN on the token.)
Repeat Authentication Code:Make sure that you have manually generated slot password for that slot.
The EJBCA Enterprise opens a form: New Crypto Token form.
There are some default settings in the various sections. We will not go into all entries, but only those where changes are required. For more information about the form, refer to Crypto Tokens Overview.
Click Save
In the settings page, the message CryptoToken created successfully will be displayed.
Create Keys for the AuthCA as SubCA in Node A
Continue and create the following keys.
Underneath the table, enter defaultKeyAuthCA (value for Alias) and RSA 4096 (value for Key Algorithm and Key Specification) and click Generate new key pair.
Click the Test button in the table. The following message will appear: defaultKeyAuth tested successfully.
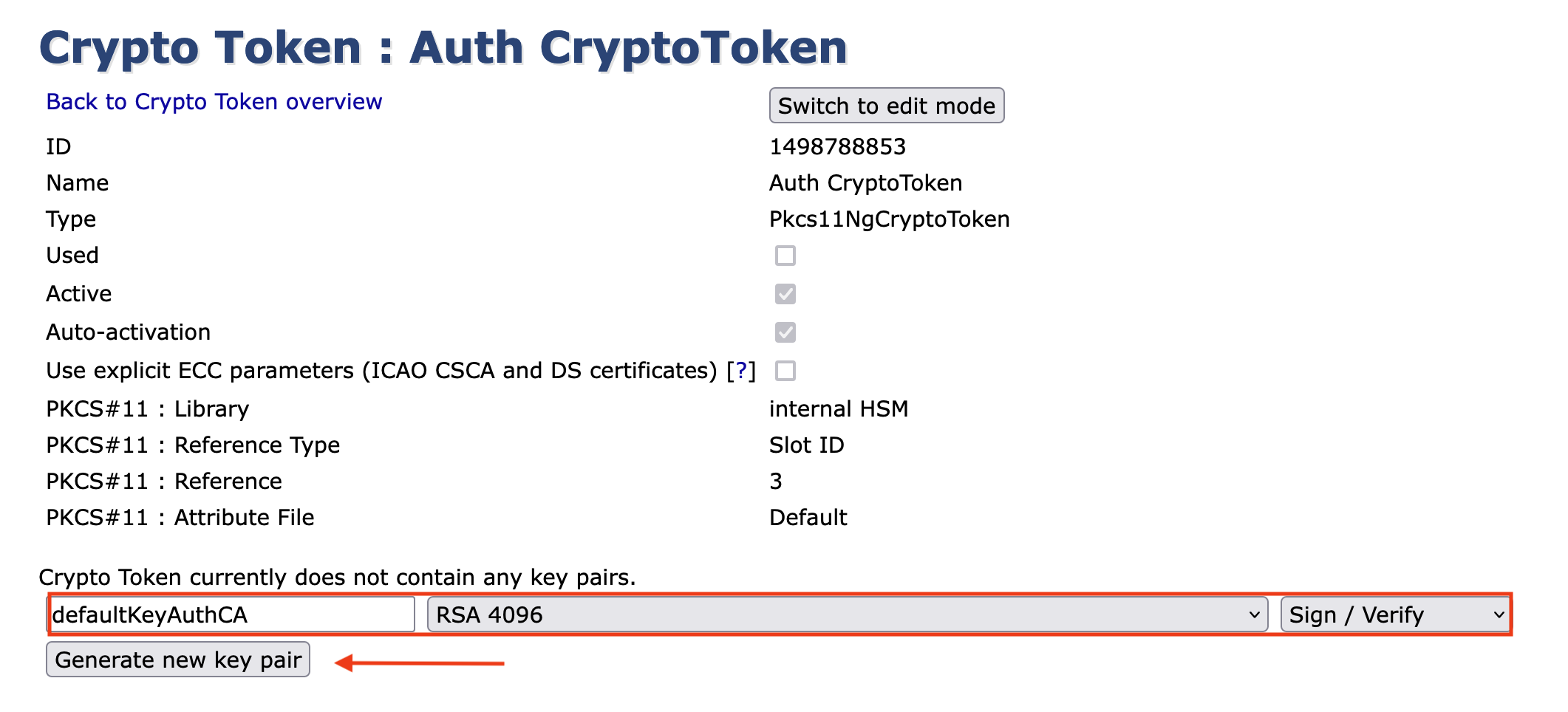
Repeat the steps for signKeyAuthCA .
