Microsoft Auto-enrollment Operations
ENTERPRISE
The following provides an overview of how to configure auto-enrollment in EJBCA.
For an example guide of setting up MS Auto-enrollment, see the Microsoft Auto-enrollment Configuration Guide and for a conceptual overview, see Microsoft Auto-enrollment Overview.
Kerberos Token Extra SID Group Membership Support
As of EJBCA 9.3, support has been added for evaluating the Extra SID group membership in the Kerberos Token. This means that if an account belongs to a group in another domain, for example, its membership will now be evaluated. Additionally, this extra evaluation may occur when the Kerberos Key Distribution Center (KDC) adds extra SIDs under certain circumstances (for example, the NT Authority\Enterprise Domain Controllers (S-1-5-9) SID).
However, Resource Group SIDs are not directly evaluated due to a known issue in Kerb4J - the library EJBCA uses to parse and evaluate Kerberos ticket data. For more details, refer to the GitHub Kerb4J issue.
As a workaround, to enable the evaluation of Resource Group SIDs, you can disable Resource Group SID compression on the Service Account used by the EJBCA. This causes the Resource Group SIDs to be moved and expanded into the ExtraSids attribute, allowing them to be evaluated in EJBCA 9.3. Keep in mind that disabling compression may increase the risk of token bloat, so this should be carefully considered.
Note that this change does not impact the existing SID evaluation in the MSAE code prior to EJBCA 9.3. Only data present in the Extra SID group membership section of the Kerberos ticket will also be evaluated.
As of EJBCA 8.3, the creation and configuration of auto-enrollment aliases is moved to the CA side and must no longer be added on the RA side. Aliases configured in earlier EJBCA versions will still be visible in the EJBCA RA instance to preserve backward compatibility, but new aliases must be added under the System Configuration on the EJBCA CA instance.
Also note that if you remove the alias defined on the CA side, you must manually clear the cache on the RA side for the change to take effect. To manually clear the cache, select System Configuration > System Configuration > Basic Configurations > Clear All Caches.
To configure auto-enrollment, select Autoenrollment Configuration from System Configuration in the EJBCA menu.
Auto-enrollment configuration is based on aliases and each alias is configured on the Manage Autoenrollment Aliases page. To add a new alias, click Add.
Configure Domain and Connection Settings
The following sections cover the Domain and Connection configuration settings.
Domain Controller and Policies Settings
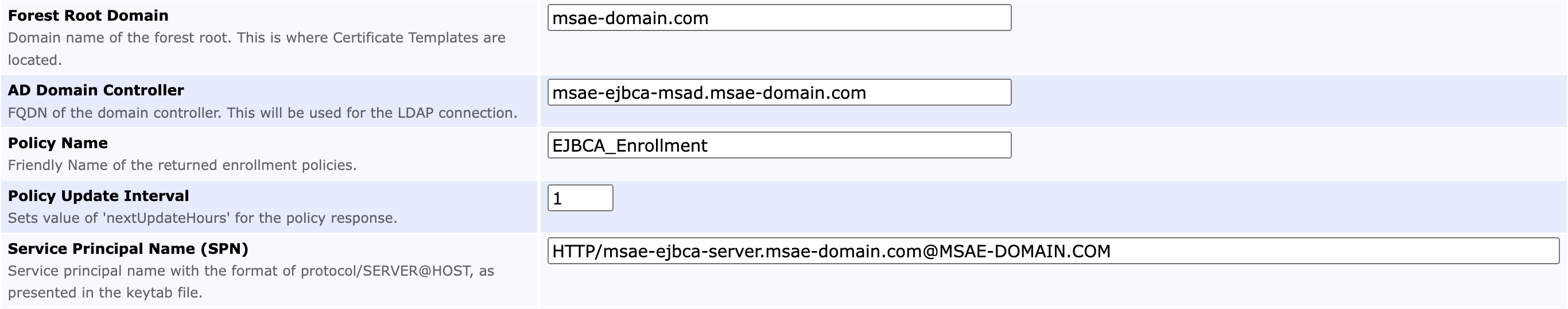
The following displays the settings on the Autoenrollment Alias configuration page.
