Step 5: Running WebConf Wizard
The final step of the initial setup is to run the web-based configurator WebConf. During this procedure all components of the system will be configured according to the parameters provided.
WebConf is designed and tested to work with Firefox 26.0+. Other browsers like Chrome or Safari are not officially supported and minor incompatibilities may be observed.
Internet Explorer is not officially supported. Depending on the version, the configuration process may not finish successfully.
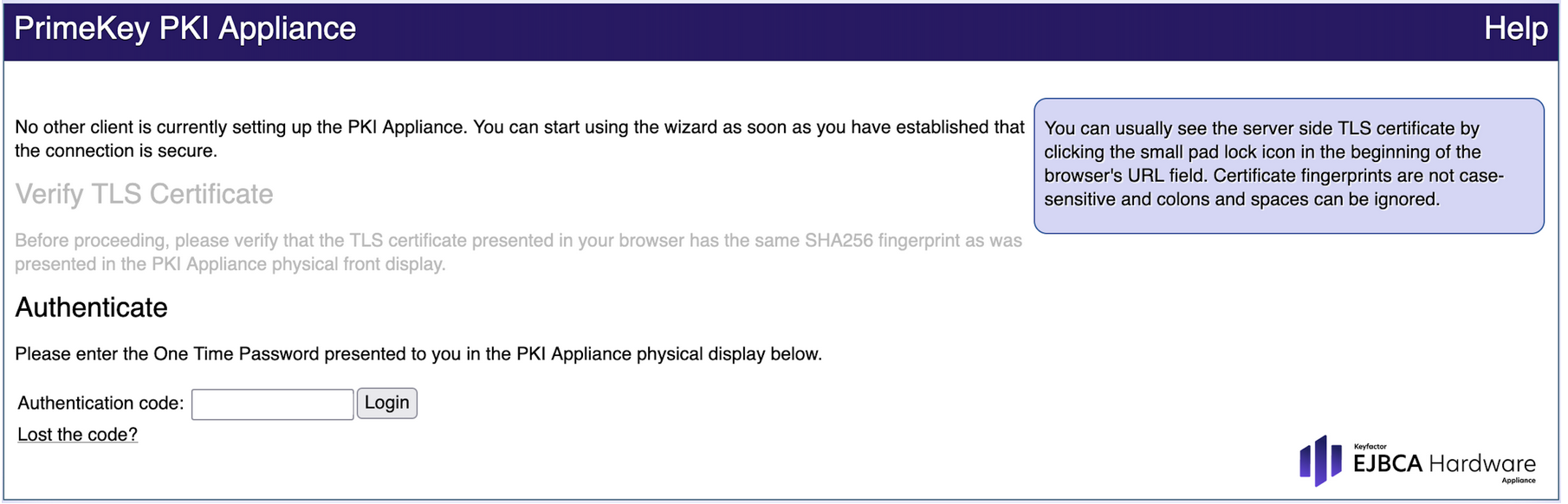
Initial Log In
For the initial log in you need to have the One Time Password (OTP) ready. It is displayed on the front display of the Hardware Appliance. Until the system is completely installed, the One Time Password is newly created when the machine is started.
- In the Authenticate page, enter the One Time Password in the field Authentication code.
Click Login.
Fresh Installation
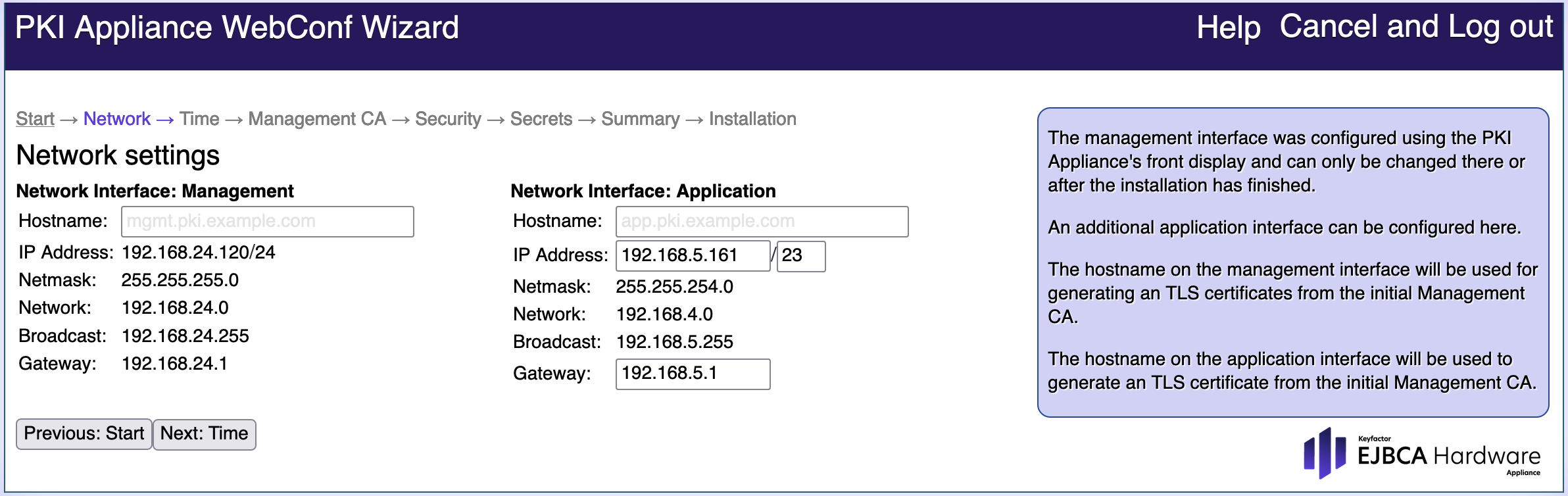
Network Settings
After the Fresh Install is complete, you can configure the network settings of the Hardware Appliance. There are two physical network setting interface designs:
- Management Interface: Provides access to the configurator WebConf and to the Admin GUI of EJBCA.