Enter signKeyAuthCA (value for Alias) and RSA 4096 (value for Key Algorithm and Key Specification). Set the -Key Usage- to Sign / Verify.
Click Generate new key pair.
Click the Test button in the table. The following message will appear: signKeyAuthCA tested successfully.
- Repeat the steps for testKeyAuthCA.
Enter testKeyAuthCA (value for Alias) and RSA 1024 (value for Key Algorithm and Key Specification). Set the -Key Usage- to Sign / Verify.
Click Generate new key pair.
Click the Test button in the table. The following message will appear: testKeyAuthCA tested successfully
Create the AuthCA in Node A
This section describes the actual creation of the AuthCA.
- Open EJBCA Enterprise.
- In the sidebar, in the CA Functions section, select Certification Authorities.
- Enter AuthCA in the Add CA field.
Click Create...
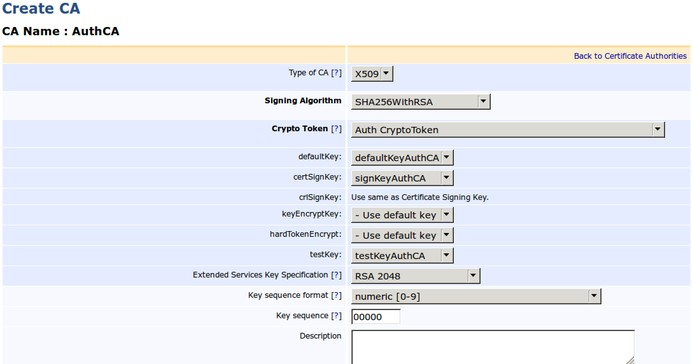
In the Create CA form, specify the following:
- Signing Algorithm: Select SHA256WithRSA
- Crypto Token: Select Auth CryptoToken
Section 'Ca certificate data' (not visible in screenshot): - Subject DN: Enter CN=AuthCA,O=EJBCA Course,C=SE
- Signed By: Select External CA
Section 'CRL specific data' (not visible in screenshot): - CRL Expire Period (*d *h *m): Enter 12h
This field defines how long a CRL is valid for. The letter d specifies days. - CRL Issue Interval (*d *h *m): Enter 0
This field defines how often the CRLs are to be issued. In this case the CRLs will be issued once every day but will be valid for two days. - CRL Overlap Time (*d *h *m): Enter 2h
This value defines the number of minutes both CRLs are valid for. For example, thirty minutes before the first CRL will expire it will issue a new CRL.
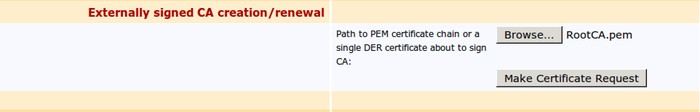
In the section Externally signed CA creation/renewal click Browse... and upload the RootCA.pem file.
This step is NOT needed in the case that you have imported RootCA as an External CA. Otherwise, RootCA.pem can be downloaded from the Public Web of the EJBCA Hardware Appliance which is installed the RootCA (check Use-Case: Import RootCA as External CA in Node A).