Field | Description |
|---|---|
Forest Root Domain | Domain name (DN) of the forest root (the location of the Certificate Templates). |
AD Domain Controller | Fully qualified domain name (FQDN) of the domain controller (used for the LDAP connection). |
Policy Name | Display name of the Certificate Enrollment Policy retrieved by clients (free text). |
Policy Update Interval | The value of 'nextUpdateHours' to be set for the policy response. |
Service Principal Name | Service principal name in the format |
The Service Principal Name (SPN) Fully Qualified Domain Name (FQDN) must be an A-record in DNS. Using a CNAME DNS record will not work for kerberos authentication when the windows client authenticates to EJBCA.
Kerberos Settings
The following displays the Kerberos settings on the Autoenrollment Alias configuration page.
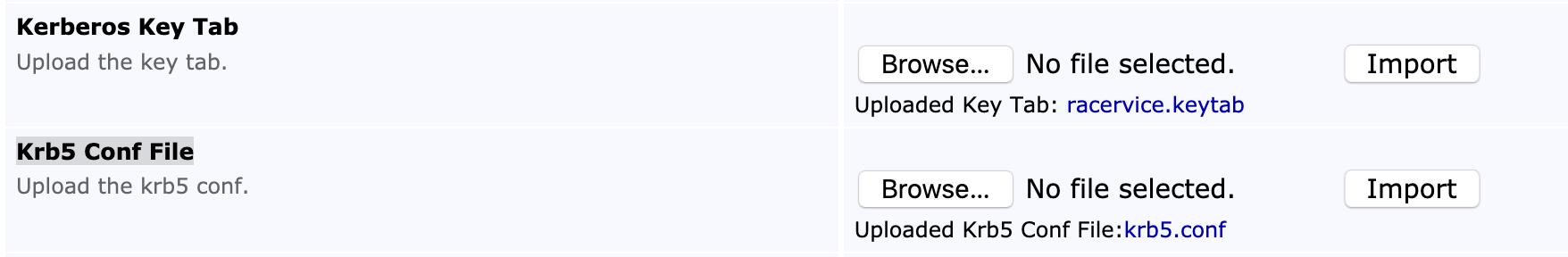
Import the Key Tab and the configuration file using the following fields.
Field | Description |
|---|---|
Kerberos Key Tab | Import a valid key tab file. |
Krb5 Conf File | Import a valid krb5.conf file. |
Configure AD Connection
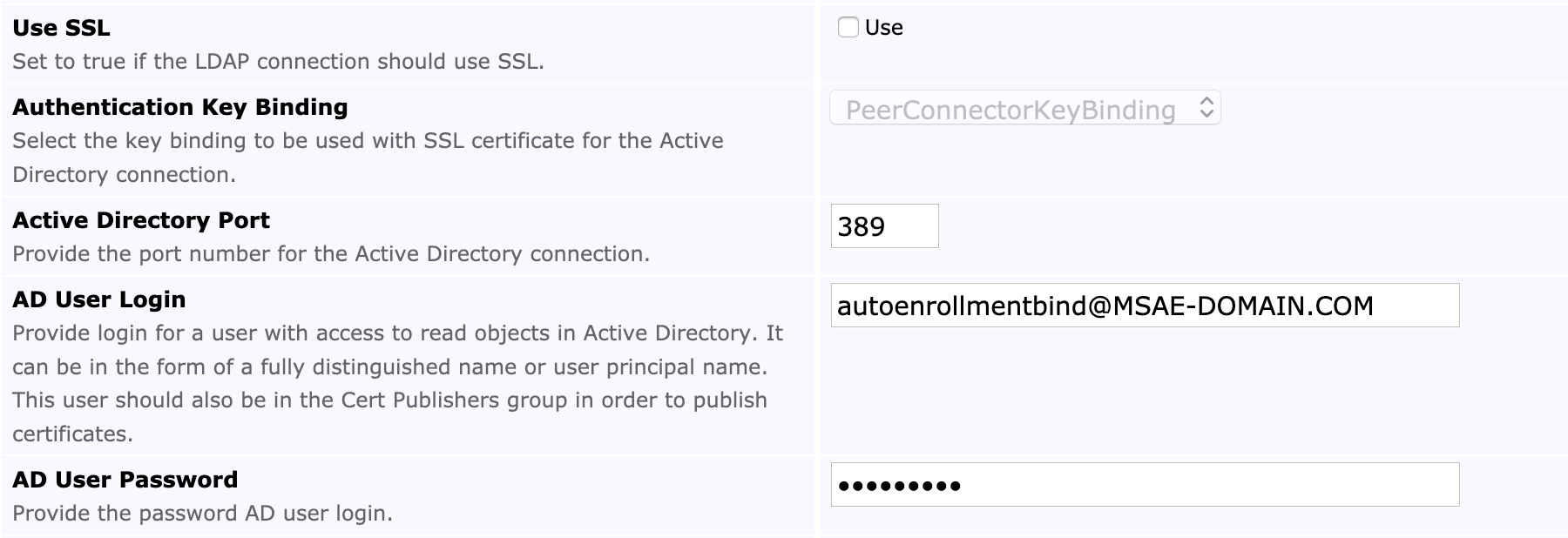
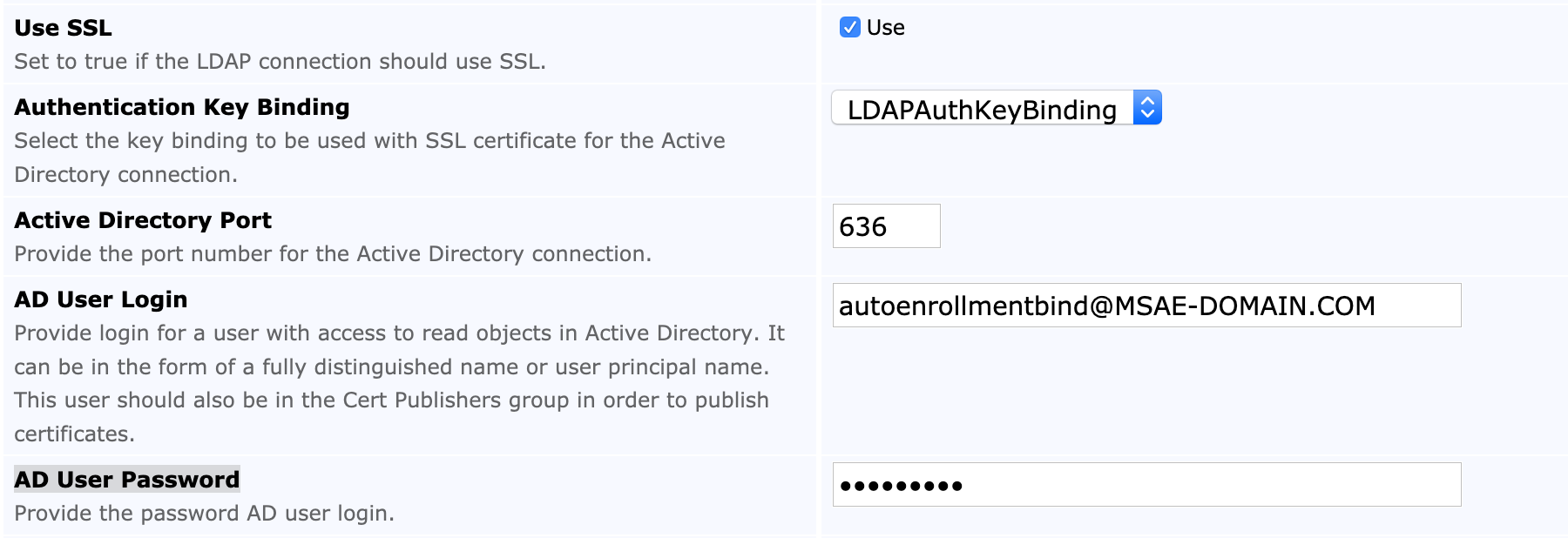
The following fields are set for the Active Directory (AD) connection. Note that SSL can optionally be used for the EJBCA instance's connection to the LDAP server.