The Management Interface IP address has been configured via the front display in Step 3: Changing the IP Address of the Hardware Appliance. It is preset to a network prefix of /24 (subnet mask 255.255.255.0). - Application Interface: Provides routing for the operational payload.
You can use this wizard step to enter the IP address, network prefix, and default gateway manually.
If needed, the two networks can be separated.
After the installation is complete you can use the WebConf > Network page to edit your network settings. However, we recommend to decide on the network configuration beforehand.
Proceed as follows to configure the Network Settings:
- Enter the Hostname for the Management and Application Interfaces.
This is required if the Hardware Appliance needs to be available through DNS name resolution. - If needed, enter the IP address, Network prefix and Gateway for the Application Interface.
Click Next: Time to proceed to the next page of the wizard.
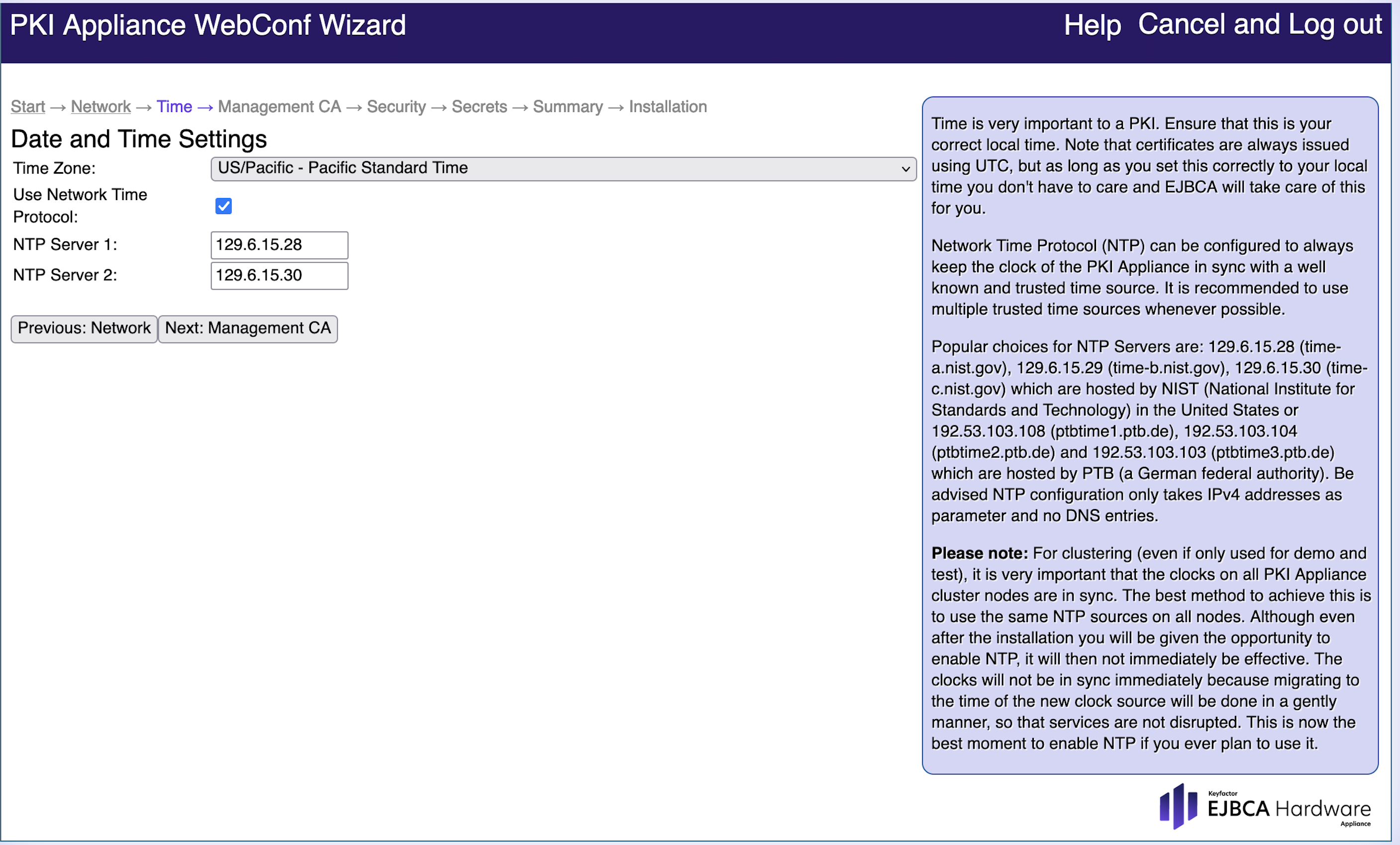
Date and Time Settings
Many Public Key Infrastructure (PKI) applications need a correct date and time. Use a Network Time Protocol (NTP) time source, as this protocol synchronizes the clocks of computers over a network. NTP is for example required to build a cluster.
We recommend to enable Use Network Time Protocol at this stage. If NTP is configured at a later time, there will be time synchronization issues between the NTP Server and the current system time.
Proceed as follows to configure the Date and Time Settings:
- Select the Time Zone from the drop-down list that applies to you (here US/Pacific - Pacific Standard Time is set).
- Enable Use Network Time Protocol if you want to use an NTP time source.
