HSM Integration
ENTERPRISE
The EJBCA and SignServer Container Sets support integration with various Hardware Security Modules (HSMs) using two primary architectural approaches: HSM integration with PKCS#11 using a separate sidecar container, or over the REST API.
PKCS#11 Integration
To integrate with HSMs that use the PKCS#11 interface, a separate sidecar container is required. This setup facilitates communication between the EJBCA/SignServer application container and the HSM exposing the PKCS#11 interface.
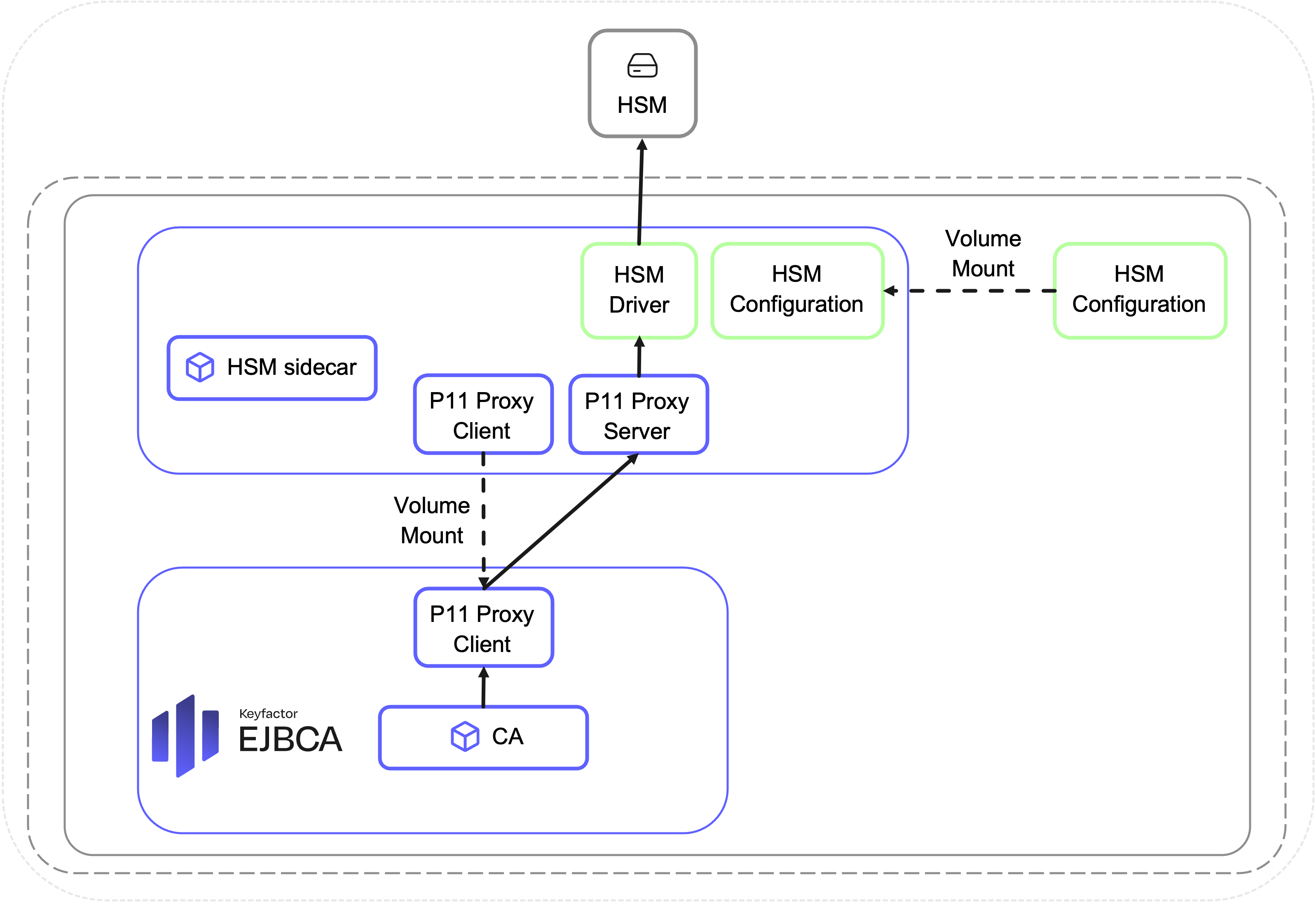
Keyfactor provides a client-server application named "p11proxy" for this purpose, enabling the PKCS#11 client application to transparently use the HSM vendor's PKCS#11 library over the network by passing PKCS#11 library calls over TCP/IP.
The P11 Proxy Client is pulled from an HSM sidecar container before application container startup, and then used by the application to connect over network with the P11 Proxy Server running in the sidecar container. The P11 Proxy Server, in turn, invokes the HSM vendor's PKCS#11 library, returning the result to the client.
HSM integration with PKCS#11 is supported for the following HSM types:
SoftHSM2 (not for production use), see SoftHSM2 integration in Kubernetes.