Field | Settings Without SSL | Settings Using SSL |
|---|---|---|
Use SSL | Cleared | Selected |
Authentication Key Binding | Disabled | Select Relevant Key Binding |
Active Directory Port | 389 (or port for your LDAP connection) | 636 (or port for your SSL LDAP connection) |
AD User Login | user@DOMAIN.COM | user@DOMAIN.COM |
AD User Password | your password | your password |
The Active Directory bind account (AD User Login) can be provided in any of the following formats:
"autoenrollmentbind@yourcompany.com" (sAMAccountName followed by @, followed by either DNS name of a domain in the same forest or a value in the uPNSuffixes of the Partitions container in the config NC replica)
CN=autoenrollment bind,CN=Users,DC=yourcompany,DC=com" (Full DN)
autoenrollment bind" (Display Name)
EJBCA instance's connection to the LDAP server can be over SSL if specified. Once the Use SSL option is selected, an Authentication Key Binding can be specified. The selected key binding is used as a trust entry for the LDAP SSL certificate. For details on creating the binding needed for the SSL connection, see Setting up a Remote Authenticator.
The following displays the settings for AD connection without SSL:
The following displays the settings for AD connection with SSL:
Configure Default CA
The default CA used for auto-enrollment is selected using the Default CA field.
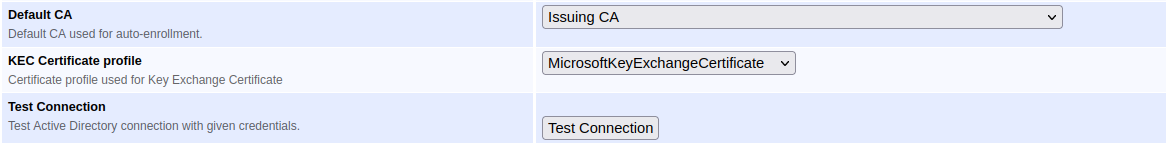
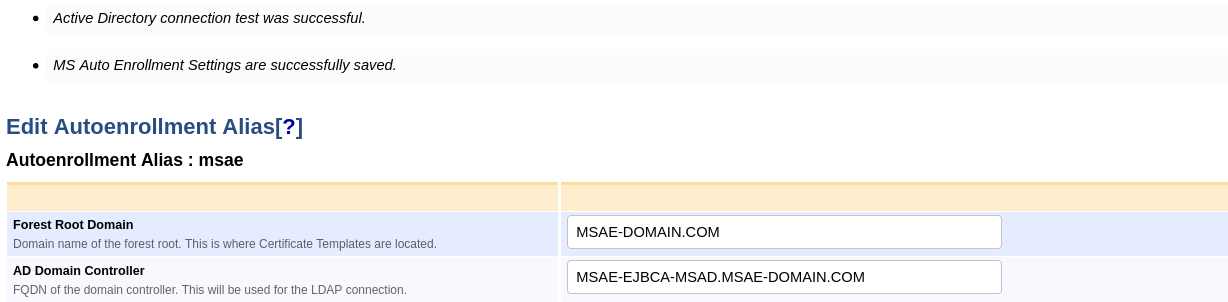
Once the configuration has been stored by clicking Save, the AD connection can be tested by clicking Test Connection.
A successful connection will show the following message:
Configure Microsoft Auto-enrollment Templates
In order to enroll through Microsoft Auto-enrollment, the Microsoft Templates are mapped to End Entity Profiles and Certificate Profiles.
In the Available MS Templates section, select a Template, an End Entity Profile and a Certificate Profile and click Add.
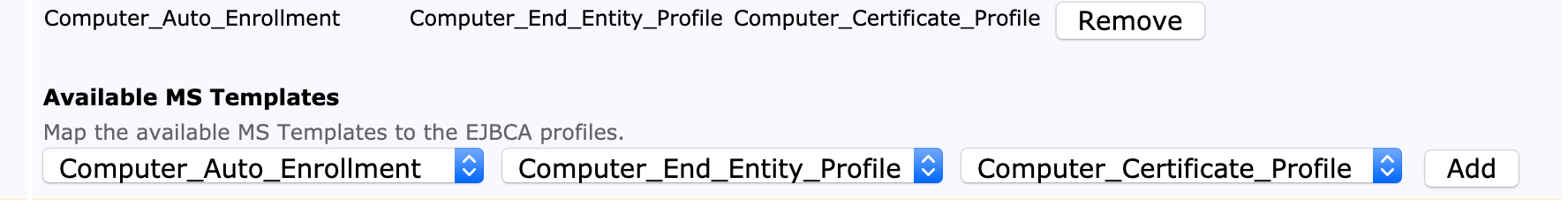
Added template mappings are added and listed as Mapped MSAE Templates.