If enabled, also specify the NTP Server to be used. - Select the exact Date and time.
Click Next: Management CA to proceed to the next page.
Management CA Settings
The initial Management CA will be used to create the Hardware Appliance's server side TLS certificate. It will also generate a client TLS certificate for secure management of the Hardware Appliance.
Proceed as follows to configure the Management CA Settings:
- Enter the Common Name of the EJBCA Management CA.
- Add the Additional Subject Fields, such as organization and country:
- It is important to specify a meaningful identifier for the Additional Subject Fields.
- The Additional Subject DN is reflected in the TLS certificates stored in your browser and in the name of the backup files.
- If you want to perform several test and/or demo installations, this is where the name can be branded.
Select the signing Key Specification and the Signature Algorithm to be used by the EJBCA Management CA:
Enter the SuperAdmin Common Name. This is the name of the first post-install user with administrative rights.
Click Next: Security.
Hardware Security Module Settings
Use this tab to configure all relevant security aspects of the Hardware Appliance.
Security settings cannot be altered after the installation.
Audit Log Storage - Detailed information
Here you can select to Store signed audit logs, that is, log records of security operations, should be stored on the clustered storage. By default, the option is enabled. Audit log records consume database disk space. For a typical installation, the creation of a single certificate issues approximately 10 audit log records. For all typical installations, the audit log database table will be at least double the size of the other database tables. If you disable the option, you can store the audit log records externally, over syslog shipping (unsigned, unencrypted).
Security Settings - Secrets
Domain Master Secret
A Domain Master Secret ensures a higher level of security. This passphrase is used to derive a symmetric key which is used to encrypt backup archives created by the Hardware Appliance. A Domain Master Secret can be specified manually or it can be generated by the system. If generated by the system, the highly secure Domain Master Secret can be printed.
Important
Document the Domain Master Secret and keep it in a safe place. If it is lost, you cannot restore the device from a backup and you cannot extend this system to a cluster.
Summary and Start of the Installation
The Summary step lists all configuration settings from the previous wizard steps. We highly recommend the following:
- Check everything on this page before starting the actual installation.
- Print this page for future reference.
Choose SuperAdmin Credentials
For managing the Hardware Appliance you need a client side SuperAdmin TLS certificate. This certificate is issued by the Management CA and can be used by your browser. The certificate will be your only authentication to the system, unless you configure other access methods. For information on configuration of further users and other authentication methods, see the section Access.
After the installation you will be automatically prompted to choose your SuperAdmin credential procedure:
To retrieve SuperAdmin credentials, select the option appropriate for the current client environment:
- Step 5: Running WebConf Wizard#Get PKCS#12 key store: The SuperAdmin certificate and corresponding key pair is generated on the Hardware Appliance and manually imported into the browser.
- Get certificate from Certificate Signing Request: The SuperAdmin key pair is generated outside the browser context and the SuperAdmin certificate will be created from a Certificate Signing Request.
The following sections provide more detailed information about each of these options.
The certificate and it‘s key pair is a vital component of your system. Protect and secure it with the same care that you take for the backups and data of the Hardware Appliance itself. Anyone in possession of this certificate can manipulate your installation. You cannot access the Hardware Appliance without this certificate.
Get PKCS#12 key store
A PKCS#12 key store is a format for storing both private keys and certificates protected by a password. Select this option to download such a key store that contains both a SuperAdmin certificate and the corresponding key pair. You will then have to manually import the .p12-file into the browser using the PKCS#12 protection password shown to you.
Proceed as follows to download a PKCS#12 key store:
Select Get PKCS#12 key store and click Proceed.
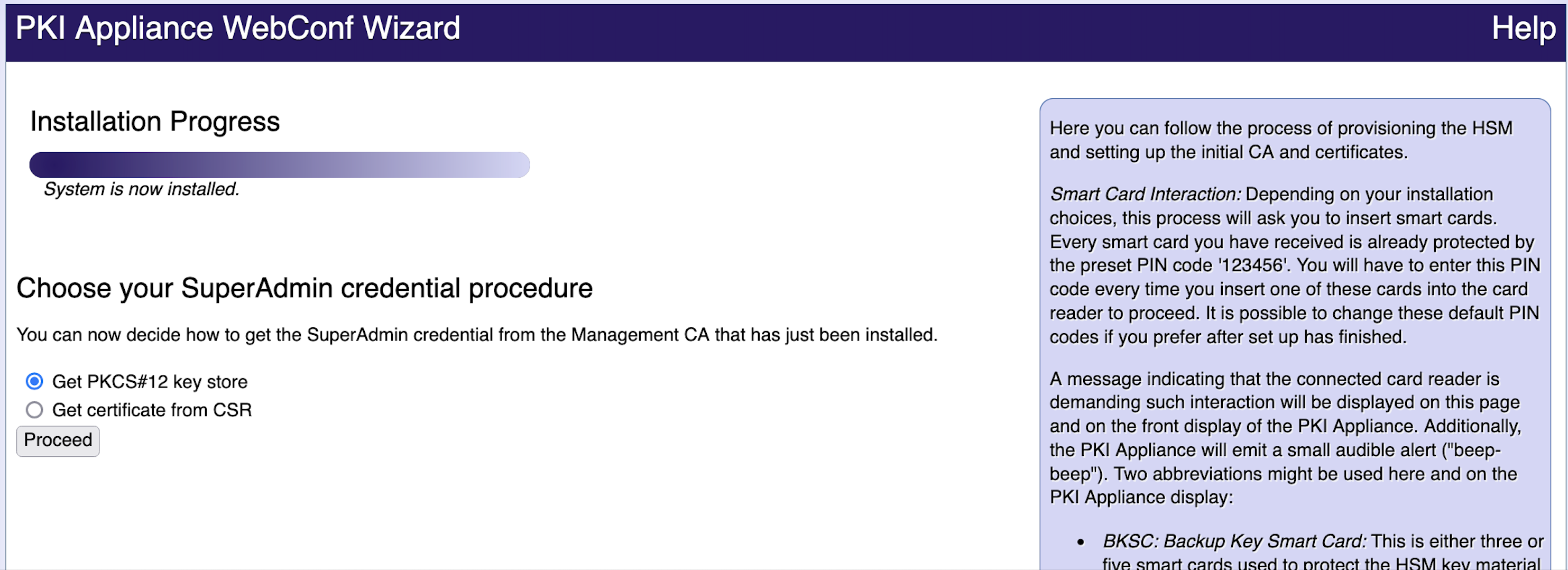
- Copy the PKCS#12 protection password.