Thales Luna, see Thales Luna integration in Kubernetes.
Thales DPoD, see Thales DPoD integration in Kubernetes.
Utimaco CryptoServer, see Utimaco uTrust and CryptoServer integration in Kubernetes.
Entrust nShield Connect, see Entrust nShield Connect integration in Kubernetes.
AWS Cloud HSM, see (9.4.2-7.5) AWS Cloud HSM integration in Kubernetes
REST API Integration
For HSMs with a REST API, the EJBCA and SignServer application containers can directly connect to the HSM over the REST API, eliminating the need for a sidecar container.
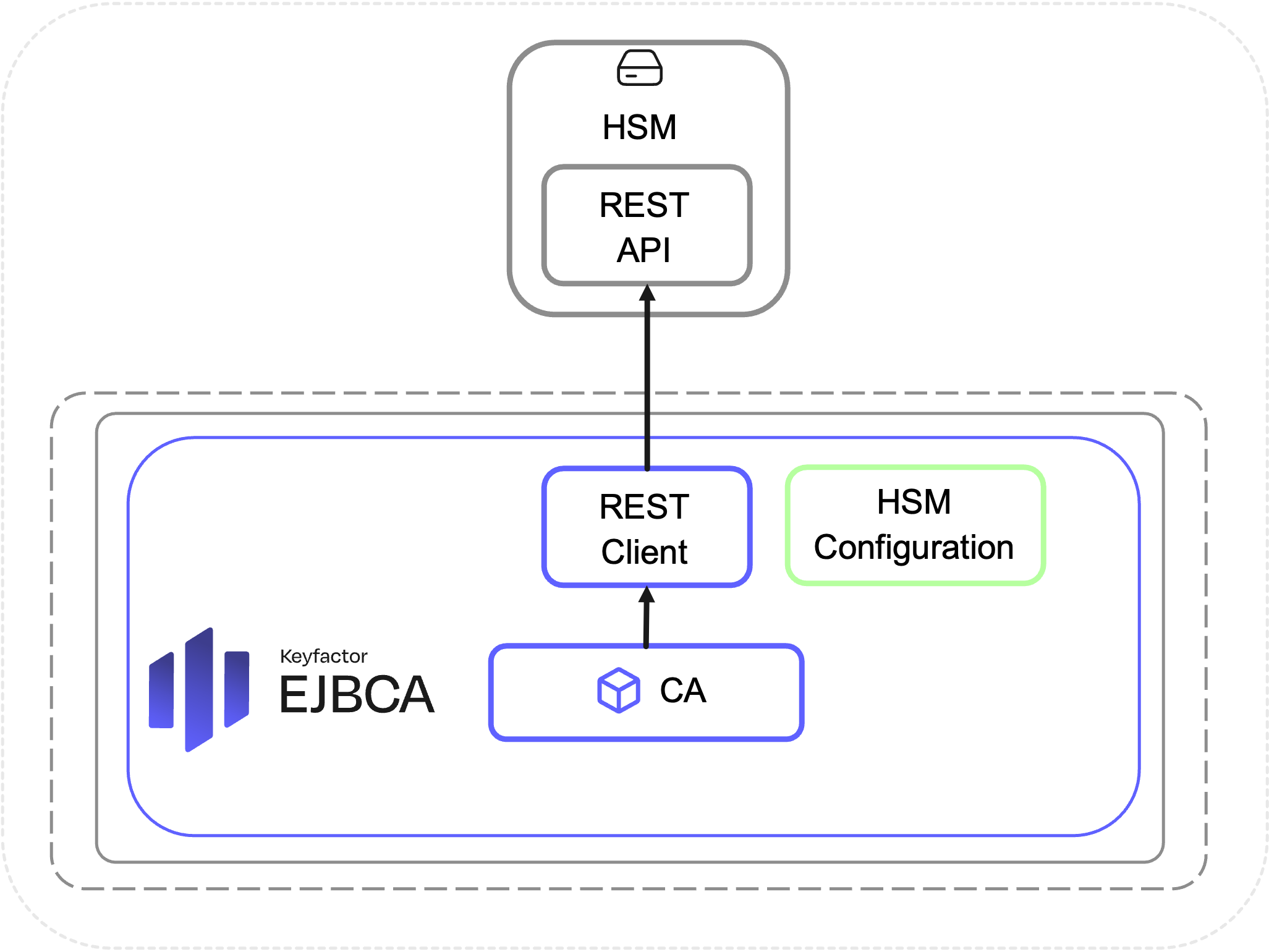
HSM integration with REST API is supported for the following HSM types:
AWS Key Management Service (KMS)
Azure Key Vault and MS Managed HSM
Fortanix Data Security Manager (DSM)
Securosys Primus HSM and CloudHSM Service
For more information on how to set up the HSM integration with PKCS#11 using a separate sidecar container, see the following sections:
.png)