Click Make Certificate Request:
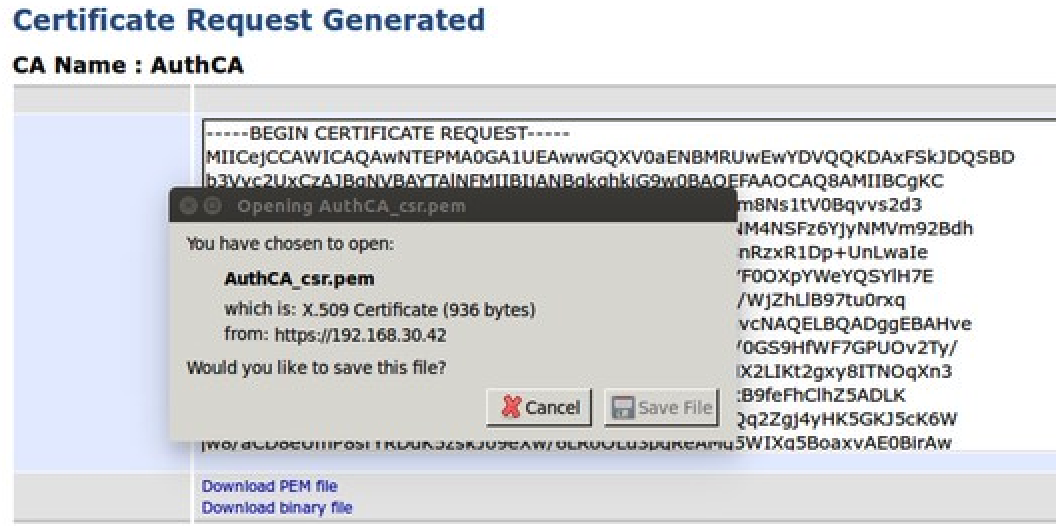
You will be asked to download or copy the request. Save the .csr file with Save File:
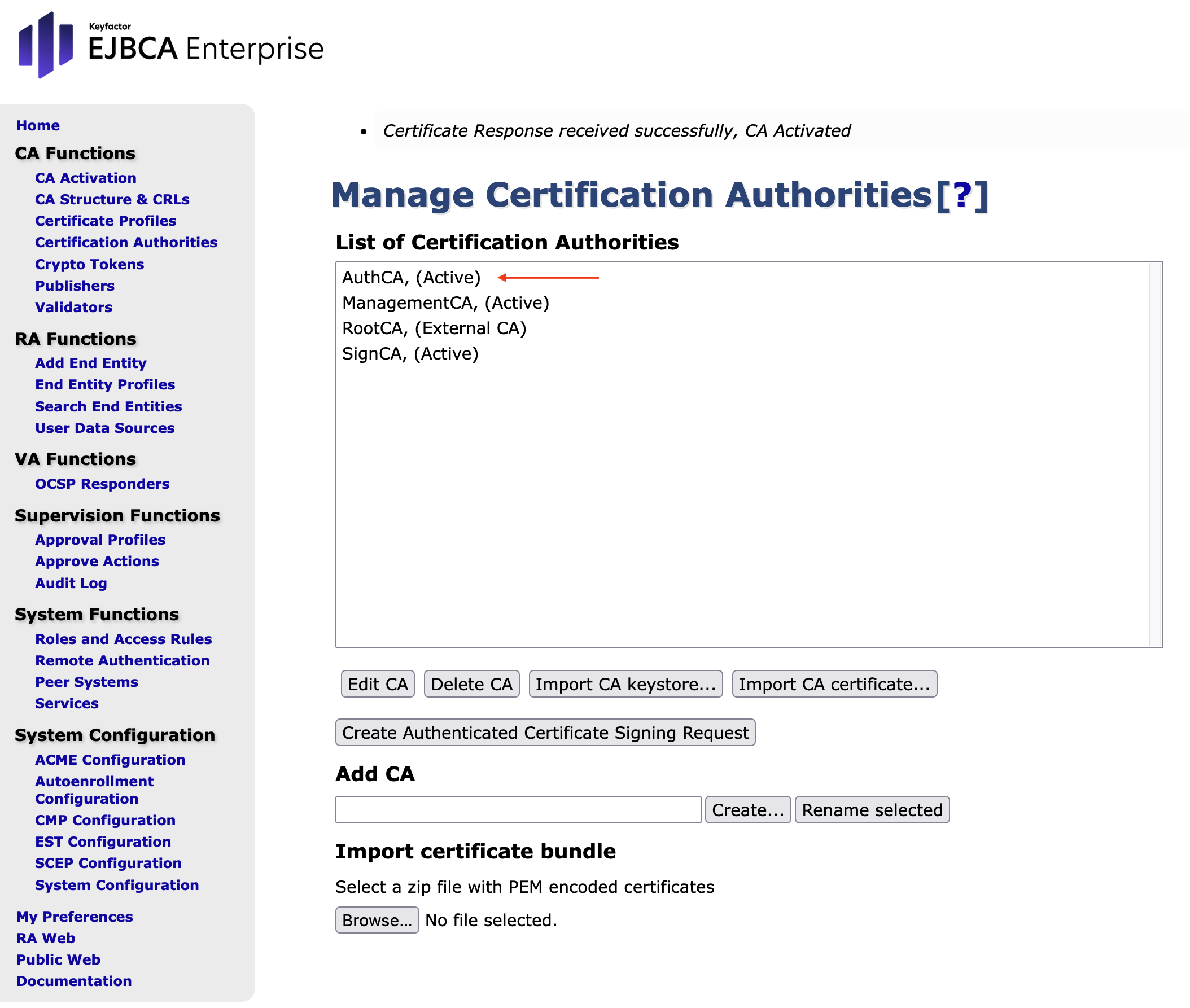
Check the status of the CAs:
In the sidebar in the CA Functions section, select Certification Authorities.