Click Get SuperAdmin PKCS#12 key store.
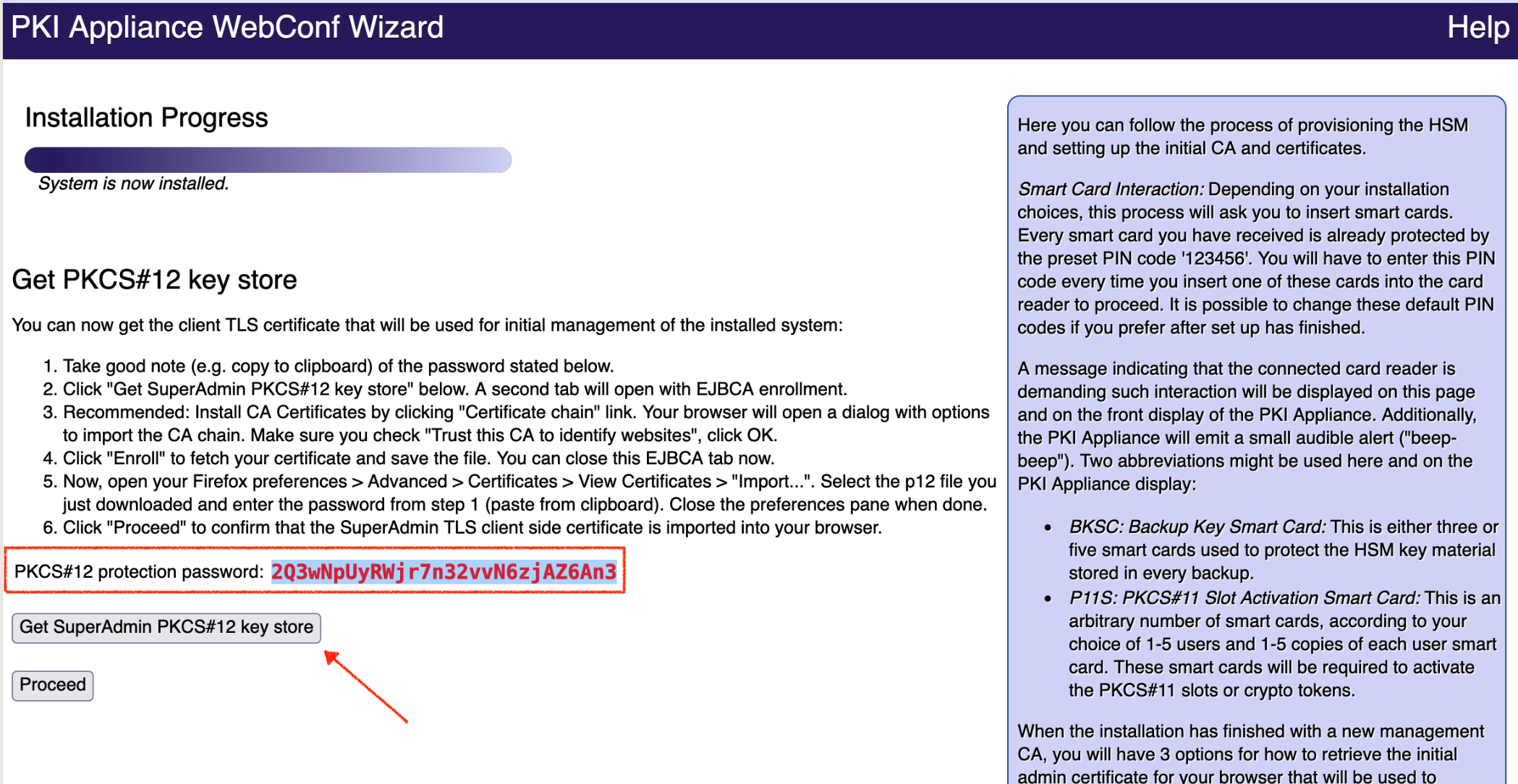
- The Enrollment with Enrollment code page opens in a new tab.
- The Username is preset. Click Check to continue.