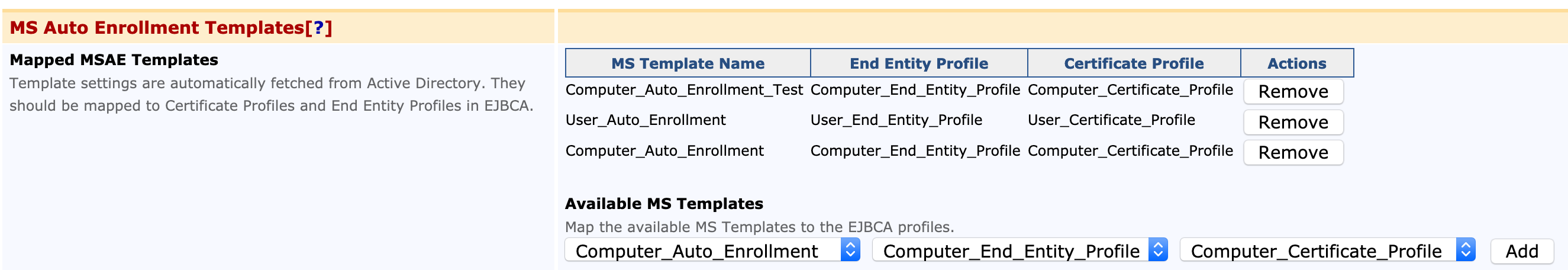
For performance reasons EJBCA caches Certificate Templates during policy retrieval from AD. How quickly this cache expires (expressed in seconds) can be configured in the Certificate Template Cache Lifetime (seconds) field.

OPTIONAL Configure Key Archival
To optionally enable key archival to allow recovering the private key, configure the following:
Select a KEC Certificate profile for auto-enrollment with key archival in the auto-enrollment alias configuration:

Activate Enable Key Recovery in the EJBCA System Configuration:
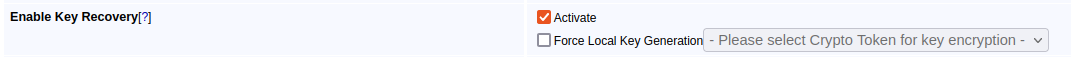
For more information, see EJBCA Configuration.Enable Key Recoverable in the end entity profiles used in the auto-enrollment alias configuration.
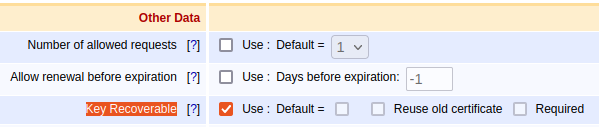
For the MS Key Archival flow to work properly, it is necessary to set the Available Token Types, under the End Entity Profile for targeted certificate, to include P12 as an available option.
Note that in future versions of EJBCA, when support for the FIPS non-compliant algorithms and HSMs is removed from EJBCA, the Key Archival flow will most likely not work if a non-compliant algorithm—such as the Triple DES (DES-EDE3-CBC) cipher algorithm—is used by Microsoft clients for private key encryption. This should be taken into consideration to avoid potential errors or risks when using the Key Archival feature.
For more information, see EJBCA Configuration.
Enable key archival in the certificate template used in the auto-enrollment alias configuration.
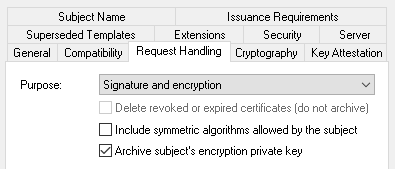
For more information, see Group Policies and Certificate Templates.
.png)