The status for AuthCA is now Waiting for Certificate Response: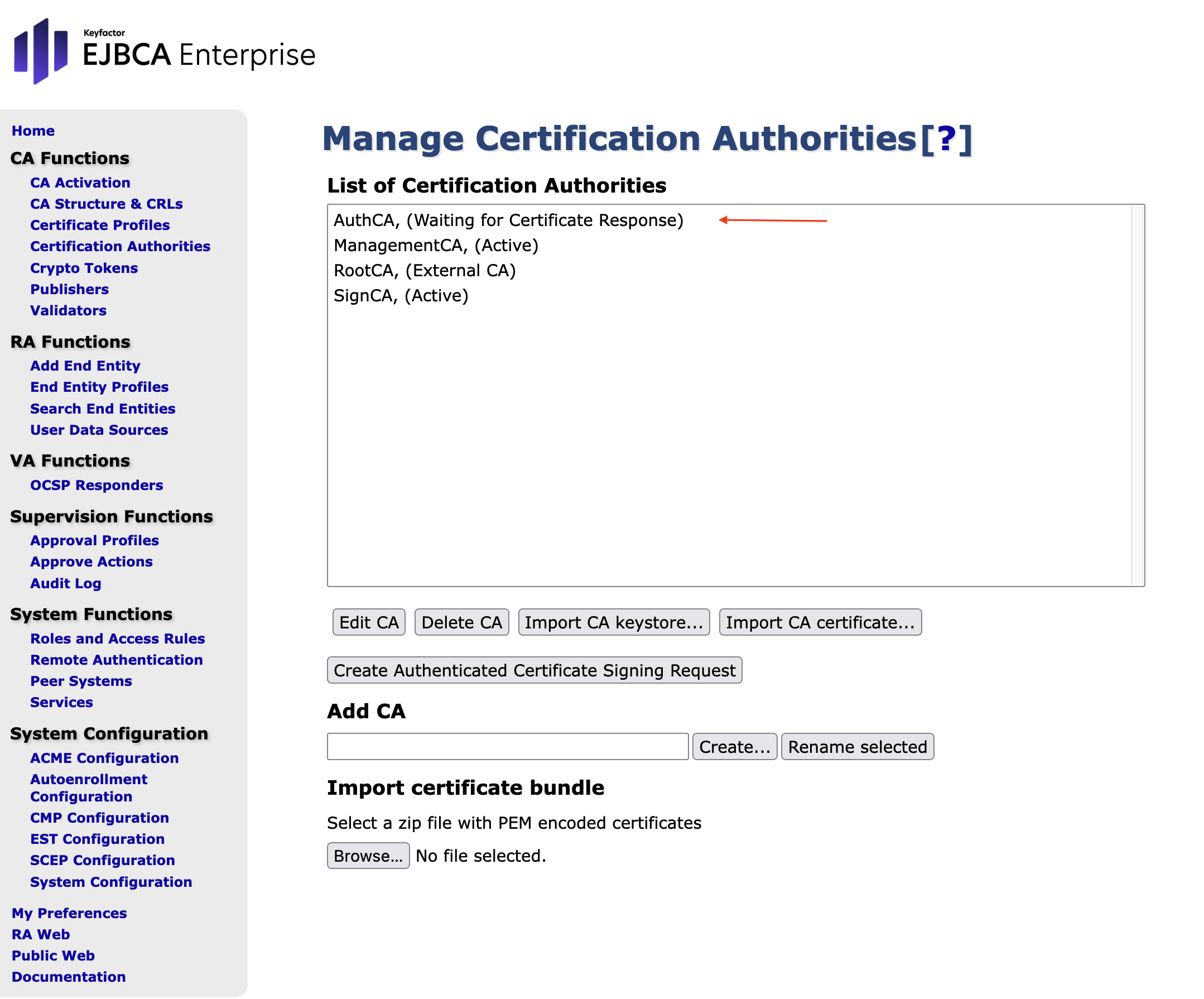
Create an End Entity for AuthCA with installed RootCA
This describes how create an End Entity that is associated with the AuthCA certificate in the EJBCA Hardware Appliance where RootCA is installed (Node B).