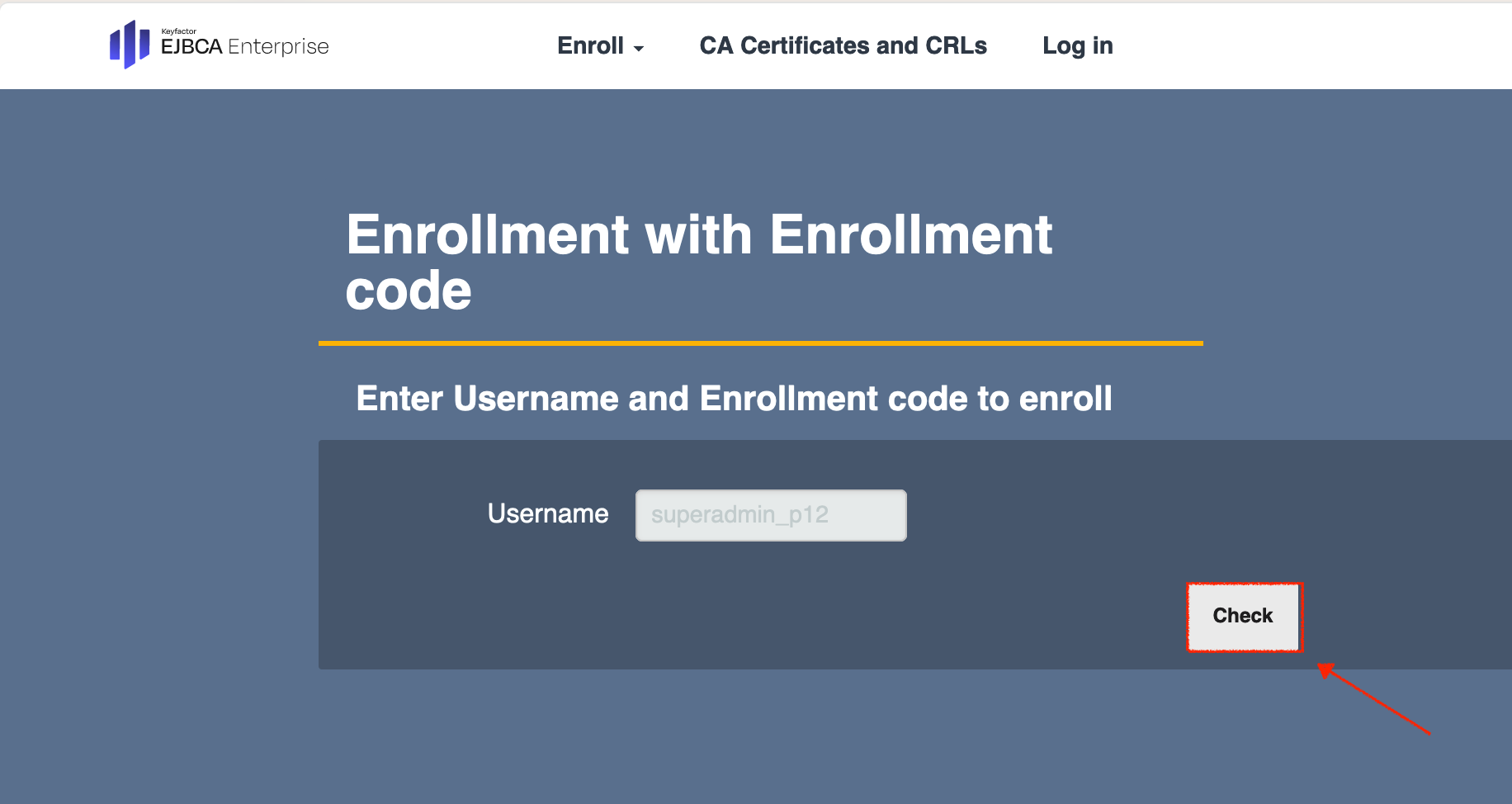
- On the next page select the Key algorithm from the drop-down menu.
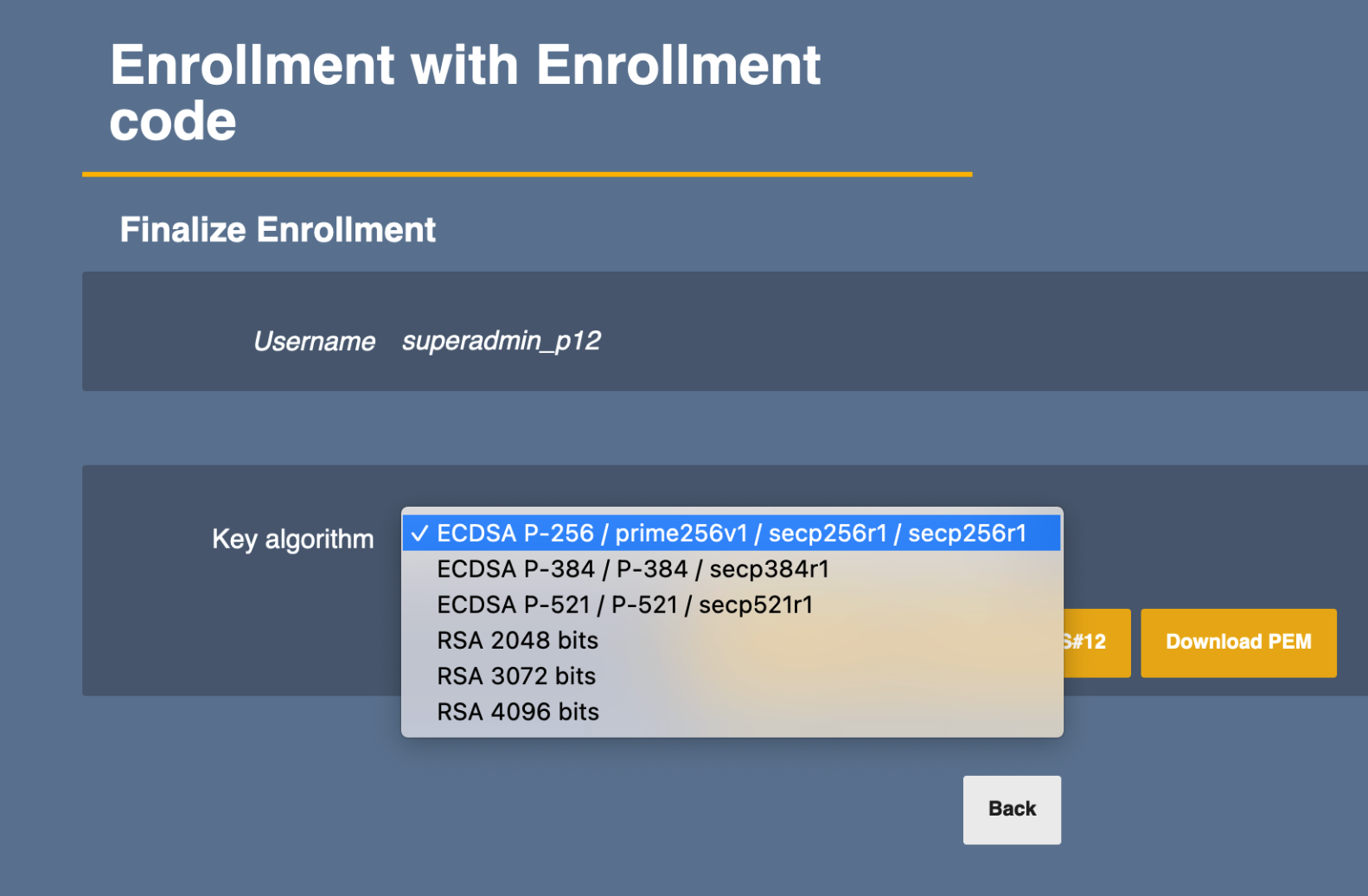
- Continue with Download PKCS#12 to download the