- Open EJBCA RA Web.
- From the top menu click the drop-down menu for Enroll.
Chose Make New Request from the drop down menu.
Make the following entries in the Make Request form. The selection and entry fields are automatically expanded.
- Select Request Type
Certificate Type: choose SSLCAEndEntityProfile from the drop-down menu.
Key-pair generation: make sure Provided by user is activated. - Upload CSR
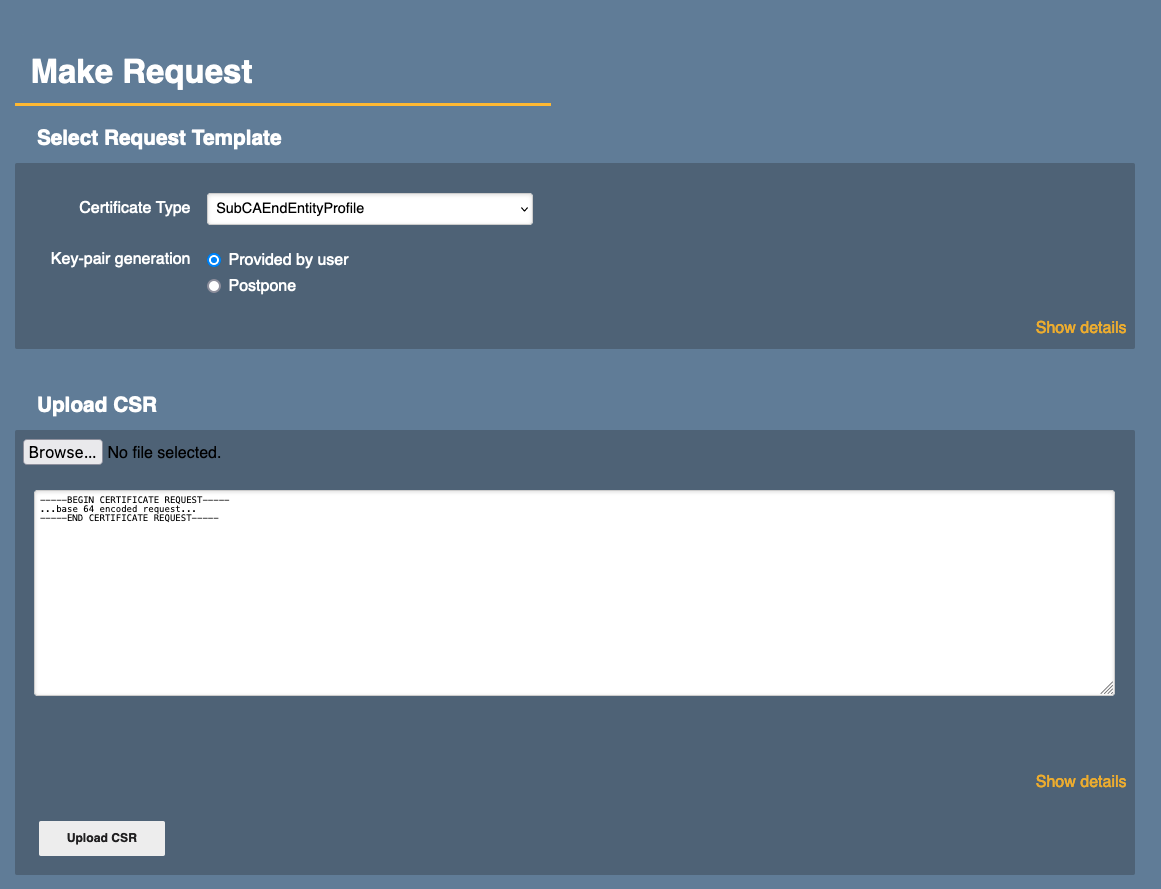
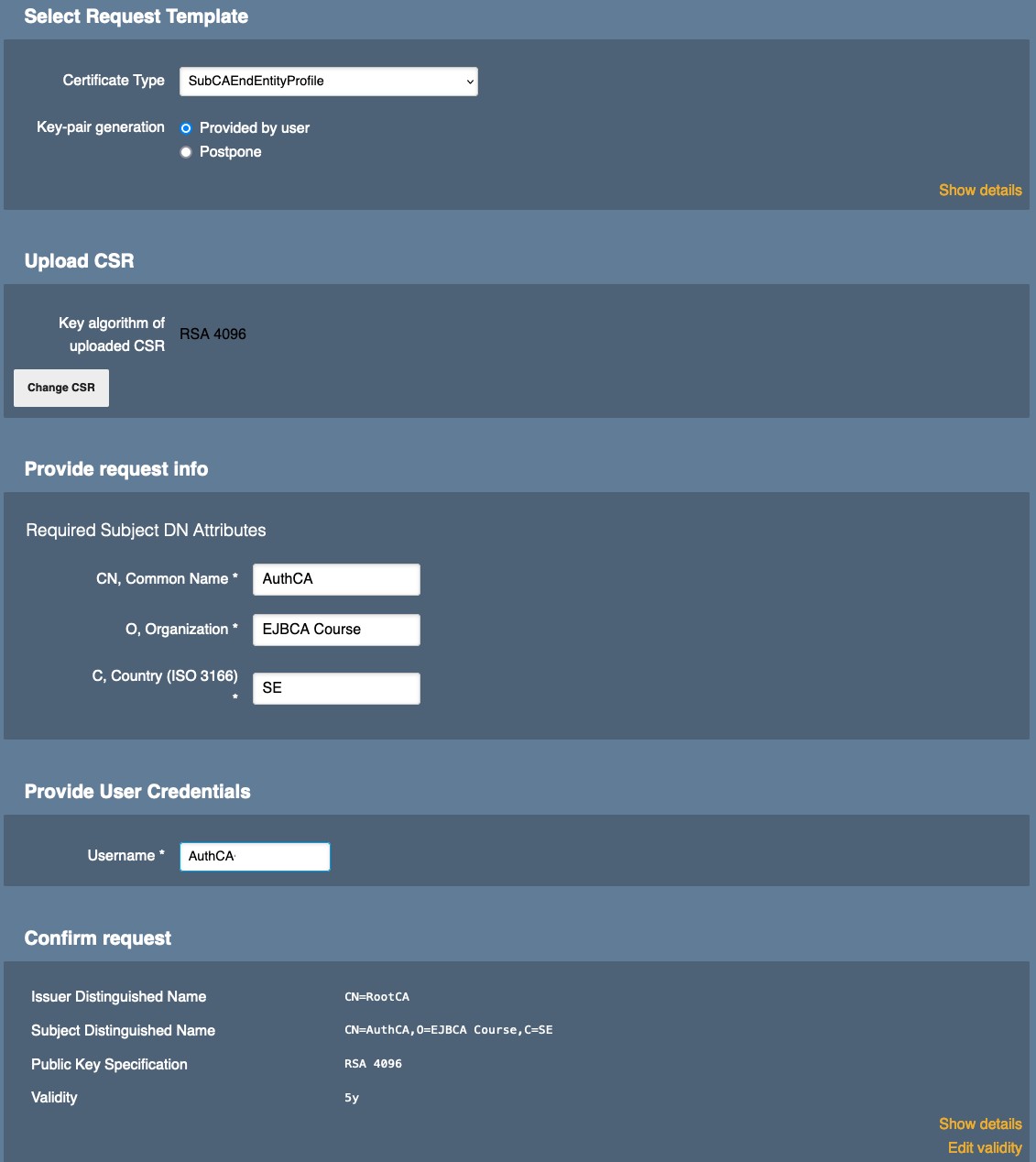
Key algorithm of uploaded CSR is set to RSA 4096.
You can change the CSR. Click Change CSR to do so (see next screenshot). - Provide Request Info. These are required Subject DN Attributes.
CN, Common Name: enter AuthCA
O, Organisation: enter the name of your organization
C, Country: enter your Country code according to ISO 3166 - Provide User Credentials. These are mandatory entries.
Username: enter AuthCA - Click Download PEM to continue.
- In the EJBCA Hardware Appliance where AuthCA is installed (Node A), go to the sidebar, in the CA Functions section and select Certification Authorities.
Highlight AuthCA, (Waiting for Certificate) and press Edit CA.