file to the local machine, and close the tab.
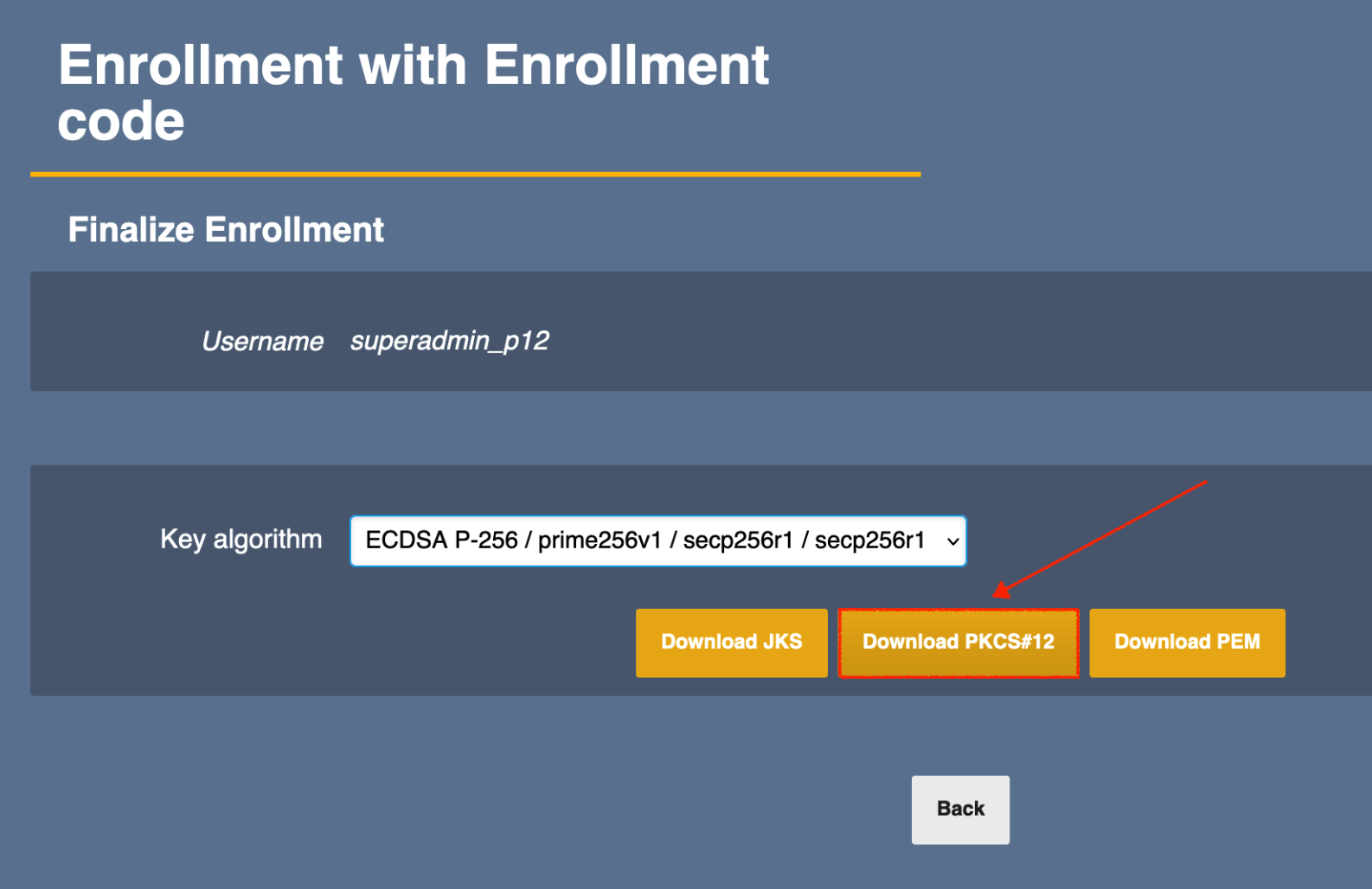
Import the .p12 file into your browser using the PKCS#12 protection password you saved in the previous step 2.
- When the .p12 has been successfully imported, click Proceed.
- After the installation is done click Finalize installation.
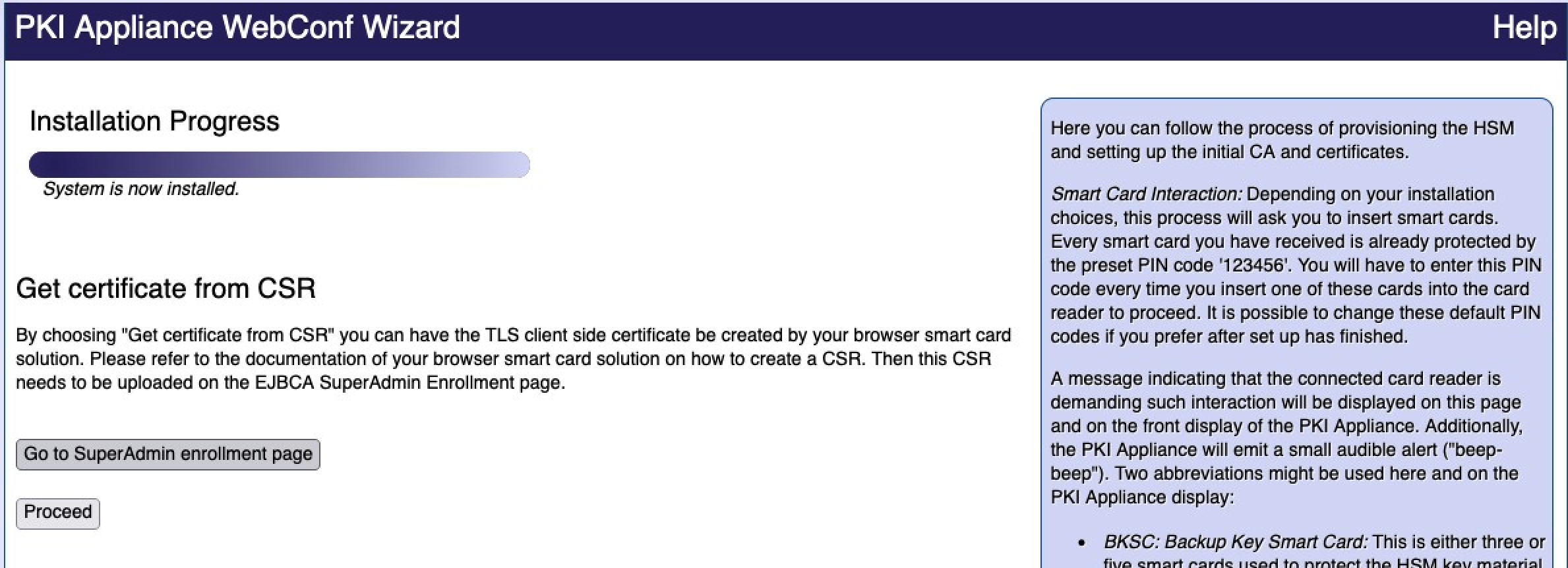
Get certificate from CSR
Only enroll the initial SuperAdmin certificate with the option Get certificate from CSR (Certificate Signing Request) if you cannot use any of the other methods. Creating the CSR and installing the resulting certificate so that it is usable for client TLS authentication is outside the scope of this document.
Proceed as follows to get a certificate from a CSR:
- Select Get certificate from CSR and click Proceed.
Click Go to SuperAdmin enrollment page.
- The Enrollment with Enrollment code page opens in a new tab.
The Username is preset. Click Check to continue.

Choose file or paste the certificate signing request you want to use to issue the initial SuperAdmin certificate.
Click Upload CSR.
- Click Download PEM full chain.
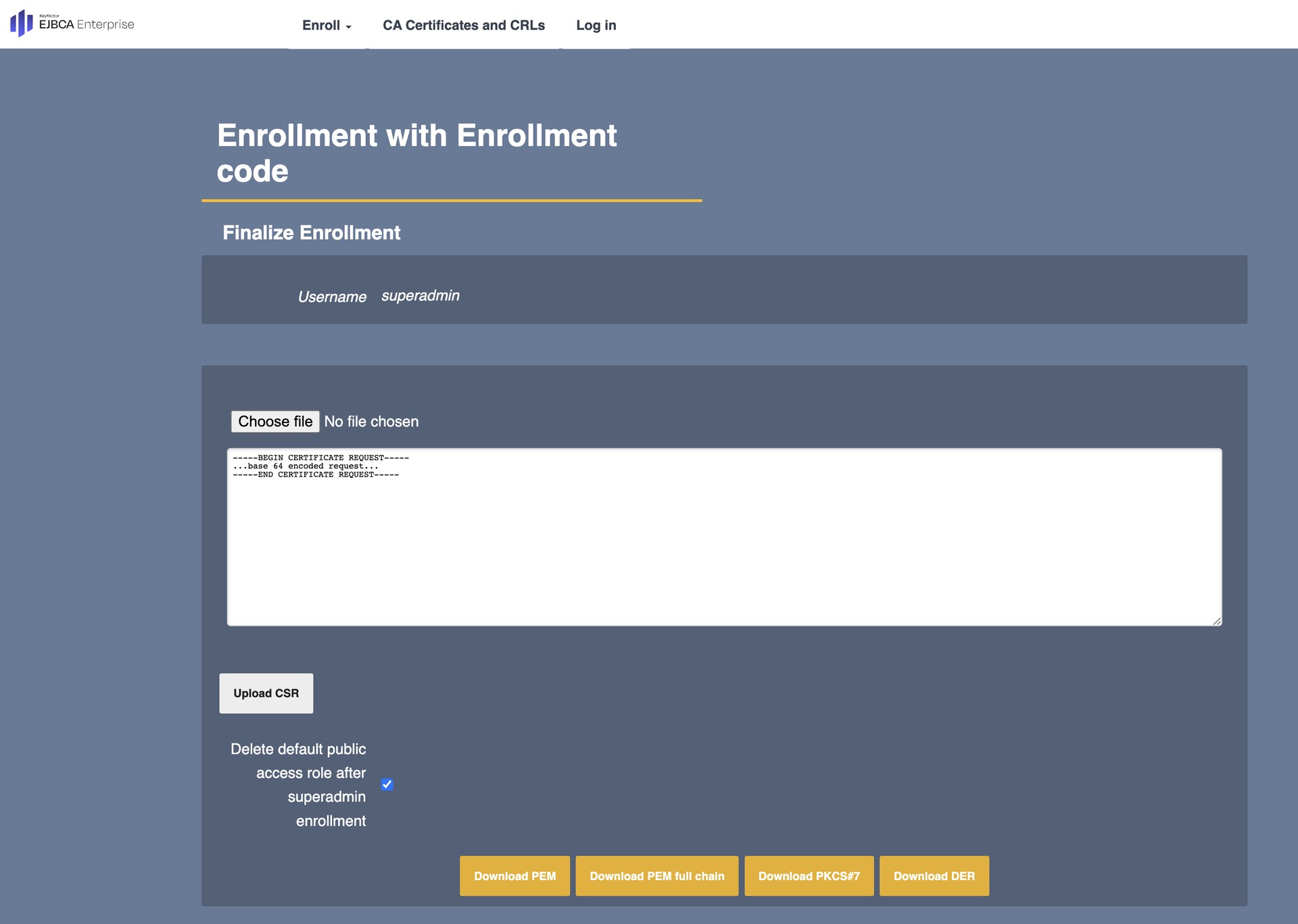
Install the certificate using a proprietary method. Close the tab when done.
In the installation wizard tab, after the installation is done click Finalize installation.
.
Finalize Installation
After you click Finalize installation, it takes about 30 seconds for the process to complete. The browser reloads the page and prompts you to confirm the client side certificate used for authentication.