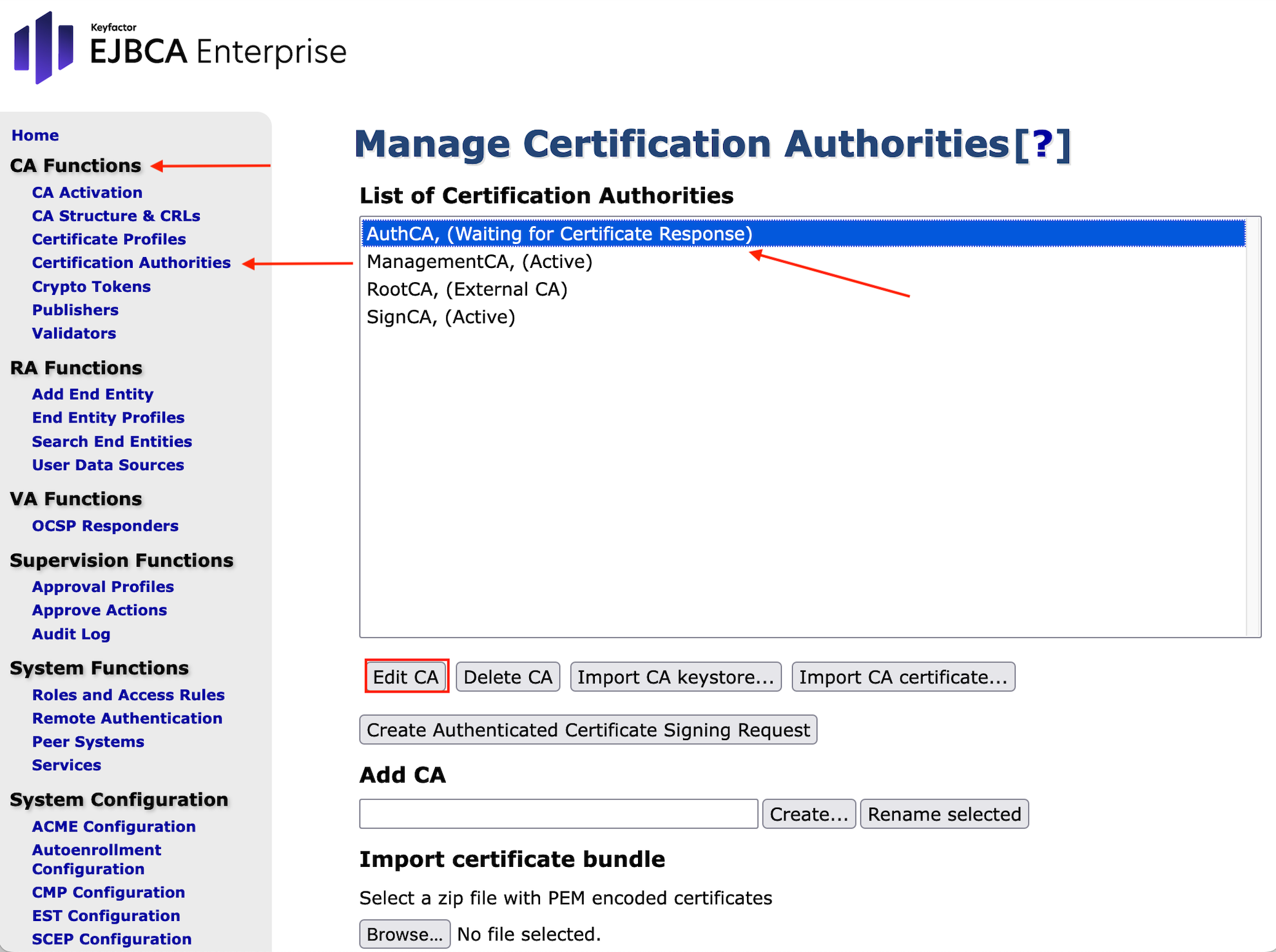
- A form Edit CA opens and in the section Externally signed CA creation/renewal > Step 2, click Browse... and select the file AuthCA.pem.
Click for Receive Certificate Response.
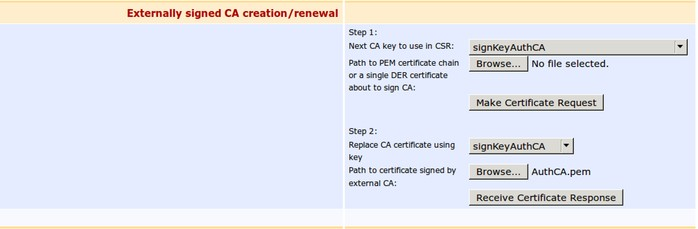
- Navigate to Certification Authorities to see that AuthCA is now active.
.png)