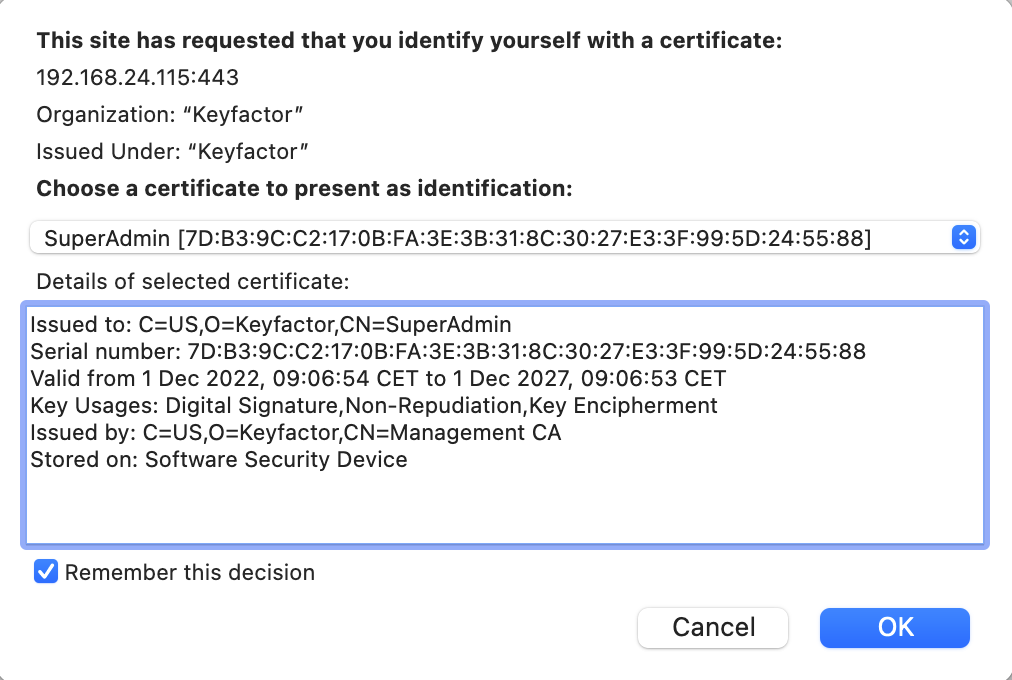
If you use different AdditionalSubjectDN for the different installations, the matching certificate should be preselected. If you want to delete certificates from your browser at a later time, you must to restart your browser for these changes to take full effect.
Some antivirus software performs a Man-in-the-Middle (MITM) on all TLS connections. In such a case, the wizard cancels the finalization step and displays the following message:
"Another client session is currently installing."
To avoid this, you must turn off the MITM feature in your antivirus software or completely disable the software.
Configuration changes become permanent only after about an hour or when the Hardware Appliance is properly shut down and rebooted. Therefore, a power outage immediately after installation can cause configuration changes to be lost. Please keep this in mind when performing a test installation on your desktop or in a test lab.
The final step of the initial setup is to run the web-based configurator WebConf. During this procedure all components of the system will be configured according to the parameters provided.
.png)